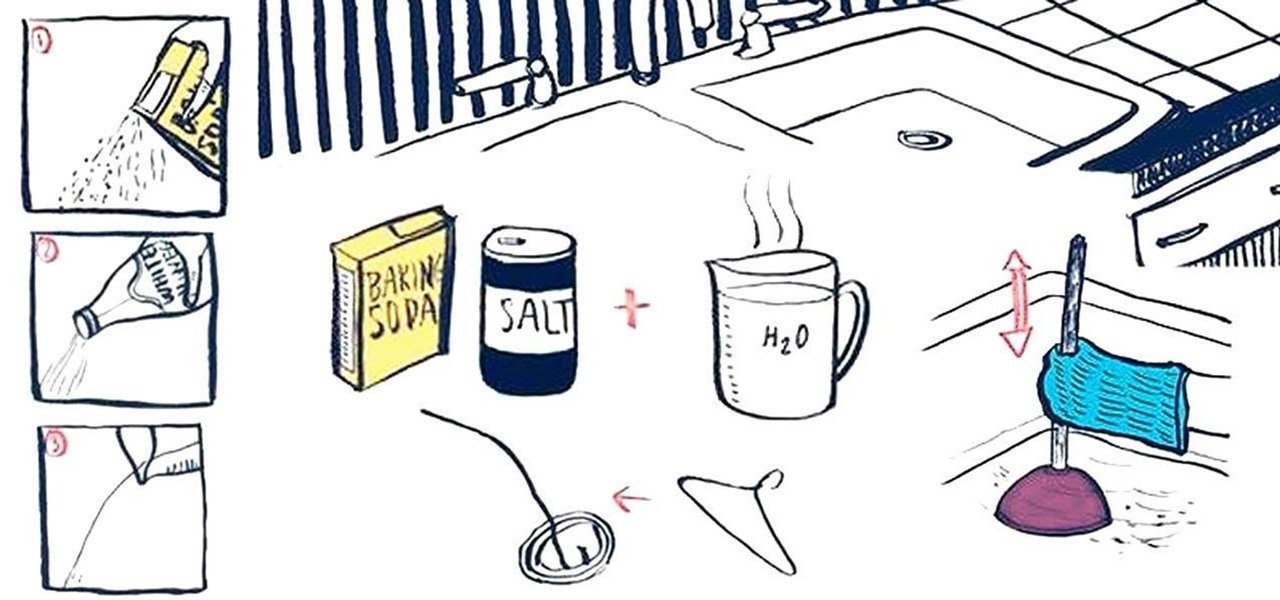
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The New York Times has made a habit of publishing augmented reality stories throughout 2018, and now the media giant's magazine is getting into the act, too.

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

The company behind Japan's beloved Gozilla, Japan's Toho Studios, has for years tried to give fans the sense of what a giant, nuclear-powered lizard invading Tokyo might feel like. Until now, those attempts have been limited to the movie theater, but now, with the help of the Microsoft HoloLens, Godzilla is finally getting its chance to invade the actual city, with terrified fans looking on from a safe distance.

As awesome as the 2017 Galaxy lineup may be, few can forget the monstrous disaster that was the Note 7's exploding battery. Needless to say, the last thing Samsung wanted was another news story about a problem with the Note 8's battery. Unfortunately, that's exactly where we find ourselves today.

Apple is working on autonomous systems for vehicles, which could then be implemented with the help of car manufacturers.

Just over a month ago, the Rubik's Cube world record was smashed by Mats Valk, a Dutch speedcuber, during the Jawa Timur Open 2016. Valk was able to shave 0.16 seconds off the previous record of 4.90 seconds, which was a pretty impressive feat.

It's now common knowledge that the blue light emitted by phone screens makes it harder to get a good night's sleep. Apple's Night Shift in iOS and its steamrolled predecessor, f.lux (still available for desktop computers), are attempts to combat these harmful effects by limiting the amount of blue light from the screen at certain times of day (nighttime, say). For Android users who installed the Developer Preview build of Android 7.0 Nougat, the included "Night Mode" feature was all set to do...

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

According to the American Osteopathic Association, "1 in 5 teens has some form of hearing loss," and some experts believe it's because of an increase in headphones use. While I understand that music, movies, and video games help keep children preoccupied, there's no reason why they can't be entertained at a healthy hearing level.

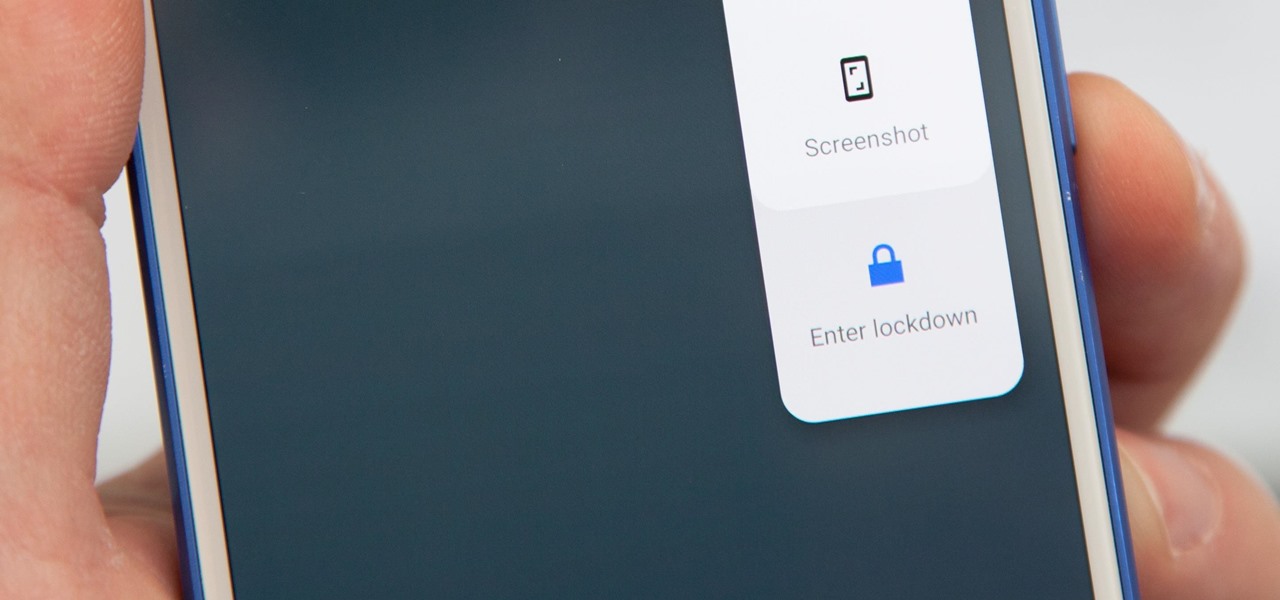
Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

Invented by Philadelphia tinsmith John L. Manson in 1858 for canning and preserving perishables, mason jars are experiencing a major resurgence in the DIY community. In addition to being a handy storage device for both food and non-food items, its old-timey, quaintly antiquated look also makes for good drinking glasses, candle holders, flower vases and eye-pleasing decorations.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

I admit, when the new iOS 5 update for Apple devices was coming out, I had iTunes open all morning with my iPhone 4 attached... waiting... waiting... waiting until finally the new version of iOS was available for download. I stopped everything I was doing and quickly initiated the process of updating my device. After two excruciating hours, my iPhone 4 was finally ready to go and I couldn't be anymore happy. Who needs an iPhone 4S when you've already got iOS 5?

Ah, subscriptions. Whether you love or hate them, they are now a fundamental part of our increasingly digital lives. If you have some essential subs on your iPad, iPhone, or Mac, like Apple Arcade, Apple Music, Apple News+, Bumble, Pandora, Tinder, or YouTube Premium, there are three key issues you need to know about that could unexpectedly stop your membership from renewing.

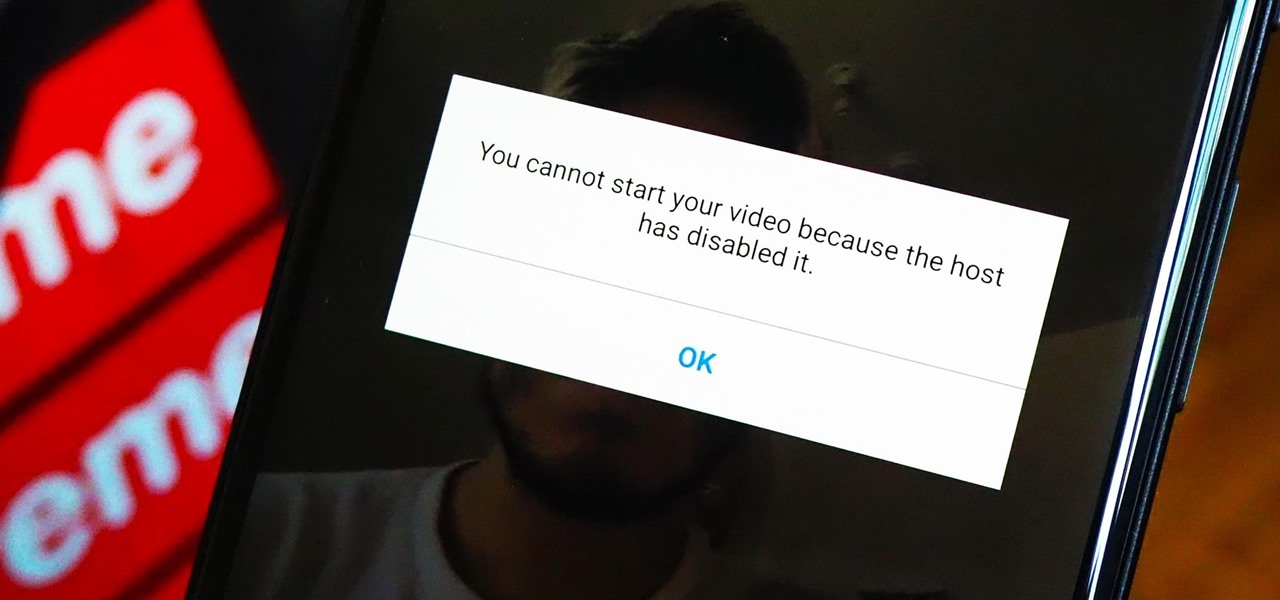
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

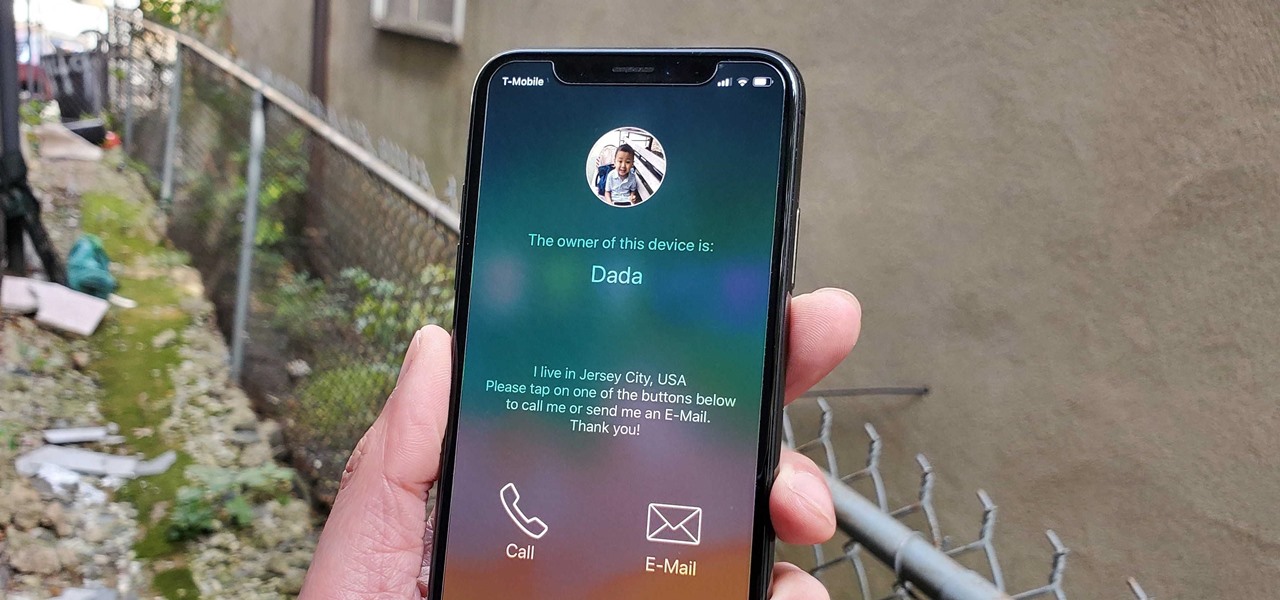
The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

On Monday, the Microsoft Build conference kicked off, showcasing a series of demos that went off without a hitch — except for one big one.

Despite the hype and potential of immersive computing, the augmented reality industry is showing that it is not invincible, as another AR hardware maker, this time Osterhout Design Group (ODG), is reportedly going out of business.

The city of London is getting a holiday gift this season, but it's not the kind you unwrap, since it's completely delivered in augmented reality.

The landscape for mobile augmented reality apps is still mostly filled with utility and gaming apps, but a new entrant into the space is looking to pull children into the mix.

Magic Leap's recent L.E.A.P. conference was free to all who registered in time, but if you weren't able to make the trip to Hollywood, the company just released video of some of the sessions that took place over the course of two days.

You want whales? Ok, you'll get whales! That seems to be the unspoken message from Magic Leap via its latest update in the form of several new experiments posted inside its Helio app.

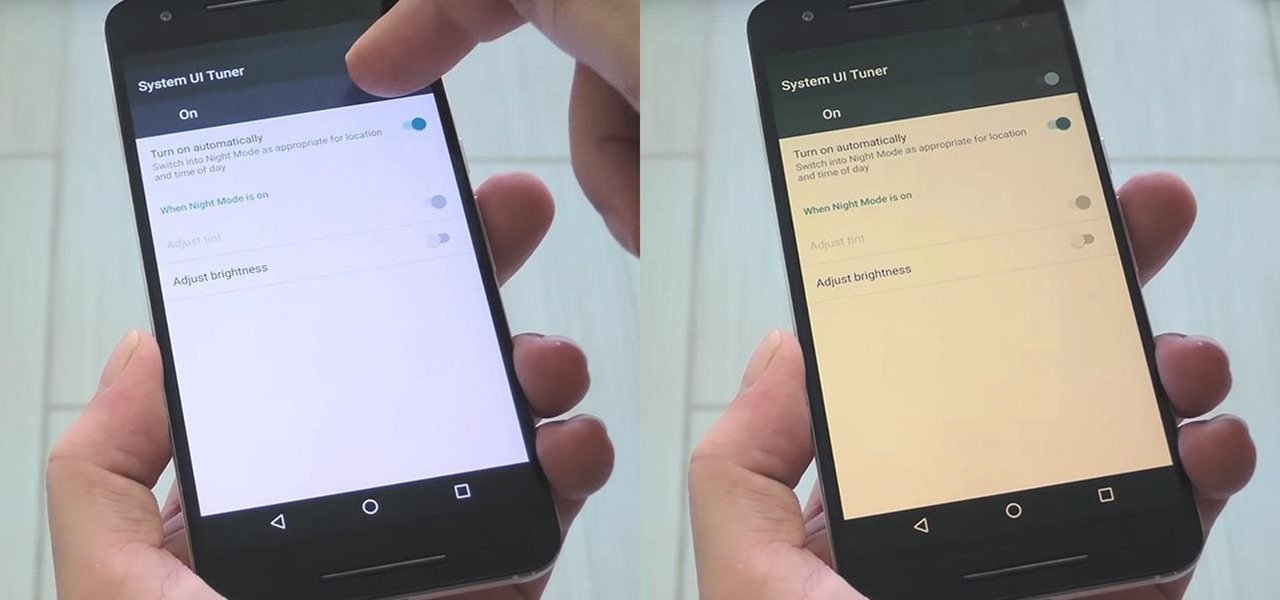
Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

Google updates the Play Store periodically, but the changes are usually subtle. A recent server-side update, however, is shaking things up quite a bit.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

Face ID is possibly the iPhone X's make-it-or-break-it feature. Apple is asking previous iPhone owners to put a lot of faith into their home button replacement, and so far, the results seem pretty good. That is until CNN tested the security feature with identical twins.

A new dating advice site, WittyThumbs, launched today that lets users offer advice to others as well as seek it; the site combines that collaboration with advice from designated dating experts.