I love making beeps and bloops with the Arduino pitches library, but sometimes archaic 8-bit tunes just don't cut it. Whether you want your robot to terrify your enemies with a demonic synthetic voice, you just need a pocket boom box on the go, or you want to a miniature guitar amp, a simple LM386 amplifier can crank up those signals loud enough to play through any speaker.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

If you've run out of time for all of our more time-consuming Halloween costume ideas, here are some places on the web for free, downloadable paper masks. There must be at least 100 options among these links to satisfy your last-minute costume needs! Just download, print, and cut 'em out to the appropriate size, then either glue a stick/handle on or tie some elastic string on.

Augmented reality enthusiasts who expected an AR hardware unveiling at Apple's annual iPhone launch event might not have to wait much longer.

New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality.

While the consensus among some in the augmented reality community is that the Microsoft HoloLens is the best device available at present, it also remains the most cost-prohibitive option, with the development edition costing $3,000.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

GE Aviation and their software partner Upskill are seeing success by giving their mechanics smart tools and smart glasses, the latter in the form of Google Glass.

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

As with any new smartphone (but especially with Apple), the iPhone 8 is generating rumor after rumor. This newest rumor, however, rocks the boat a bit, as BGR reports that the iPhone 8 may release at Apple's standard time in the fall, but the 3D camera will be pushed to the 8s.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

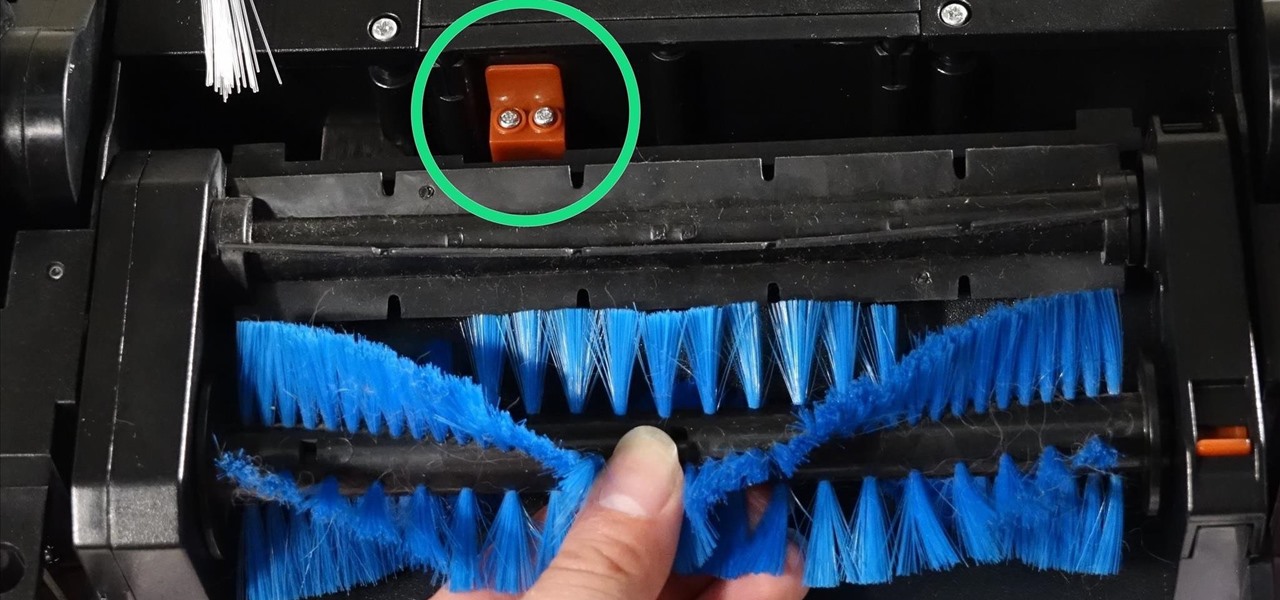
One of the quickest repairs for bObi is replacing the main brush motor. To do this, you'll need a Phillips head screwdriver and a replacement main brush motor.

The Samsung Galaxy S5 display can be replaced by most do-it-yourselfers with some basic mechanical skills and a few inexpensive tools. The good news is that once you replace your display assembly your screen will be good as new with no bubbles or dust on the inside. The replacement part is a bit pricey but that is a good percentage of the cost involved with manufacturing this device. Below is a video showing the entire process from start to finish. It's best to turn on your volume for the nar...

Presentational video for our DIY Camera Crane project. Video: .

Here are instructions to make an origami tarantula. Detailed visual instructions are on the video that contains a map and images of the origami.

There are tons of ways to make simple DIY lamps out of things you have lying around at home. If you've got an empty container, (even an orange or tuna can), there's probably a way to upcycle it into a lamp of some sort, and they can come in handy if you ever lose power.

Steaming food has a lot of advantages over other cooking methods. The gentle heat of steam allows for meats, such as chicken wings, to become more moist after cooking.

Former soccer star and current celebrity David Beckham has the augmented reality abilities of Facebook and Instagram as allies in the effort to eradicate malaria from the world.

Between Renault Truck's testing of the HoloLens in factories and BMW promoting its newest model through Snapchat, the auto industry is hot for augmented reality to improve internal operations and engage consumers.

Christmas came early for Apple, as the company was awarded more than 40 patents by the US Patent and Trademark Office on Tuesday, including one covering a system for compositing an augmented reality construct based on image recognition.

You can bet Thor costumes will be prominent among the superheroes seen this Oct. 31. Since the summer, there has been no shortage of coverage for Thor: Ragnarok, and the timing of its November release couldn't be better as a tie-in with the cosplaying holiday known as Halloween. This year, the success of pulling off the Thor costume will rely on how well your new Thor helmet looks, which as it happens, you can DIY at home, using a few simple supplies and perhaps a trip or two to the craft and...

Perhaps in tribute to the season premiere of Game of Thrones, Google Glass is demonstrating that what is dead may never die, as Alphabet's X (formerly Googlex) has revealed that the Enterprise Edition of the smart glasses are now available to businesses.

New research reveals how E. coli bacteria construct elaborate and effective tunnels to pump unwanted molecules like antibiotics and other toxins out of cells. The discovery could help us better understand how antibiotic resistance occurs and give us a leg-up to beat them at their own game.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

With just a Phillips head screwdriver and this walk-through, you can open and close any bObi robot vacuum. So long as you have a replacement wheel, follow these steps to install it yourself.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Most people wouldn't think of butter as a flammable substance, but in this project—it definitely is! We're making emergency candles that burn for hours using just some toilet paper and a bit of butter!

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

Ford's appointment of Jim Hackett as its new president and CEO reflects how the company is largely pinning its long-term survival hopes on its driverless business. Following his previous role as head of Ford's Smart Mobility division, which overseas Ford's autonomous driving activity, Hackett will help the company take a more self-driving direction as a whole.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

Alphabet's moonshot factory, X (formerly "Google X"), is a secretive place, but it seems that when they are close to graduating a project, then they need to staff it up quickly. Watching for these job ads is one easy way to know they're close to budding off a baby.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.