
How To: Use a framing square
Tim Carter of Ask the Builder demonstrates the basics of a framing square. Tim shows how to make the marks for a simple roof rafter.


Tim Carter of Ask the Builder demonstrates the basics of a framing square. Tim shows how to make the marks for a simple roof rafter.

Learn how to do one arm neutral grip pull ups on a Gravitron machine. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single-leg twisting dumbbell curls. Presented by Real Jock Gay Fitness Health & Life.

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

In his famous 1996 "Content is King" essay, Bill Gates predicted that content is where tech companies will make money on the Internet. The adage clearly holds true in the current phase of augmented reality experience.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe.

The HoloLens has become a frequent sight in medical facilities around the world, but a new demonstration shows just how seamlessly it can be integrated into traditional medical procedures to improve the experience for physicians and patients alike.
Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

Electrical impulses course through our heart and keep it beating. That's why a jolt from an automated external defibrillator can boost it back into action if the beating stops. But new research says there may be more to keeping a heart beating than just electrical impulses.
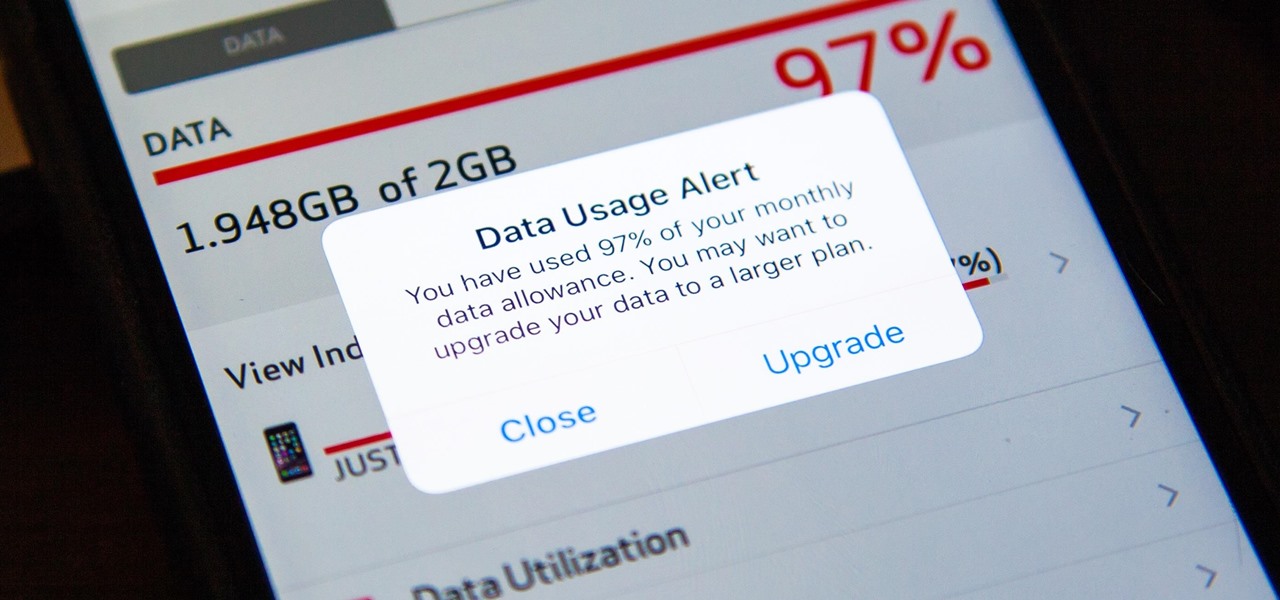
I was one of the first to install the iOS 10 developer beta, and I remember thinking that everything was working insanely well compared to the first iOS 9 developer beta—but then I got a warning that I used 90% of my data 11 days into my following cycle—one day before I updated to beta 2.

When you wear a holographic computer on your face, you gain some things and lose others. That's certainly the case when using Skype in Microsoft's HoloLens. Some video chats will work better because your caller can see what you see, rather than your face—but others just feel weird.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.
Welcome back for another How-To on the Xbox Community Ambassadors World! In this How-To, we are going to tell you how to help someone the right way so you can get a 9/9 rating when your finished assisting someone! Lets begin, shall we?

How to Henna Your Hair Tutorial Pt.2 Please Dont forget to Watch Pt. 1

Video: . How to Henna Your Hair Tutorial #1
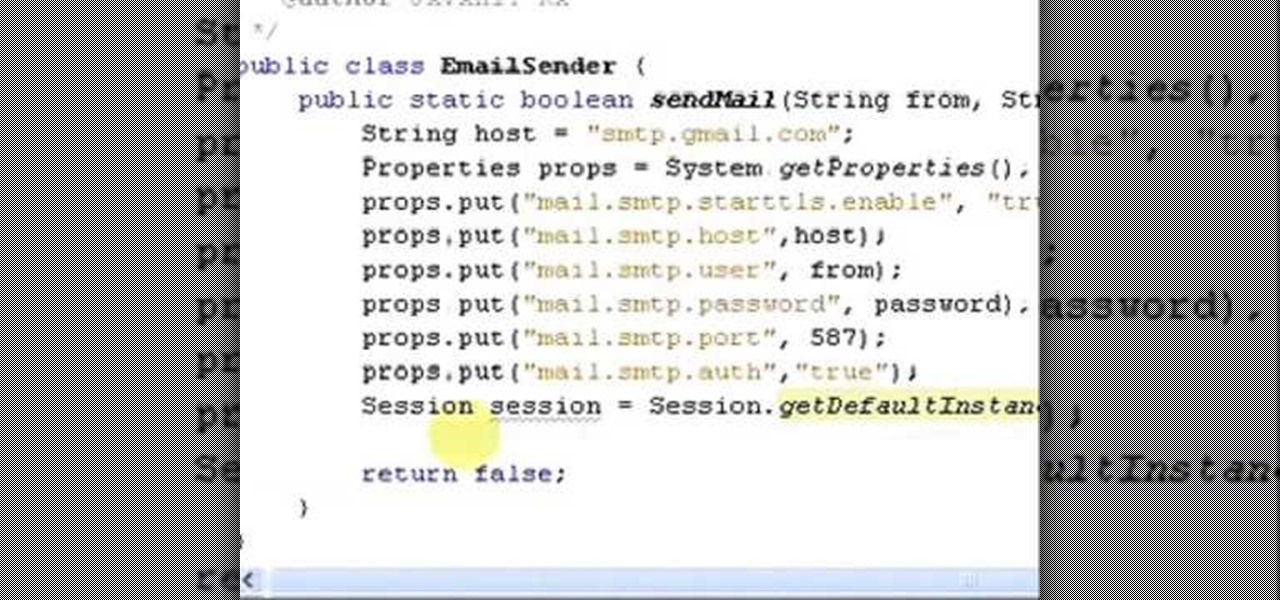
It uses JavaMail API, NetBeans IDE 7.0.1 First download the JavaMail API as shown in beginning of the video then follow the video to send email dynamically from your Gmail account. No need to open your inbox.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

Tattoo lady and reality TV star Kat Von D is obviously extremely talented with the tattoo needle. Creating interesting designs for clients that include celebrities, Kat Von D exudes a distinctive style that includes looking like a tougher version of a classic pin up.

In this video, we learn how to give a professional hand massage. First, spread oil onto the hand with your hands, which will prevent you from sticking together. After this, open the hand up and interlock your fingers with theirs and start to massage the inside of the hand. Open the hand up and work your fingers into the sensitive muscle areas. Go slowly, but apply enough pressure around the hands to make a difference. After this, work the tendons on the front and work your hands around each o...
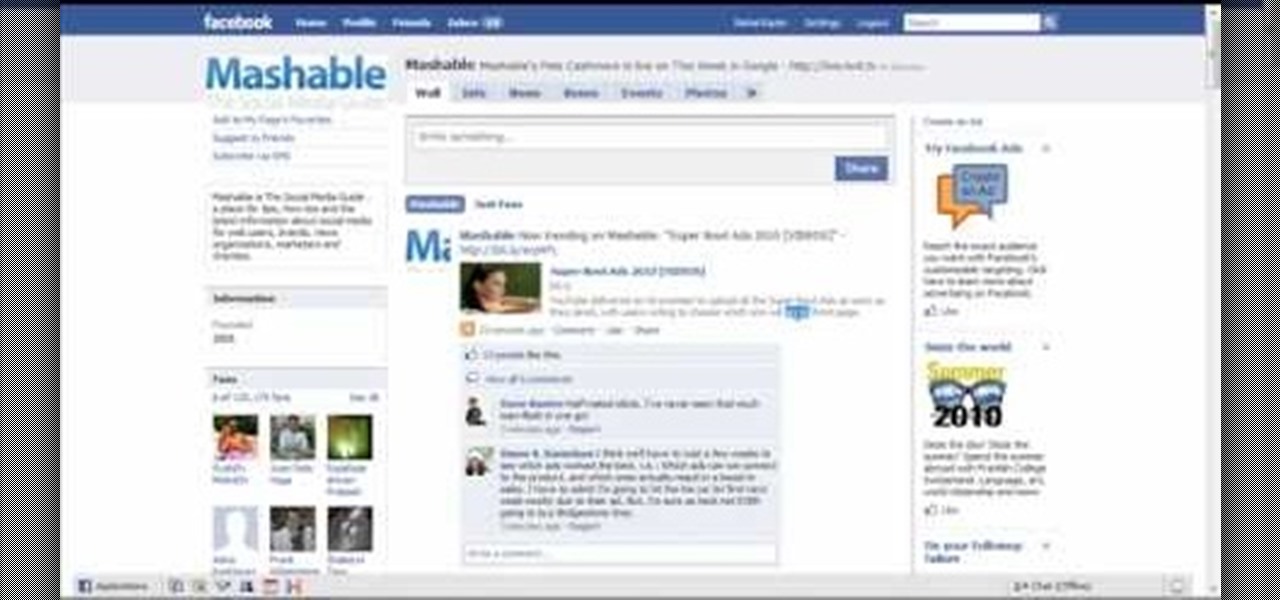
This instructional video Nehal Kazim from Site shows you how to make a complete Facebook fan page. Before creating a fan page evaluate the reasons of making a fan page. A fan page lets you connect with your future clients and fans and keeps them updated and gives them a platform to talk about your organization. To create a fan page go to the bottom of any page and click 'Advertising', select pages and click create a page. Select a suitable category and a suitable name make sure to select it c...

For a mom, there is always so much to do that your own personal care routine may take a back seat. But in this video, top hair stylist Gary France offers tips on how to style very short hair for the busy mom. France shows us his process on a busy working mom. The client receives a lighter color to brighten up her look, a trim to texturize her hair and styles the hair without using a blow dryer, which is great for saving time. France shows us that just because you have kids to take care of doe...
Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.
Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
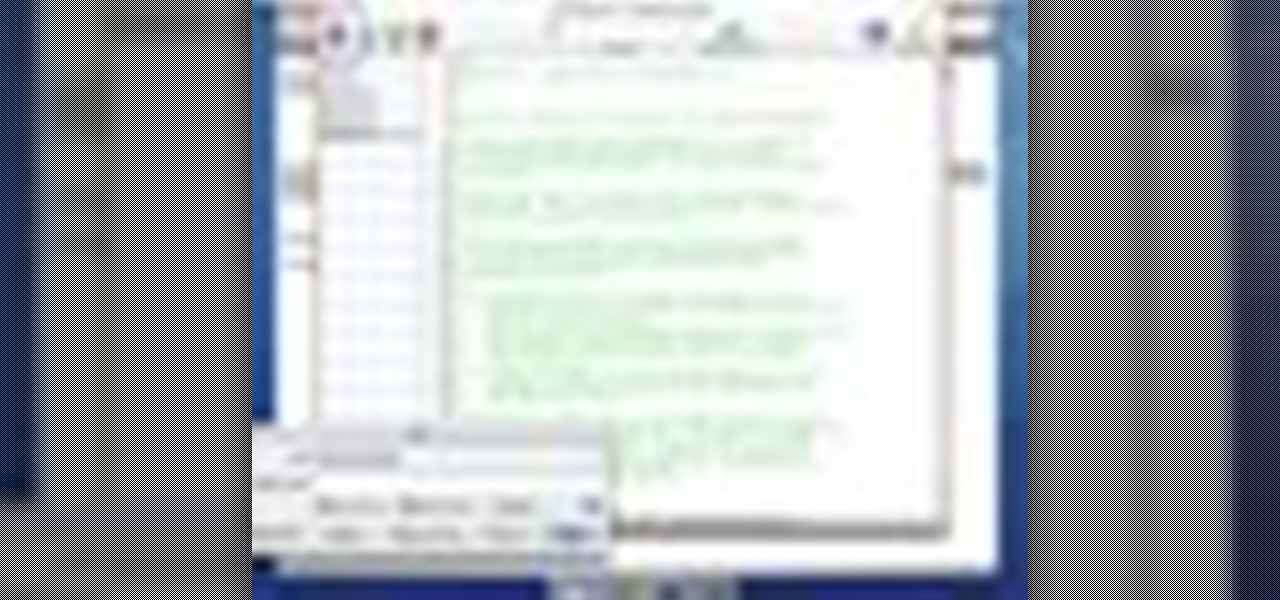
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
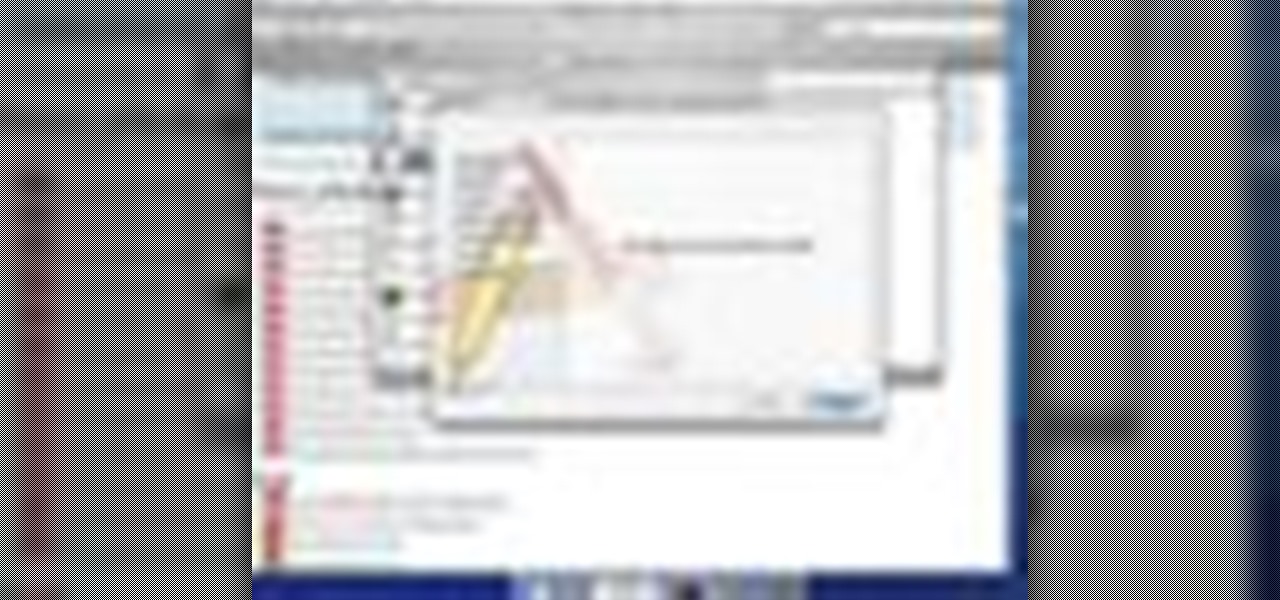
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
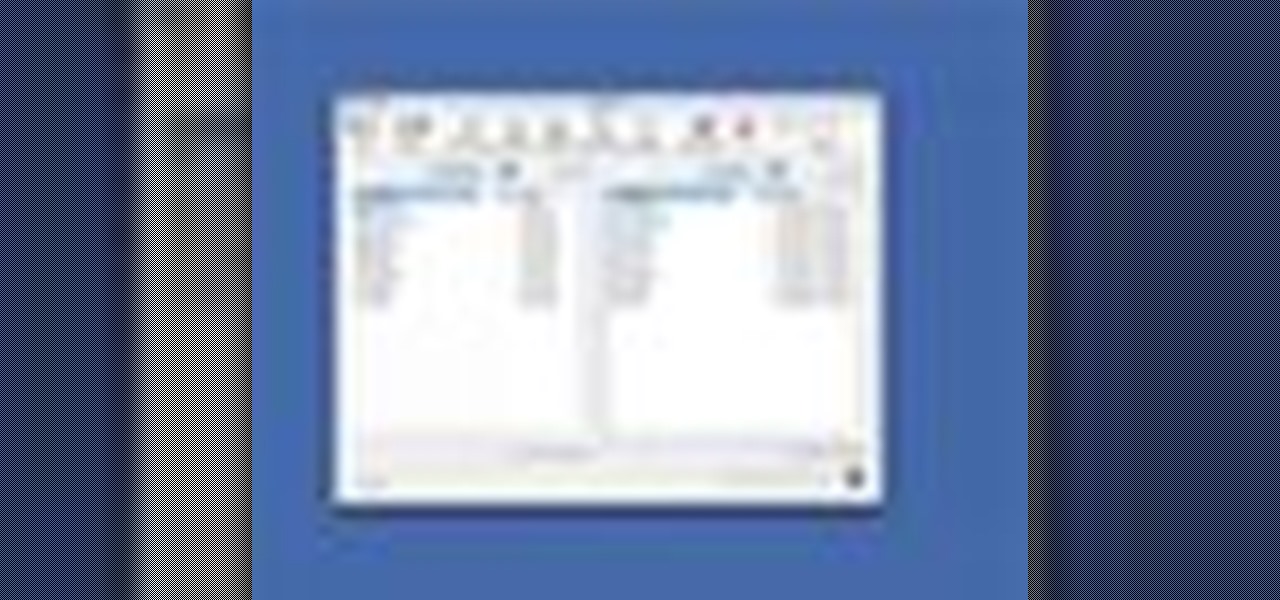
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
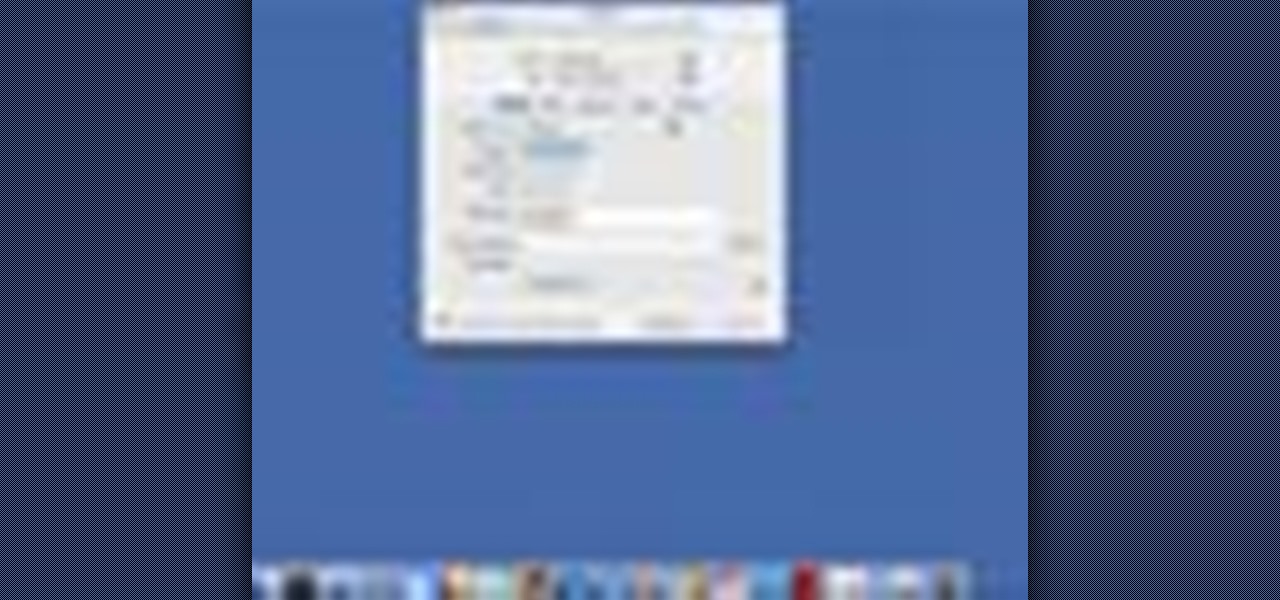
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.

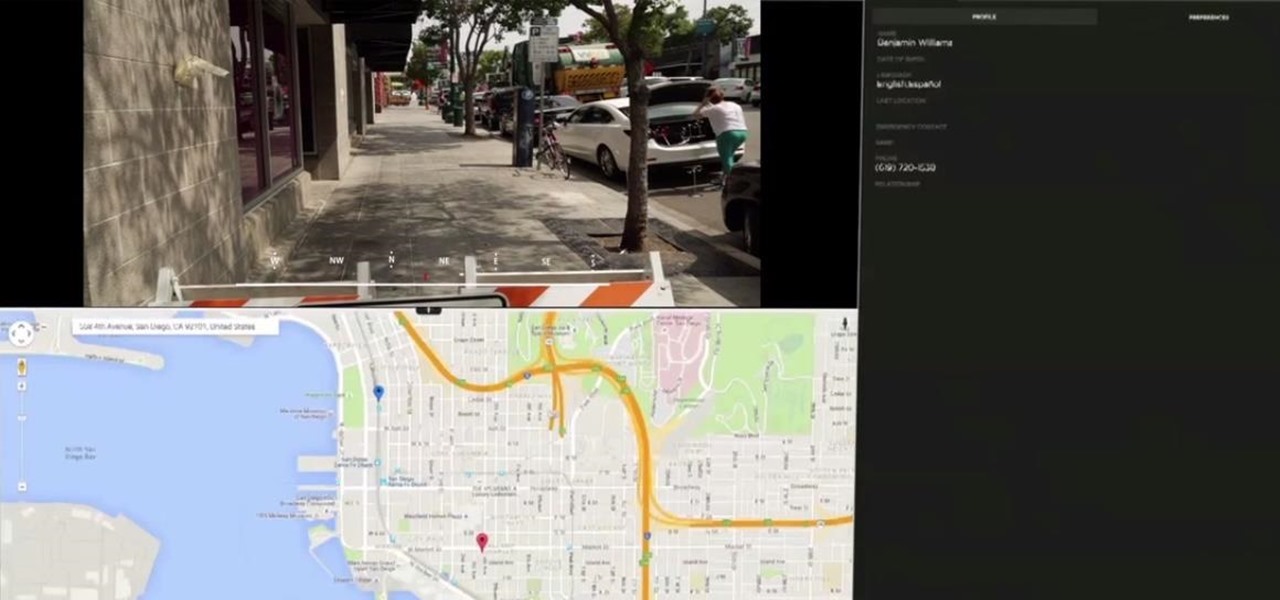
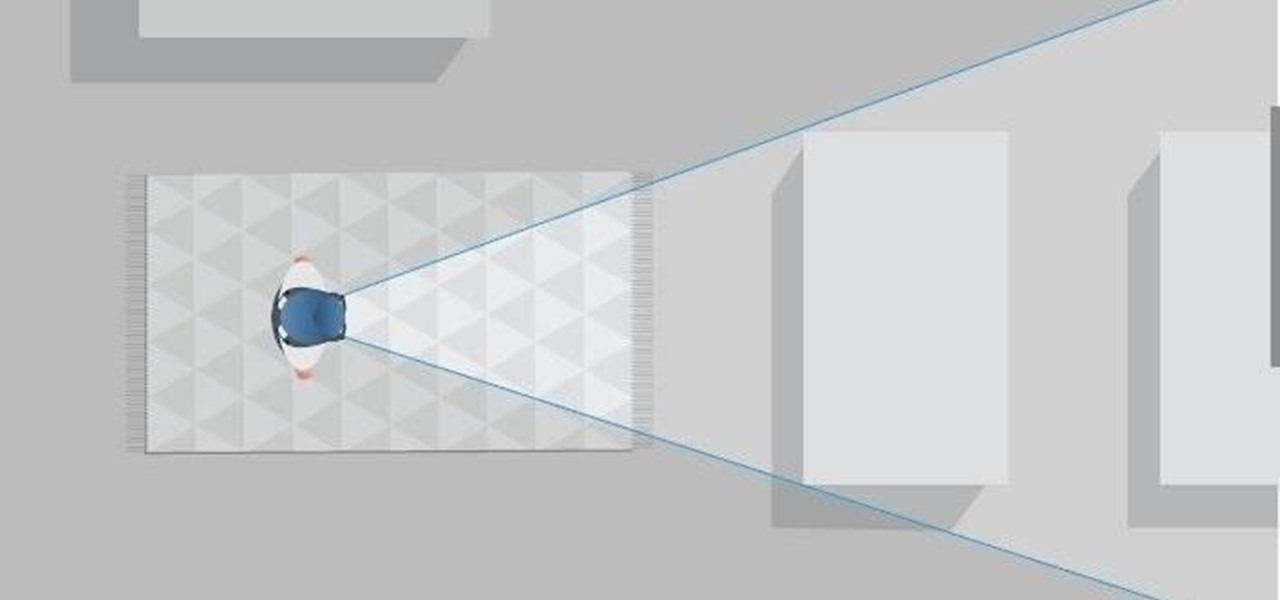
Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.
The arrival of Magic Leap One is tantalizingly close and, although the company has been saving the last details for launch day, a few of the more important details were found this week hiding deep in the code on Magic Leap's website.

Upon Google's release of ARCore in February, the platform wasn't only playing catch-up with Apple and ARKit in terms of downloads, but it also lagged in capabilities, as Apple already had vertical surface recognition and image recognition on the way with ARKit 1.5 for a March release.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.