If you want to learn how to play 'Blessed Assurance' on the lap guitar you should first print out the tab to Blessed Assurance so you can follow along. On the first note you want to roll on the first three strings of the 6th fret and then you want to roll on the first string of the 7th fret. Then play an open third string. This will all be open, a quick roll on the 6th, 2nd and 4th string. Now do an arpeggio on your 4, 3 and 1 string open. Now go to the 3rd, 4th string. Now go to the C chord ...

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade DS-2000 Series Telescope to ogle the universe.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade ETX-AT Series Telescope to ogle the universe.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

If there's one company that is a fan of the TrueDepth camera on Apple's iPhone X devices, it's the popular eyeglasses retailer Warby Parker.
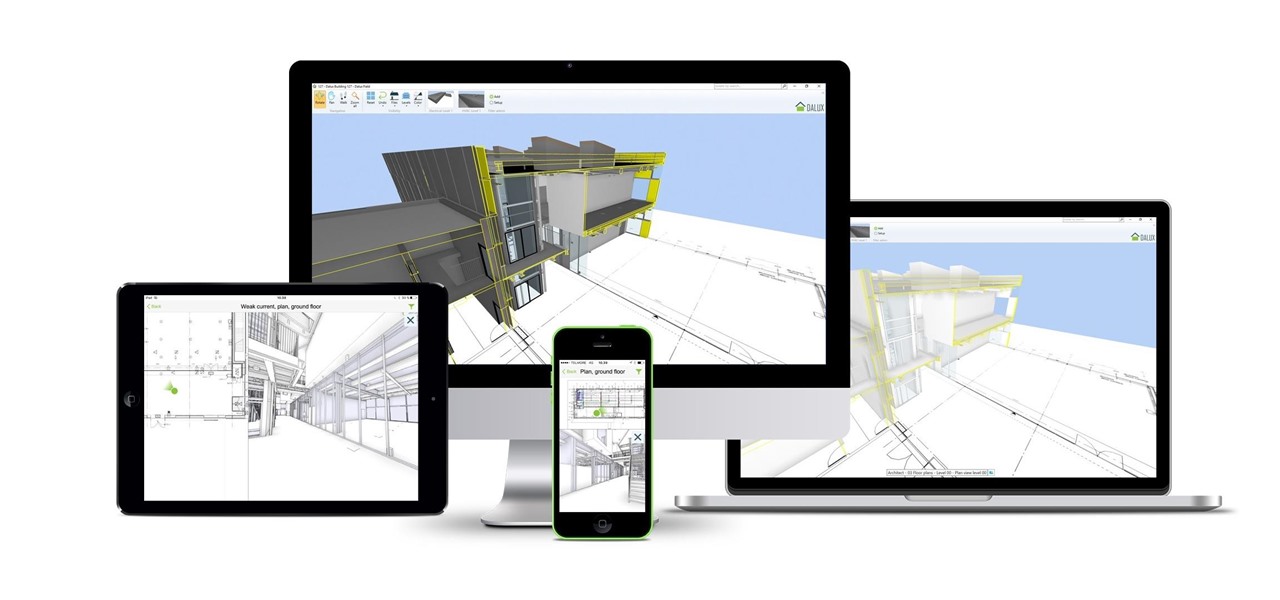
HoloLens developers have created some useful solutions for visualizing building models and viewing construction plans overlaid on the job environment.

With a fresh infusion of $9.7 Million in funding on its ledger, enterprise augmented reality company Scope AR has now expanded the functionality of its WorkLink platform.

The skinned versions of Android that come with Samsung, LG, and HTC phones usually have a feature that displays a small icon in your status bar when you connect a pair of headphones. It lets you know that your earbuds are plugged in or connected properly, and offers assurance that your music won't be blaring out of the loudspeaker—but mostly, it's just a nice little touch.

No one is perfect, and this goes double for software developers. All of the quality assurance testing in the world does nothing when you put a new OS in the hands of everyday users, since we all use our devices in different places and for different reasons. Recently, Cyanogen released their version of Android Lollipop, Cyanogen OS 12, and with it came a whole lot of great features, but some bugs also slipped in.

Silencing my phone always gives me mild anxiety; while my Android is muted, my girlfriend or boss may be trying to reach me with some urgent news or task. On the one hand, I want to enjoy some peace and quiet, but on the other, I don't want to come back to a phone with 100 missed calls and countless exclamatory texts.

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

You may think your iPhone has all the features you could ever need or want, but that may change once you discover the features and services you're missing out on by residing in the United States.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

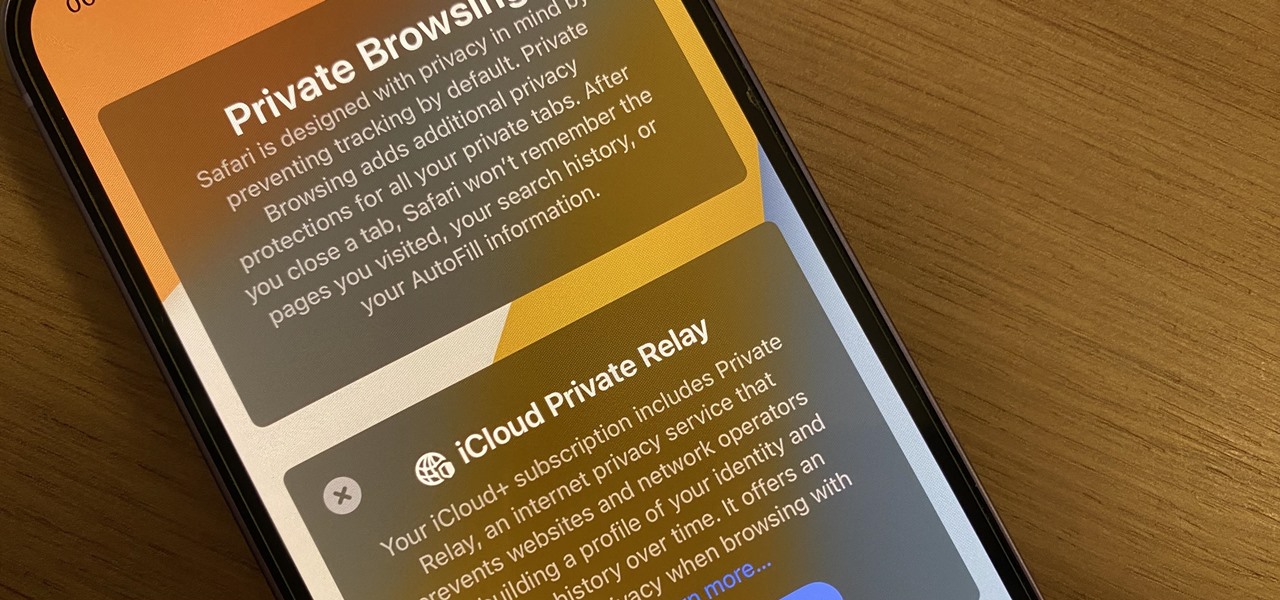
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.