
Have you ever come across somebody on the streets looking like this? Pretty freaky, especially if it's not Halloween. But you know what, Halloween is almost here, so freaky is good. Thanks to creative folks like Eric Testroete and Bhautik Joshi, you can now create an awesome papercraft portrait of your own head for Halloween this year.
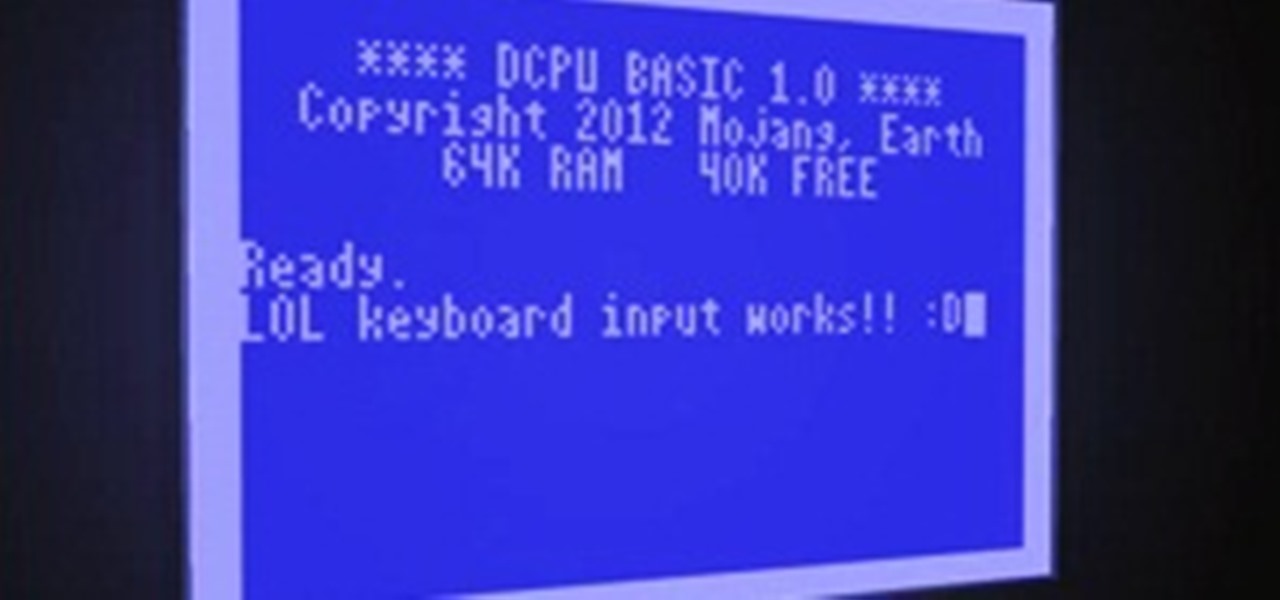
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered with spending enormous amounts of time writing anything much more complicated than a "hello world" application in assembly. What's on the top of everybody's mind is creating a compiler for a more widely used language.

Hey bros, broettes, and normal people. This post is all about INSPIRATION, a word that we hear a lot during years when the Olympics are on, but screw that, they don't own the copyright and I'm using it.

Submit The Rattling Wall is accepting sophisticated short fiction, travel essays, and poetry submissions for Issue 4 until April 1, 2012. The literary journal accepts simultaneous submissions, but asks to be contacted immediately if work that a writer has submitted for review has been accepted for publication elsewhere.

Medicine, like the internet, is serious business. So when the text that appears on the labels of our medicine bottles makes about as much sense as an epileptic in a rave club, we can't help but take pause. Follow us on a journey of prescriptions and misdescriptions!
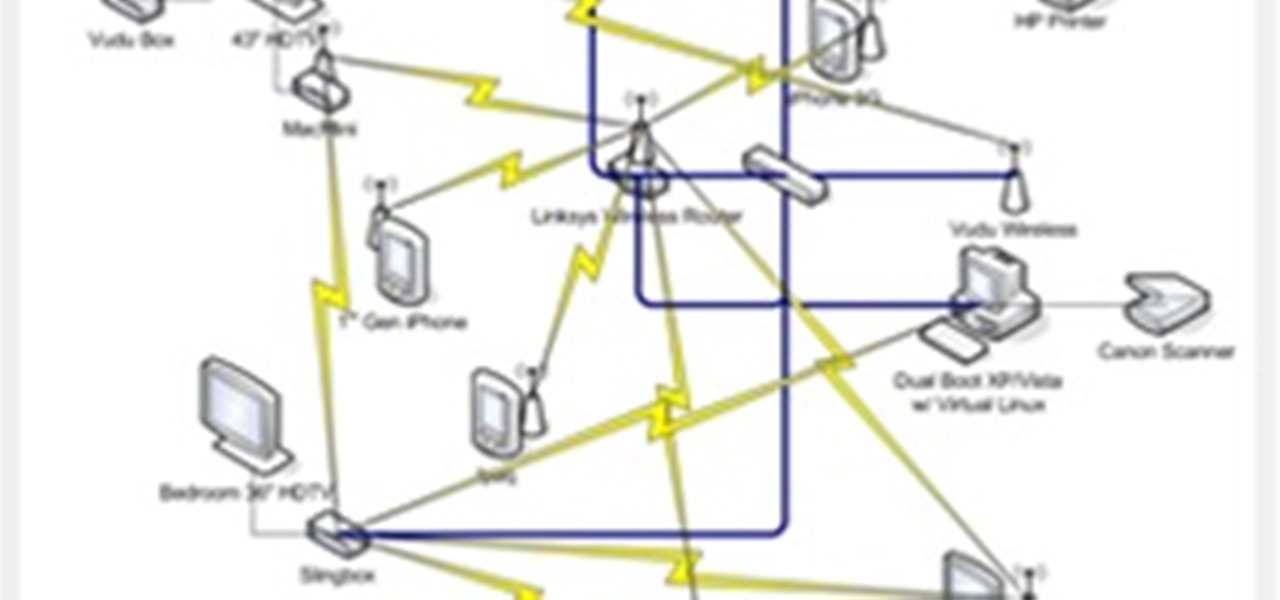
This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Have you grown tired of the standard "Mojang Doors" that are vastly overused? Are you interested in learning an alternative piston door method? Well, this week's Saturday workshop will show you a unique and inspiring way to hide your hidden treasures! This workshop will be centered around creating a hidden passageway using pistons in a way you've never seen before.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Have you ever fallen victim to a redstone trap? Well, this week's Saturday workshop will give you the confidence you need in order to make your own! This workshop will be centered around creating a suffocation trap with an extra added surprise.

I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.

Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone (and consequently snagged a hidden prepaid phone), sometimes having a cell phone jammer comes in handy.

In this week's Phone Snap Challenge, we would like you to experiment with lighting and mood setting to create a silhouette. A silhouetted photograph contains a subject that is defined with an outline, appearing dark against a bright background. The subject generally appears dark, without any detail, while the background is bright and more exposed. Silhouettes in photographs appear to be simple, yet they can convey a sense of drama and emotion. Before you get started, check out this guide on h...

Null Byte is looking for forum moderators! Last Friday's mission was to accomplish solving HackThisSite, basic mission 9. This mission delves a little further into Unix commands and remote directory traversal (which is just a fancy term for going through folders blindly).

Merry Christmas all! I hope you are all having a very wonderful day!

Lots of people are going to be getting the latest iOS devices this holiday season. But what good is a portable device if you don't hack it? Jailbreaking on the latest stock iOS, version 4.3.5, is a bit of a trivial endeavor. Not many people know how to downgrade from this firmware to a firmware that can be jailbroken (pre-iOS 5). If you want the added functionality and the complete control over your device that comes with jailbreaking, then read on.

Erik Demaine is a Professor of Electronic Engineering and Comp Sci at MI, but he is also an origami folder who has had work displayed at the Museum of Modern Art in NYC. He makes some beautiful models and intricate puzzles, but in my opinion the really inspirational work is the curved creased models. In Erik's own words describing the above models: "Each piece in this series connects together multiple circular pieces of paper (between two and three full circles) to make a large circular ramp ...

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

Let's face it, CDs and DVDs are a thing of the past. We no longer use them as a storage medium because they are slow, prone to failure in burning, and non-reusable. The future is flash memory. Flash memory is cheap, fast, and efficient. Eventually, flash drives might even replace discs as the preferred prerecorded selling format for movies.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. If you missed this Workshop check out the follow up tutorial Techniques in Architecture.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

With the computer's rapid increases in power and efficiency, computer virtualization has taken the scene by storm. With virtualization software, and powerful enough computer hardware, your computer can run a virtual computer within itself. This effectively gives you multiple OS's on the host OS. This can be used for a lot of cool stuff that your computer would normally be limited by. Let's take a look at a few.

This is the Windows OS counterpart to my tutorial on how to burn the new XDG3 formatted games on Xbox 360. Microsoft invented a new disc format system to trump piracy, it's called XDG3. XDG3's standard is to burn a whole extra gigabyte of data to the disc, to allow more content, but more importantly for stopping piracy. This extra gigabyte of data makes it impossible to burn or rip a game the traditional way. So how on earth can we burn our fully-legal back-ups that we should rightfully be ab...

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

This video tutorial shows you how to insert and remove page numbers in word 2007. The new interface of word 2007 makes it very easy to perform the most common layout changes quickly. To help you get used to the new interface we show you some of the more basic tasks in this video tutorial.

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

Halloween is just a few days away, and since I've been churning out the creepy Bingo of the Days for everyone the past few weeks, it seems fitting to do a puzzle based on them.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Social network fatigue sets in when it starts to feel impossible to keep up with all that new content from your friends, followers, and acquaintances on a daily basis. You lose track of stuff you wanted to read more about, and you miss important news from your friends, but are bombarded with inconsequential details from people you don't actually care about. What's the solution? Filter your streams so that you only see the content you do care about, and get rid of the rest.

One of the main reasons I was held back from fully switching over to Linux was the fact that media streaming is nearly impossible. You have two choices in Windows: either you use file sharing with Windows Media Player, or you can just use the Windows Media Center. But both of these softwares are not for Linux or Mac. Microsoft doesn't like to make open source software because they believe in making a profit, instead of allowing others to innovate it.

Gamers who have their Xbox 360's firmware flashed may have recently noticed an inability to play backups, or even make backups of newer games that have come out: Gears of War 3 and Dead Island, to name a few.

Welcome to the Google+ Insider's Guide to all things Google+. We're dedicated to keeping you updated with all the latest news, tips and tricks on Google+, and this official index will serve as a one-stop catalog of all our How-To articles, as well as all the news & updates we've covered over time.

Get ready to rack your brains, because it's time for another Scrabble Challenge! I may have gone a little overboard on last week's challenge (there was over 25 anagrams to solve), so I'm slimming things down this week. This time, there's only one puzzle.

WonderHowTo is currently seeking a new staff member to head up FarmVille World as a highly active community admin. This new community leader would clean up any and all troublesome issues relating to the World, write extensive guides, and be available for all World member FAQs. Help us continue to grow FarmVille World into an increasingly vibrant FarmVille community!

If you want more people to follow you on Google+, you'll have to work for it. Not everyone can be +Tom Anderson or +Robert Scoble overnight, you know.

Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the latest updates on Google+ Photos.

Google+ isn't filled with just Google workers and tech-obsessed nerds. Many creative people are part of the community, and they're using Google+ to connect with their fans. Authors, especially, love talking to people about their work. We've rounded up the best published authors for you to follow on Google+. We've listed their best known works so that you can get an idea of the topics they write about.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Although in recent years street art has reached a high point of public appeal many of the great artists are over shadowed by the likes of banksy and shepard fairey (who are amazing artists for sure, just not the only amazing artists out there). Some of the best urban artists have never had a gallery show or exihbit, and most have only been out of their own country once or twice. But of course, thanks to the internet and movies, i )along with many others) have been lucky enough to see the work...









































