At one point in the '90s, about fifty percent of the CDs produced worldwide had an AOL logo. About fifty percent of the CDs in my home still have that AOL promise of 500 free hours on them. Though they never got me to join their internet service, I did get a lifetime supply of coasters. Thanks to the rise of high-speed internet access and bigger and better hard drives, there's no reason for companies to snail mail any more of those obnoxious plastic discs.

Shark jumps Steampunk, experts unsure of the meaning. Cape Town -- In an unprecedented move today, a Shark have jumped a steampunk couple as they were attempting to work on their hobby steamboat.

Lurking inside your old junk microwave is an abundance of useful parts that can let you melt metal, spot weld, and make electrifying Jacob's ladders. You can even make a powerful AC arc welder, perfect for making hard-to-solve puzzles and even makeshift weapons for the zombie apocalypse.

Now that there's a working jailbreak for every iOS 6.1 device, there are more and more people jailbreaking their iPhones (including me) for better customization. But for those of you who have no desire to jailbreak, you can still do some pretty cool tweaks.

Here's how to make dry-ice at home, or wherever you feel like it! All you need is a pillow case, and a CO2 fire extinguisher.

Back in 2007, YouTube user HouseholdHacker posted a parody video on how to make a high-def speaker for under a buck. MythBusters took on the challenge and busted it.

Many people that I know who have gone to see the Hobbit have come back unimpressed or annoyed with the film. I LOVED it. When those non-specific people, cough Loziers cough, gave me their reasons for not liking the movie, I was very annoyed... I considered the demands that they were placing on Peter Jackson and his team to be very high and unreasonable. So, as a method of venting my anger, here is how to watch the Hobbit. If you’ve read Lord of the Rings and the Hobbit, please, go back, and R...

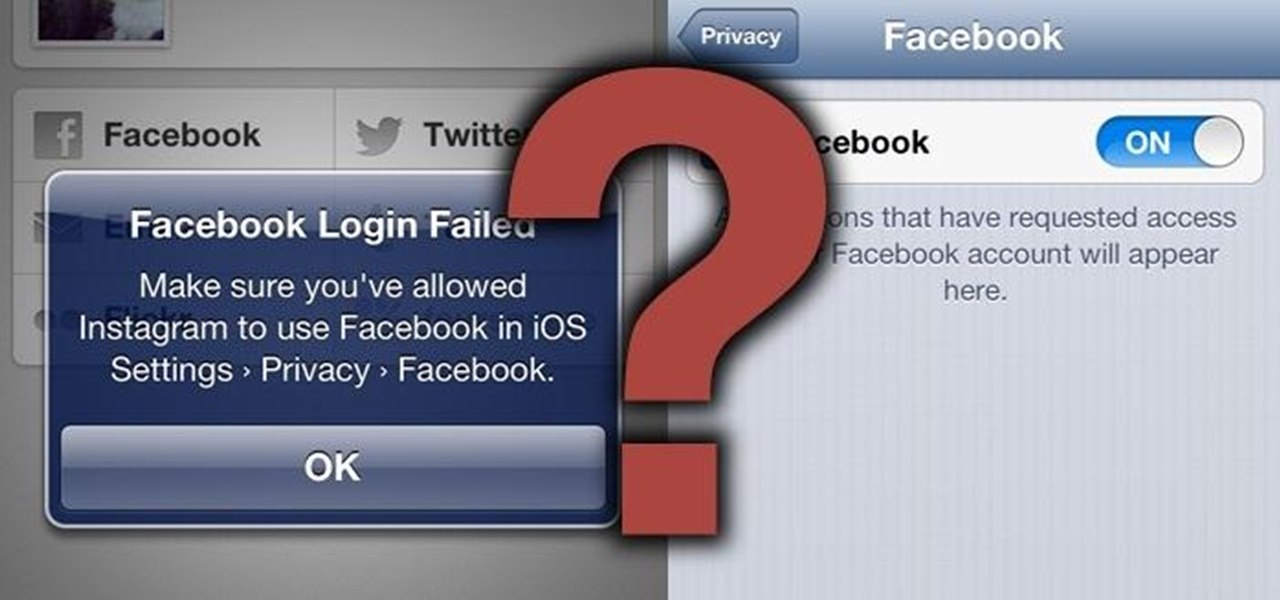
I recently ran into a problem connecting my Instagram app on my iPhone 5 to Facebook, and neither Instagram's or Facebook's help pages were as helpful as they claim to be.

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

You've had your Xbox 360 for a few years now and your game collection is pretty extensive. Maybe it's not that extensive, but it's still substantial. Now imagine that you live in Europe and you're moving to the United States. I don't know why—maybe your dad got a job offer. Don't ask me, ask your parents. They're the ones that are making you move. Anyways, as most Xbox users know, games are coded by region. Games that work in Europe might not work in the United States. Does this mean you shou...

Getting two sticky-pistons to pull eachother, a piston-train, isn't anything new but the pistons and their timing in 1.3 are and there has been alot of QQ-ing on the Minecraft-forums about how bad they are and that Jeb should bring back the old pistons we all know. I, for one, not only welcome out new 1.3-pistons but have also made a small mini-game out of them. A two-player tug-o-war. The players stand on the diamond or emerald area and press a button to make the piston-train take one step t...

It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up the lock.

With the upcycling revolution, folks are turning their otherwise useless junk into something functional for the home. Practically anything that you would normally toss or recycle can be reused for a bigger and better purpose. Your milk jugs, chopsticks, toilet paper cardboard, glass jars, and even your old junk computer keyboards can be upcycled into something totally useful around (or away from) the home.

Redbox recently announced a partnership with Verizon to bring a new streaming video service called Redbox Instant to an already crowded table. No prices have been released yet for the service, but with Netflix, Hulu, Amazon, YouTube, iTunes, and many others all attempting to get a hold of your dollars, what are currently your best options? Subscriptions Services

If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect.

Thermal cooking saves energy costs and preparation time, so why not try out this delicious recipe using a thermal cooker? You'll learn how to make a fruit cake inside a thermal portable cooker, which could get you addicted. Give it a try, see if you're a thermal cooker.

This video shows you how to add a believable reflection to any image using Photoshop. There's no sound so you have to attempt to follow along on your own with the cursor.

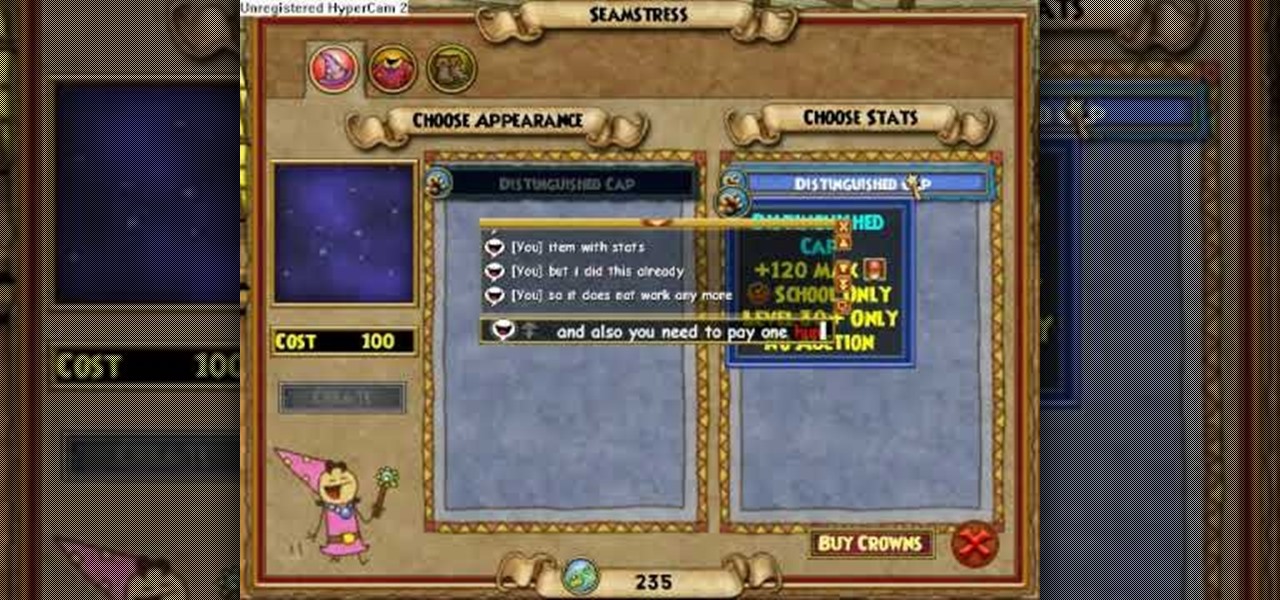
Hemming and stitching in Wizard101? Yep, learn how to stitch itms together and make an awesome wizard-like costume.

Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to get into Nightside without beating streets in Wizard101. You don't have to beat all of the streets to get to Nightside in Wizard City.

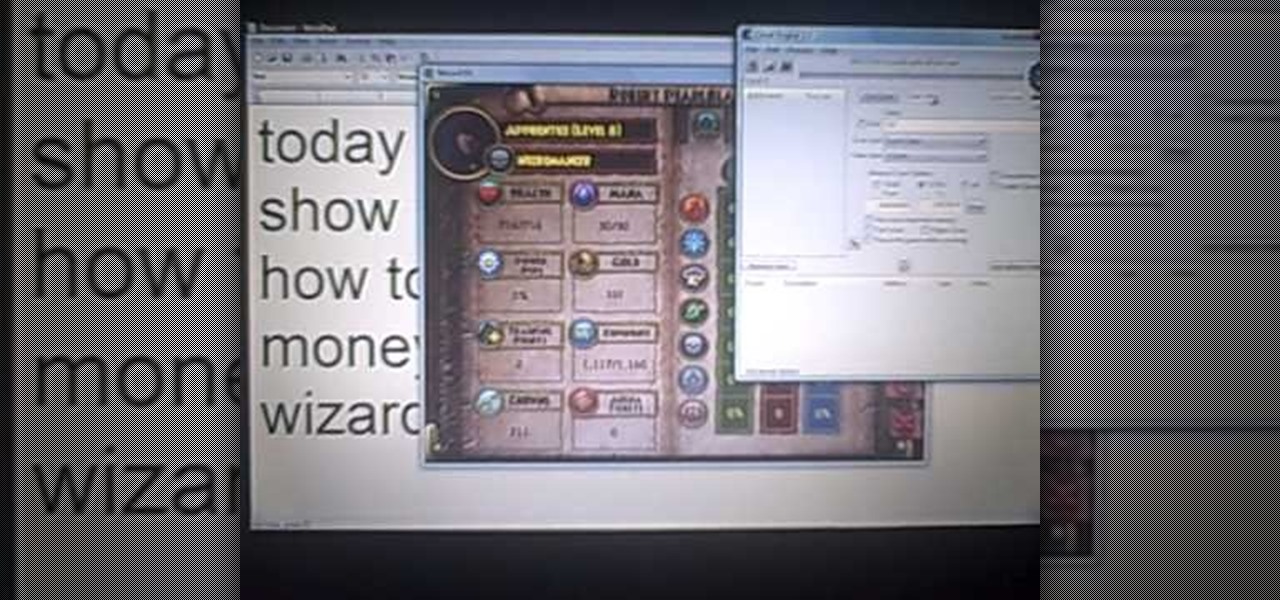
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 money with Cheat Engine (09/27/09).

Check out this tutorial that teaches you how to apply pink and purple eyeshadow drag queen style. You will need Elizabeth Farrell Eye Shadow in Pink, Maybelline Eye Shadow in Lasting Lilac, (Darker Shade), Urban Decay in Polyester Bride, Clinique Lash Doubling Mascara in Black, and Sugar is Good For You Palette. This is a perfect tutorial for drag queens and transexuals. Watch this how to video and you will be able to create a pretty pink and purple eye look.

This four part how to video teaches you more advanced steps of the Charleston. You must have the ability to do the basic steps of the Charleston before attempting the dance steps in this tutorial. Watch this dance lesson and you will be able to do the Charleston in no time.

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Candy is not just for the kiddies. You’re wedding guests will feel like they’re in Candyland when they are presented with the whimsical wonderment of a candy buffet. You can easily match candy to your wedding’s color scheme and theme.

Perform tasks when you’re at your best, hormonally speaking, by scheduling around your menstrual cycle.

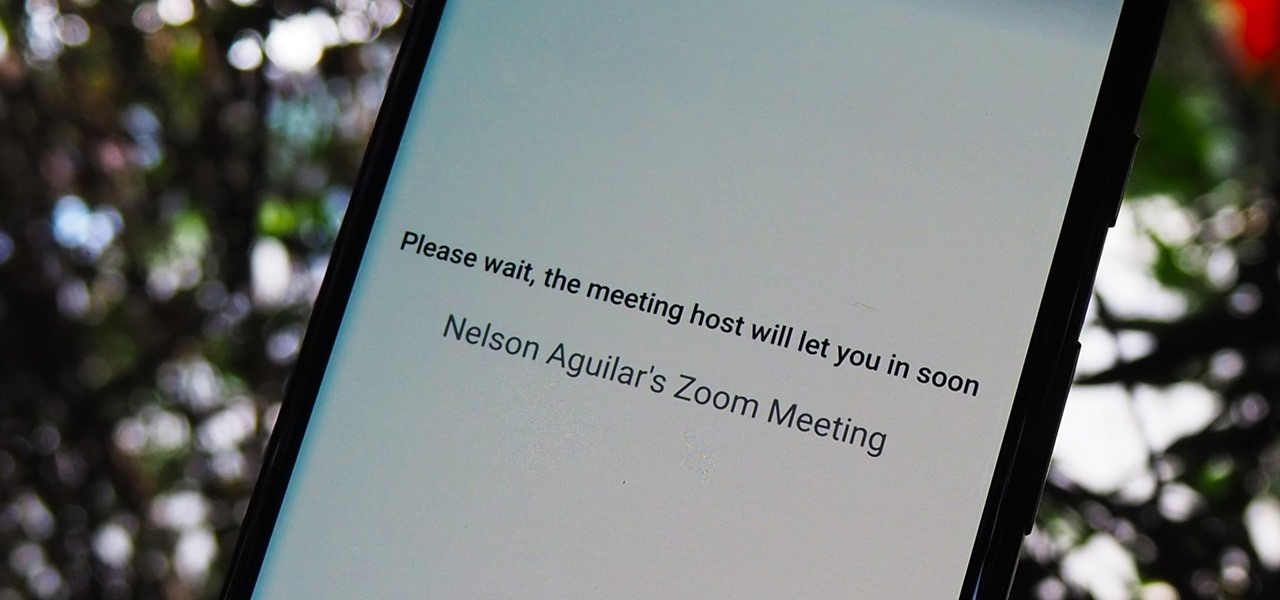
The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Since its debut, retro thriller Stranger Things and its characters have become ingrained in our popular culture — especially the telekinetic Eleven. For cosplayers, it didn't take long before they grabbed their boxes of frozen Eggo waffles, blonde wigs (or bald caps), and pink smocked dresses to transform into El herself.