Most of you are familiar with using Ettercap for attacking systems, but what about using it to find attackers? This tutorial will cover using Ettercap to find people sniffing on your network. The plug-ins we will be using are search_promisc, arp_cop and scan_poisoner. Have fun detecting network sniffers. Detect hackers on your network with Ettercap.

Buddy Mason demonstrates how to play the square cut for the game cricket. You should play this shot on a delivery that is short of length on or outside the off stump. If you get a ball outside your off-stump, you may be able play this attacking shot. Get it right, and a four is yours! Play the square cut.

Buddy Mason demonstrates how to play the sweep shot for the game cricket. The shot is ideal for playing spin bowling on the leg side in an attacking way. You must lean forward and extend your arms. Play the sweep shot.

Just like late-night bar hookups, a wingman in soccer is indispensible for scoring a win. Robert Pires, a midfielder who has won the FIFA World Cup and UEFA European Championship with France, demonstrates in this video how to be a good winger.

Buddy Mason demonstrates how to play the straight drive for the game cricket. You should play a straight drive to a full delivery on middle or off stump. You have to lean forward and keep the bat straight. The straight drive is one of the key attacking strokes in cricket, hitting the ball back down the wicket and hopefully to the boundary! Play the straight drive.

This is a guide on achieving the Insane Blitz Achievement in StarCraft II. This shows the achievement being awarded along with the Very Hard Blitz achievement.

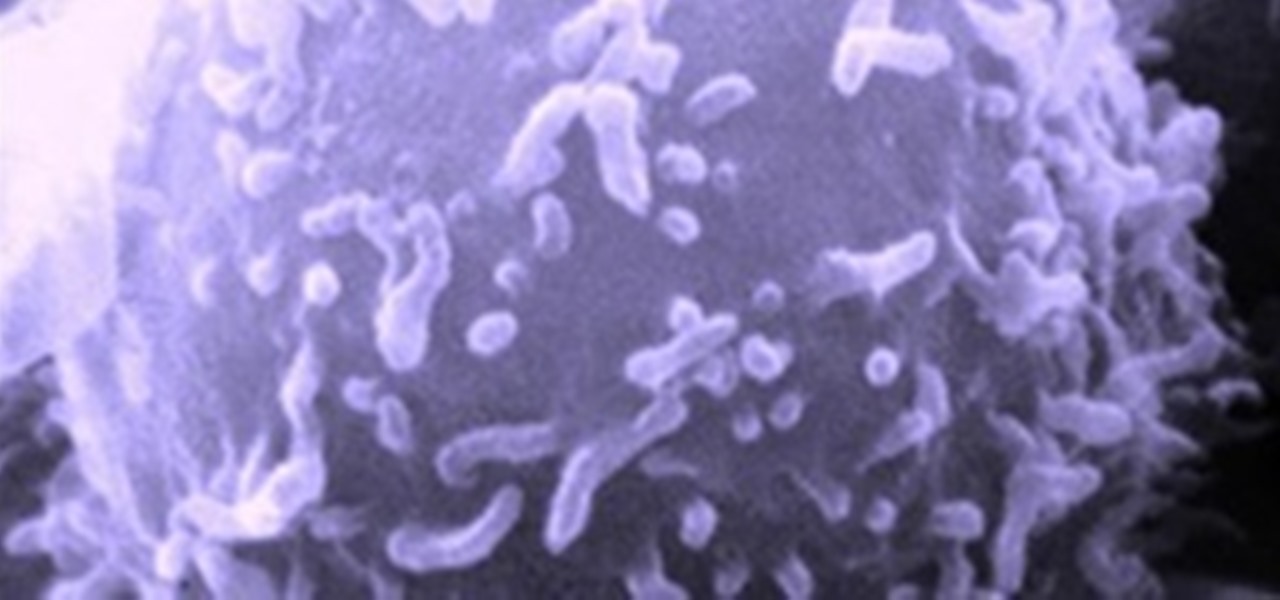
The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

My friend Javi (who will join this group eventually that lazy sack) is a masterful MTG player and deck-constructor. Hell, he's damn impressive nerd all around. One time he made a Black deck out of my cards, and it is pretty devestating despite the fact that I never really collected Black and thus don't have multiples of good cards for it. It has more creatures than most Black decks (again, my fault) but uses it's excessive Mana to deal absurd amounts of damage with them.

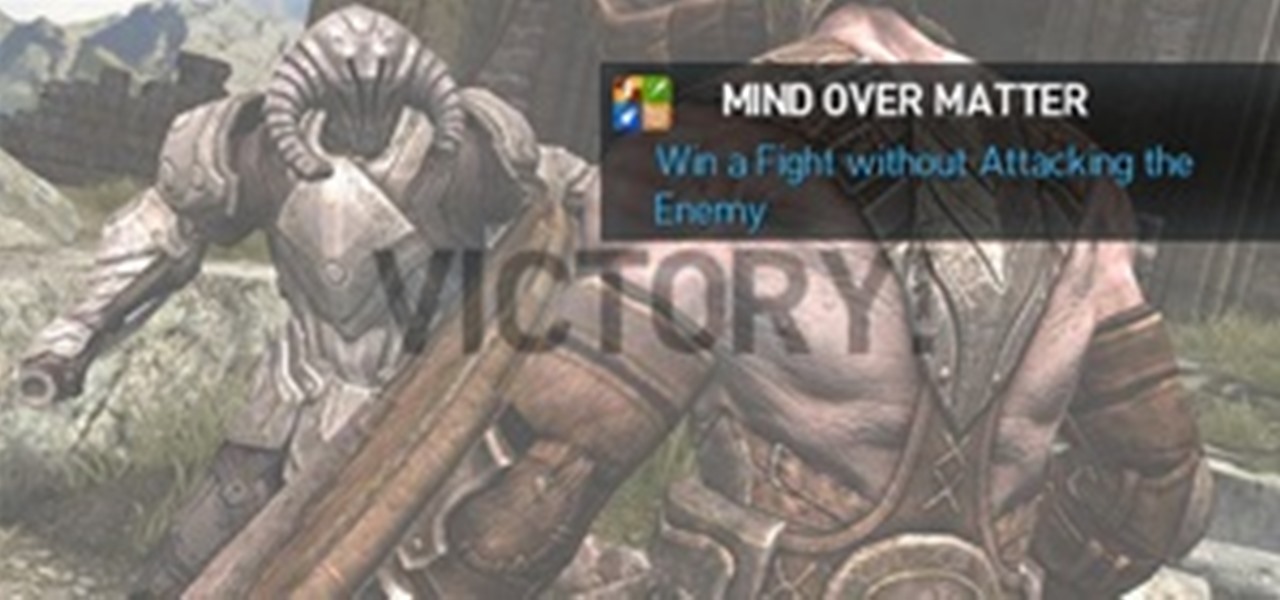
If you were to read the achievements list for Infinity Blade II, you'd come across a rather peculiar one called 'Mind Over Matter'. To get this one, you have to defeat an enemy without attacking him. Say what?

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.
Today my friend finished his house then got blown up by a creeper upon finishing it. He also found 3 wolves- two of which fell off a cliff.

Here are Jerry Brown, Meg Whitman and Arnold Schwarzenegger at the Women's Conference a couple weeks ago. The host of the "Today" show, Matt Lauer, asked both gubernatorial candidates if they were willing to get rid of their negative ads and make positive ones instead. Brown said yes but Meg Whitman said no and gets booed by the women in the audience.

Two Points for Flinching? I wish... In a game marred by a terrible start by the US and a the worst call in World Cup history by the referee as he called back the US's winning goal in the 88th minute.... The bright spot of the match.
to be honest with everyone, this is probably the first thing ive written about magic the gathering, but i figured i might as well start somewhere. in the game of magic the gathering there are countless different keywords, some being common, like trample, or rarely used or seen, like splice. what i wanted to do was take a closer look at some of the different keywords out there, and see just how they change the average game.
This are my tips for fifa 11. The following are purely my opinion and what has worked well for me, it is not my fault if the same things do not work for you.

Posted with permission via HereComeTheYanks.com 1776...a group of colonies walked away from the British, effectively starting a war that ended in the defeat of the mighty Brits.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

Any time a feature is introduced in an MTG set and not replicated in subsequent sets, balancing issues are surely forthcoming. You wind up with one set that can do things the others can't, forcing players to counter that set with other cards from it, and generally limiting the creativity with which one can effectively play the game. Playing these types of cards is like playing trap defense in hockey or boxing like Floyd Mayweather: you might win, but neither you, your opponents, nor the peopl...

If you look up the word SAWBUCK in the SCRABBLE Dictionary, you'd see that it was a sawhorse, but there's another definition that we're all probably more familiar with:

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

The aging and maturity of video games as a medium has lead to some unfortunate consequences. One of these, perhaps drawn from the film industry, is the spate of remakes that has overtaken the game market over the last few years. It hasn't been as bad as the remakeorama trend in cinema, but developers have recognized the value in releasing the same thing they already made and making more money off it. Below, a roundup of some remakes of classic games released for XBLA recently, some fantastic,...

Kizeme This Japanese word, kizeme, means "spirit of attack." It is said of Miyamoto Musashi, the famed Japanese swordsman, that as he grew older he relied more on kizeme to defeat adversaries and, as a result, emerged victorious from challenges without taking the life of his opponent.

Chi gyo ichi nyo is a familiar expression in the dojo. The word chi means knowledge. Gyo means doing, or action. Ichi nyo means inseparable. Action and knowledge are one! Acting without adequate knowledge or understanding is a constant source of frustration and problems. In our lives we are often busy and active without really understanding the basis of our actions and their full impact. Some people practice karate without really knowing why they are training. In class they do the techniques ...

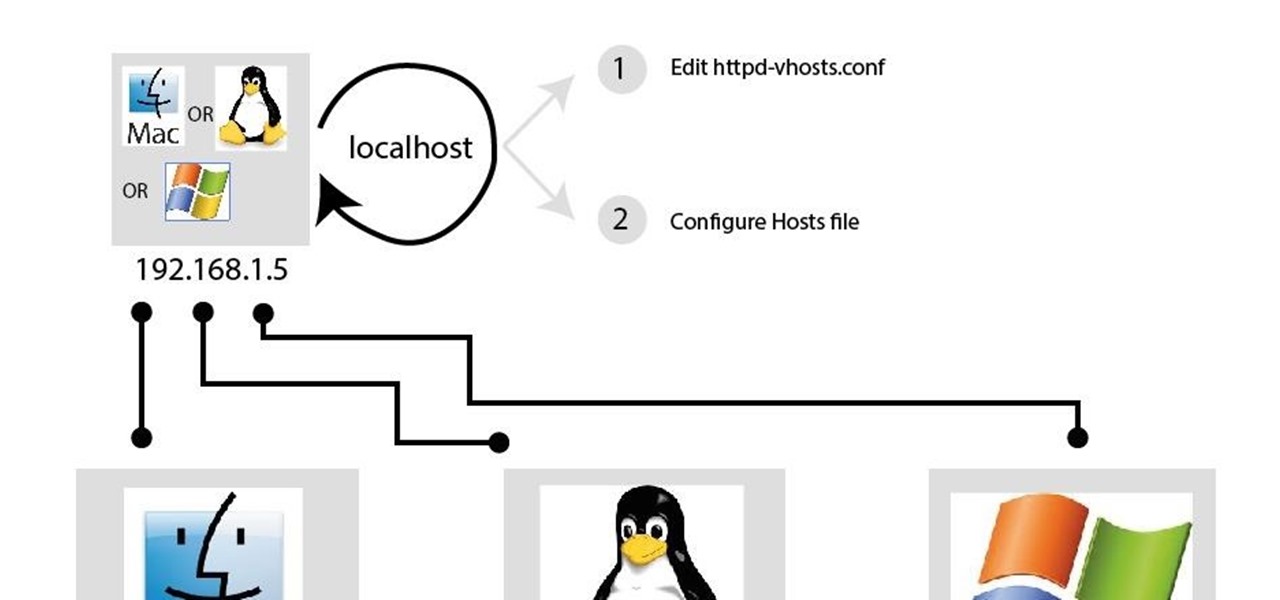
In my last article, I discussed: How to install xampp

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead to mistakes, discouragement, or fighting among a community. What better way to relieve stress and entertain the troops than some old fashioned competition?

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

Posted with permission via HereComeTheYanks.com Ok, so my prediction of a 3-1 USA victory didn't come true. But I can honestly say that I am extremely happy with a 1-1 draw!! There were times where we looked shaky (first 15 minutes). But there were also times when we were taking it to them (Jozy's great run down the flank only to be denied by the woodwork).

Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up.

The Stun-Gun In this article, I'll show you how to make a small, weaponized highlighter. Before I get into how to built this device, let me warn you. This device is harmful! When used, it can cause burns and/or serious muscle spasms. The voltage is potentially deadly! DO NOT attempt to build this device unless you are experienced with safety, electronics, soldering, and understand circuit schematics.

Dungeon Defenders is the most exciting craft game on the Fall 2011 release schedule. I got a chance to play it at PAX in August and interviewed developers Trendy Entertainment last month. After more than a year of publishing difficulty and delay, the game finally came out on PSN, XBLA and Steam. I put about 20 hours into the XBLA version over the past weekend, beating all the campaign maps and racking up a huge pile of in-game money. It is not a perfect game. But it is a huge, challenging, an...

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.