Keep your Runescape account safe from hackers by following the instructions in this video. Don't get hacked by giving your password away or using unsafe websites. Watch this video and learn how to take precautions against hackers so you can enjoy Runescape worry free.

Are you interested in developing your artistic talents? Have you got great ideas for cartoons but not enough technical know-how to make them come to life? This video will show you to draw a cartoon cat that will jump right off the page.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Disabling your opponents legs is the fastest way to make sure that you can get away from a fight situation without killing your opponent. Attacking the pressure points associated with the large blood vessels and nerves in the legs is an effective way to do that. This two-part video features an extensive walkthrough of the legs pressure points and ideas for attacks that can be used against them to get your fight over with as quickly as possible without risking killing someone.

This video details how to survive a knife threat from behind. When threatened from behind with a knife, do not attempt to move the body first, this will result in the attacker maintaining the capability to thrust the knife into the body. When threatened, place arms out and low in a submissive position, this is to be followed by moving the left arm backward in a sweeping motion to push aside the arm which is holding the knife. Once the arm is moved, turn the body and bring the elbow up into an...

Sharks. The first thing that comes to mind is "Jaws", Steven Spielberg's horrifying shark film that scared generations of young adults from entering the ocean waters. But not all sharks are as violent (and hungry) as "Jaws", so jump in the water and know a few guidelines to stay safe. Escape a shark’s jaws of death with these lifesaving strategies.

Every foil fencer must learn attacks and attacking strategies to succeed at fencing for any level; learn advanced attack moves and strategy for foil fencing in this free fencing video lesson.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

ESP8266-based microcontrollers can be used to create exciting and legal Wi-Fi hacking games to test your or your friends' Wi-Fi hacking skills.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

For a field hockey offense to score, their attacking must be better than the defense's tackling. Speed and accuracy are essential for an effective field hockey attack. Learn how to attack in field hockey in this video tutorial.

Dumb Idiot Have the guys at the zoo. One fan (actor) comes up who is crazy and wants to be on the show. He jumps into the place where there are gorillas. But all the gorillas will secretly be fake because they are people in costumes.

The SAW lead is the most recognizable sound in hardstyle and hardcore electronic music, sounding like a swarm of bees attacking with the precision of an honor guard. Watch this video to learn how to program a patch for a SAW (or sawtooth) lead on a MicroKorg.

The Shiva sisters fight in Final Fantasy XIII is more to prove yourself to the sisters so you may summon them than to actually fight them. To win the battle, you must fill up the gestalt meter which appears over the sisters' heads. No one will die, one sister will actually heal you throughout the battle, but you do have a timer over your head which will give you a game over if it runs out. To begin, use Libra on the sisters to determine their weaknesses, which will make you realize that physi...

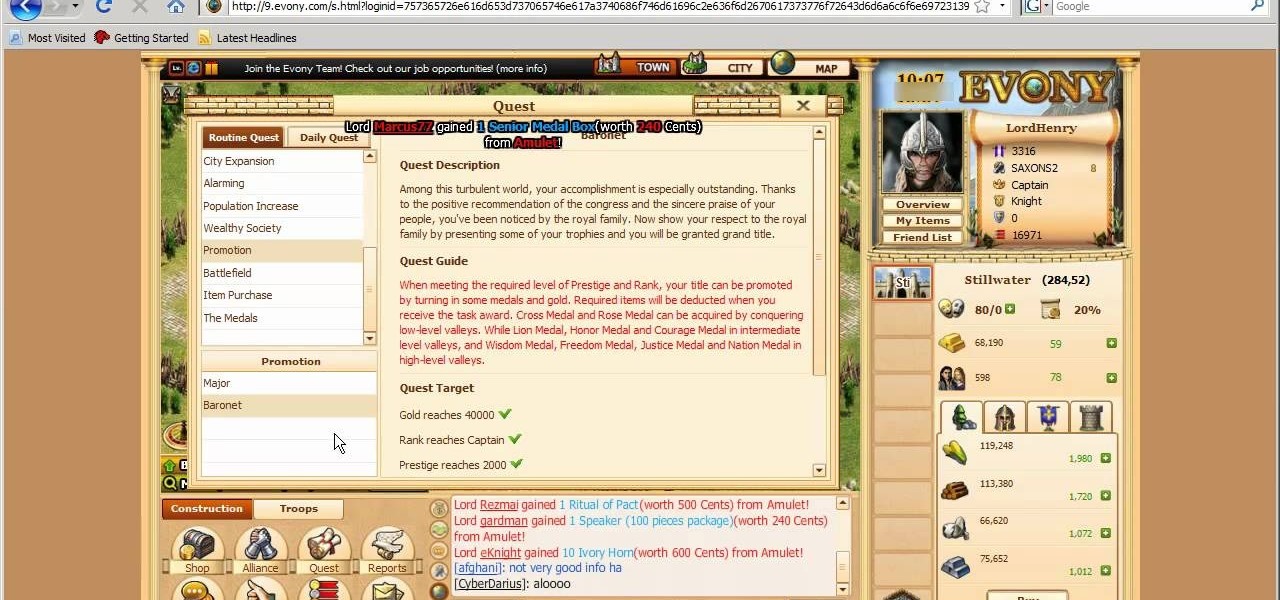
Learn everything you could possibly want to know about the internet, multiplayer game Evony with tutorials from EvonyTutorials. Watch this video tutorial to learn how to play Evony - promotions and medals. See exactly what the game Evony is!

Dragon Age 2 is the latest fantasy RPG from the folks at Bioware, and if you're watching this video you've probably either just gotten it or are thinking about it. Check out the vid for a walkthrough of the prologue quest, Destruction of Lothering.

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

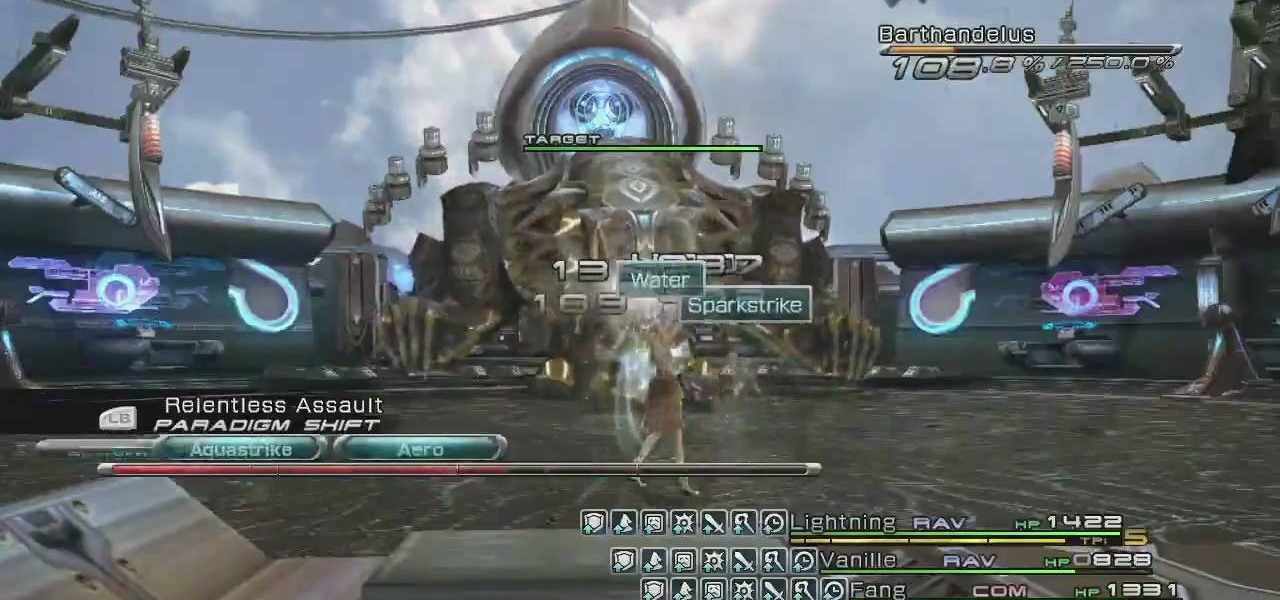
Make sure to buff up before fighting Barthandelus. Make sure you use the aegisol buff. Then use your Liba Scope ability in order to understand its weaknesses. Attack the smaller heads before attacking the main upside down head, because in the beginning it will be almost invincible. After attacking the sides of the boss, attack the main head. If your health drops to about half, switch over to medic class and heal. The boss has some strong attacks so make sure to be ready for them. If you buff ...

Are you using the Queen too much, or attacking with one piece at a time, or making mostly pawn moves, or that tricky Knight obsession, or "freeing" the Rook with a side pawn, or are you being a victim of a back row checkmate? Well, watch this video to to avoid these common chess mistakes.

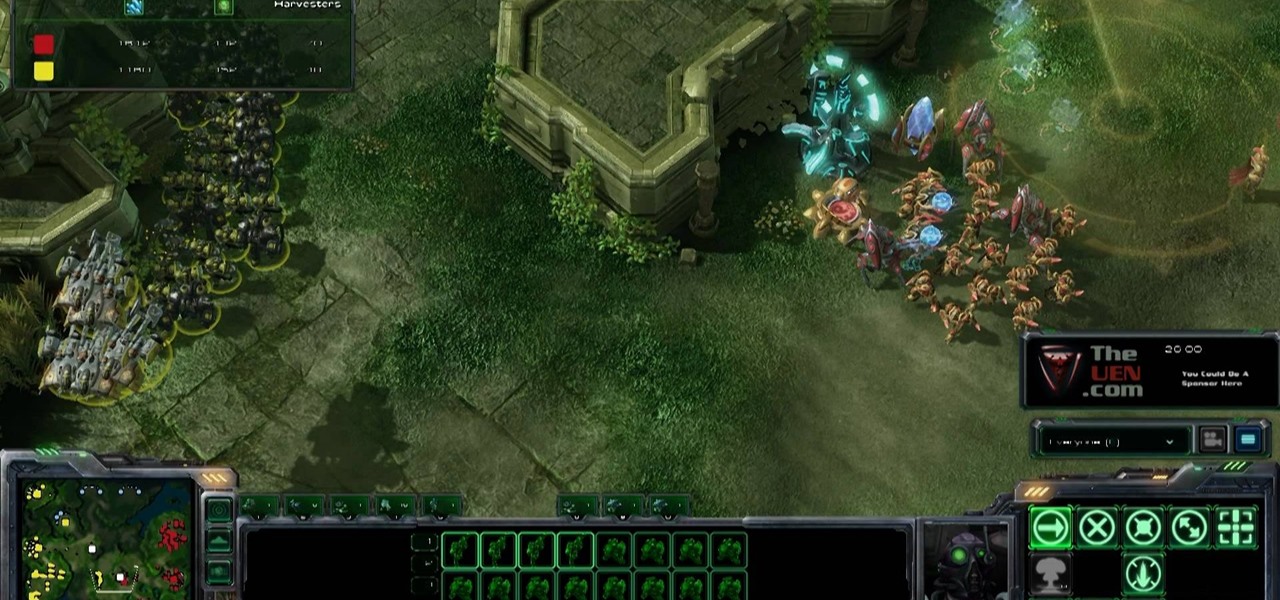
After 12 years Starcraft 2 is finally here to blow your mind. If you're looking for help with the game, you've come to the right place. We have tons of videos about how to do just about everything in the game. We have strategies for winning campaign and multiplayer games. We have guides to using the immensely powerful level editor. We'll even teach you how to build a Terran Barracks out of Legos. This video will show you how to use the Protoss High Templar's Psionic Storm ability most effecti...

In order to play the game Risk, begin by setting up. Name a banker. Players choose a color. The number of players determines the number of armies. Remove the jokers from the country card packs. Shuffle the cards. Deal them face down. Players may not get an equal number.

In this Sports video tutorial you will learn how to play midfield in soccer. Adrian Heath, Head Coach of Austin Aztex, explains the role of the midfield player in this video. Midfield player is the engine room of the team. He moves forward and feeds the ball to the strikers for attacking the opponent's goal and falls back in to his own half when defending. Two midfield players combine to pass the ball from the defending half to the attacking half past the opposing midfielders. There are many ...

Worried about the MAC Defender that's been going around? Don't let your Mac get infected, watch this informative video to learn how to keep it virus free. If you are concerned with malware attacking your OS X Mac, you should watch this video.

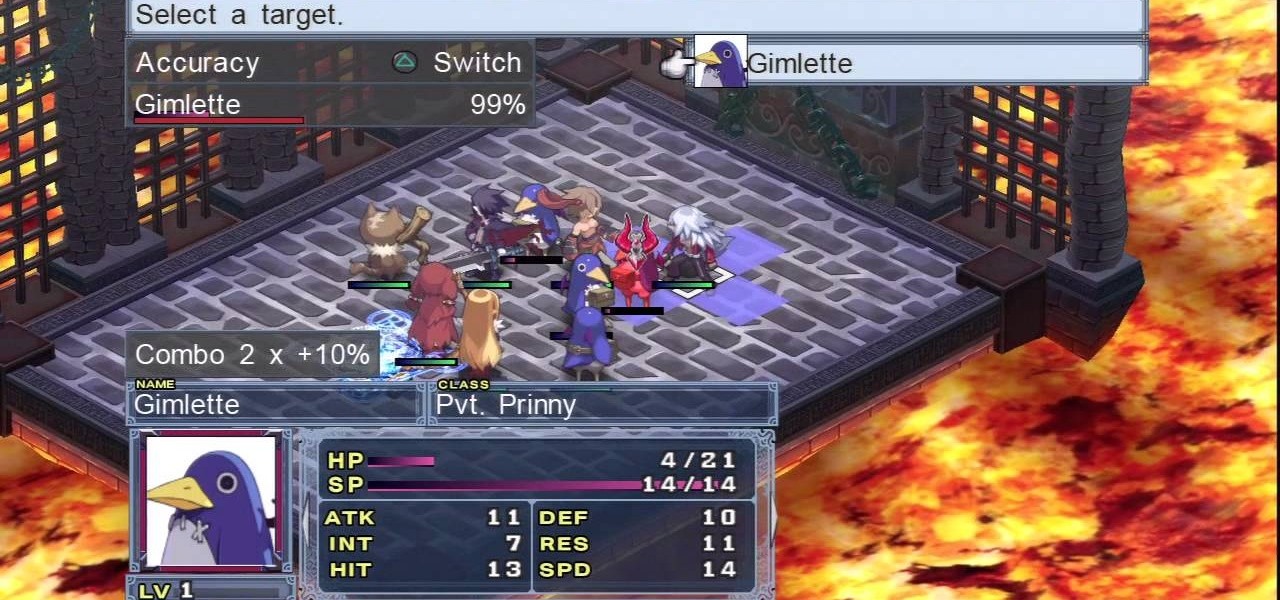
If you're trying to figure out how to play the Disgaea 4 combat modes effectively, take a look at this guide on positioning, attacking, defending, and more while fighting against opponents in the PS3 game. The combat can be a little confusing but there are many different options such as team attacks and combo attacks. This tutorial will give you some understanding of the early fights in the game.

In MMA nearly every part of the body is fair game for attacks and attacking, even the toes. In this video Joanne and Risha of MMA Girls will teach you how to use a toe hold to submission an opponent.

Fighting Straga is the main boss fight In the Xbox 360 game Darksiders - The Black Throne. Can you beat him? Quickly shoot a portal onto one of the floor stations in front of Straga. Watch his mace carefully and you'll see another orange portal point on the side of it. Shoot a second portal onto the mace then wait for Straga to raise the mace back behind his head. When he does this, drop through the portal you made on the ground so your pop out of the portal on his mace and land on the platfo...

Are you ready for the last boss fight in the Xbox 360 game Darksiders? Once you fight Abaddon in the Destroyer, you win, unless you lose. You'll now have to face Abaddon in his "normal" form. He is a powerful swordsman so you'll want to take the defensive route as he can block most of your basic attacks. Instead of attacking him, be patient and stand near him. You'll need to perform a Block Counter but simple tapping the Dash button (without hitting the directional stick) the moment before Ab...

If you can't beat Silitha in the Xbox 360 video game Darksiders, then perhaps you should check out this video on accomplishing just that. Silitha is a gigantic and ugly spider-like creature that dwarfs War. She can teleport around the arena and likes to appear directly above War and attempt to crush him beneath her. Silitha will appear around the edge of the room and taunt War. Get just about past the middle of the room towards her then use your Abyssal Chain to pull yourself directly at her ...

This video will teach you the basics of ping pong. Includes simple strokes and attacking and defending strategy.