Hak5 is at it again, with a plethora of somewhat accessible solutions to your technological problems. If you've ever needed to get through your school's firewall, or secure traffic tunneling, or try out applications in a fast, efficient manner? This video has it all and more.

Watch this video fashion design lesson to see who took second place in the Generation-t tee recon contest with how-to make a wrap shirt. All you need is two t-shirts and the steps, so follow along and get sewing.

Watch this fashion design lesson to see who took third place in the Generation-t tee recon contest with a how-to for making a no-sew fringe halter top!

This week Meg takes us back in time and shows us how to make an amazing Starburst mirror. Follow along with the home interior how-to video, and learn how to add a little vintage flair to your own home decor.

Grand Illusions is a site for the enquiring mind. This how to video demonstrates how to make Japanese origami tumblers. Your wonderful & charming host represents Grand Illusions, an amazing toy, magic & illusion web shop and gallery.

Tim and Kevin meet up/hang out & talk their talk. They discuss buying domain names, choosing business names, starting companies, and selling books by their color. These two entrepreneurs have lots to teach us about selling ideas and making profitable businesses.

This video explains how to fold the Spiral by Tomoko Fuse. You need 4 sheets of paper of different colors of any combination of your choice. 2 sheets of 2 colors each would give you a dual colored spiral.

This video will show you how to fake a RAM, Flash, or entire memory clear. Lots of teachers and test administrators go around and clear your calculator so students don't cheat. This is any easy way to subvert the teacher's security measure. This is a good thing to know if you want to cheat on your GED, SAT or ACT test / exam.

This homemade cake mix can turn your least kitchen-savvy friend into a star baker. And you’ve done 90 percent of the work, which is the greatest gift of all.

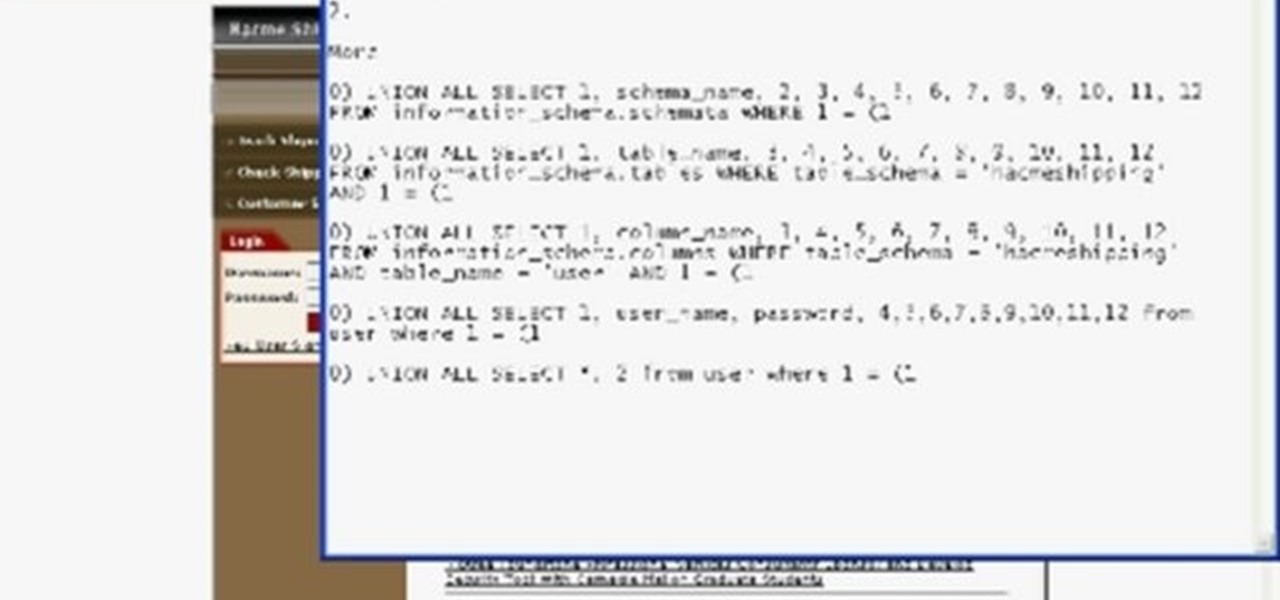
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Watch this video tutorial on how to perform a bone marrow aspiration biopsy on an animal, specifically a dog or cat.

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...

If you are using a 7mm prussik cord to build your anchor you must learn this knot. This knot can be used to beef the attachment point.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

We've been predicting the rush of augmented reality wearable makers from China for a couple of years, and now it looks like it's in full swing, with one of the most promising entrants coming from startup Pacific Future.

The Reminders app has always lacked the oomf that would make a person switch from a powerful third-party task manager. But Reminders has received quite the makeover in iOS 13, including a revamped UI and several new features, such as timed reminder alerts, which make the app a worthy to-do list option for the iPhone.

Adobe is best known for its photo and video editing software, but they also have a number of lesser-known apps that you may be interested in. Adobe Fill & Sign, available on iPhone and Android, is the best way to electronically fill out important documents on your smartphone with a third-party app.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

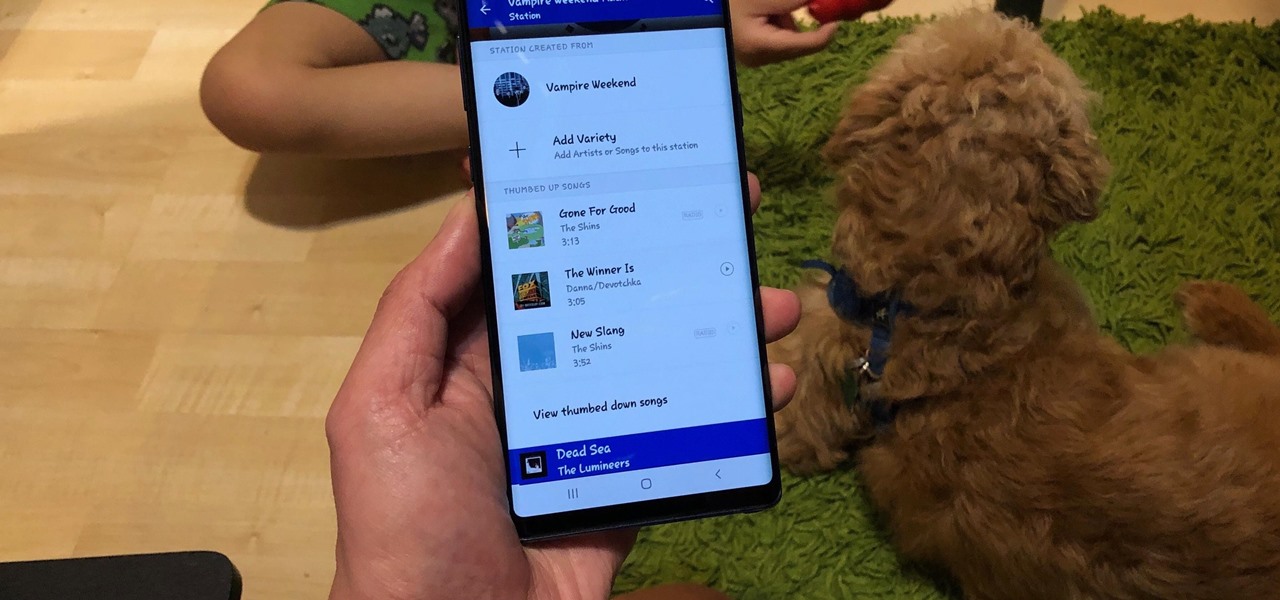
Pandora has a simple rating system that works by hitting either the thumbs-up or thumbs-down icon on a track that's playing on your station. If you choose the former, the song you like along with others similar to it will play with more frequency, while selecting the latter will prevent that song and others like it from playing in your station moving forward.

Popular chat apps like Messenger allow us to communicate with friends and family across iOS and Android phones alike. However, that interconnectivity doesn't mean both apps are the same. While Facebook has made strides to close gaps between these two platforms, chat heads remain an exclusive feature for Android devices, and they let you keep Messenger threads close by.

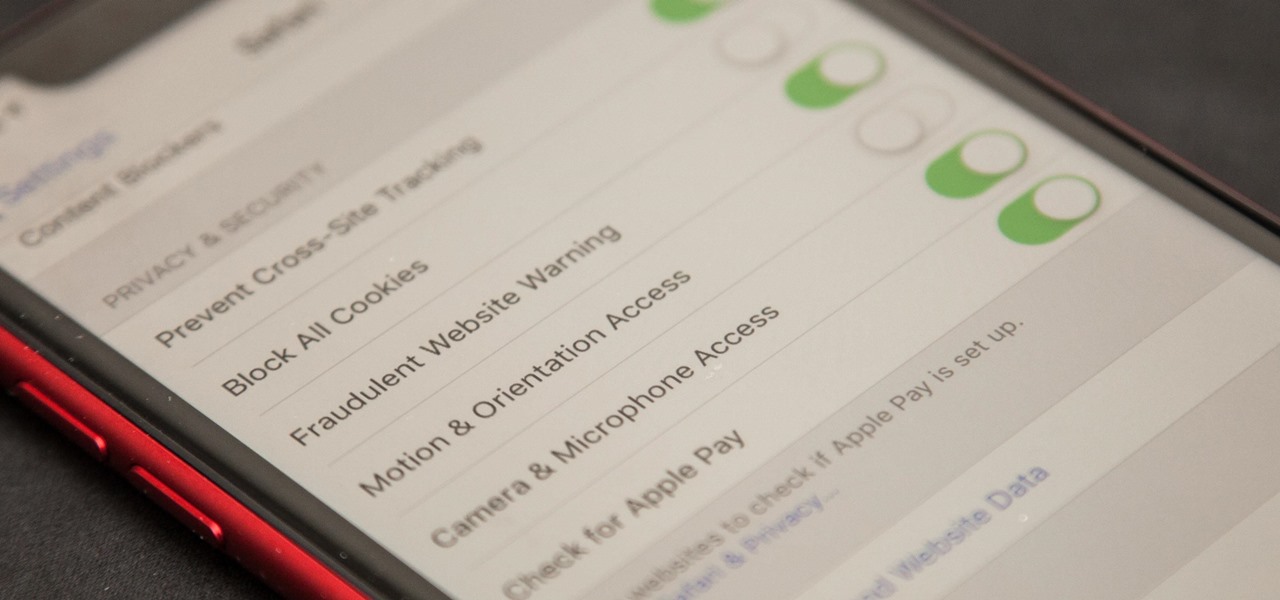
Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

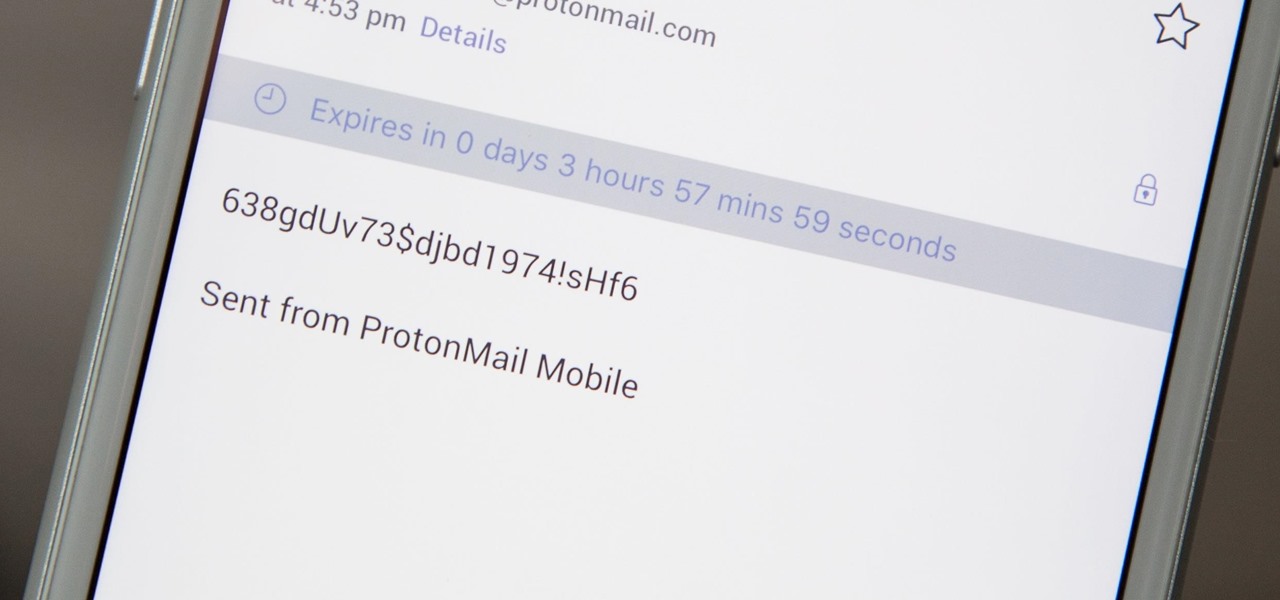
When you're sending sensitive information via email, it's best to do so with end-to-end encryption. Even better, set the email to destroy itself after a set amount of time for a little piece of mind.

A virus easily spread among trout and salmon could make it harder to keep your favorite fish on the menu.

Unless you're a WhatsApp pro user, you may be surprised to know that there are text formatting options that you can apply to your messages. Markdown characters can help you emphasize certain words or phrases by making them italicized or bold, and it'll even let you cross out words and change the font. It's one of those nice touches that isn't available in most other messaging apps.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

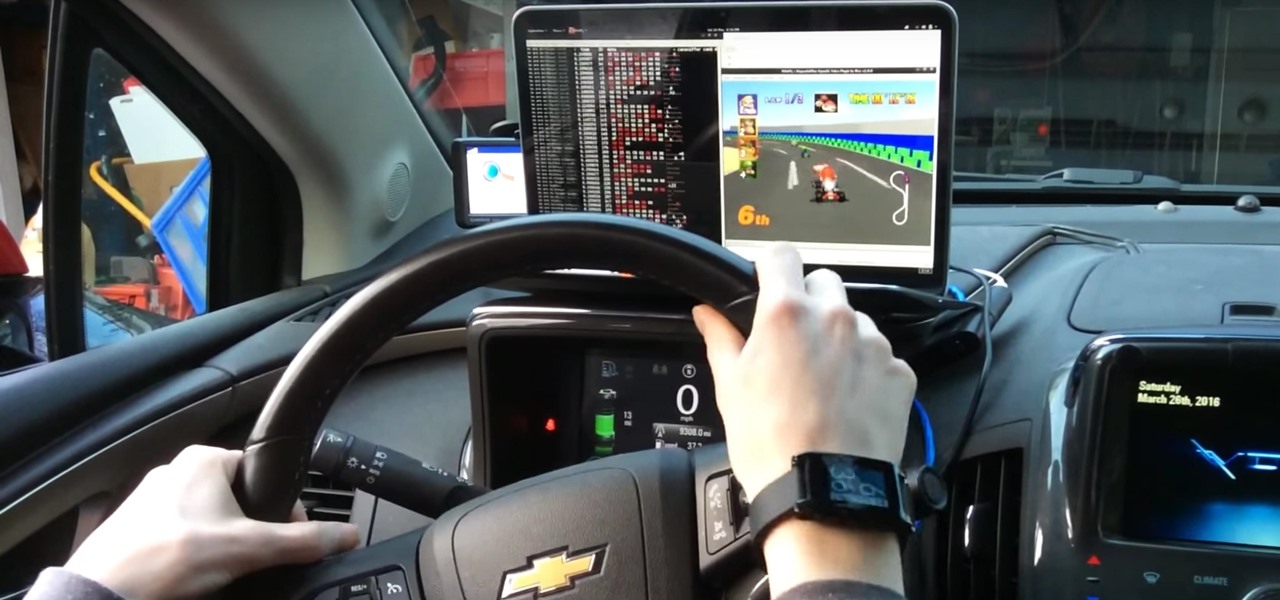
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

For photographers, the "plus" in the iPhone Plus models used to mean optical image stabilization, but now that the iPhone 7 and iPhone 7 Plus both have OIS on board, that "plus" has moved onto something else—the dual-lens camera. Actually, the new dual-lens setup on the iPhone 7 Plus is a much bigger deal than OIS ever was. While OIS stabilizes the image before it's converted to digital information from the sensor, creating a much cleaner photo, two lenses working together in unison unleashes...