
How to Java: E3 (If/Else Statements)
Hello Java-ers, In the previous two tutorials, we learned about installing the JDK, Installing/CreatingAProject in Eclipse IDE, and data types in Java.


Hello Java-ers, In the previous two tutorials, we learned about installing the JDK, Installing/CreatingAProject in Eclipse IDE, and data types in Java.
I assume you are on the same network with your router 1 - open a terminal window
Apple's latest update, iOS 7.1, has flooded to iPhones and iPads across the world. Despite the buzz across the web covering most of its newest features, we found one nice little enhancement that has been overlooked.

Stock prices be damned, HTC is ready to right the ship with it's soon-to-be-released follow up to the HTC One. The financially challenged device maker, according to inside sources, plans a March release for it's newest flagship.
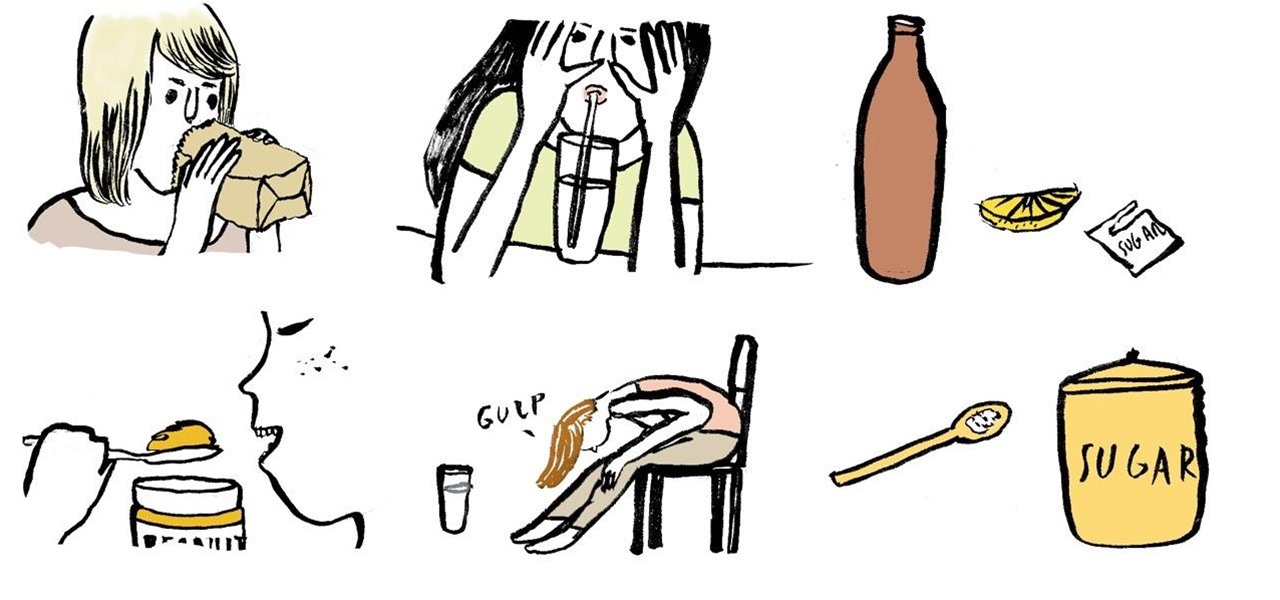
Most bouts of hiccups tend to go away on their own, but every so often there's that stubborn hiccuping fit that seems to last for hours. In these cases, you have to get creative and nip them in the bud by trying a few simple home remedies.

If you want to keep your inner snack monster under control, sniff an apple. Studies have shown that sniffing an apple or a banana helps curve your appetite. Craving something deliciously sweet? Take a whiff of something vanilla-scented, like a vanilla-scented candle.

Facebook recently revamped its Newsfeed in order to save us some time when scrolling around the website. But an even cooler, more underground time-saver are these super legit keyboard shortcuts. Facebook actions have been around forever, but I bet you never even knew about them. I sure didn't.

Uh oh. Somebody screwed up big this time. It has recently been reported that Iraqi insurgents have used $26 software to intercept live video feeds from U.S. drones located in Middle East conflict zones. The drone (a remotely piloted aircraft) is considered one of the U.S. military's most sophisticated weapons. Apparently not sophisticated enough, however.

So, I suppose we're going both redneck and Thanksgiving turkey twice today (Redneck Slingshot Chick + Extreme Thanksgiving Recipes).

Really? A string? In half? Yes. This is not a hoax. Just old fashioned science.

We assumed the novelty of the Apple iPhone would have worn off by now. We were wrong. It could get better than TapTapRevolution and Shazam.

Forget the Apple iPad. Forget the Samsung Galaxy Tab. If it's a tablet computer you're looking for, then the Notion Ink Adam is what you want. Hell, you can forget the Amazon Kindle, too, because reading eBooks in the sun-drenched outdoors is easy on the Notion Ink Adam. At least, that's what was unveiled by Engadget today at the CES 2011.

Here's a quick, simple prank to pull on anyone in under 2 minutes. It works especially great for someone who has tons of icons on their desktop! It makes the computer look the same, but nothing on the desktop works!

Every kid has had a lemonade stand. It's a child's first glimpse at responsibility and making a living, but the lemonade in this video isn't your typical lemonade stand variety. This is more like a slushy than a drink. This is a great summertime treat your guests will love, but remind them to drink it slowly to avoid that inevitable “cold headache.” John Verlinden of Mucho Gusto shares a favorite pitcher-style drink with plenty to go around. Fresh-squeezed lemon juice is the star with just a ...

Take out your wand and get ready to give it a whirl…'cause conjurer Ryan Oakes is going to show you how to make an awesome magic paper tree! All you need is a newspaper, scotch tape and scissors! Sometimes we use materials that require adult supervision... like scissors so make sure you have friends and family around whenever you do magic tricks.

Today isn't actually Pi Day, but I was unable to get this article out in time. Pi Day was actually yesterday, March 14th (3.14), so let's call this a post-Pi Day treat!
Our class had been assigned interviews with political representatives from different branches. In these interviews we asked questions that we had generated about their career position, advice to young activists, our government system, getting involved, and their opinion on certain laws. Here are the results from the two interviews that were done.
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Let's face it, the world we live in is far from the fairy-tale land we want it to be, where violence doesn't exist and weapons are not needed. Our foremost goal in life out there in the scary world is simply to survive. And if we need a few tools to accomplish this, we should use them, right?
1.) If you do not know something, keep our mouth shut.* No-one, I repeat no-one, is interested in your uneducated guesses about why something is the way it is, or why someone did something a certain way. At best, you will trick them into temporarily thinking you know what you’re talking about. At worst, you will convince them that you are speaking the truth and they will perpetuate your bullsh*t to others. Do not contribute to making the world a more foolish place just because you had to say ...

Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things like fences and chains.

The purpose of this article is to discuss how you can change your Windows 7 logon screen. This post will explain how to require a user to enter a username and password by default like the classic version of Windows.

In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user).

Minecraft might still be in development, but that doesn't mean a creative guy like Notch doesn't have time for other projects. A few months ago he and his company Mojang announced their second game, a digital collectible trading card affair called Scrolls. A simple title (perhaps too generic if anything), but it's not the name of an extant game, and it's appropriate given the visual style and card-based gameplay of the game itself.

I am the sort of man whom game companies fall all over themselves to seduce. I'm sweaty, pale, awkward, and spend too much money on video games. There are many of us, especially among XBox 360 owners. We are the most stereotypically "gamer" group of console owners. The XBox 360 doesn't have motion control like the Wii or a blu-ray player like the Playstation 3. It just plays games really well. That's why hardcore gamers like me prefer it amongst all the consoles, and probably why Silver Dolla...

So I totally blanked on taking pictures of my last project so I could share it, mea culpa. Instead, I figured I'd write a post on all the different ways you can sew a pouch.

Last week I did some beach camping at the San Onofre State Beach "Trails" and my experience was less than satisfactory. I'm hoping that by reading what happened through my trip, you'll be able to plan for a better trip.

If you look up the word SAWBUCK in the SCRABBLE Dictionary, you'd see that it was a sawhorse, but there's another definition that we're all probably more familiar with:

Nana korobi ya oki (resilience, unflagging effort) is the core belief of Seido Karate. It assumes that life is challenging and that we sometimes fall, unable to meet the challenge. Still we get up, undaunted, embracing our own spirit, our own capacity to prevail. The alternative, to stagnate or dwindle in spirit and action, is simply unacceptable.

These are great times. It is about time advertisers invaded our video games in the same way they do our driving (billboards), walking (fliyers, posters), and our private home (emails, bulk mail, text messages).

Almost everyone uploads their very personal photos in facebook trusting facebook's privacy settings. But question is - is facebook's privacy settings really that trustworthy? Few months ago, while browsing facebook, I found that one can easily access your private photos using the same browser you used to browse facebook.

In order to take the perfect picture of your handmade wooden project, it's helpful to have a lightbox that's similar to what professionals use but definitely cheaper to make yourself.

It's every home cook's nightmare...burnt on the bottom, mushy on the top! RICE, the simplest of foods, but not so simple to cook...or is it? I'm from South Louisiana (think New Orleans then go further south) where rice is served with everything and cooking it is second nature. You can be sure we keep it simple, I gar-on-tee!

How to Create Scenery in FSX

Playing your favorite songs by Twisted Sister on the guitar is not as difficult as it seems. With this tutorial you can learn how to play "I Wanna Rock" by Twisted Sister on the acoustic guitar. This lesson is geared towards intermediate guitarists because it assumes prior knowledge of guitar playing. Marty Schwartz covers the strumming pattern as well as the chord structure for "I Wanna Rock." Watch this how to video and you will be able to sing and play "I Wanna Rock" by Twisted Sister. Pla...

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

At some point, we all go from organized to disorganized. Let's assume you are a business executive working in a busy corporate building. Chances are you are going to get a heavy workload and it will impact how clean your workspace is. However, this article is about keeping your desktop clean and clutter free, along with the use of software to find documents you have misplaced.

Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a decent hacker can easily go undetected and even make it look like someone else did the hack job.

I'm pretty sure that it's a universal dream for everyone in the world to retire early. Who wants to to be stuck with the rest of the country and retire when you're almost 70 years old? You heard me right, 70! Most people can't go out and do the things they love to do by the time they're 70, unless they've been practicing good health and exercise their entire life.