
Hack the News: Build Your Own Media-Altering Newstweek Device
At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.


At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

In this video the instructor shows how to check if your computer has a home group setup or setup one if required. Home group is Microsoft's new way of making networking easier with computers. They allow you to share documents, pictures, videos and all kinds of media between computers that are a part of a home group. Go to the start menu and go to Control Panel. In the Control Panel select the Network and Internet link. Now in the Network and Internet window select the Home group. In this page...
Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.
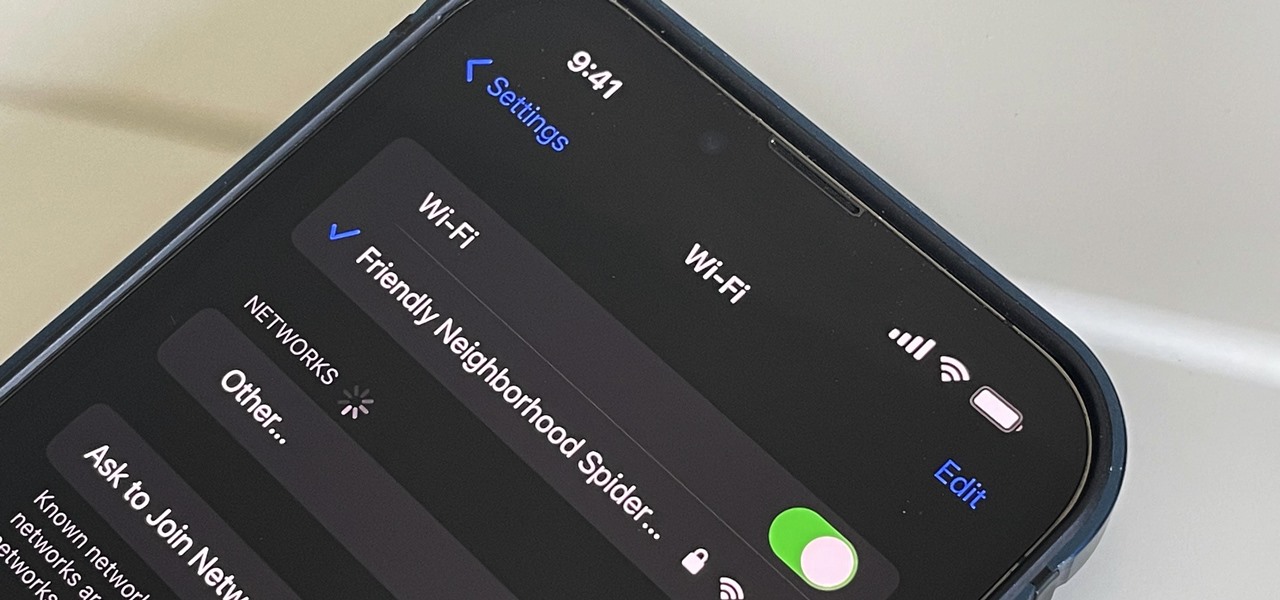
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.
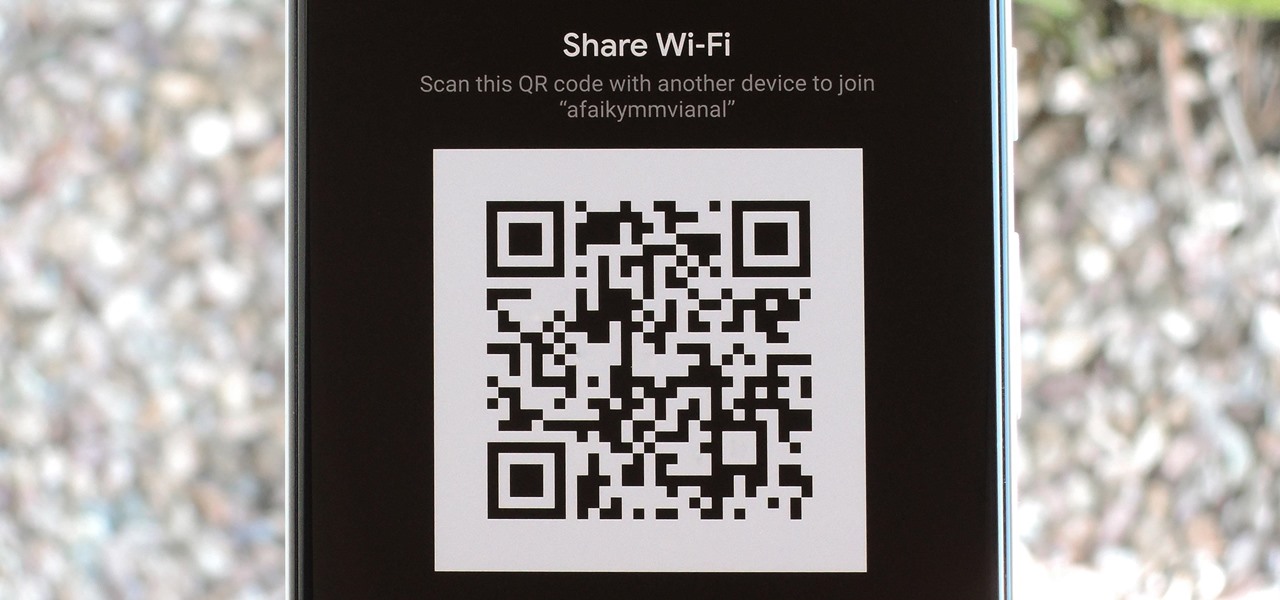
If your phone is running Android 10, you can now share your Wi-Fi network with friends using a handy QR code. The other person doesn't have to be running Android 10 — in fact, you can even share this code with iPhone users. In most situations, this is now the fastest way to share your Wi-Fi password.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

5G is showing up more and more in the news, as an increasing number of companies jump on the bandwagon. AT&T made a splash earlier this year with their embarrassing "5G Evolution" debacle, and the other three major wireless carriers soon followed suit, detailing their own vague plans for 5G. Today we find another company has joined the fray, just not a cellular one — Apple has officially been approved to test 5G networks.

Shapr is a new networking app that aims to help professionals connect more efficiently, and draws much of its format from dating-focused social networking apps. Shapr could be especially useful for those who have recently moved into their industry or location, and for those seeking employers or employees. For example, the app already has 65,000 users just in New York City alone.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Five Phases of Hacking:- The five phases of Hacking are as follow:

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

I am very new to Null Byte but I find much of its content and community incredibly interesting. I spent quite a bit of time just chronologically going through the posts and I noticed a common theme in many of the beginner posts. Many people seem to want to know the 'secret' or a paragraph on "How to Hack" and become a hacker in a few minutes. I started off this post as a reply to a question from a beginner but thought it might be beneficial to have for those stumbling across this site.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.
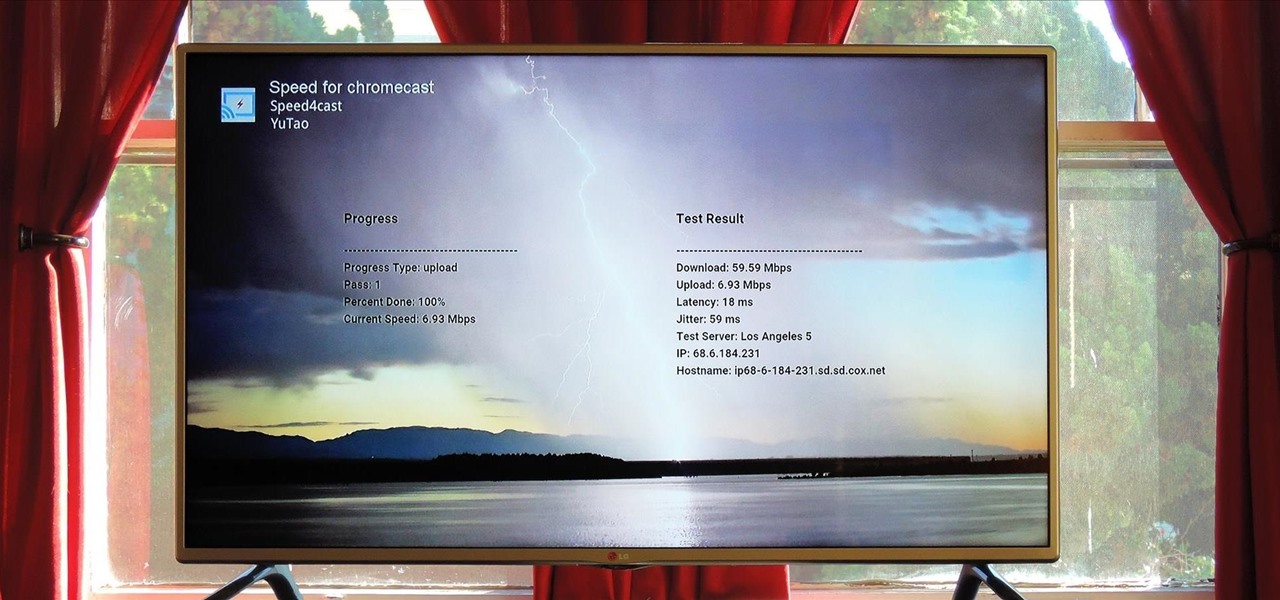
At its core, the Chromecast is essentially a web browser on a stick. When you cast content from your computer or smartphone, all you're really doing is telling the Chromecast which website to load.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Why unlock your Samsung Galaxy S3 to use with a different SIM card? One possible reason is that you love your phone, but not your cellular provider because of the poor service or an unreliable connection. If you purchased a Samsung GS3 with AT&T, T-Mobile, etc. on a contract, it might be locked for a specific amount of time called the contract period.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

With the new year right around the corner, it's time to talk about the end of the 19th century, a time which plays an enormous role in Steampunk. If you've done any reading of British books written from about 1890 to 1899, you may have come across the phrase 'fin de siecle' and wondered what it meant. You also may have come across this term in reading about the late Victorian era. No worries, I'll tell you all about it! Image by Giovanni Dicandia
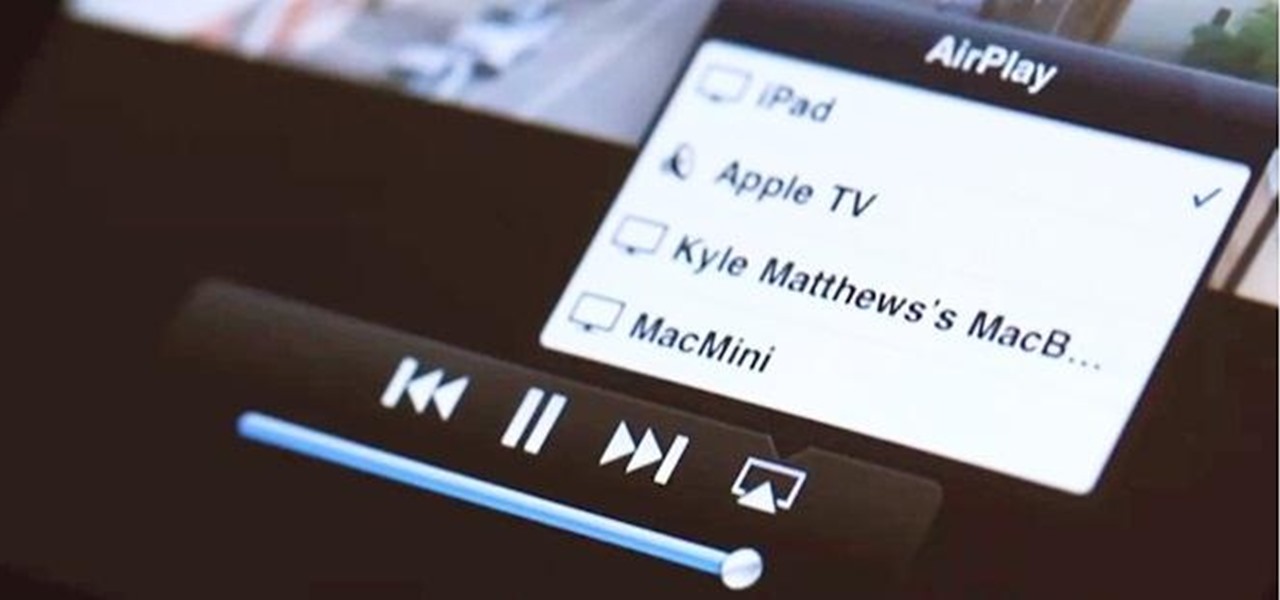
AirPlay is probably one of the most underutilized features in Apple products. It allows users to wirelessly stream photos, music, or video directly from their iPad, iPhone, iPod touch or Mac to their Apple TV or AirPlay-supported speakers. The Apple support page has a complete list of all the supported and needed devices. Mirroring is also available, but only for the iPhone 4S, iPhone 5, and iPad 2, all of which need to be running iOS 5 or later.

Matt describes the necessary steps to take before you begin to build your infrastructure. Find business and design requirements.

Learn how to improve wireless networking on Verizon's FiOS Router. You'll see some easy tips on how to improve wireless networking with the MI424WR Verizon FiOS Router, by Actiontec.
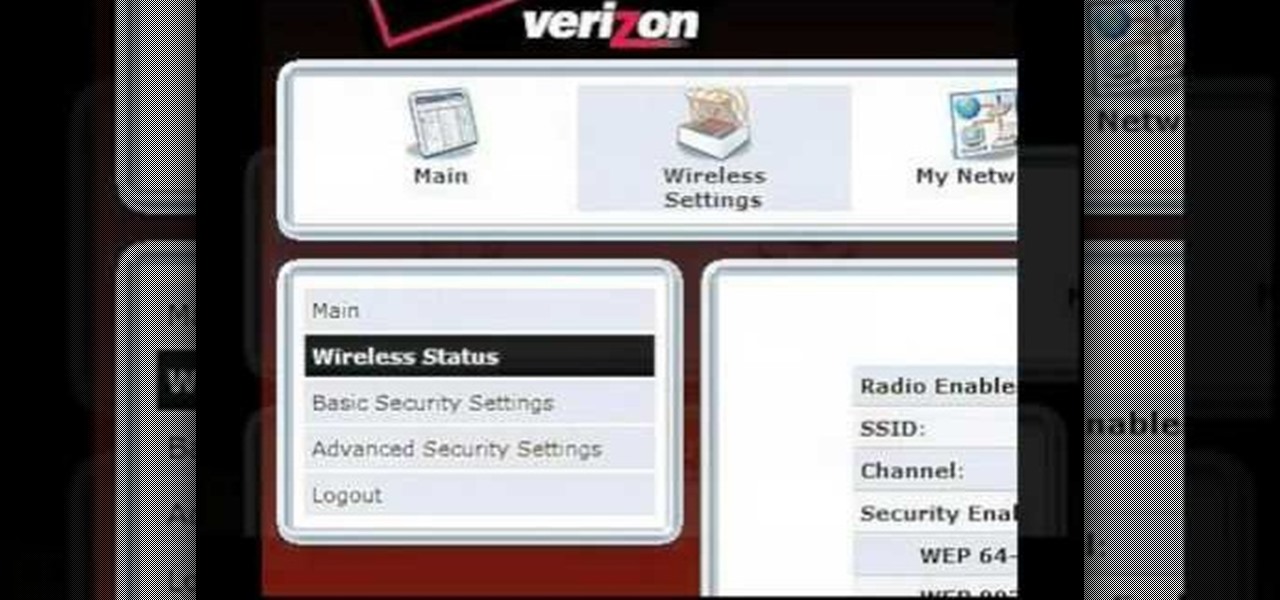
Learn how to change your wireless network name on Verizon's FiOS Router. You'll see the easy steps on how to change your wireless network name and / or password for your MI424WR Verizon FiOS Router, manufactured by Actiontec Electronics, Inc.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
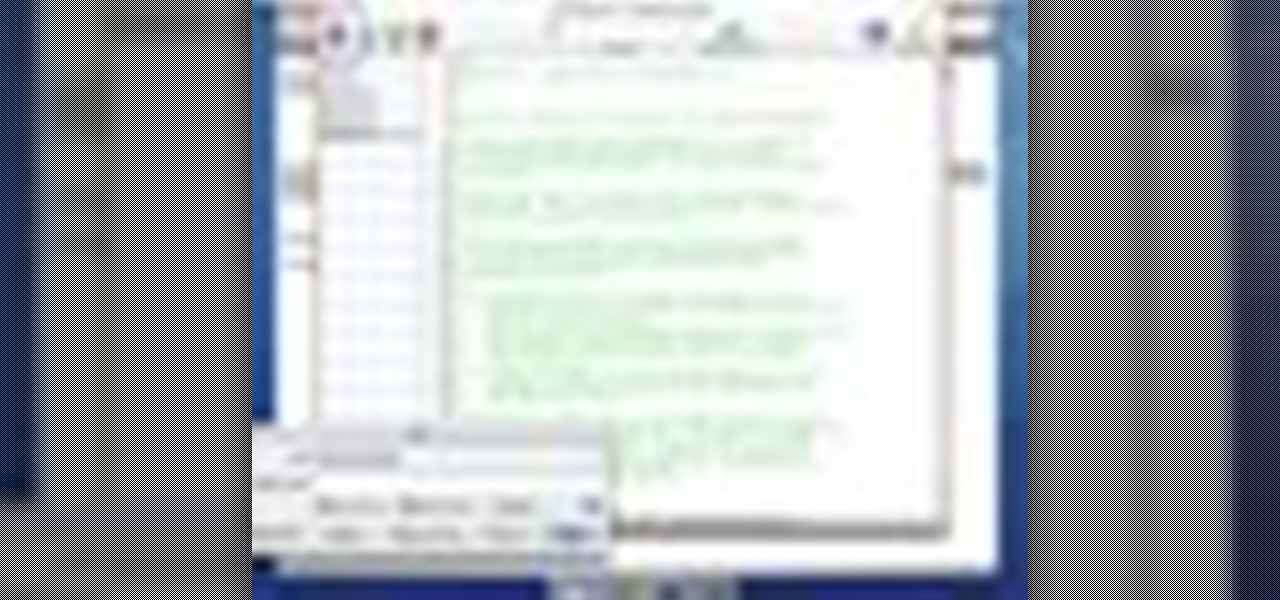
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
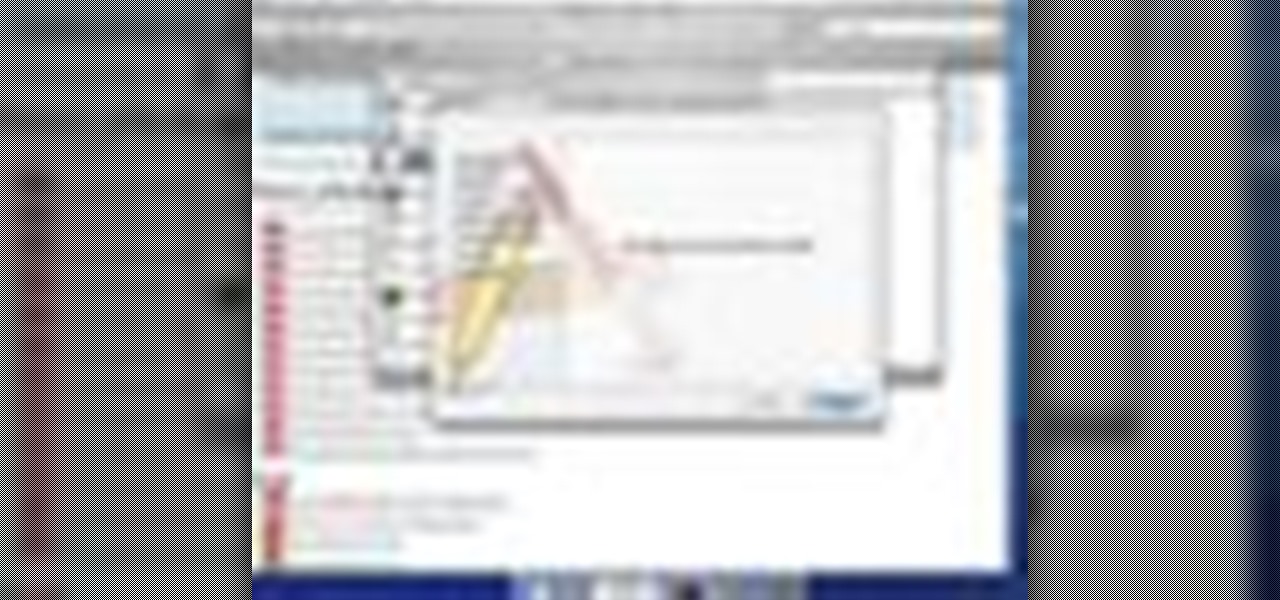
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
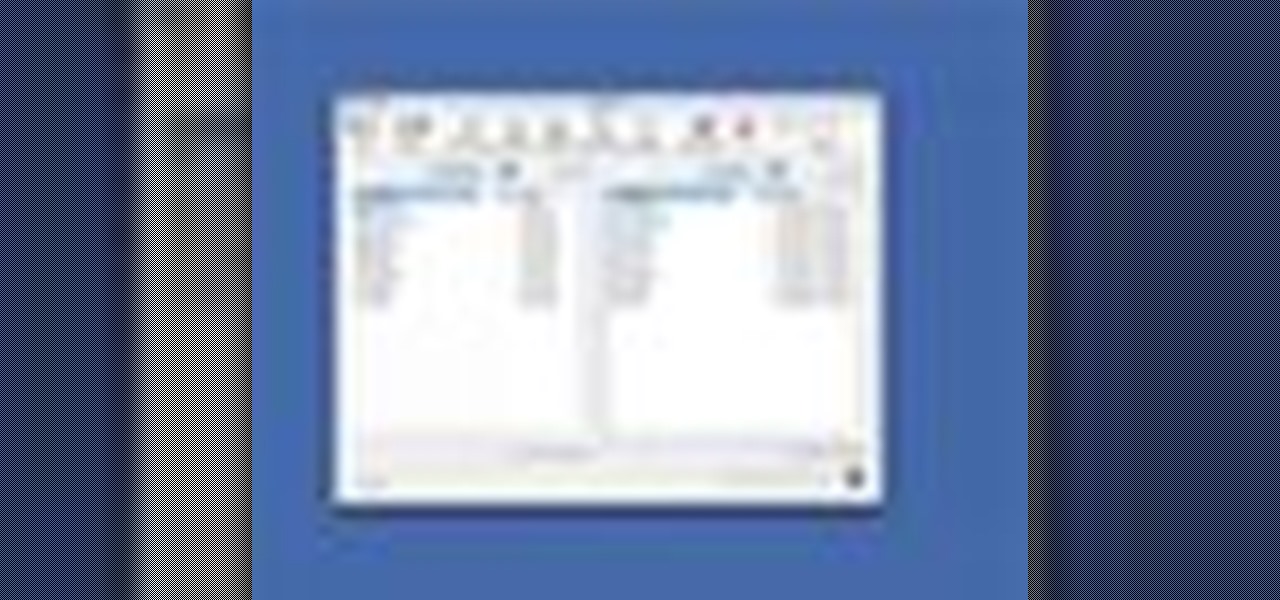
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.
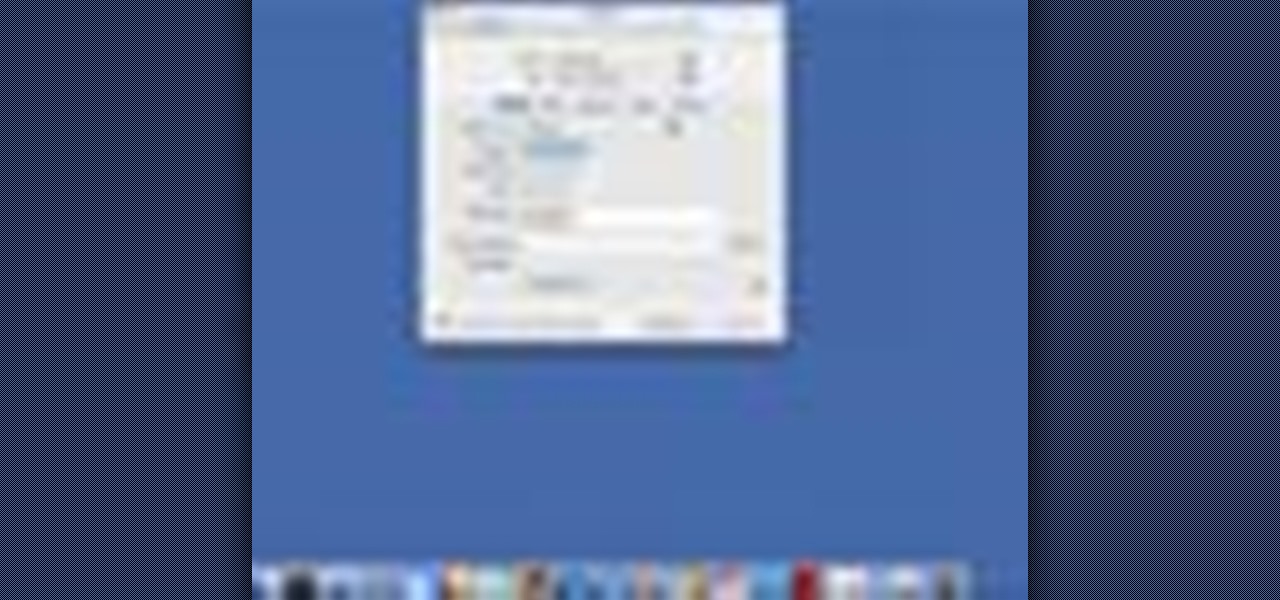
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.