ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public beta opened up just five days after the release of iOS 11 developer beta 2, so iOS 12 is pretty much right on track in that regard.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Before Apple jumped into the phablet game with their iPhone 6 Plus, there was the Samsung Galaxy Note series. Initially knocked for their size, the Notes slowly but surely gained popularity, thanks to powerful hardware, incredible displays, extensive features, great battery life, and a surprisingly-useful stylus.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Ray Boone shows us how to grip the golf club to correct an over the top golf swing. Part 1 of 21 - How to Correct the over the top golf swing.

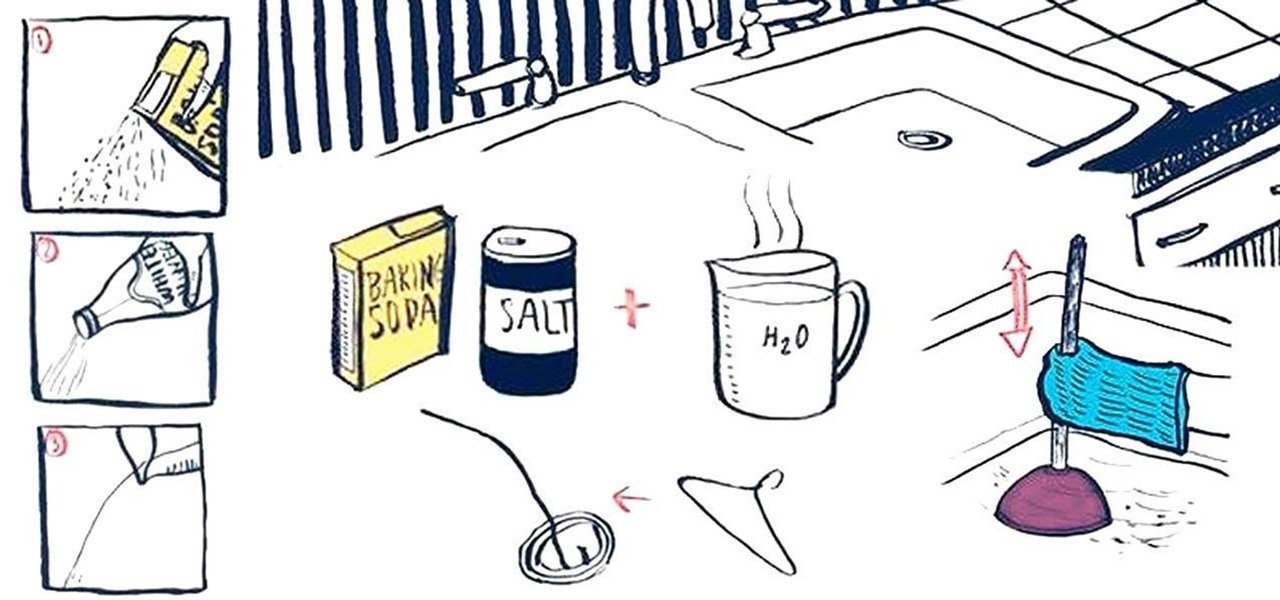
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

There’s nothing more special than a beautiful pearl necklace. But how do you know if they are real? Knowing some qualities that pearls have should help you determine when there is an obvious fake in your presence. It might ultimately be necessary to leave it to a professional to authenticate those pretty little presents from the sea.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

As soon as you try recording a video in the Camera app on your iPhone, any music playing on your device comes to a halt. Apple Music. Spotify. Pandora. Tidal. Deezer. No matter what you're listening to, as soon as you switch to "Video" in the Camera app, the music will stop. However, if you want background music in your movie files, there's a workaround to avoid having to add an audio track in post.

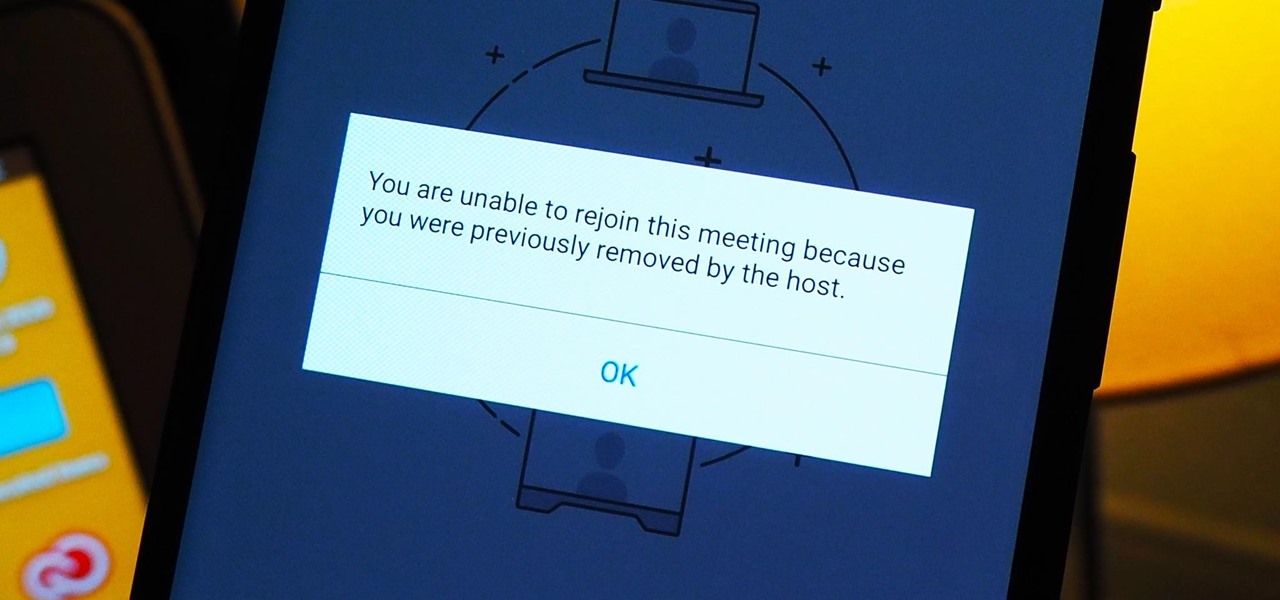
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Part of the fallout from the canceled Mobile World Congress is that a range of products, ideas, and designs slated for reveal in Barcelona are now being showcased without the framing and context of the massive tech gathering.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

Filmed in what appears to be a single continuous shot, war film 1917 is now the front-runner to conquer the Best Picture category of the Academy Awards after bringing home the Golden Globe for Best Motion Picture in the drama category.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

All those Apple commercials encouraging people to use their iPhones to make their smartphone movies look amazing, but how can you achieve some of the same looks? That's the question many often ask after plunking down over $1,000 for a brand new iPhone, shooting some video, and getting somewhat mediocre results.

The iPhone's autocorrect feature is wonderful and convenient, but it doesn't always work with informal language like profanity. If you've ever used the F-word, there's a good chance you've had your curse words "corrected" to other words that don't ducking make sense. And with the release of iOS 13, swearing in your messages and on social media could get a little harder.

Until Star Wars-style 3D hologram projection technology becomes commonplace, the near future of certain kinds of remote work is in robotics. Now, a new dynamic is using augmented reality to give this kind of telepresence a kind of superpower.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

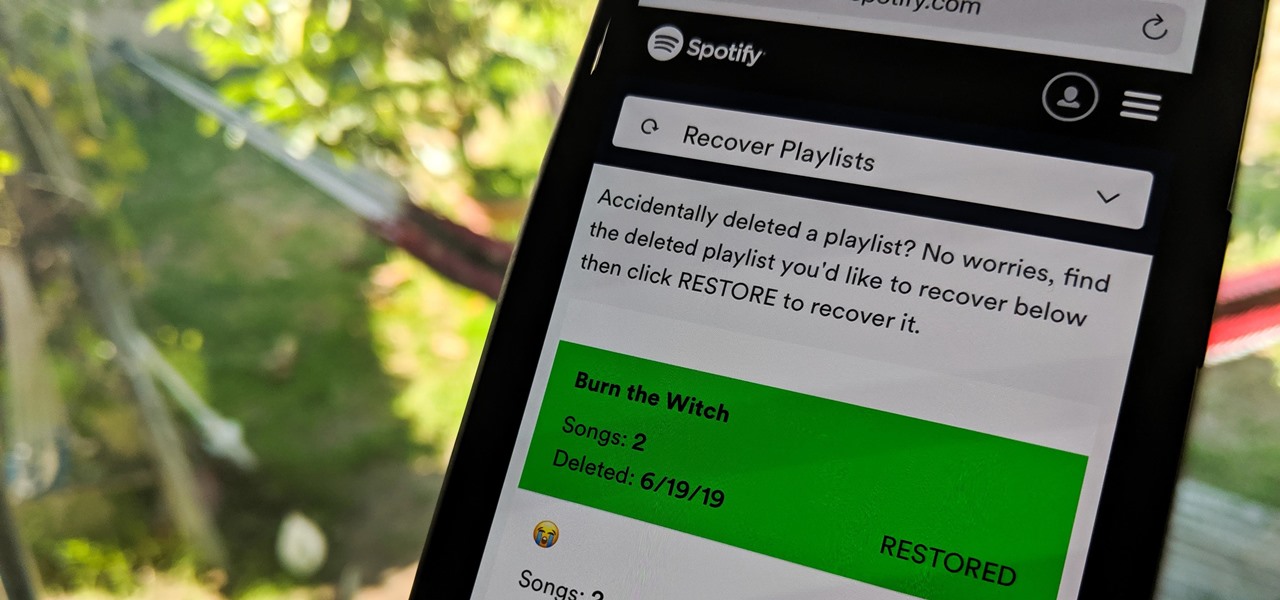
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

After winning the 2015 FIFA Women's World Cup, the USA Women's National Soccer Team is ready to defend its title in the 2019 tournament.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.