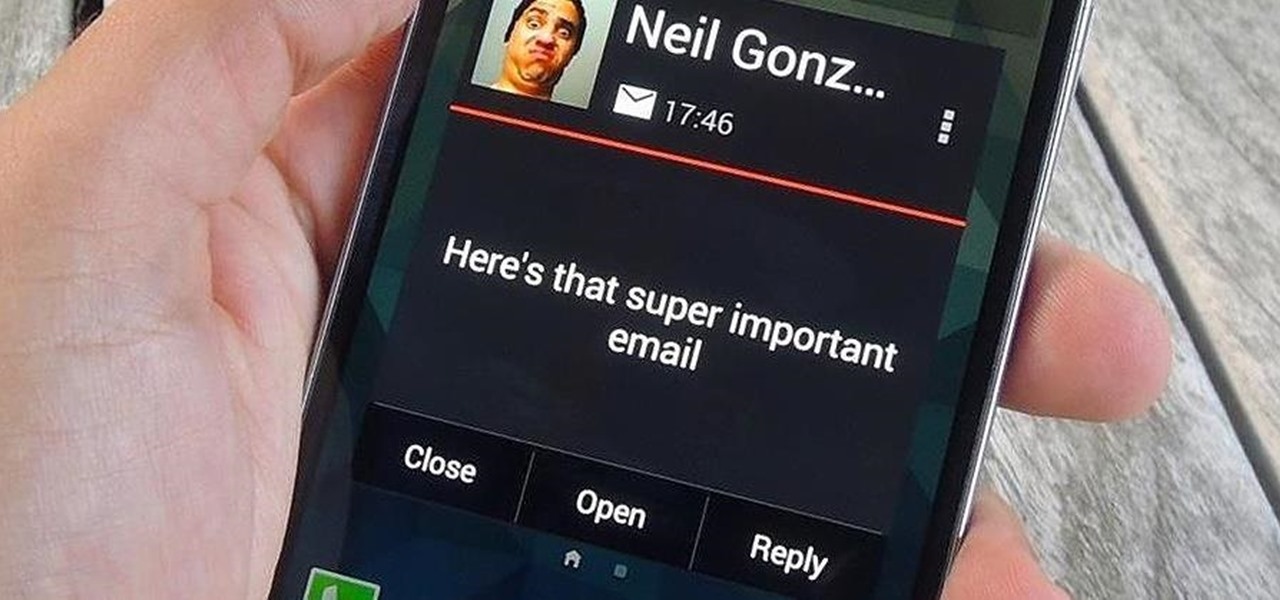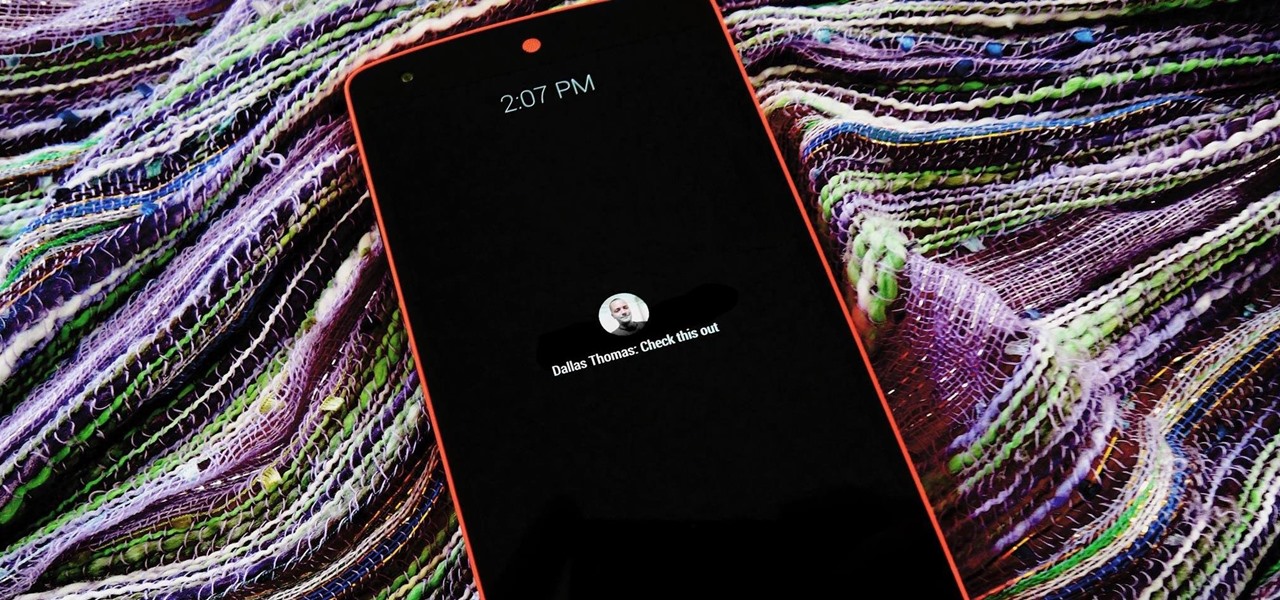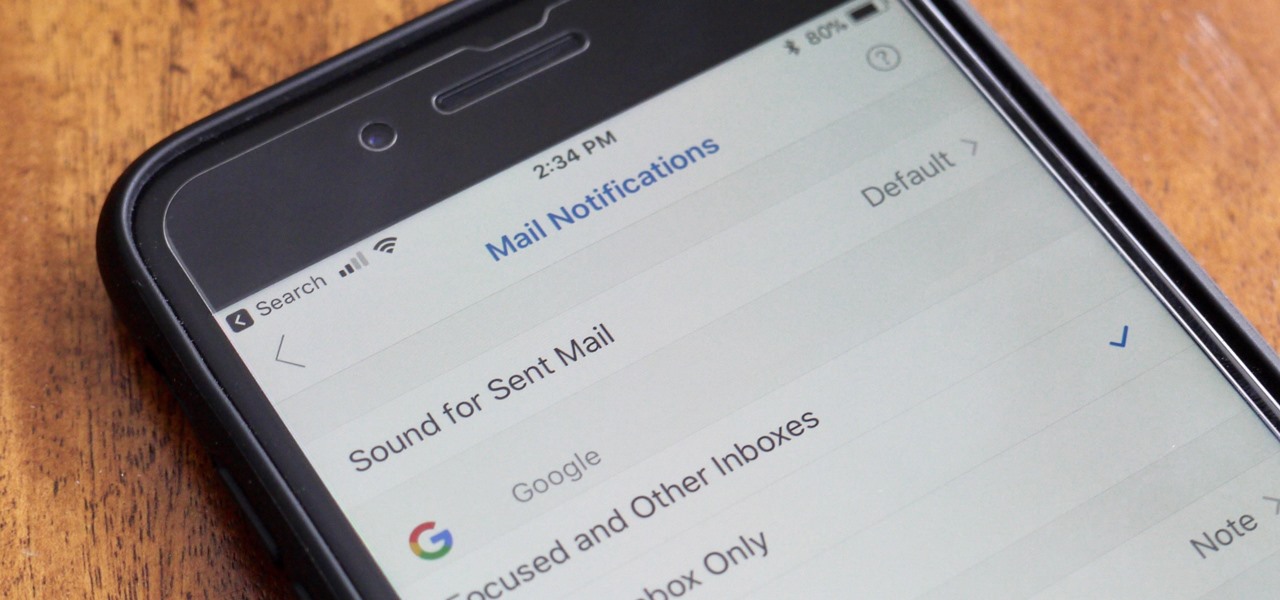
With email, one size does not typically fit all. You have multiple email accounts, each for different purposes and with varying levels of importance, so it only makes sense to customize the way your phone alerts you to each account's incoming emails. Luckily, Outlook allows you to do just that.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

Results of an early-stage clinical trial of an HIV vaccine could mean a hoped-for breakthrough in the battle against AIDS.

So it's 2017 and there are no flying cars and teleportation devices around, but there might be holographic smartphones sometime soon. As cool as that sounds, should we trust a holographic smartphone from a company that has never made smartphones before?
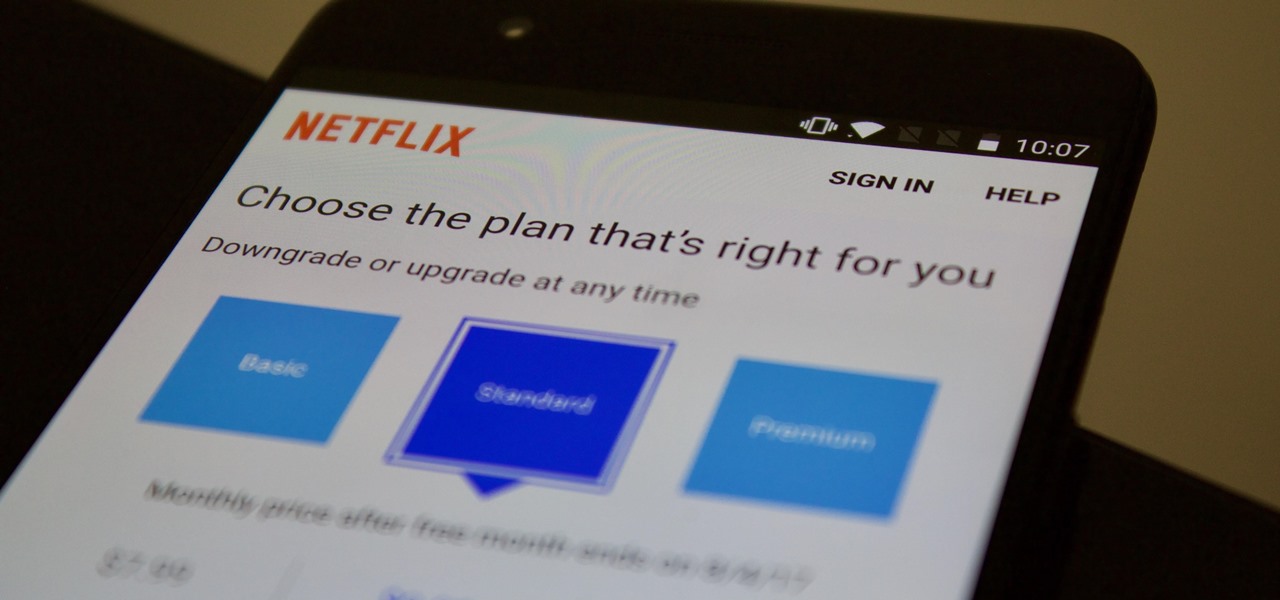
Netflix offers three different tiers of service. The good news is that no matter which subscription plan you choose, the available content is the same. Whether you choose the cheapest plan or the most expensive, you'll be able to watch any TV show or movie in Netflix's library. But there are other things to consider when choosing the plan that's right for you and your smartphone.

We were really rooting for you this time, BlackBerry! With the phone company having minimal success in the past with smartphones, the BlackBerry KEYone was extremely promising. That is until YouTube Reviewer JerryRigEverything discovered a fatal flaw, the phone's screen popped off with just a bit of pressure and then stopped working. So...there's that.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

Samsung's new personal assistant, Bixby, is making its debut on the Galaxy S8 and S8+. In addition to taking voice commands and performing visual searches, a new Hello Bixby feature predicts what you might want to do next with an integrated home screen feed. All of these features look nice, but if you're not ready to shell out at least $750 for a new phone, you'll be glad to know that Hello Bixby just leaked.

The Galaxy S8 and S8+ haven't even hit shelves yet, but some of the stock apps from Samsung's latest flagships have already been leaked. The biggest one so far is the new Samsung Experience Launcher, which replaces TouchWiz Home, and is quite a bit different from anything you'll find on previous Galaxy models.

Huawei is making a fresh attempt at launching into the US market to challenge Apple and Samsung's monopoly on premium smartphones. In its latest attempt to break into America, Huawei is trying to get its Chinese mobile chipset accredited by AT&T.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

The brand new Pixel and Pixel XL, Google's first direct attempts at taking on the iPhone, haven't rolled out exactly how Google would have liked. The devices have already had more than their fair share of issues, starting with the camera, and now extending to the built-in speaker. The camera issues were marked as "solved" by Google, but the lens flare is still very much there, just not as prominent.

There's no question about it—Skype is one useful program, but has always been lacking in the mobile department. On your desktop, Skype works just fine and all of its options are available for usage. However, the same cannot be said for Android. On Android, you can't even change your status to "Away" or "Invisible."

There's not much you can do to customize the look and feel of your iPhone's home screen, at least when it comes to official options provided by Apple. But thanks to a new bug discovered by YouTuber iDeviceHelp, you can now hide text labels for app icons and folders on your iPhone or iPad, and this hack doesn't even require a jailbroken device.

The reviews for the Google Pixel phone have hit the web. There's a lot of praise, but not all are so positive. We've collected some of the best takes on the new devices from the top tech sites around.

You can easily take audio for granted in virtual reality, but realistic sound in VR isn't an afterthought. It not only involves creating surround sound within a pair of headphones, but figuring out where the sound ought to exist based on your position and line of sight.

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

If you spend weekend mornings sadly turning your omelet attempts into scrambled eggs rather than enjoying a perfectly flipped omelet, reach for a resealable plastic bag. Using a ziplock bag to make an omelet is not only foolproof, it's the perfect solution to cooking for a crowd, where you can make everyone's customized omelets at the same time. How cool is that?!

Not content with bringing the first untethered mixed reality headset to market, Microsoft wants to expand their Windows Holographic operating system beyond HoloLens into vastly more robust technologies.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

For the past couple of years, random internet dwellers have embarked on an ambitious quest to see just how useless a box can be in hopes of earning sweet, sweet internet points. Welcome to the world of useless machines.

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

Believe it or not, but people are actually texting less than they did before, and that's all thanks to Facebook Messenger, Snapchat, WhatsApp, and other split-second communication services. However, one communication method that is still going strong—and dominating—is email.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

The act of viewing a new notification on your Nexus 5 can feel a bit clunky and cumbersome at times. When a new message comes in, you hear the notification sound, you see the LED blinking, but you can't see what the actual notification says without waking the device and opening the notification tray.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

The final chapter of Christopher Nolan's Batman trilogy is here, The Dark Knight Rises, and if you're anything like me, it made you want to immediately don a cowl of your own and run around punching criminals. Don't forget though, one of the most awesome aspects of Batman is his never-ending supply of crazy gadgets. Unfortunately for most of us, we don't have a billion dollars, nor Morgan Freeman, so we'll just have to make do with some good old-fashioned DIY tricks. Read on for a rundown of ...

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

There's no denying that native Dark Mode in iOS 13 is awesome. Stock apps that were blindingly white for over a decade can now be comfortably used in the middle of the night. You might find, however, that some of your third-party apps aren't taking the hint. Why won't YouTube switch to dark mode when iOS as a whole does? We put together a troubleshooting checklist to get your apps cooperating.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.