In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

A translation via msnbc.comMeg Whitman says she's a different kind of Republican...But Pete Wilson is in charge of her campaign.Whitman attacks undocumented workers to win votes, but an undocumented woman worked in her home for nine years.She says she'll create jobs---but wants to eliminate forty-thousand state job, including teachers and nurses.Whitman says one thing in Spanish---and something different in English.The real Meg Whitman has no shame. She's a two-faced woman. Resource:http://ww...

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

If you're having difficulty dispatching any of the Corrupted from 2008's Prince of Persia, this helpful battle guide from IGN might be just what you need. If forewarned is forearmed, this video tutorial will arm you to the teeth with the necessary knowledge to beat each of Ahriman's four lieutenants – the Hunter, Warrior, Alchemist & Concubine.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

Wolverine in the most well-known X-Man and arguably the most famous face in Marvel comics. Of course he kicks ass in Marvel vs. Capcom 3! This video will teach you the basics of fighting with Wolverine, including his basic attacks, special moves, and some combos.

Okami was one of the best games of the last decade, perhaps Capcom's finest, and it's heroine Amaterasu makes a much-deserved appearance in Marvel vs. Capcom 3. She isn't quite as powerful as you'd expect the God of Everything to be, but she kicks serious butt and this video will teach you the basics of fighting with her, including tips on all her normal attacks and special moves.

Marvel vs. Capcom has been the flagship series for frenetic 2D fighting games for years, and Marvel vs. Capcom 3 hit store shelves in February. This video tutorial will teach you the basics of the game, including basic combos, hyper combos, team combos, special attacks, and more. Everything you need to start off your MvC3 career right.

Dragons and goblins are two of the many enemies that may come attack your fort in Dwarf Fortress. This video will show you how to deal with attacks by both and preserve the sanctity of your fortress.

If you recently purchased Castlevania: Harmony of Despair on your Xbox 360, this next tutorial will help save your life. In this strategy how to tutorial, you'll find out how to defeat the game's most difficult enemies, the stage bosses. Each one has unique powers and attacks, but they also have some different weaknesses as well. They're easy to follow and should be easy to follow. Good luck and enjoy!

Here are 2 pins for arresting techniques in jiu itsu. One attacks the elbow the other the shoulder.

Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

In this video tutorial, viewers learn how to receive the "Hunter Special" and "Alchemist Special" achievements in the video game, Prince of Persia. To receive the Hunter Special achievement, users will need to deflect the Hunter's attack 5 times in one battle. To deflect an attack, press the Right Trigger as the same time the Hunter attacks you. To receive the Alchemist Special achievement, users will need to defeat the Alchemist without using the acrobatic button. Only use the X button to fi...

The Shiva sisters fight in Final Fantasy XIII is more to prove yourself to the sisters so you may summon them than to actually fight them. To win the battle, you must fill up the gestalt meter which appears over the sisters' heads. No one will die, one sister will actually heal you throughout the battle, but you do have a timer over your head which will give you a game over if it runs out. To begin, use Libra on the sisters to determine their weaknesses, which will make you realize that physi...

The Knights of Gray are back, and they're are here to teach you some boffer sword fighting drills to practice with for your upcoming LARP events.

If you're a God of Mount Olympis, you may want to leave town, because Kratos is still angry in God of War 3 for the PS3. Killing Gods and defiling women are just a couple of his his hobbies. The other is treasure hunting. And in this IGN Strategize video, you'll find the locations of all ten Godly Possessions in God of War III. The Godly Possessions are more than just conversation pieces. Each has a special power you'll be able to use after beating the game once. You'll also get a gold trophy...

Finding all of the rare trade objects in Assassin's Creed: Brotherhood can be infuriating, what with random item drops and quests to juggle. Watch this video for a guide to farming trade objects by killing bandits along a particular route.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

A shield isn't just for defensive maneuvers - you can also use a shield in several different ways to augment your weapon attacks. This tutorial shows you how you can use a shield effecitvely in boffer combat or at a fighter practice.

In this tutorial, we learn how to get the Phoenix achievement in Soul Calibur IV. To do this, you will need to win with all your equipment destroyed. Hit high and do low attacks to help you get the advantage. Don't fight and just stand there until all your equipment is gone. Go to the Tower of Lost Souls and do this on Floor 11 to help you get this achievement more easily. After the opponent knocks off your equipment, you will be able to start fighting and hurting the other person until they ...

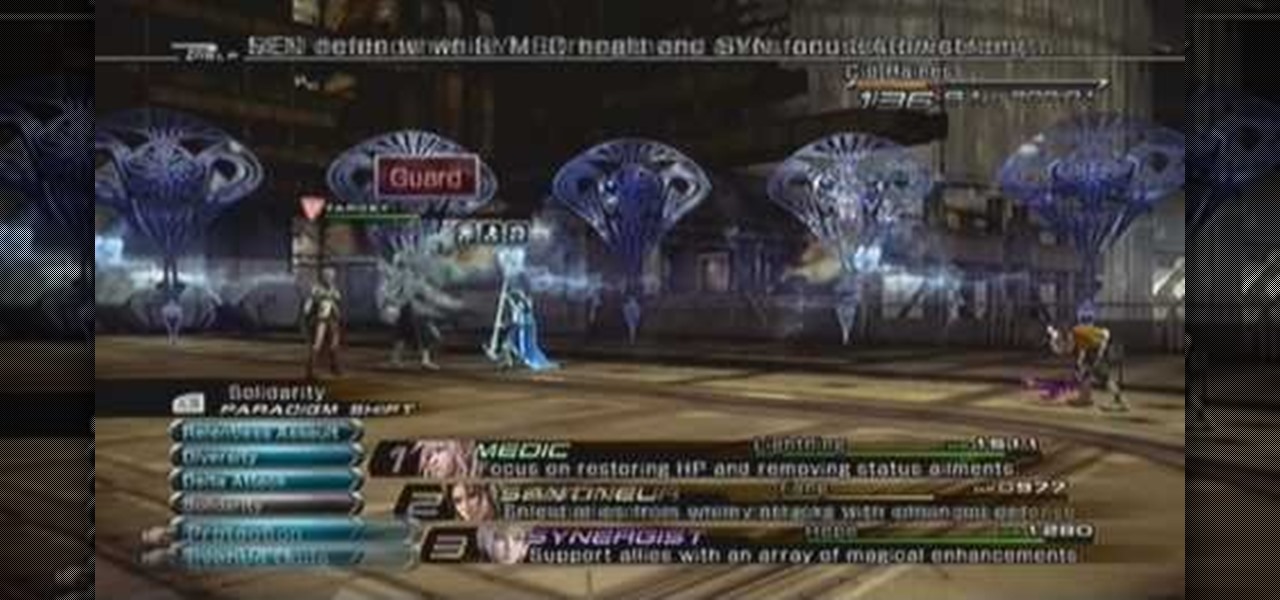
Make sure to buff up before fighting Barthandelus. Make sure you use the aegisol buff. Then use your Liba Scope ability in order to understand its weaknesses. Attack the smaller heads before attacking the main upside down head, because in the beginning it will be almost invincible. After attacking the sides of the boss, attack the main head. If your health drops to about half, switch over to medic class and heal. The boss has some strong attacks so make sure to be ready for them. If you buff ...

Street Fighter IV : Blanka, the Brazilian Beast unleashes havoc upon the World Warriors once again. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

Street Fighter IV : Vega, the beautiful Spaniard delivers gruesome damage. Street Fighter IV is a 2008 fighting game produced by Capcom. Street Fighter IV is currently released for PlayStation 3 and Xbox 360, with a Microsoft Windows version in the works as well.

'Wayward Son' is a main story quest about halfway through Act 1 of Dragon Age 2, in which you are called upon to, big surprise, help a mother and son in need. This video series will give you a walkthrough of the entire quest, allowing you to complete it yourself and also making a compelling viewing experience in it's own right.

California is struck by earthquakes everyday, but the biggest ones, on average, appear every 150 years, just south of the San Gabriel Mountains. The last super-destructive earthquake in California was over 300 years ago, which could mean a long overdue Californian earthquake is on the horizon.

This is a tutorial for controlling the Pine tip moth. Identifying and controlling the pine tip moth consists of studying the small plants of pine. The attacks on pine trees is caused by Nantucket pine tree moth found along the Rio Grande Valley as far north as Espanola, it has spread to South Arizona and California by importing grafts from Mexico. The moths are 3/8 inch long reddish brown to grey in color. They attack the main stem of the baby plant and the pines instead of growing vertical g...

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Cid Raines has always been a formidable foe in the FInal Fantasy series. This video will show you exactly how to beat him in FInal Fantasy XIII.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

If you're trying to figure out how to play the Disgaea 4 combat modes effectively, take a look at this guide on positioning, attacking, defending, and more while fighting against opponents in the PS3 game. The combat can be a little confusing but there are many different options such as team attacks and combo attacks. This tutorial will give you some understanding of the early fights in the game.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Learn to perform a Jiu Jitsu Banana Split leg submission. This is a submission for grappling not self defense. It attacks the groin by pulling the muscles apart.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

In this video tutorial, viewers learn how to checkmate an opponent in four moves in Chess. This task is very easy, simple and fast to do. Begin by moving your pawn to E4. Then on your next turn move the bishop to C4 to attack F7. Now move the queen to A5, which also attacks F7. Finish by moving the queen to F7. This is an automatic checkmate because the opponent will lose the king in either way. This video will benefit those viewers who enjoy playing board games such as Chess, and would like ...

This video answers some questions on how to identify some of the problems that occur in vegetable gardens: for example, if there are missing leaves on your tomato plant, then it is an indication that they are being eaten by something. In some cases, this pest is the Tomato Hornworm. The Mosaic Virus and Curly Top and Tomato Spotted Wilt also attacks tomato plants.