
How To: Use a wasp and dremel to etch concrete
Watch this video from the Concrete Network to learn how to uses wasps and dremels to make designs in concrete.


Watch this video from the Concrete Network to learn how to uses wasps and dremels to make designs in concrete.

Watch this video from the Concrete Network on proper use of the notched squeegee & spiked roller to apply epoxy floor coatings.

Watch this video from the Concrete Network to learn proper use and function of concrete grinders on decorative concrete floors.

Watch this video from the Concrete Network to learn how to use the turbo roller tool to apply concrete overlays & toppings to patios, walkways & floors.

Watch this video from the Concrete Network for tips & techniques for using a concrete trowel, magic trowel, skimmer, or squegee to apply overlays.

Tampers are used to push large aggregate and rocks into the concrete surface. Watch this video from the Concrete Network to learn how to use this tool to place concrete that has large aggregate or what is called a harsh mix.

Squeegee vacuums are used after water or liquid is used to clean concrete. Watch this video from the Concrete Network to learn how to vaccuum wet surfaces in preparation for finishing.

Watch this video from the Concrete Network for tips on using the Mongoose concrete cutting machine to cut intricate designs in concrete surfaces before coloring.

Pump sprayers are used to apply stains & sealers to decorative concrete surfaces. Watch this video from the Concrete Network to get various tips & techniques on selecting the right sprayer for each type of job.

Watch this video from the Concrete Network to learn how to clean & maintain concrete with this high-speed propane burnisher. Scrub & buff concrete surfaces to restore the original shine.

Watch this video fromt the Concrete Network to learn proper function and use of the vibratory plate compactor tool for preparing the concrete subgrade before placing the concrete. This is done to provide a stable foundation for the new slab as well as provide drainage.

An overhead projector can easily be used to transfer high-end graphics onto a concrete floor in preparation for saw cutting or coloring. Watch this video from the Concrete Network to see how.

Watch this video from the Concrete Network to learn the proper function and use of the moisture test, calcium chloride test, and pH test when pouring a concrete overlay or epoxy.

Watch this video from the Concrete Network to learn the proper function and use of the mix-n-go tool, which is used to mix small amounts of concrete.

Watch this video from the Concrete Network learn how to use a Micro-Fiber mop tool to apply floor wax to concrete.

Watch this video from the Concrete Network to learn the proper function and use of the laser level or builder's leveling tools for forming a concrete slab.

Watch this video from the Concrete Network to learn the proper function and use of the hopper spray gun tool.

Watch this video from the Concrete Network to learn how to use the different types of hand floats and darbies. This video includes tips on selecting the proper trowel and an explanation as to why each concrete finishing tool is used.

Watch this video from Concrete Network to to learn the proper function and use of the gauge rake and smoothing paddle tools used for leveling concrete.

Watch this video from the Concrete Network to learn how to use the come-a-long concrete tool to push and pull concrete into place.

Watch this video from the Concrete Network to learn the proper function and use of the fresno tool.

Watch this video from the Concrete Network to learn how to use a variety of edging tools including hand, combination and walking edgers.

Watch this video from the Concrete Network to learn how to use the cut-off saw, used to cut control joints in concrete in order to prevent cracking.

Watch this video from the Concrete Network to learn the proper function and use of handheld concrete grinders and blades, used for making detailed cuts in concrete.

Watch this video from the Concrete Network to learn how to use high end decorative concrete tools, grinder and blades.

Watch this video from the Concrete Network to learn how to properly use the baracuda and shark air driven tools to engrave grahics into concrete.

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...
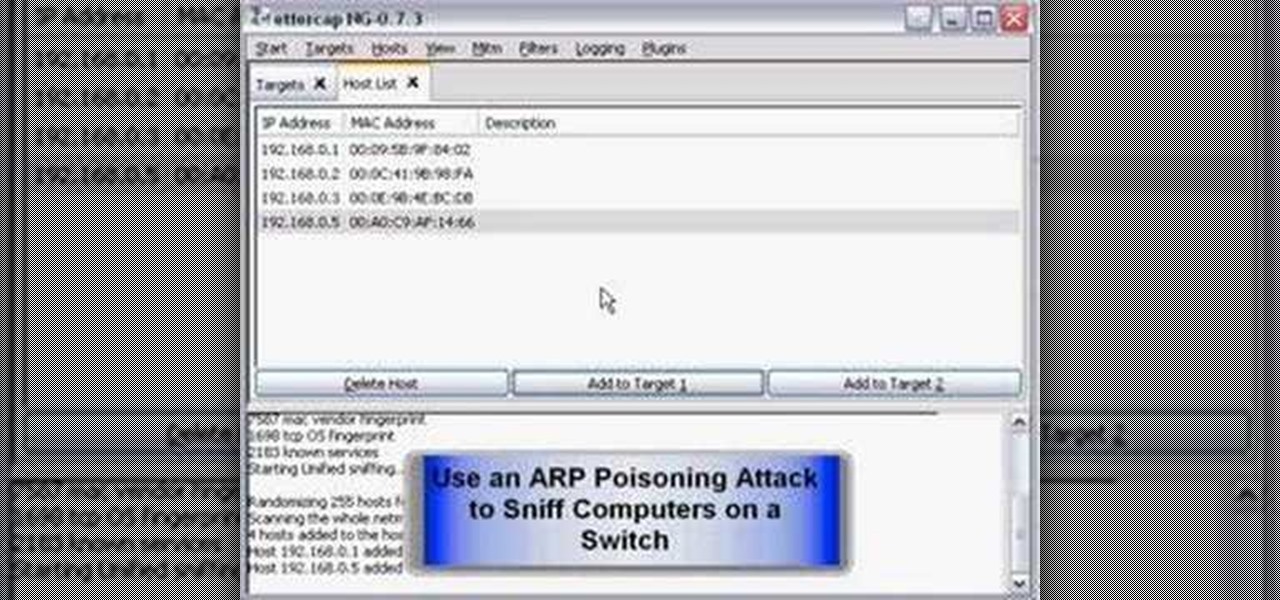
How to hack a network by sniffing passwords with Ettercap software.
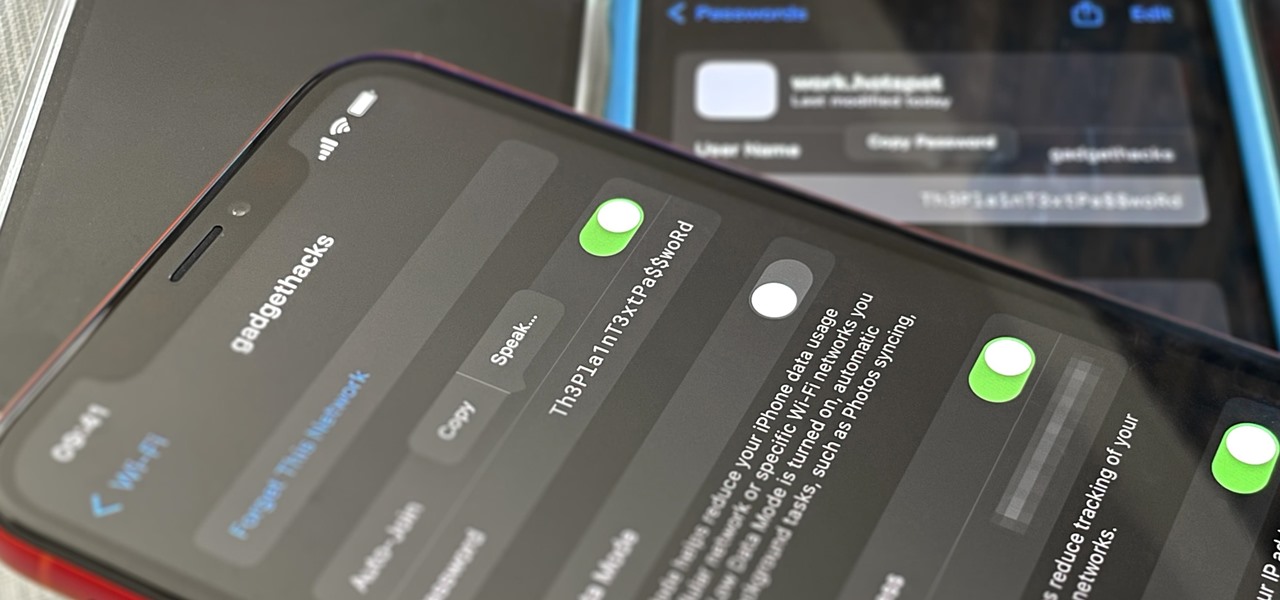
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.
So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.