Part of the fun of an online game is being able to chat with your friends! This tutorial goes over how you can use the in-game chat system to join a chat channel. It also gives you a few channels useful for everyone to join, especially new players. Or create your own channel. Avoid pirate corporations!
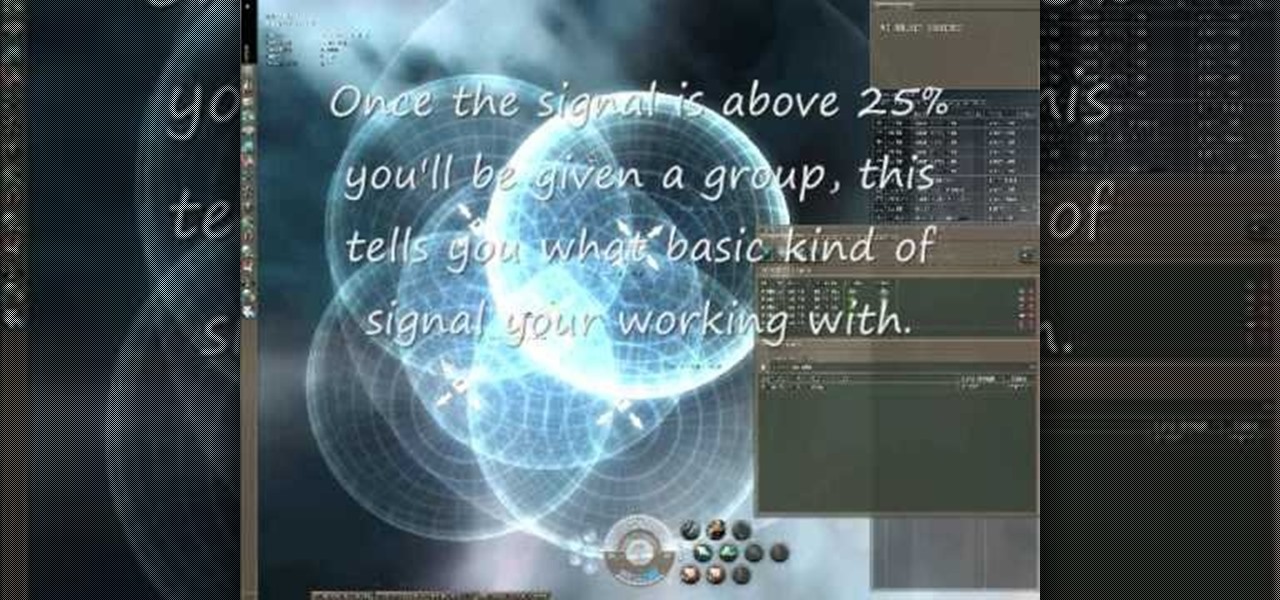
Know what's out there! You can send out probes to explore the area surrounding your ship. This tutorial shows you how to send out five probes and manipulate them in order to quickly and easily scan the local territory.
Quickly turn a profit during a combat mission by ratting - killing NPC enemies who spawn in asteroid belts. The difficulty of rats depends on how secure your system is - the lower security, the harder the rats are to kill. This tutorial shows you the best way, as a new player, to earn money by ratting.

This is a video from the Certified Horsemanship Association (CHA). See more at CHA-ahse.org and CHAInstructors.com. In this video, Brent Morgan, Christy Landwehr, and a horse named Phoenix show us the correct riding position. In the basic, safe riding position, what you're looking for is a line from the ear, through the shoulder, through the seam of the jeans, down through the heel. That is the correct riding position. As riders, we have a tendency to let our feet slide forward like we're put...
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional brushes for GIMP on Ubuntu Linux.

Teaching your dog to sit establishes trust and also creates a foundation for other tricks. Learn how to teach your dog to sit with this dog training video.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Part of what makes EVE Online so much fun is the option to explore different moons, planets and asteroid belts. However, it can be dangerous. This tutorial explains the equipment you'll want and the best way to explore in a non-combat situation.

Need to find a good agent for your character when playing EVE Online? Starting from docking your ship in the station, this tutorial shows you how to find the best agent possible to help out your character in the game.

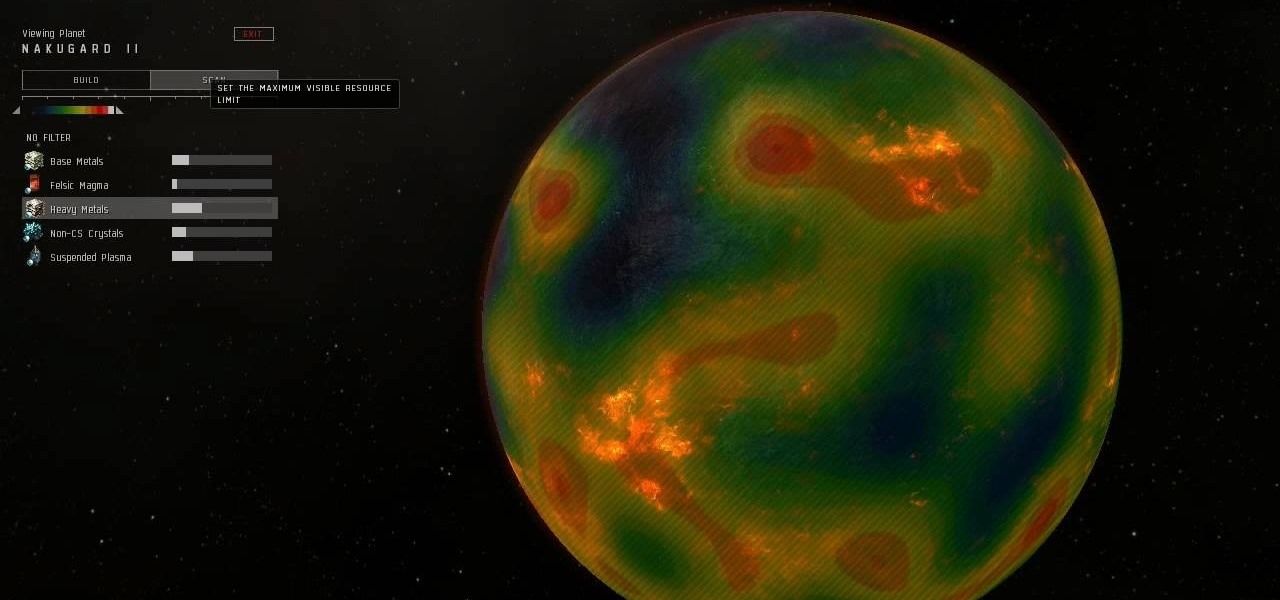
Planetary Interaction is a feature of the EVE Online expansion, Tyrannis. This video guide shows you how to use this new function. Choose your own planet, buy the command center and start exploiting its resources for your own gain!

How many stitches does your crochet art have? How can you tell? Why would you even want to know how many stitches are in your crocheted sweater or crocheted hat? Knowing how to count your stitches is a fundamental step in learning to crochet – assuming you want your finished product to be the right size and shape.

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

The iPhone is great for a lot of reasons, but one fault it may have is the keyboard and the ability to type. It's hard enough to actually type emails and notes on the small keyboard, but when auto-correction thinks it knows more about what you're writing than you do, it could become frustrating. So how do you stop Auto-Correct? Best Buy has answers. The Best Buy Mobile team explains how simple it is to turn off Auto-Correction on the Apple iPhone 3G.

Calculating probablities can be used to help us make decision. PatrickJMT explains how to calculate probability in an "either A or not A" scenario. The probability of A plus the probability of not A is equal to one. Therefore, the probability of A is equal to one minus the probability of not A ; P(A)= 1 - P(not A). The probability of a major earthquake in San Francisco over a period of time is used as an example. The probablity of an earthquake of a magnitude of 7.5 or greater in San Francisc...

Tinfoilchefdotcom shows us how to make green bean casserole, the easy way. You will need, 5 cans of green beans, one and half can of cream mushroom soup, quarter cup of milk and one and half can of French onions. Heat the oven to 350 and keep it ready. Take a clean dish and put green beans to it. This might look a bit too much, but it cooks down. Next, take cream mushroom soup in a dish and add quarter cup of milk to it. Mix it well till it loosens. Add this soup to the green beans and mix it...

If you want to know how to do Michael Jackson's moonwalk, you should watch this. 1. Find a flat, smooth surface that won't provide an immense amount of friction and wear any comfortable clothes and trainers. 2. Stand with both feet flat on the ground. Lift your left leg into "L" position so that the toe of your right leg is pointed to the floor. 3. Learn how to balance your self. With your weight on your bent leg, slide back your left foot. Be sure to keep your left foot flat on the floor as ...

If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

Look at the money you are receiving. Carefully inspect it for any strange colors, marks, or texture. Do not assume that a different color, texture, or design is simply a mistake made at the treasury. The bills there are all made the same based on the denomination.

This is a two-part video tutorial on cold smoking country style pork sausage. IN part one, the recipe for this sausage is provided. Most of this video's concentration lies on ways the residential sausage maker can reduce his or her hazard exposure. From the video maker: "It is not meant to be taken as more than an introduction to the concepts of where some pathogens may come from and how they might be limited." Part two investigates these hazards, but is deemed: "not a substitution for a HACC...

Elegant fashion is easier to come by than many assume. This tutorial shows you how to sew your own simple V-neck women's tunic with added flutter sleeves. You don't even need a pattern, just a few torso measurements for your wearer!

As with any investment, putting your money in foreign markets requires due diligence and the willingness to take risks.

Whether you're on a job interview or a first date, follow these simple steps to give the impression that you're quite intelligent – even if you're quite average.

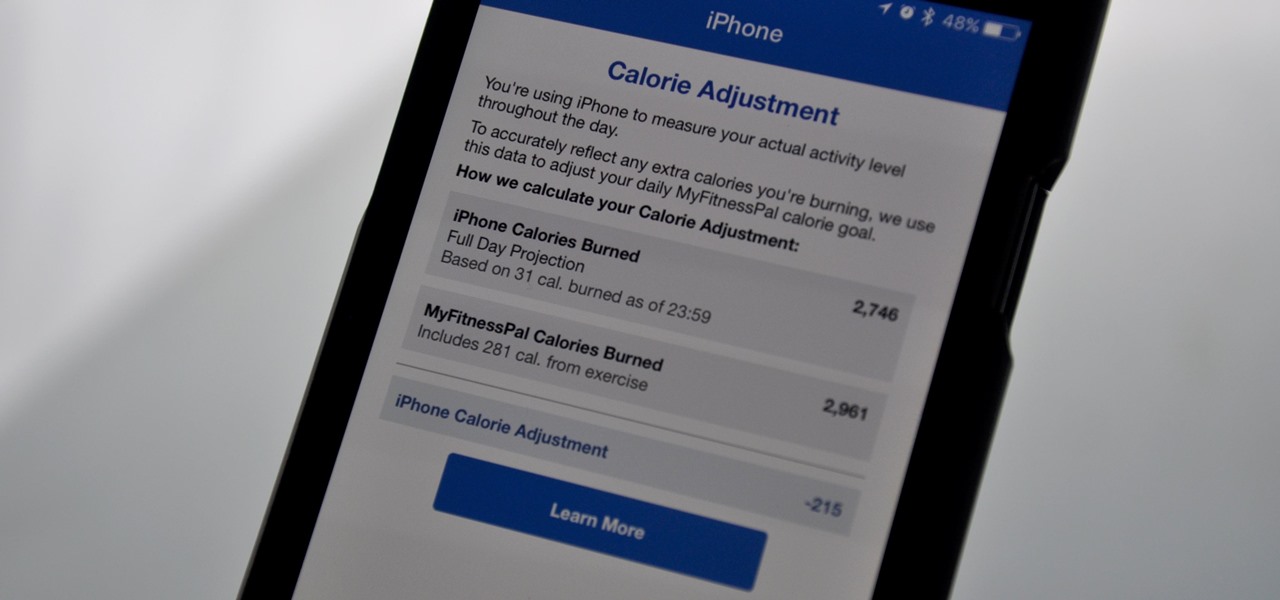
MyFitnessPal adjusts your calorie goal for the day according to your activity level. The more active you tell the app you are, the more calories it tells you to consume — simple, right? Unfortunately, MFP doesn't tell you to consume fewer calories when you don't work out. However, an activity tracker like a FitBit or Apple Watch can help.

Don't let the lack of owning a HoloLens stop you from joining in on the fun of creating software in this exciting new space. The HoloLens Emulator offers a solution for everyone that wants to explore Windows Holographic development.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Lemons are often displayed as a bright and beautiful pop of color in many home kitchen displays. They lend a lovely scent to the air and an aesthetic sense of freshness to any setting. Therefore, it would be easy to assume that lemons are best left at room temperature.

Think eating food is as easy as putting it in your mouth? It's considerably more complicated than that. Your brain plays a big role in determining what and how you eat. Understanding how your brain interprets food choices is key to managing your eating habits.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

We wear bras every day, and we all assume that we are wearing them properly, but how do we know? In this tutorial, learn exactly how to put on and wear a bra so that it looks great and feels comfortable. With a few simple steps, you will be on your way to being an expert.

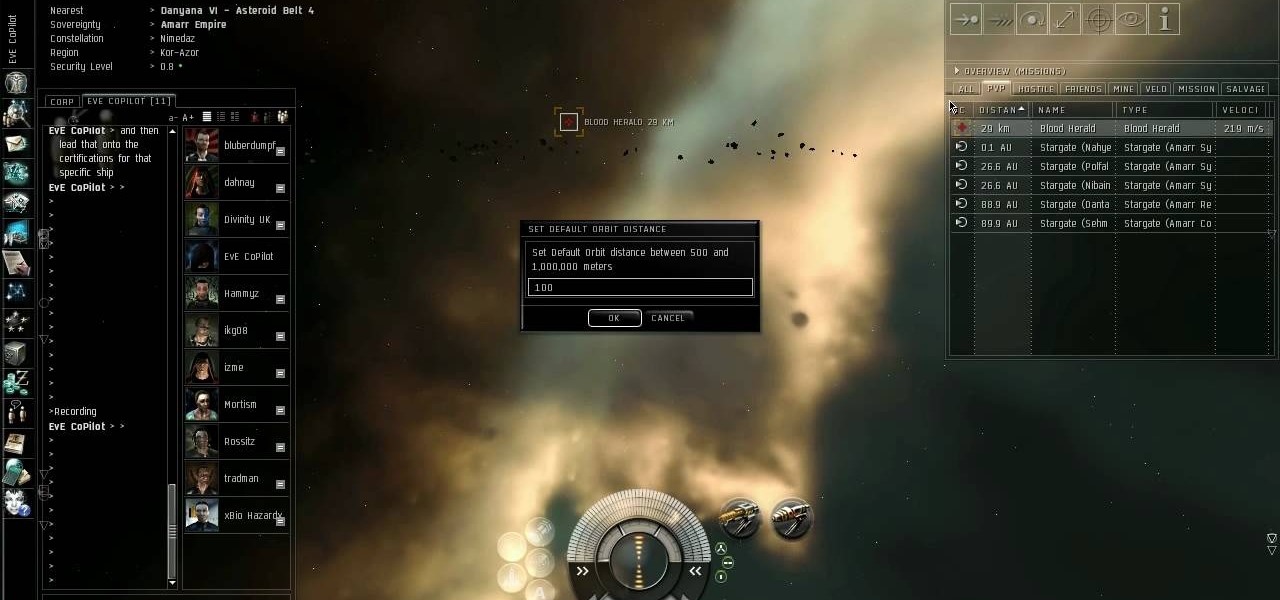
Weapon grouping has become available in the Quantum Rise expansion for EVE Online. This allows you to load ammunition for up to three separate weapons at a time - useful in a dogfight! This tutorial shows you how to group your weapons to take advantage of this new feature.

Hack Mafia Wars. Mafia Wars hacks, glitches, cheats. Mafia Wars is a popular facebook app / game. Watch this video tutorial to learn how to mass add hundreds of Mafia Wars family.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw an architectural cliff house.

Playing popular songs on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "Stairway to Heaven" by Led Zeppelin on the electric guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. This lesson covers the finger picking as well as the chord structure for "Stairway to Heaven." Watch this how to video and you will be able to sing and play "Stairway to Heaven" by Led Zeppelin.

When you set an alarm on your iPhone, you assume it'll go off at the set time. However, that's not always the case. There's one quirk in how iOS handles alarms that, if gone unchecked, will silence every alarm you set so that you won't wake up on time.

After jumping to the head of the class of augmented reality journalism in 2019, USA Today is continuing to push the medium forward in 2020.

It's always great to see a company pull off a bit of augmented reality magic, but what we see is not always what it's cracked up to be.