If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Watch this video tutorial to learn how to bypass the cumbersome process of making squaring backings for your quilts. This is an attempt to show you how and why you may never want to make a perfect square backing for your longarm sewing machine again.

This instructional ceramics video will show you how to throw a large tiered bowl with expert, Simon Leach. Leach provides some of the delicate visuals needed to throw a large clay bowl. It is important to keep the clay evenly moist as you add the tiers. You may have to go back later to attempt to even out the balance of your tiered ceramic pot.

Here is the first attempt to make a scorpion on video using copper wire bending.

This video provides a tutorial on how to disable the seat switch on your riding lawn mower. The riding lawn mower will stall if you attempt to put it in gear and no one is sitting on the seat. This video will show you how to prevent that.

MrfixitRick and his assistant Rowan try four "Will It Spin?" experiments in an attempt to see if different objects spin with the rotating magnetic field of the Tesla CD Turbine.

Learn about ancient iridized glass and a method for creating iridized glass surfaces. This video is part of the exhibition "Reflecting Antiquity" at The Corning Museum of Glass (February 15 - May 27, 2008). Note: the method portrayed uses stannous chloride fumes, which can be highly toxic. Do not attempt this without proper protective equipment.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

With Apple preparing to bring a slew of new features to its Animoji app this fall, Samsung has updated its AR Emoji imitator with the ability to create more realistic digital doppelgängers.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."

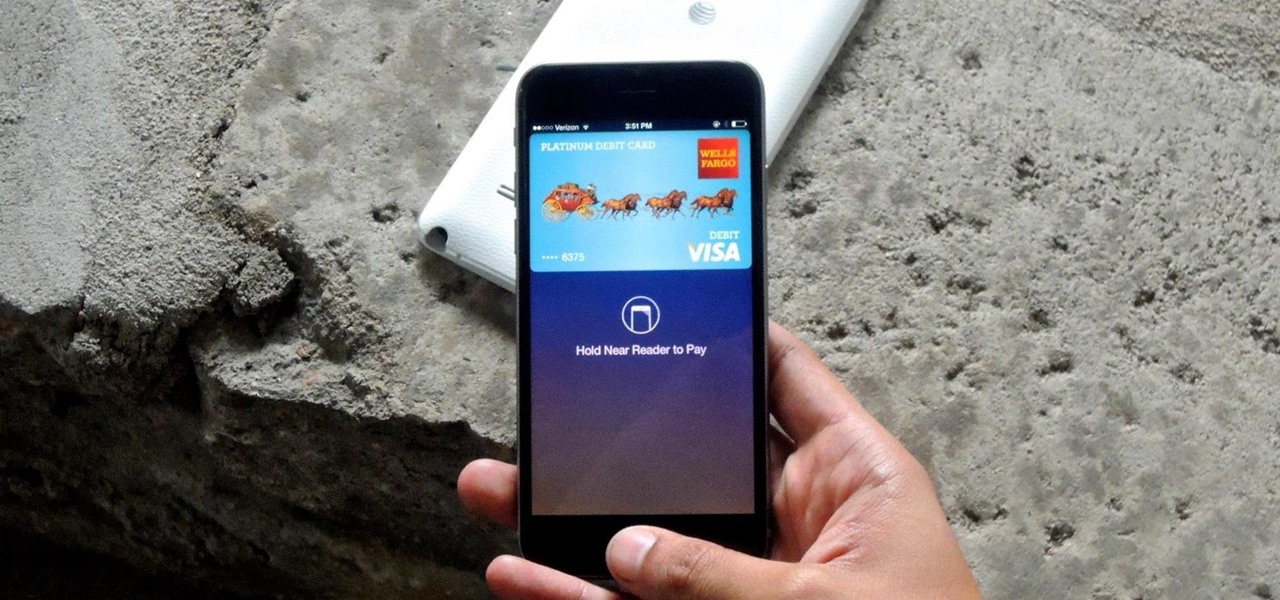
Apple Pay is ready for use at over 220,000 outlets across the United States. By using your iPhone 6 or 6 Plus, all you have to do is point your device at any NFC-enabled point-of-sale system compatible with Apple Pay, press your fingerprint on the home button, and voilà—you've just paid for something with your card. As a matter of fact, the store doesn't even need to have Apple Pay compatibility to work with your phone. If their machines have NFC-technology, they'll recognize your device (unl...

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

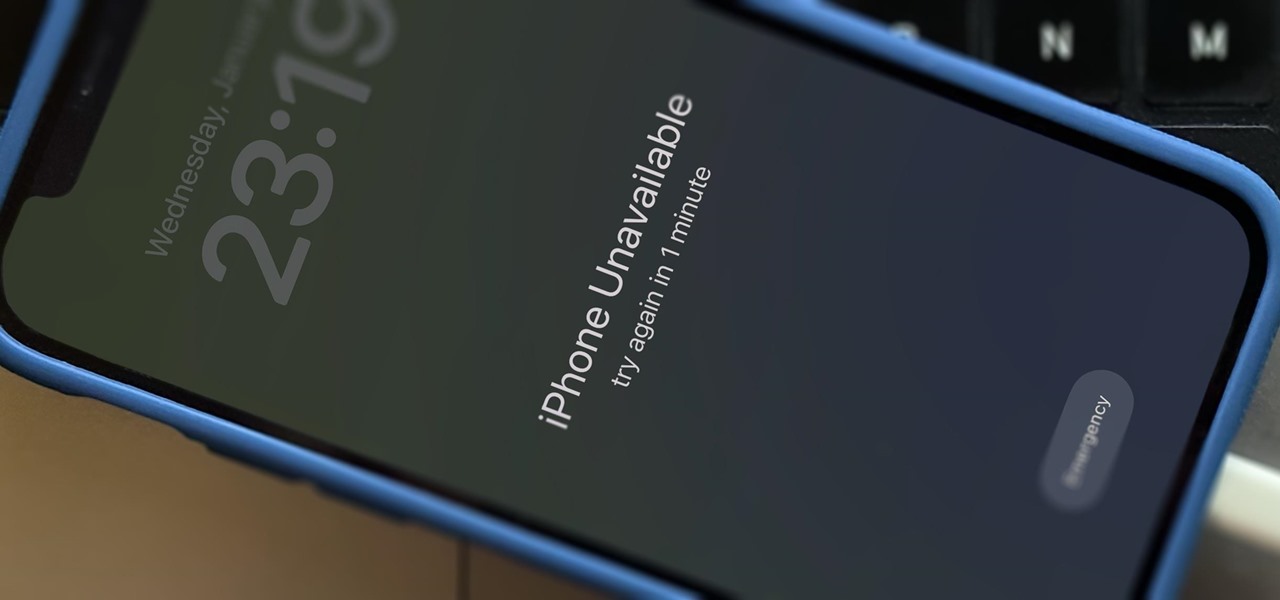
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an easy way to make it an almost impossible feat.

Guy Fieri is no stranger to oddly-placed restaurants, but in this episodes of Diner's, Drive-ins, and Dives, he visits one of the strangest yet, a combination car wash / laundromat / gourment cafe in San Antonio, Texas to sample and observe the preperation of a lamb burger that he claims is the best he has ever had. The lamb burger is a delicious dish that remains somewhat obscure in America, but if you've ever wanted to attempt one, this recipe is what you've been looking for. It includes a ...

See how to hack the flash game Jetman, which you can play on Facebook. This Jetman cheat will give you top score using Cheat Engine.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 with Cheat Engine (09/25/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get money on Wizard101 (09/23/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get to find a walk through walls glitch in Wizard101 (09/20/09).

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to download Wizard101.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial from Wizard101Tutorials1 to learn how to walkthrough "Skeletal Pirates" in Wizard101.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to find the Smiths locations in Wizard101.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

Compared to fully untethered jailbreaks, semi-untethered methods like Chimera for iOS 12 have one major handicap: you need to re-enable the jailbreak every time your iPhone turns off or restarts. As intimidating as it seems, however, kickstarting the mod and restoring your tweaks is still pretty easy.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

In a bit of a strange decision, Microsoft has made it to where some users don't have a choice in the matter of applying failed automatic updates. When a Windows or driver update comes your way and fails to apply for any reason, your computer will continue to attempt applying the broken update at seemingly random intervals. The Pro and Enterprise editions of Windows 10 will allow you to delay or stop updates altogether when something like this happens, but the Home edition has no such setting.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

The volume is maxed out, but that doesn't stop me from hitting the volume key on my Nexus 7 in hopes that it will magically get louder. This happens to me everyday as I watch videos or play music. The simple fact is that a Nexus 7 tablet just doesn't get very loud. At least, not loud enough for me.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.