
News: Capture the Flag/King of the Hill - Massively Multiplayer Map (Map Update!)
Yeah, it's not done yet! But it will be soon!!! I had an exam today and that was my last one so I will hopefully be done before I leave for Perth this weekend! :)


Yeah, it's not done yet! But it will be soon!!! I had an exam today and that was my last one so I will hopefully be done before I leave for Perth this weekend! :)

Learn how to connect a DVD or Blu-Ray player to the Internet. You'll see the simple steps on how to connect a DVD or Blu-Ray Player to the Internet using the powerlines in your home with Powerline Adapters from Actiontec Electronics.

To get the Guerilla Tactics achievement / trophy in Bulletstorm, you must execute 25 skillshots in a single Echoes map. Skillshots are the most fun part Bulletstorm. This video will give you a handy step-by-step guide to getting the achievement in Collapsed Building.

How far would you go to save your life? For James Franco, who plays real-life hiker Aron Ralston in Danny Boyle's "127 Hours", staying alive means cutting off your own arm with a dull pocketknife. If you've seen the movie (or even heard about all the people who fainted and threw up after watching it), you know that it presents one of the most grueling self-amputation and bone breaking scenes in movie history.

If you're a fan of the Oklahoma City Thunder, then you must be a fan of Kevin Durant (previously of the Seattle SuperSonics). And since you're a fan of Kevin Durant, you should try putting your art skills to test and attempt to draw a nice portrait of this great basketball player in his Team USA uniform.

Deaf people are just like everyone else, and they have a responsibility to save lives just like the rest of us. Those with hearing impairments might not be able to benefit from most online first aid training, but this video is signed to give those with hearing problems the info they need to help out.

Michelle Phan presents this tutorial on how to take a tomato and turn it into an invigorating scrub.

Watch this great cooking video on how to cook Indian shrimp biryana, which is a Goan rice dish. If you’re tired of the same old biryanis, try this Goan-inspired recipe for shrimp (prawn) biriani. With the creaminess of coconut milk and freshness of mint, it’s the perfect combination!

The people from openorigami.net demonstrate how to make an origami ray fish.

The emergence of Facebook's collaboration with Ray-Ban to launch Stories smartglasses has finally put an exclamation point on a new category of smartglasses: the pre-augmented reality wearable segment.

Facebook promised that it would release a pair of smartglasses in partnership with Ray-Ban sometime this year and now it looks like we have our first look at the device.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

This walkthrough guide will cover the complete Overload DLC mission pack for the Mass Effect 2 action role-playing game on the Xbox 360. Overload became available for download in June 2010 on Xbox Live Arcade (XBLA), and features four different missions. Watch this series for all the gameplay action from Mahalo.
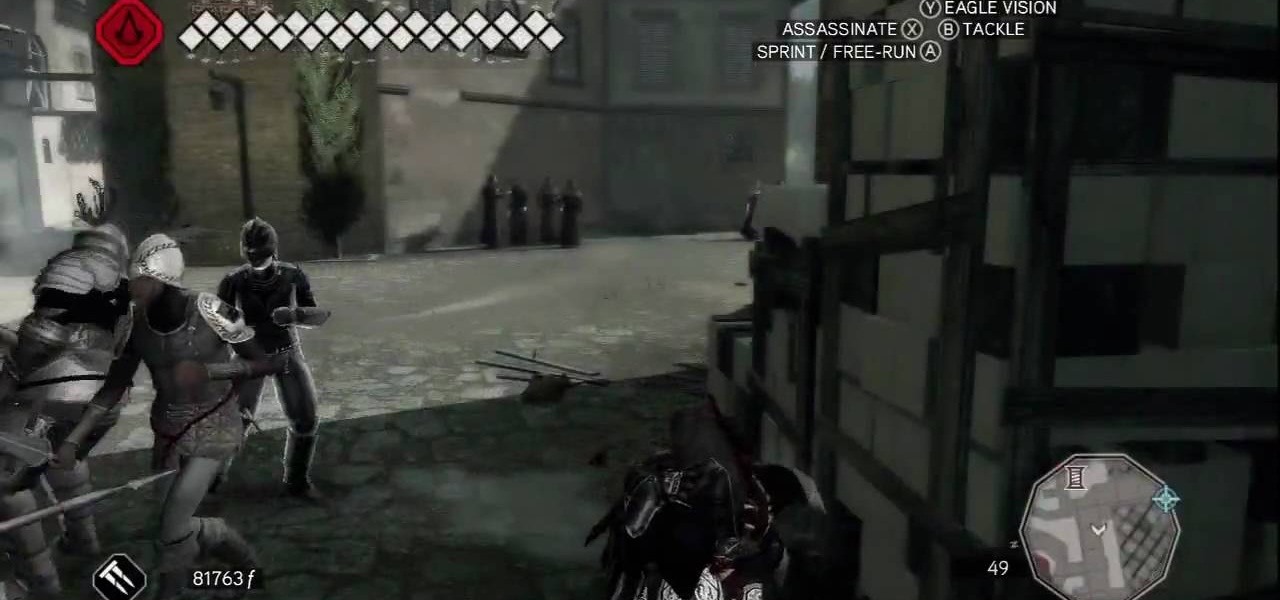
Assassin's Creed 2 was so popular of a game, that it spawned not one, but two downloadable content expansions, for both the Xbox 360 and PlayStation 3 versions. The first DLC was called The Battle of Forlì, and the second, Bonfire of the Vanities. This video game walkthrough focuses on the latter, in 1947 Florence, Italy, where the mass burning of sinful objects is an everyday event.

This is the end of L4D2. Your last campaign. Your last chapter. See the best part: Campaign 5: The Parish - Bridge. Stock up on items and heal up. Climb the ladder and you should find some more medkits and weapons to take. Open the door and head outside. Use the radio on the ground to hear your situation explained to you. You will have to lower the drawbridge and get to the rescue chopper on the other end. If you complete the bridge sequence in under 3 minutes, you will unlock the "Bridge Ove...

You don't need flying broomsticks or magic balls to play this version of the game – it's tailor-made for muggles like us.

An online English teacher explains to English-language learners how to correctly use the word "make" as a causative verb in this instructional video. As usual, he provides many examples to in order to make the contextual usage of this important verb more clear to those attempting to learn American English for work or pleasure.

This how to video has whole food recommendations for relieving depression from a nutritional and herbal perspective. Watch and learn how simple it is to prevent and beat depression with a wide variety of fruit, vegetables, and whole grains. Avoid caffeine and make an attempt to incorporate leafy greens into a diet.

This video teaches you how to do a back flip on a swing. Doing back flips can be dangerous so make sure you are supervised by a professional before attempting to this on your own.

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Step 1 Wash your canning jars, along with their lids and screw bands, in very hot, soapy water. Rinse well and let them air dry. Check for cracks and chips before using.

Make the most of summer's bounty by learning how to preserve it for winter. You Will Need

Okay, Mr. Thrifty, you reserved the least expensive hotel room that you could. But your inner Donald Trump doesn’t want to settle for low-frills. Go ahead, it never hurts to ask. Watch this video to learn how to get a hotel upgrade.

Learn how to play the intro to "Voodoo Chile" by Stevie Ray Vaughan on the electric guitar

Watch this video to learn how to tie a Ray Charles for fly fishing.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you've read or watched anything Harry Potter before, you know friendship and teamwork are huge parts of the story. The same goes for Harry Potter: Wizards Unite, with its "Wizarding Challenges." Here, you can tackle Fortresses full of Foes alone, but why do that when you can battle with up to four other friends at once? Here's how it all works on Android or iOS.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.
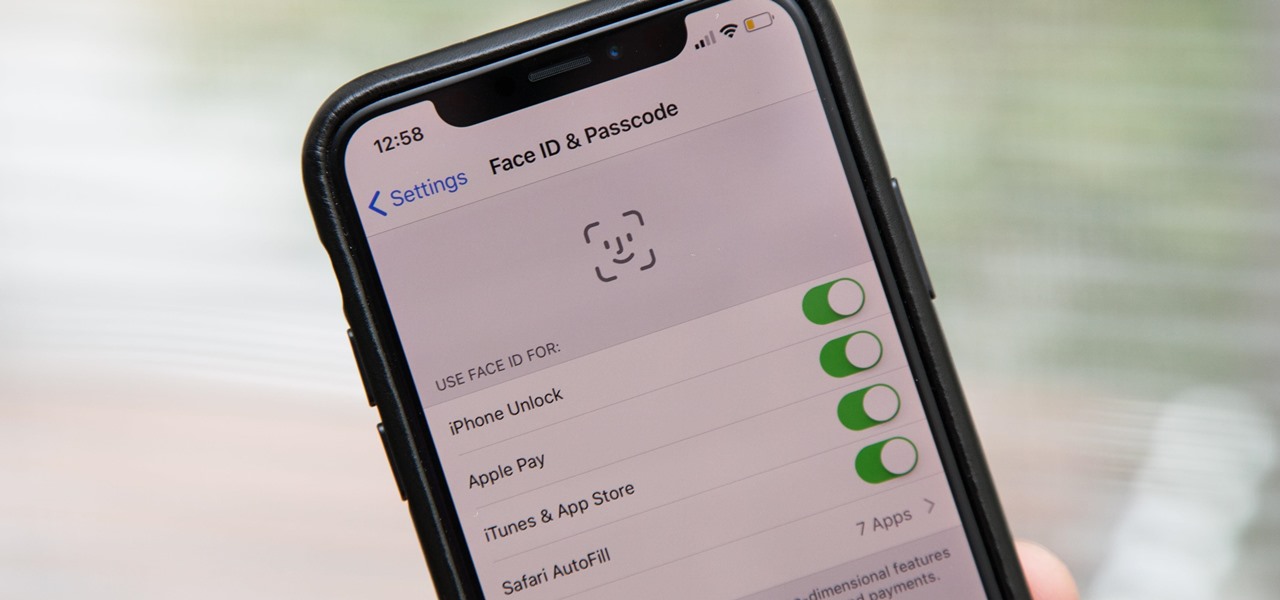
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.