Royal icing is the glue that holds ginger bread houses together, so it is very tough. When you use royal icing for cookie decorations it creates a great layer for more decorations. This how to video will show a quick recipe for making royal icing at home. You will need: egg whites, powdered sugar, pipping tips, cream of tartar, and lemon extract.

Forget the take out tonight. Watch this how to video and learn to cook some Korean style food. In this particular video our host shows you how to make Korean style stir fried squid.

Shed those dead skin cells with homemade lip exfoliant. Using safe and natural ingredients, Roni Proter, host of Simply Beautiful, makes a gentle lip exfoliant. All you need is sugar and olive oil. Watch this how to video and you will have smoother, softer lips in no time.

Forget the store bought rhubarb, grow your own in your back yard and use it to make some delicious homemade pies. Watch this how to video as our host shows you how to prepare rhubarb for delicious pie. All you need for this rhubarb pie recipe is: rhubarb, puff pastry, brown sugar, cinnamon, cloves, apples, and canned fruits.

The Lindy Hop is a fusion of many swing dances that preceded it or were popular during its development but is mainly based on jazz, tap, breakaway and Charleston. This how to video demonstrates demonstrates the push break (aka sugar push) with tuck turn variation lindy dance step. This step is fun and easy to do. Follow the steps in this tutorial and you will be dancing the Lindy Hop in no time.

The Lindy Hop is a fusion of many swing dances that preceded it or were popular during its development but is mainly based on jazz, tap, breakaway and Charleston. This how to video demonstrates the push break (aka Sugar Push) lindy dance step. This step is fun and easy to do. Follow the steps in this tutorial and you will be dancing the Lindy Hop in no time.

Impress your family and friends with fried ice cream for dessert! It's warm and crispy on the outside, frozen on the inside. Simply wrap French Vanilla ice cream in bread, dredge in a flour and sugar batter, and deep fry until golden brown. Watch this video tutorial for step-by-step instructions on how to prepare this dessert.

This is a video tutorial on how to make fried ice cream without the frying! Just coat Blue Bunny Homemade Chocolate Ice Cream in a mixture of cereal crumbs and sugar and garnish with caramel sauce and berries.

Eyes: MAC - Creme Shadow (White)

This video shows you how to create a tartan pattern on sugarpaste or fondant. Great for decorating cakes - cool sugar art video!

These two Thai pork dishes are quick and easy to make. You will need pork, oyster sauce, sugar, soy sauce, garlic powder, salt, celery, carrots, mushrooms, and fresh garlic. Watch this video cooking tutorial and learn how to prepare pork chops and stir fry pork from Thai chef Kai.

Hide leftover vanilla bean pods in the sugar bowl, that way you can re use them.

A simple but tasty party snack, these glazed nuts are both sweet and salty with an added spicy punch. For this recipe you will need:

Add mouth-watering flavor to cabbage with this delicious sweet and sour recipe. With just a few ingredients, you'll have a hearty and healthy meal. You will need:cabbage, salt, pepper, tart apples, butter, flour, brown sugar and apple cider vinegar.

This video gives you a recipe for light fluffy crepes. It also shows you a technique for makeing them. You can add you own ingredients once they hit the table, fruit or sugar and cinnamon are always a good addition.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you've read or watched anything Harry Potter before, you know friendship and teamwork are huge parts of the story. The same goes for Harry Potter: Wizards Unite, with its "Wizarding Challenges." Here, you can tackle Fortresses full of Foes alone, but why do that when you can battle with up to four other friends at once? Here's how it all works on Android or iOS.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

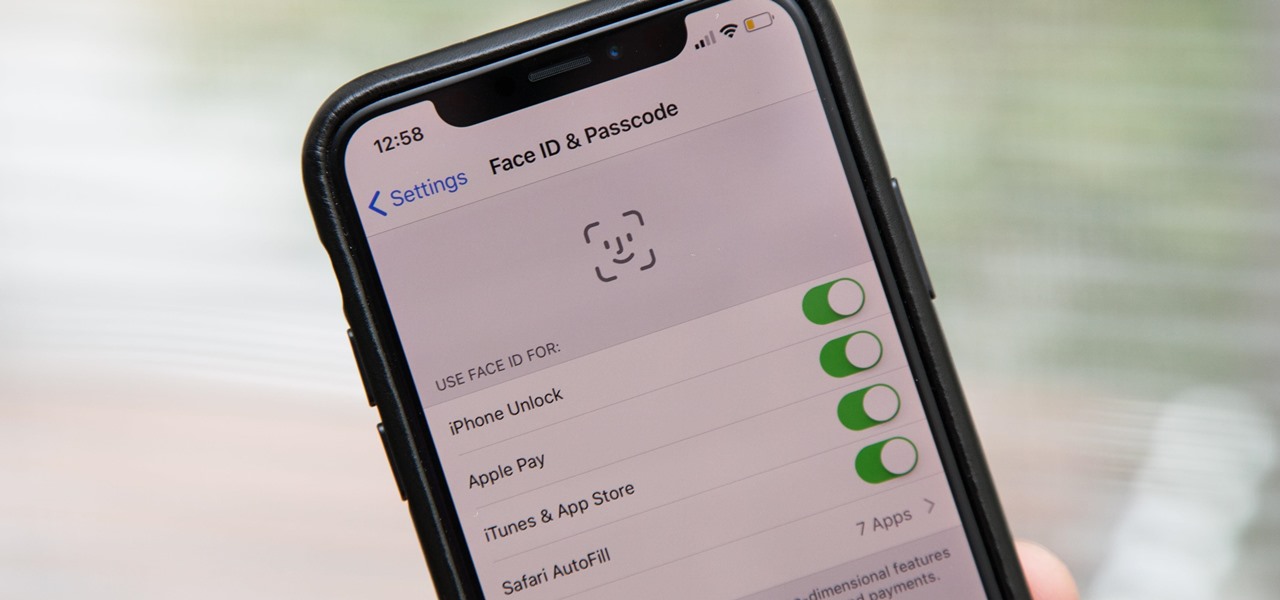
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

With folks drawing lines in the sand before the upcoming election this November, it's important to know where you stand on some of the most important issues: the economy, foreign affairs, domestic affairs, and apples—caramel or candy apples, that is.

Harry Potter fans got a treat last week when Pottermore, a site created by Harry Potter author, J. K. Rowling, released a test that let users learn what form their Patronus protective charm would take.

Starbucks last big hit was definitely their Vanilla Sweet Cream Cold Brew, which became a permanent menu item—not just a summer fling—on May 31, 2016. It's the perfect blend of 20-hour cold brew and vanilla sweet cream; The result not only tastes great, but the cream makes is visually mesmerizing as it floats down through the brew.

From vodka to beer, booze is great for drinking, great for mixing, and, yes, great for cooking with. But there's really no alcohol better for bringing into the kitchen than wine. From savory dishes to sweet ones, wine is so versatile that it can make almost any meal better. And contrary to popular belief, it's easy to cook with.

The decadent, chewy, fresh-from-the-oven brownie is a classic American dessert. US History Scene states that the first brownies ever made were a result of socialite Bertha Potter Palmer's request of her chef at Chicago's Palmer House Hotel in 1893 "to create a dessert that could be tucked into a box lunch for ladies to eat while attending the Columbian Exposition."