Your Apple TV is just that — your Apple TV, which means you probably want to personalize it a bit, to make yours stand out from everybody else's. And the easiest way to do this is by renaming it. If you live in an apartment building, this will help differentiate your Apple TV from your neighbors' when trying to use AirPlay.

Developers looking to create shared experiences that support both HoloLens as well as ARKit may be able to get it working in Unity since that the engine supports both platforms — though, the amount of effort it might take to get that working could be a bit much. Up to this point, Unity has been the only real approach to attempt this combination — at least, until now.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Luden.io just revealed more details about their mobile game "AR Tribe," made using Apple's ARKit. The company has previously focused on VR games such as InMind 2 and VRobot. This is the company's first attempt at AR, and it looks like it's going to be pretty cool.

If there's one thing I know, it's that people hate buying mobile games. I'm the same way — no matter how good a game looks, if I have to pay for it, I have to fight the urge to immediately walk away. That's why it's such a big deal when a great game goes on sale. Right now, that game is 'Reigns.'
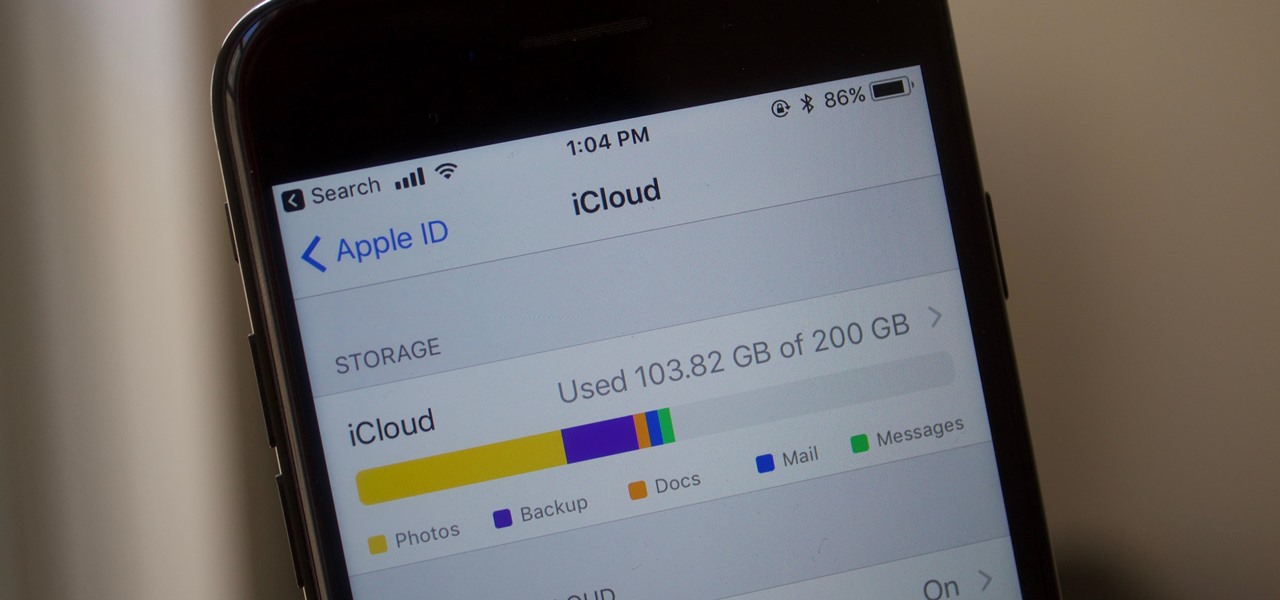
iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

Lately, the biggest news in driverless has been the raging lawsuit between two autonomous spearheads, Uber and Google's Waymo. A new bill back by General Motors, however, could take them both out of the race towards driverless.

The Last Supper, or L'Ultima Cena, is a mural painted by Leonardo da Vinci in 1498. It is considered one of the greatest paintings of all time, and if you live in the San Antonio, Texas area, or are willing to travel, you can get it shaved into the back of your head.

Lightning is scary and powerful, yet when harnessed correctly, it can become a beautiful pattern for hand-crafted wooden furniture. Muchd like Zeus in ancient mythology, Canadian Woodworks is harnessing the power and beauty of lightning, but they're doing it for aesthetic purposes.

Hey everyone, this will be a quick post. Facebook does not use HTTP Strict Transport Security (A header that tells the browser to only use HTTPS when communicating with the server) on subdomains of facebook.com. That means, if someone uses facebook in a different language, the browser will attempt to connect using HTTP first. An attacker can intercept that request and serve a different page, including a fake login one.

If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

According to George Gjoka, a professional Paintless Dent Repair (PDR) technician, when you attempt to take a dent out of your car, you're probably doing it wrong.

In an attempt to get more people to subscribe to Apple Music, the Music app was completely revamped in the iOS 8.4 update for iPad and iPhone to include new tabs for New, For You, and Connect.

In an attempt to remain a mobile-exclusive app, Instagram doesn't let users upload photos or videos from their computer. On the Instagram web app, you can pretty much only like and comment on items in your feed, but what about all of those photos on your computer that scream #tbt?

For a number of years, I have had a vortex cannon on the top of my list of projects to attempt. Creating a sturdy cone for the barrel has always been a hurdle in the design, one I finally found a solution for in this video.

The display on the Apple Watch is way too small to even attempt typing on it, which is why the Messages app only allows for responses using default replies or by speaking a message. But you won't always be able to speak a message, and often the default replies will be too generic to want to use.

If you have an Apple Watch, it's easier than ever to ask Siri for directions, send a quick text, or locate the nearest Chipotle—because you don't need to pull out your iPhone anymore. Luckily, Apple made it fairly painless to get Siri up and running on the Watch, so let's go over the two quick activation methods.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

Reminding a spouse or roommate to pick up some last-minute groceries is typically done with a quick message that can easily go unnoticed or unseen. Your feeble attempt of a reminder won't work unless it's conveniently sent at the right moment, like when they're on their way home. Chances are, you'll forget to text them and they'll forget the earlier reminder you sent.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

If you ever wanted to communicate with friends without having to deal with those pesky essentials like words and phrases, have no fear, Emoj.li is here!

Imagine this: You're driving on the freeway in Canada, enjoying the view and sipping Tim Horton's, when all of the sudden you see something out of the corner of your eye. You expect it to be a moose, obviously, but instead you see a robot with his thumb hitched up. So, after insuring that you didn't accidentally take some hallucinogens a few miles back, do you pick it up?

Peeling apples is pure grunt work, especially if you have a recipe that calls for a lot of 'em, like apple pie. You can make this task go by much more quickly if you use something from your tool box—your literal tool box, that is.

Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it feels.

Just like some of its popular puzzle predecessors, 2048 is an extremely simple yet insanely addicting game that pits you against a slew of blocks, to be configured into increasing sums with fervid, high-paced moves. If you have yet to play it, check out either the iOS (by Ketchapp) or Android (by Estoty) versions of the game. Due to its overwhelming popularity, dev TalkLittle has ported the puzzle game as 2048 for Chromecast (available for Android only), which lets you play the game solo or b...

In an attempt to keep things simple, Snapchat has a limited amount of editing features, made up of "smart" photo filters, drawing pens, and special text captions. If you want more editing capabilities, you'll be pleased to know there's a way, no thanks to Snapchat, but you will need to be rooted.

I hate typing in my password every time I want to install an application on my iPhone. My fat fingers make it so that I rarely get it correct the first time. If you're like my mom, you might not even remember it. Keyboard shortcuts are not a viable option either, since they are disabled for passwords.

If you're a user of Google Play Music, but not a fan of being relegated to a browser tab, I've got you covered. Developer Sajid Anwar has created a desktop client for Google's music service, but since he made no attempt to hide logos and trademarks, it may not be long before the app vanishes completely. So get it while it's hot...and before Google takes it down.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

Yes! soon I will be able to log in more as I untie the shackles this map has placed on me in the time leading up to its eventual release and log in once in a while!

Yeah, it's not done yet! But it will be soon!!! I had an exam today and that was my last one so I will hopefully be done before I leave for Perth this weekend! :)

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.