What companies do you think have a unique and compelling take on social media? Wendy's is certainly confident, to say the least. But Lufthansa Airlines is taking a different approach than most — and it seems to be working — as they give passengers a look behind the scenes through Snapchat Stories.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

Pennies may only be worth $0.01, but if you want a coin with everyone's favorite donut-eating dad on it, you're going to need to shell out a little bit more.

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

Virtual reality and horror were meant for each other. You'll get all the positive aspects of experiencing a terrifying situation such as excitement and an adrenaline rush, without any of the real-life consequences, like being ripped to shreds by a herd of flesh-eating monsters.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Unless you have a newer iPhone 6S or 6S Plus, the front-facing "FaceTime" camera on your iPhone has a pretty weak, low-res sensor, which means unflattering selfies. You could use the rear "iSight" camera to take a high-res selfie, but framing your mug properly and hitting the shutter is difficult, takes many failed attempts, and usually results in a lackluster photo.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

We've all been there: slipping on a pair of perfect yet slightly uncomfortable shoes, hoping they'll stretch to fit perfectly. After about 30 minutes of wear, suddenly those fantastic shoes aren't feeling very great. By the end of the day, your poor feet are covered in throbbing blisters.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Apple released iOS 8.2 on March 9th for iPad, iPhone, and iPod touch, which contains bug fixes and stability enhancements for certain stock features. If you've updated your device already, you've probably already noticed that you get the new Apple Watch app, too—no matter if you plan on getting a pricey Apple Watch or not.

One of the best things about talking to other people who love food is that they point you to weirdly beautiful ingredients, like this: No, that's not an escapee from Middle Earth you're seeing. It's one of Mother Nature's best attempts at making fractals come alive into a golden spiral: the Romanesco (sometimes called fractal broccoli, broccoflower, or Romanesque cauliflower). Here's another view: So Just What Is It & What Does It Taste Like?

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

The noodle is a noble thing. And while I love ramen and pasta, I have a real soft spot in my heart for macaroni salad (especially the kind that comes with Hawaiian plate lunch) and the type of pasta salad that's dished up during picnics and barbecues.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Ever since its introduction back in iOS 6, AirPlay has been helping us iOS and Mac users stream content over to an Apple TV or third-party speaker system. It's an incredibly useful feature. However, it's also severely limiting. The few compatible products out there are extremely expensive, making wireless streaming a not-so-easy task.

Here's a technique I used to whip up a batch of super cheap and easy to make smoke flares! WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of this video content is at your own risk.

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

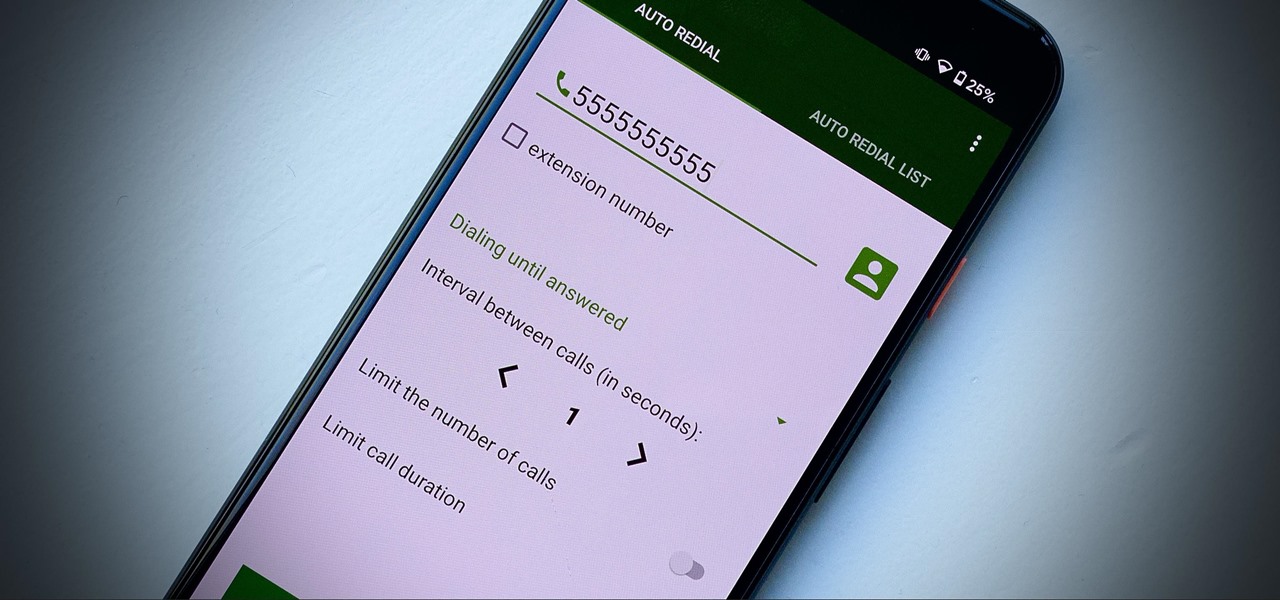
Some phone lines make it nearly impossible to get past the busy tone, whether it's a viral call-in giveaway, your state's unemployment office, your local post office during the holidays, or the repair office for a broken warrantied product you have. Thankfully, there are apps you can use to help break through the noise.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

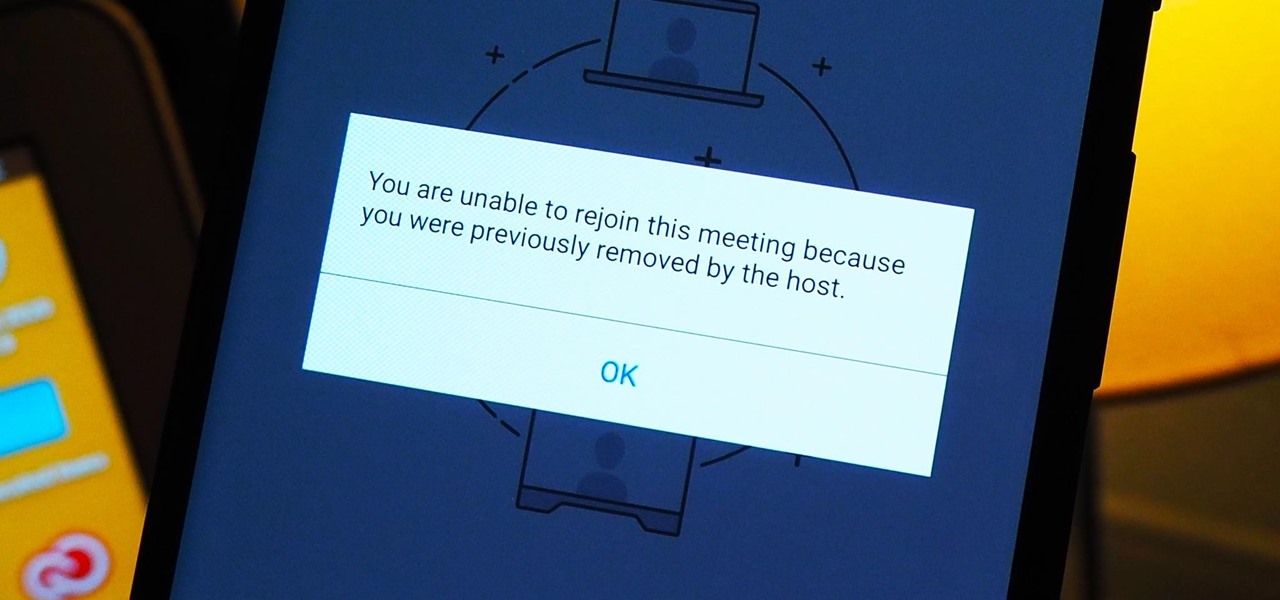
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

One Instagram creator's augmented reality homage to Disney's deep bench of animated characters has earned him fifteen minutes of fame.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.

If you're hungry for pizza and ordering from Domino's in Australia, you can now see what your pie will look like in augmented reality before placing your order.

Now that we've had a few days to recover from the VR geek versus augmented reality nerd battle between Oculus founder Palmer Luckey and Magic Leap founder Rony Abovitz, we can get back to taking a closer look at the Magic Leap One. This time, we take a very brief dip into the Abductor app.

Starting in iOS 11, Apple introduced a QR code scanner for iPhone that's baked right into the Camera app, reducing the need for a third-party scanner. However, not everyone knew it existed, so a lot of users were still using third-party QR code scanners. In iOS 12 and later, Apple addressed the issue, making theirs much more visible, as well as improved QR code scanning in general.

We've seen all the Magic Leap One glamour shots, and we've even shown you a bit of what it looks like to view augmented reality on the device. But there's something else us super geeks appreciate more than anyone else: the grand unboxing!

Last week, the first possible image of the upcoming OnePlus 6 leaked. It was met with mixed reactions, most notably for its apparent iPhone X-style "notch." OnePlus fans seem concerned that the company is implementing a design choice based on what it thinks is trending, not necessarily what's best for the product. If you're one of those uneasy about OnePlus' future, don't be. At least not yet.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.