Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

The 68th Annual Golden Globe Awards take place this Sunday, January 16th, 2011 between the hours of 5 and 8 PM PST — that's 8 & 11 PM for those of you on the East Coast (and Somewhere in the Middle for those of you Somewhere in the Middle).
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES...
Technology: The Less You Know the Better?

Accounting and Finance Degree

In the age of automatic video editors and all around software-assisted creativity, how can a humble blogger help people master a program if said program does all the work for you?

STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/

STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC

Update This issue has been resolved

On June 23, 2003, Linden labs created a free client program known as Second Life. This program allows users, or residents, to interact with each other in a virtual world by using avatars. Thanks to this program, residents are able to explore, socialize, and create and trade virtual property, and services with each other. Second Life has become one of the most popular programs used by various age ranges from 16 to 60, but how do you enter this world and get your own avatar?

hey im jesse...whats up u guys!..listeni know there are alot of panks that have been send to you guysand most of them probably have to do with pranking one of the jackass crew...am i rightbut i think we need a new kind of prank that would be involving a real civilian ( not actor) and one of the jackass crew...that way at first one of the jackass crew member wouldnt be suspecting something that he will be pranked...so we prank the civilian first then one of the jackass crew member, so here is ...

In this video series, watch as massage therapist Sufi Bradshaw teaches how to give a Tai Chi massage. Learn how to warm up for a massage, how to make the client feel comfortable, how to massage the legs, back , and arms, and how to finish a Tai Chi massage. Start helping your friends relieve stress with the help of this great video series from the experts at Expert Village. Do Tai Chi massage therapy - Part 1 of 9.

This article is going to talk about video and only about video. Why? Because video is very important for any size of business. Even small businesses can use video to promote themselves on the internet. And in the next few years, you’re going to see more and more businesses using video. Even now, I’m going to show you some articles that have been written on different websites talking about video and how small businesses can use them and how businesses need to use them now, especially to rank o...

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

WonderHowTo welcomes guest contributor, +Ryan Crowe - formerly the man behind GPlusTips. Crowe will be providing tips and tricks on how to use Google+ in interesting and innovative ways, and the self-proclaimed Google+ User Experience Enthusiast is nearly ready to launch a website examining social interaction on Google+ called SocioloG+.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Their were many pedestrians in the scene as,they seen firefighters struggling with the horrifying disaster and they couldn't do much only continue to stare as bodies continued to drop..

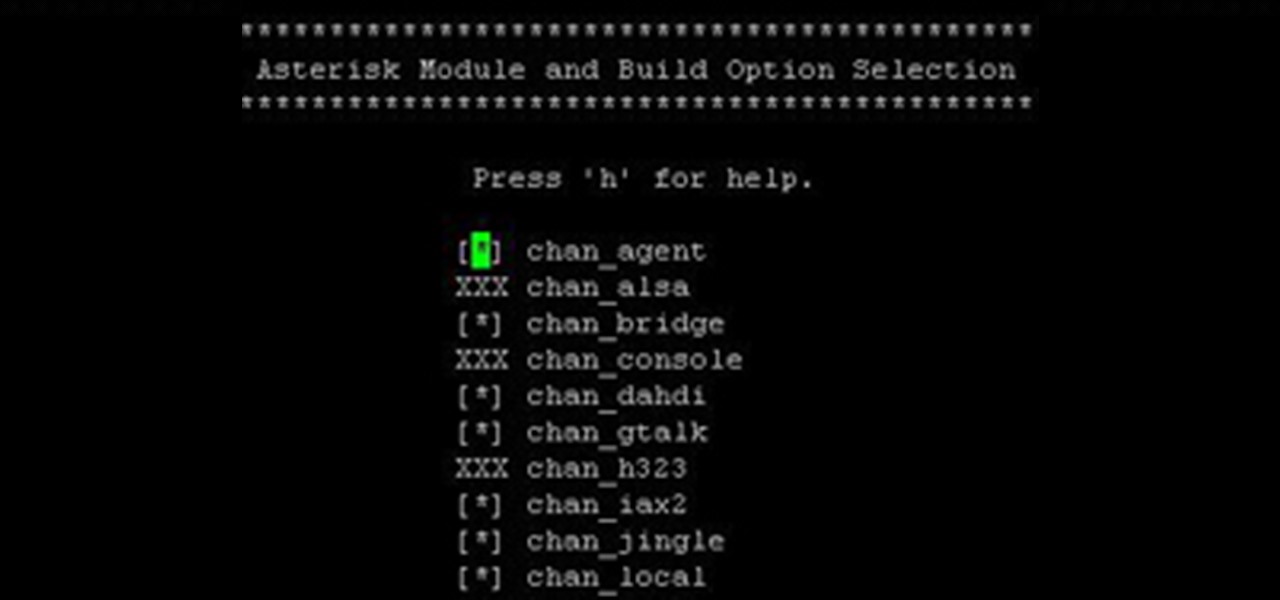
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address?

Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotgun, Gamespy, The Verge, Joystiq and many more websites!Exciting!You can see the full details below are head straight here for the downloads.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet another edited version. Soon you're drowning in a desktop folder full of mismatched documents, all with the same name.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

I don't know what I'd do without my computer. I can't do my job without the internet. I communicate with employers, friends, and family through emails, video chat and Twitter. I schedule meetings and plan deadlines. I bank. I shop. I read the news. I play games. I watch my favorite shows. Yes, I'd be rather lost without this little plastic box of circuits.

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

Introduction Halo: Reach is Bungie's latest and final addition to the franchise. Microsoft has claimed the title and from now on 343 Industries will be working on the Halo franchise. In my opinion, Bungie's last game is the best out of all of them. These are some tactics and bits of advice that I've picked up.

I've been dealing with emotional difficulty for many years. It started when I had surgery for the epilepsy I was dealing, and quite literally, dying with. Since the surgery on March 28, 1990 I have had no seizures, but I have had plenty of emotional difficulty. Along with that, surviving some traumatic events has added some emotional baggage...in other words struggling...along the way.
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States