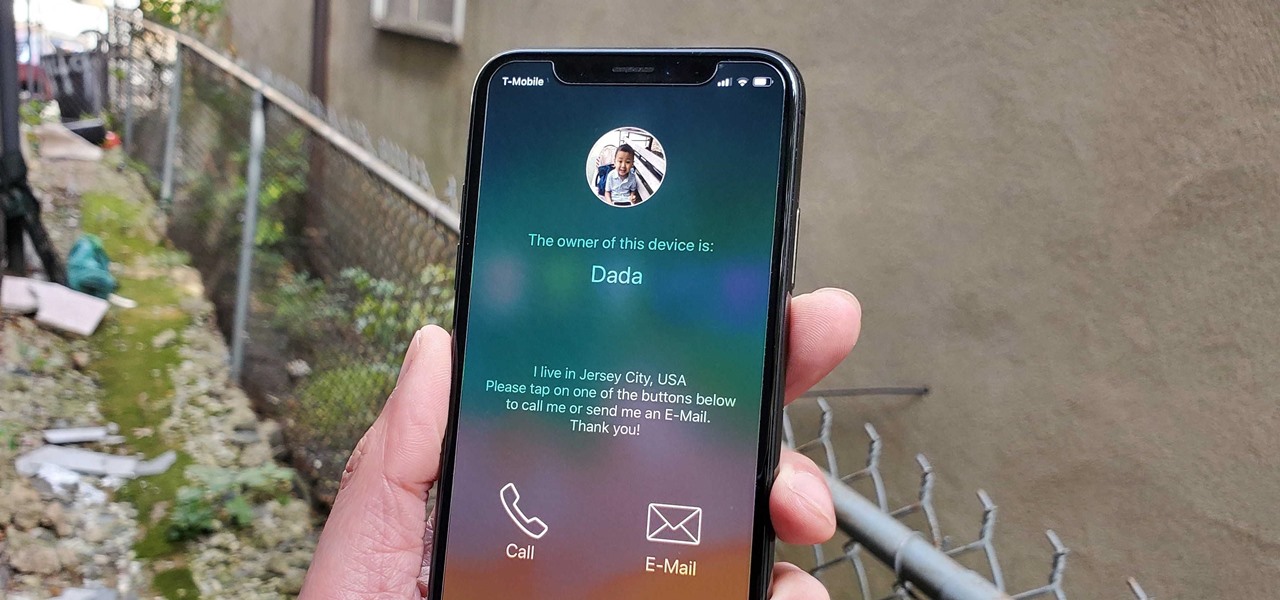
Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Did you know that cookies are one of the most popular holiday desserts? Sugar cookies in particular are so easy to make and easy to decorate. They are the perfect treat for your office, friends, and family…or just yourself!

French toast is one of those things that everybody kind of knows how to make, but few people know how to do really well. And while the dish originally does hail from France (its original name, pain perdu, means lost or wasted bread), it has become a beloved American breakfast dish.
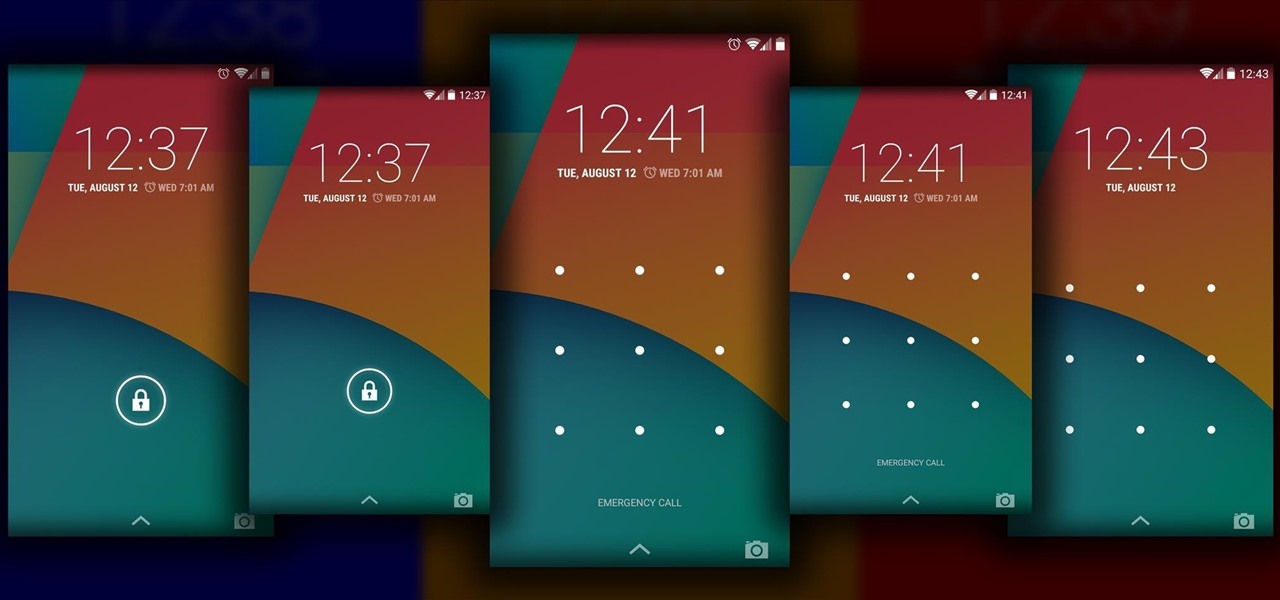
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

The paper towel is a wondrous invention. It allows cooks to wipe up really gross stuff without having to constantly do laundry and drain fried foods so they're crunchy and crispy instead of oily and heavy. But did you know that your humble paper towel has several other uses besides the obvious ones? Read on to find out these essential hacks.

Biting into a perfectly ripe mango is living proof of nature's goodness. The flesh is at once creamy, smooth, tart, and sweet. Plus they're incredibly good for you.

You probably already know that cooking involves a ton of chemistry. Bread rises because of the reaction between the flour and leavener, and the delicious crust on your steak is formed by the Maillard reaction. Understanding the chemistry going on behind the scenes is one of the best ways to improve the quality of your food—it's much easier to fix a problem when you know what's causing it.

Cooking may be an art, but baking is a science. It requires precise measurements since the outcome is based on chemical reactions. Using too much or too little of one ingredient can be the difference between perfect, crunchy-yet-chewy cookies and the dreaded "one big cookie." That's why frozen cookie dough and pre-made bread and cake mixes are so popular. They're easy to throw together, and pretty much guarantee success every time. But what if you're feeling so lazy that you don't even want t...

To add flavor and moisture to your chicken, beer can chicken can allow you to cook a whole chicken on the grill. This tutorial outlines how you can do it to get moist, flavorful chicken. It also ensures that your meat cooks evenly. To begin, combine 1 teaspoon of sugar and salt, 1 1/2 teaspoons of paprika, 1 teaspoon of ground black pepper, 1/2 teaspoon of onion powder, 1/2 teaspoon of garlic powder, and 1/2 a teaspoon of cayenne powder. Stir these ingredients together. Next, rinse your chick...

The best chemistry experiments are those you can perform with items already laying around your house. With only some sugar, salt substitute and an instant cold pack, you can make your very own gunpowder! Being able to make homemade gunpowder without a trip to the store can be a lifesaver, no matter if it's just for testing out a Civil War-era musket, blowing up stubborn tree stumps, or preparing for battle when imperialists overrun your country.

If you've ever been in the kitchen making your grandma's famous cookie recipe and when it comes time for the brown sugar found yourself stuck with an unmalleable, rock-hard chunk instead of measurable granules, then you will appreciate this tip.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

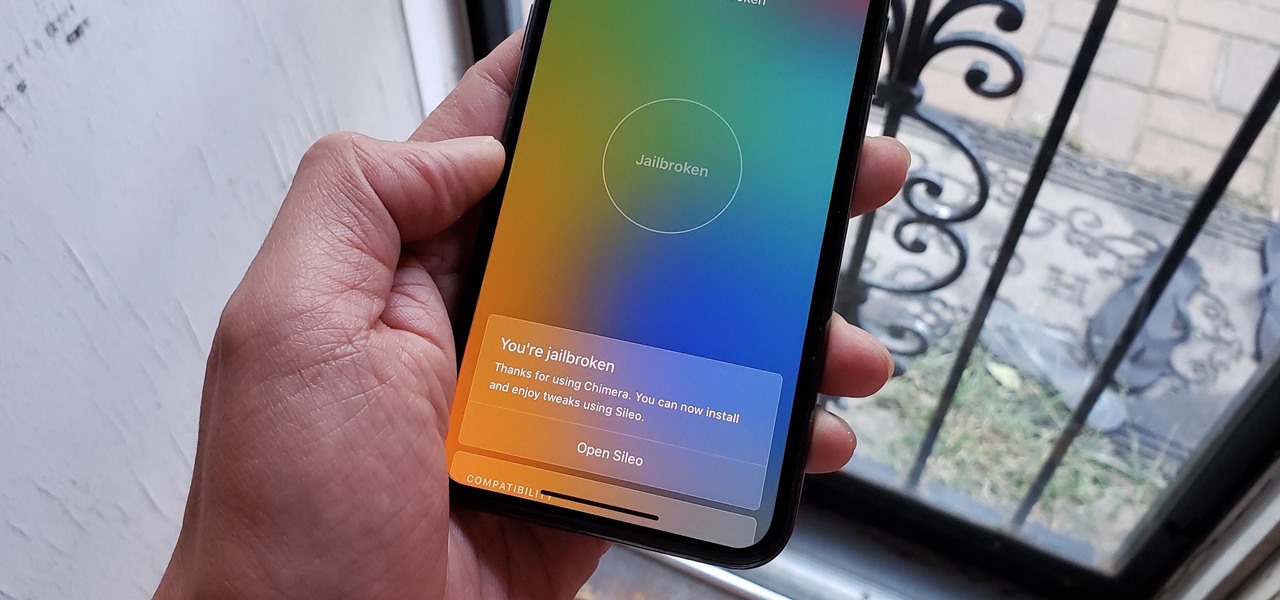
Compared to fully untethered jailbreaks, semi-untethered methods like Chimera for iOS 12 have one major handicap: you need to re-enable the jailbreak every time your iPhone turns off or restarts. As intimidating as it seems, however, kickstarting the mod and restoring your tweaks is still pretty easy.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Google updates the Play Store periodically, but the changes are usually subtle. A recent server-side update, however, is shaking things up quite a bit.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

On Wednesday, Snap, Inc. unveiled a revamp of its Snapchat app that draws a hard line between content from your friends and content from professional media organizations.

Face ID is possibly the iPhone X's make-it-or-break-it feature. Apple is asking previous iPhone owners to put a lot of faith into their home button replacement, and so far, the results seem pretty good. That is until CNN tested the security feature with identical twins.

Nope, it's not 2016 again. Samsung is giving it another go at beating its competitor by attempting to unveil their new Galaxy Note 8 before the new iPhone. Because it worked out so well the last time.

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

The headline above may have some spice addicts shaking their heads, but, believe it or not, there are people out there who either don't like or can't handle a ton of spice.

A little less than a year after announcing "Project Astoria," Microsoft announced Thursday, February 25th, that it will end the "Bridge," which would have brought Android apps to the Windows Store.

Oven space is scarce on that fated fourth Thursday of November. Even if you can find a spare space for pumpkin pie on the bottom shelf, you risk turkey drippings overflowing from above and ruining your beautiful dessert — not to mention a burnt crust from different temperature requirements. The bottom line is: oven real estate is valuable, and it's tough to multitask cooking for Thanksgiving when every dish requires baking or roasting.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

If you've been watching the latest USA TV Series Mr Robot, you will have seen the Raspberry Pi used by Fsoeciety to control the HVAC system. OTW covers this very well here with his take on setup they may of used.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

We all know that opening our work emails at home is a bad habit. Yet reading and responding to emails every time your iPhone dings is worse than you might realize. Not only are you extending the workday, but you are also sacrificing your ability to perform on a daily basis.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

The idea of a no-churn ice cream seems like the ultimate dessert hack. But, in fact, this concept has been around for at least the past 100 years in what Italians call semifreddo.

Notifications are an integral part of our day-to-day smartphone usage. They allow us to easily see and act upon all of the latest information that comes our way. Well, most of the time, that is.

The volume is maxed out, but that doesn't stop me from hitting the volume key on my Nexus 7 in hopes that it will magically get louder. This happens to me everyday as I watch videos or play music. The simple fact is that a Nexus 7 tablet just doesn't get very loud. At least, not loud enough for me.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Kids have an infamous reputation for thinking vegetables are icky. After all, when compared to more fatty and grease-loaded foods like Hot Cheetos and french fries, it seems veggies just taste too...healthy. Which is apparently not a good thing in the eyes of a sugar and salt-obsessed child.

In order to prepare and decorate a Wildlife Safari Cake, you will need to pre-prepare royal icing and a pre-made cake.