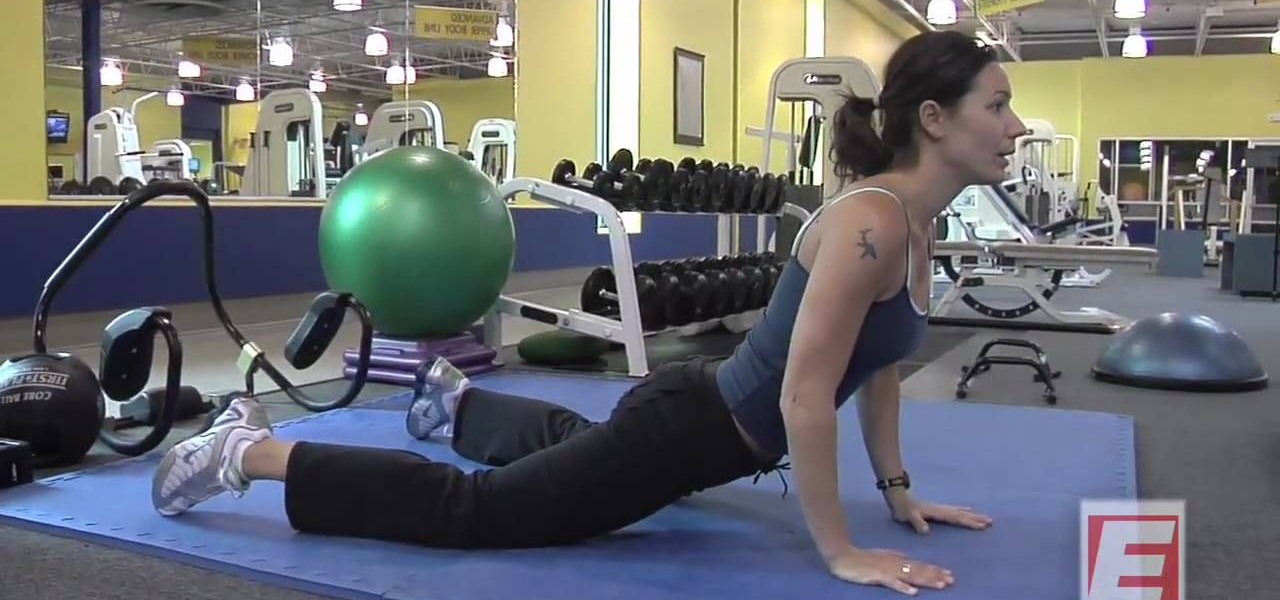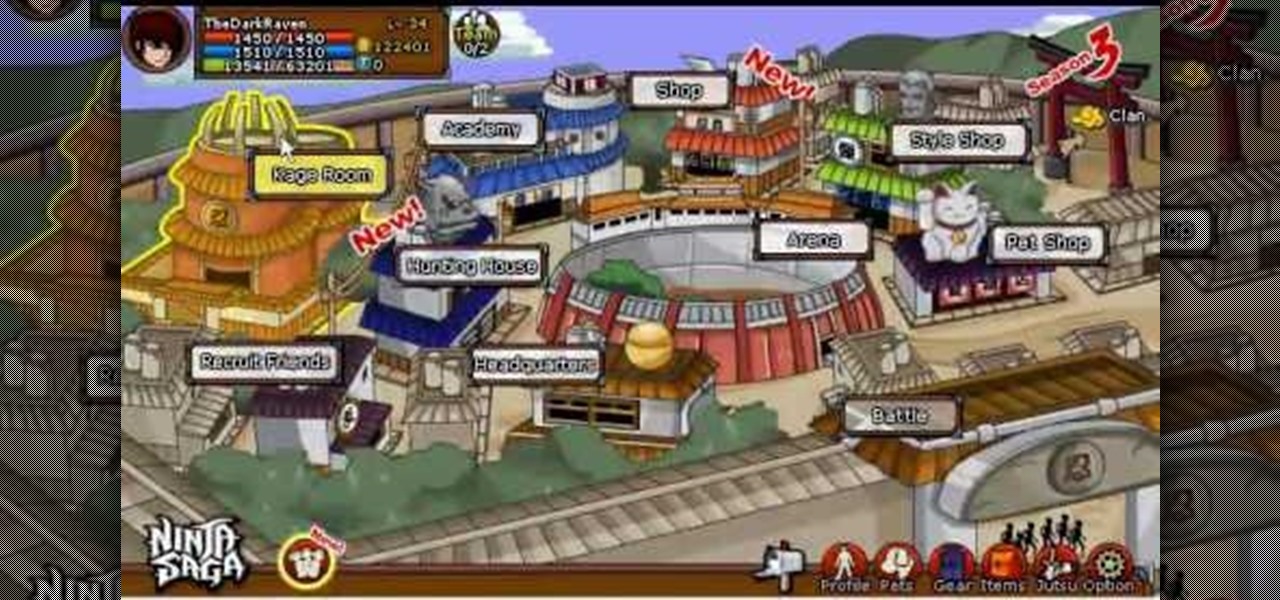
Get higher skills in Ninja Saga! This cheat lets you hack into the game and give yourself higher skills in your jutsu. This shows you how to use Cheat Engine 5.6 and increase all your jutsu skills for your play session. As long as you're using Mozilla Firefox, this cheat will work!
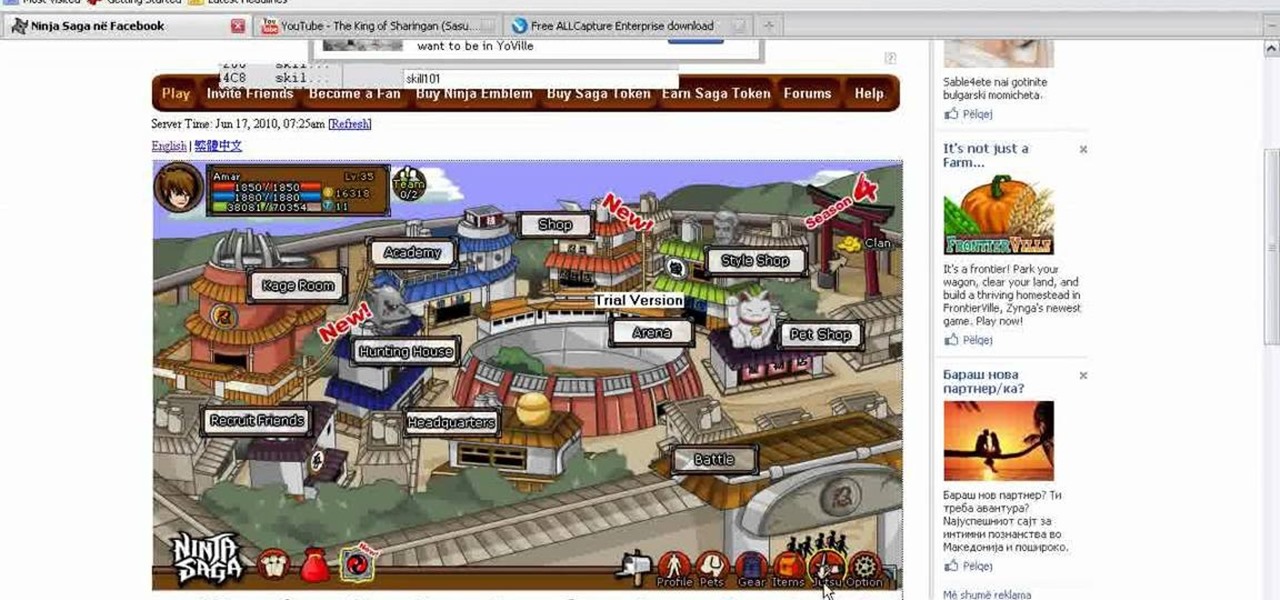
Hack Ninja Saga. The flash-based game Ninja Saga is a role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack Ninja Saga (06/17/10).
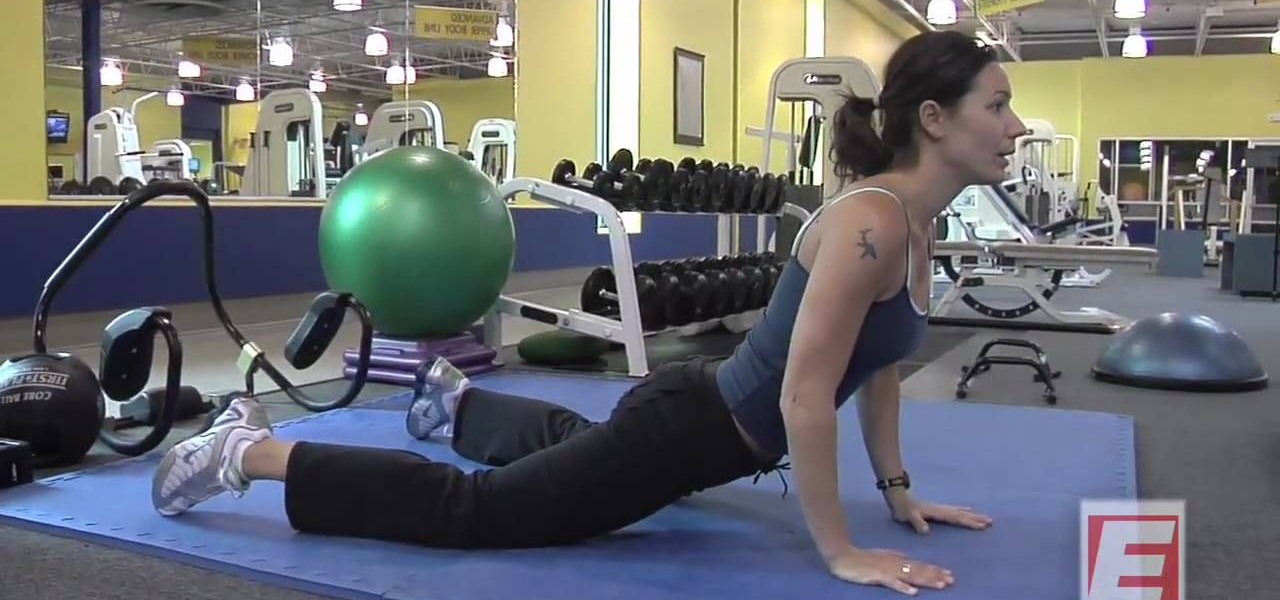
This video is about having a flat stomach with an ab workout routine. Fit tip of the day-4 omega 3 foods which are salmon, avocado, olive oil and almonds. Flat abs-feet flat with abs pulled down flat. Put your hands behind your head. Exhale out for 10 repetitions. Cross over and crunch, squeeze, exhale when you come up. 10 repetitions on each side. Don't release the abs. Keep them tight. Come straight up. Finish off with bicycles. 10 repetitions. Stretch out. Hold yourself up, stretch it back...

Are you a young aspiring actress? A triple threat? Many top singers and entertainers today got their start on the Disney Channel. In this video, learn how to get that audition with the Disney Channel... Who knows, it could be your big break!

With the growing popularity of digital downloads, it's important for aspiring musicians to have some sort of download available of their music. If you're an unsigned musician, selling your music on iTunes might seem daunting, but it's actually very easy! Learn how to do it in this video.

Aspiring artists? Try your hand at painting with acrylic paints with this instructional video. Follow these tips & be on your way to creating a personal masterpiece.

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

Whether or not you're an aspiring magician or just curious, this trick is great to learn. It requires only one prop and only involves a very slight modification.

Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack levels and gold in Ninja Saga (11/11/09).

Hack Ninja Saga. The flash-based game Ninja Saga is role-playing game involving… you guess it… NINJAS! Check out this video tutorial so you can learn how to hack Ninja Saga EXP (11/07/09). Download Cheat Engine.

How do you get bigger biceps, the age-old quest for bigger guns. Well, first things first, more is not better. Hefting around 50-pound dumbbells as opposed to 20-pound dumbbells is not necessarily going to build you bigger biceps because what's probably happening, you're probably not using full range of motion, you're jerking a lot, you're not focusing on that muscle alone. Practice lifting weights to get bigger biceps. Learn how to increase arm strength and size in the biceps with weightlift...

Have you tried working out with hanging knee lifts? If so, you know that they are an essential part of lifting weights and strength training. This fitness how-to video demonstrates how to work out the legs and abs with hanging knee lifts. Learn how to do knee lift exercises in this training video.

Have you tried working out with a bicep curl? Biceps curls are an essential part of lifting weights and strength training. This fitness how-to video demonstrates how to do these exercises with perfect form. Getting big biceps means doing curls and lifting dumbbell weights. Learn how to do biceps curls to workout the muscles in this weightlifting video workout.

Have you tried working out with outer thigh presses? Outer thigh presses are an essential part of lifting weights and strength training. This fitness how-to video tutorial demonstrates how to increase thigh power with outer thigh presses. Learn about muscle training and exercises in this video.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

More and more tech-savvy leaders are flocking to the lucrative and exciting world of project management thanks to the high-pay, analytical environment, and nearly unparalleled flexibility. But this means that competition for the best positions in this dynamic field is fierce. If you want to stand out from the crowd, you're going to need to have more than a few base-level certifications on your résumé.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Soon, kids young and old aspiring to imitate Iron Man will only need to learn how to duplicate Tony Stark's snarky wit, because Hasbro will now supply the augmented reality helmet.

Although The Last Jedi hype has mostly passed, there are still a good number of fans out there dueling Sith lords in augmented reality via their new Lenovo Mirage headsets. Now, thanks to an update on Thursday, those aspiring Jedi have a new AR challenge to engage in the Star Wars: Jedi Challenges app.

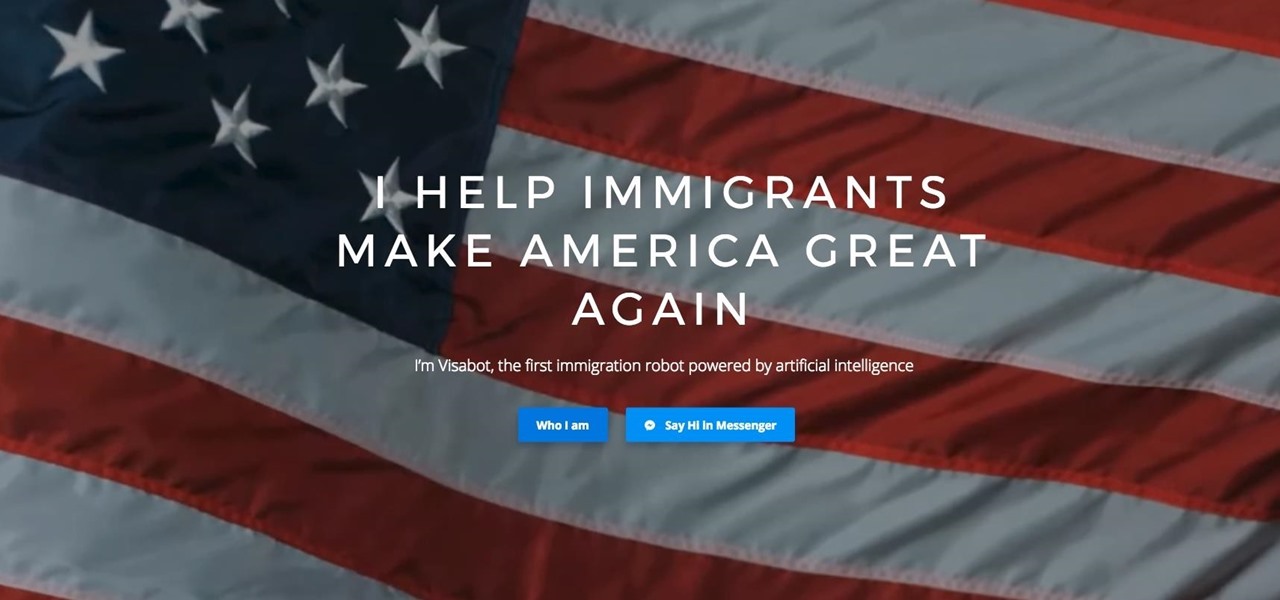
Getting your green card can be an extraordinarily complicated and difficult task. Often times it seems so daunting that it's hard to know where to begin. Thankfully, Facebook Messenger introduced "Visabot" last year, a chatbot in the app that helps with all things immigration. Now including applying for your green card.

Uber has lost market share to Lyft, its main competitor. Uber's US market share dropped from 84% to 77% between January and the end of May this year, and the ride-sharing company has continued to run into legal, public-image, and internal trouble. Lyft, on the other hand, has been growing.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

Love him or hate him, we all know President Trump has a strong presence on Twitter. Whether it's 3 pm or 3 am, the president is probably tweeting. His frequent Twitter habits are often discussed by the media, and they've especially caught the attention of lawyers at Columbia University ... but not in a good way.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

The big Waymo versus Uber trial isn't scheduled until May, but the heat between Uber and Waymo is rising fast; Waymo wants Uber's driverless trials shut down by a court injunction, unless ex-Google employee Anthony Levandowski testifies in court.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

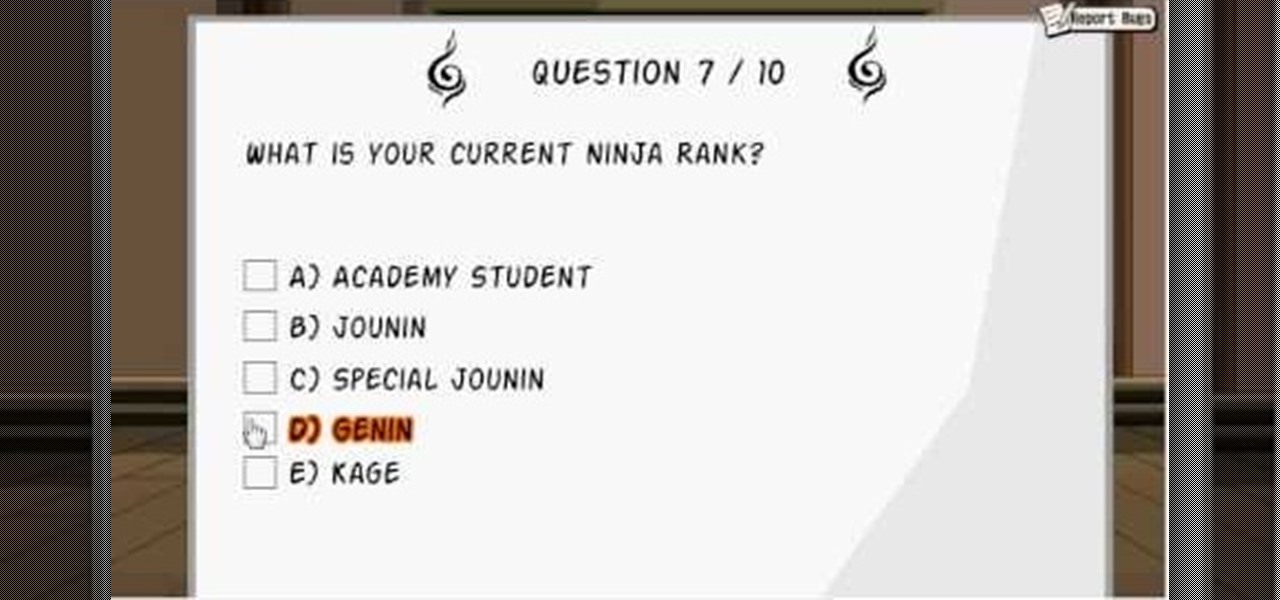
The chunin exam. It's one of the hardest parts of Ninja Saga. Can you pass the test? Or do you need a little help on this exam?

If you're an aspiring actor, your headshot is a vital part of your arsenal. It is the first thing that most casting agents will see, so it has to be perfect. This video will give you tips for getting the heashot you want, the one that will get you your big break!

Aspiring card shark? Sink your pearly whites into this easy, impressive card illusion. In this free video magic lesson from YouTube user experthowto, you'll learn how to perform the simple "twirl" color change card trick using sleight of hand. For more information, including a step-by-step breakdown of the trick, watch this prestidigitator's guide.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Welcome back, my greenhorn hackers!

Rum is no ordinary liquor. If you have a yearning for some rum, you need to know the basics of rum culture, like what rum is (and isn't), what kind of rums are available, and how is rum made. Once you know this information, you'll be a rum master. Rum is available in a wide variety of weights, ages, and blends. If you aspire to become a connoisseur of fine rums, start with the basics.

If you want to learn how to be a real graffiti artist, it can be a challenge to know where to get started. This tutorial video walks you through some of the beginning steps. Presented as a text slideshow, it's very basic but contains some sound information for aspiring graffiti artists.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.