
AR Snapshots: Anime Makeovers, Mandalorian Helmets, Twerking Muppets & More on Snapchat
In the three years since Snapchat launched Lens Studio, developers and artists have created more than 1.5 million AR camera effects with the desktop tool.


In the three years since Snapchat launched Lens Studio, developers and artists have created more than 1.5 million AR camera effects with the desktop tool.

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

MicroPython is an exciting language to use on ESP8266 boards and ESP32-based microcontrollers, but it doesn't always include all of the libraries you'll need for a specific project. This issue is less of a problem, thanks to the upip package manager.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

We're still awaiting the arrival of consumer-grade AR smartglasses from the likes of Apple and Facebook. But that doesn't mean there aren't AR products out there to try this holiday season.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

I won't mince words: the Notes widget in iOS 14 is bad. But you're not stuck with it if you want sticky notes on your home screen.

When you're playing a game on your iPhone, the chances are good that you'll come across an ad you have to watch before you can continue — especially on free games. While it may be annoying to be forced to wait for 10 seconds or even up to a full minute, it can be even more frustrating when you accidentally leave the game to visit the ad's linked app or site when trying to hit the little "x" to continue gaming.
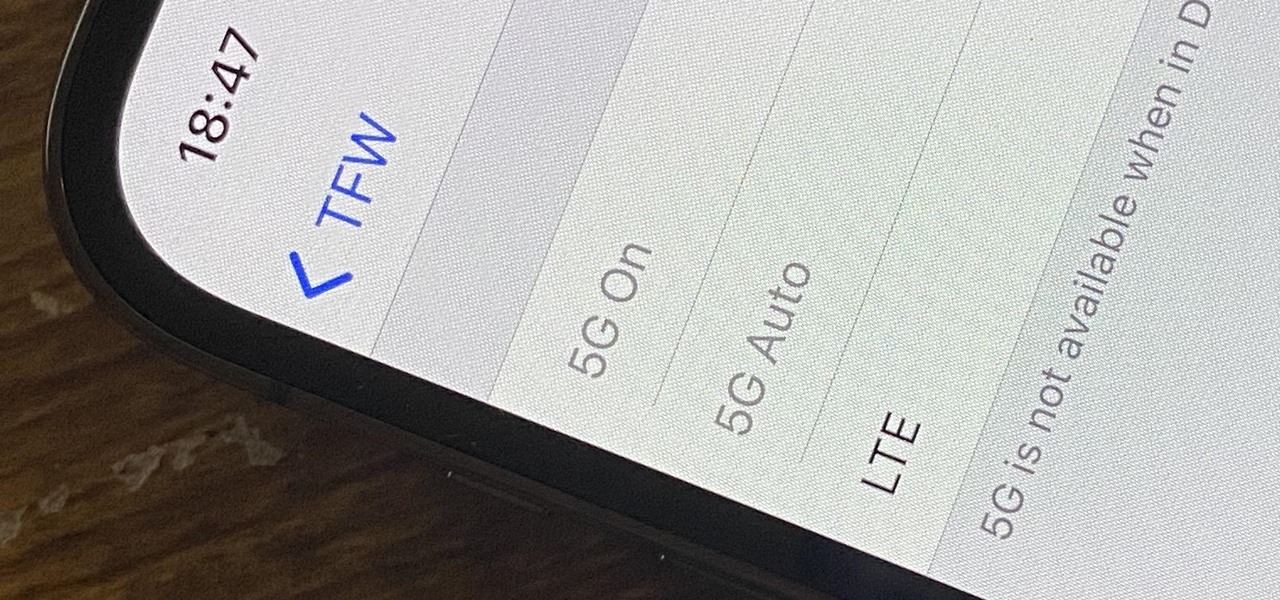
One thing you can expect from Apple is that big features work right out of the box. The company designs its products to be easy to use for any experience level, so you might expect the same to be true for 5G, one of the biggest selling points for the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max. Yet, you might have trouble getting 5G to work on your brand new iPhone. Here's how to avoid that.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.
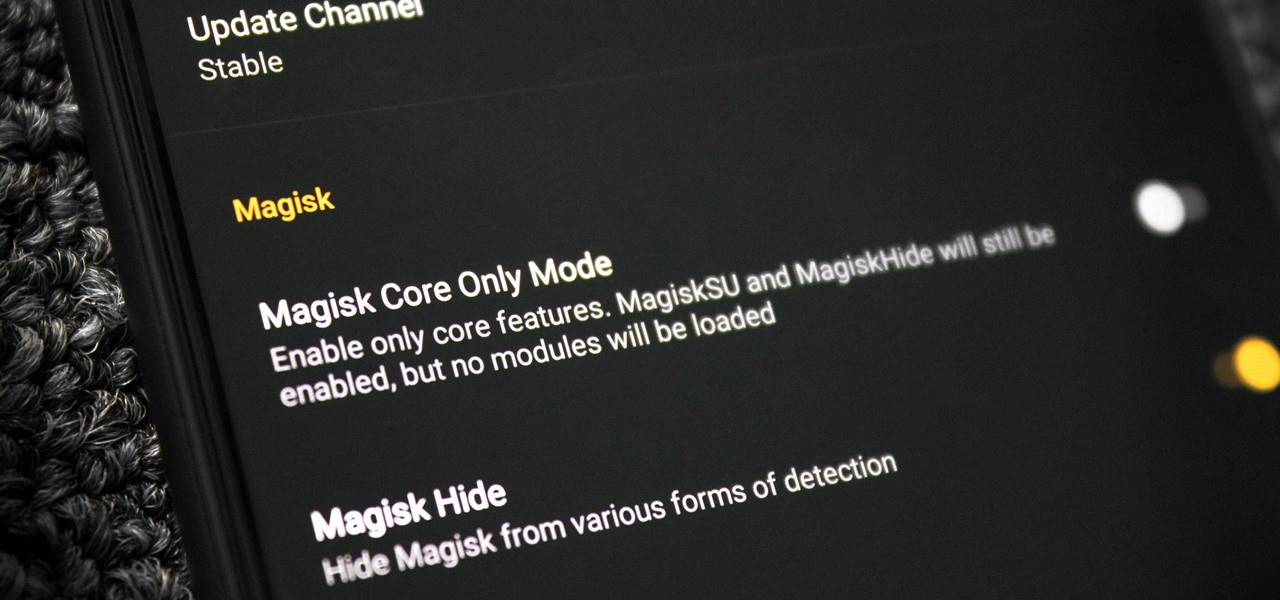
Bootloops are a risk inherent to rooted devices — with great power comes great destroyability, after all. While custom recovery sometimes provides a quick fix when you flash the wrong Magisk module, with TWRP becoming more challenging to implement thanks to Android 10, the solution is a bit more complicated nowadays.
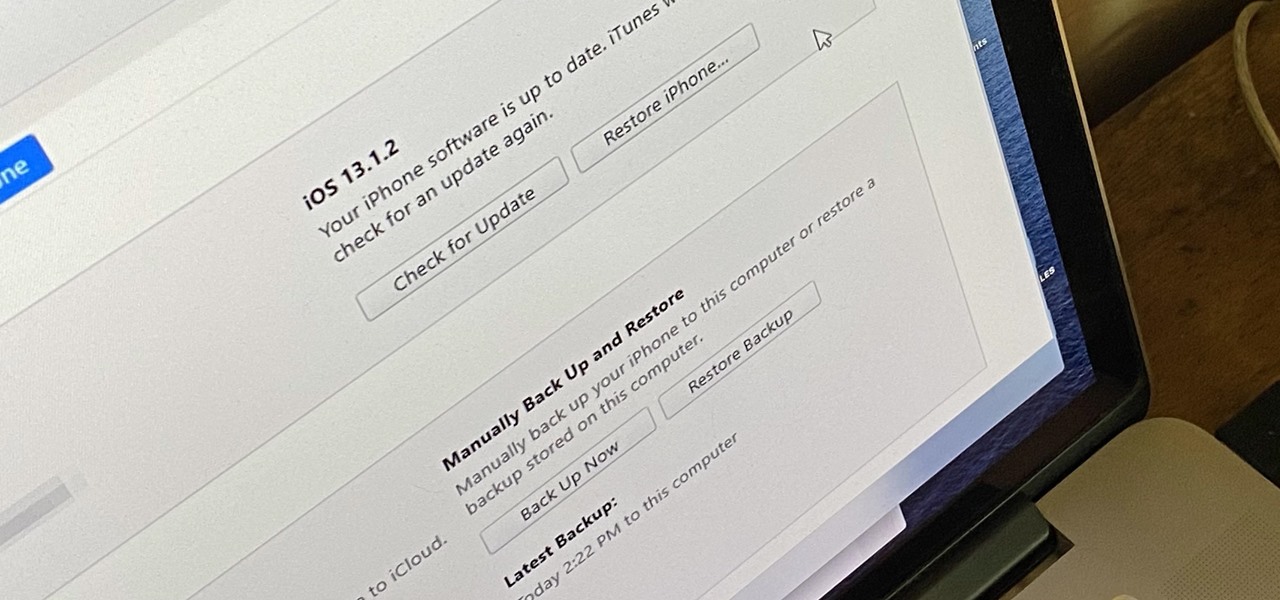
Whenever something goes wrong with your iPhone, or whenever you want to downgrade from an iOS beta back to the regular iOS release, you can restore your iPhone to your last saved state. Restoring to an iCloud backup is great but won't work in all situations. Plus, if you saved a backup on your computer, that may be the best route to take to get back all of your data.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

The Home button on an iPhone does a lot. That's not necessarily news for anyone who's ever owned an iPhone with a Home button, but what you might not know is that it's capable of so much beyond the standard everyday functions. So if you have an iPhone 7, 8, or the new SE model running iOS 13 or later, keep reading to learn about 17 secret Home button tricks you're missing out on.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.
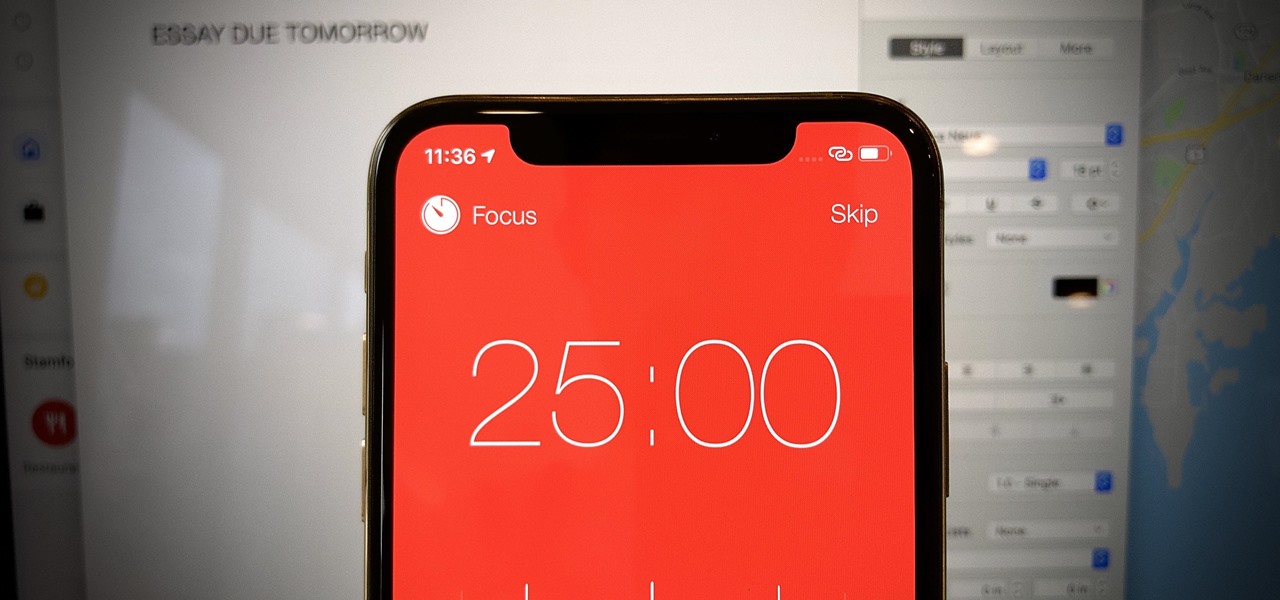
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.
Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.
The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.
We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Unlike VR, when you're talking about augmented reality, describing what an experience is like can be incredibly difficult — primarily because the experiences are even more contextual than relatively static virtual worlds that don't involve real-world settings.
Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.