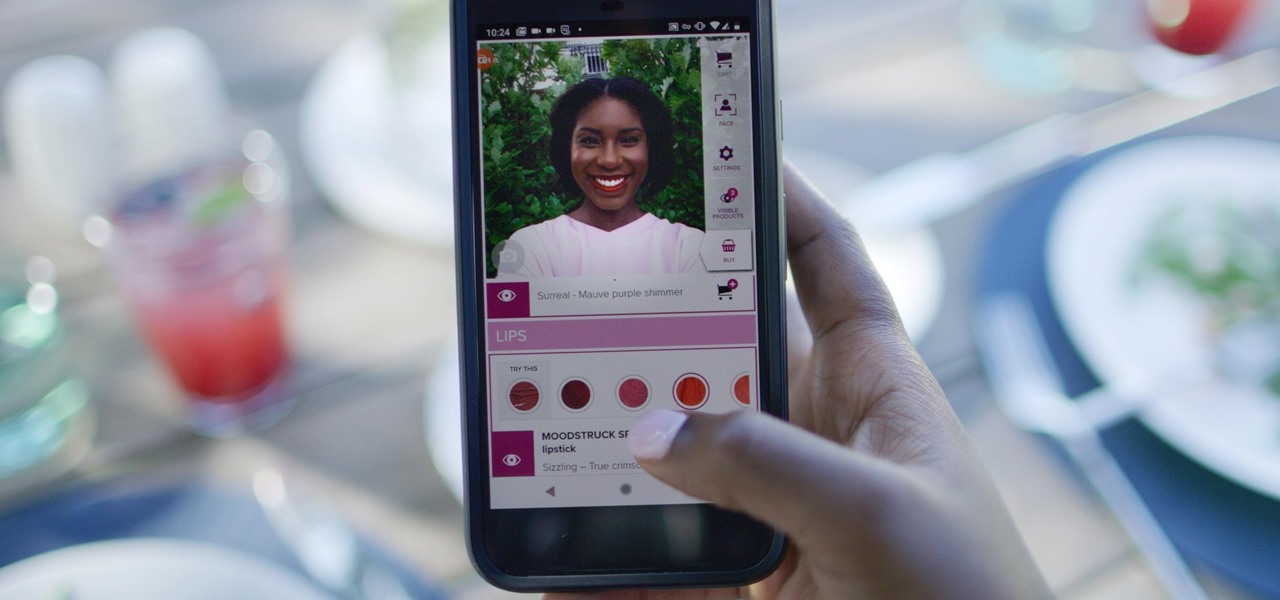
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

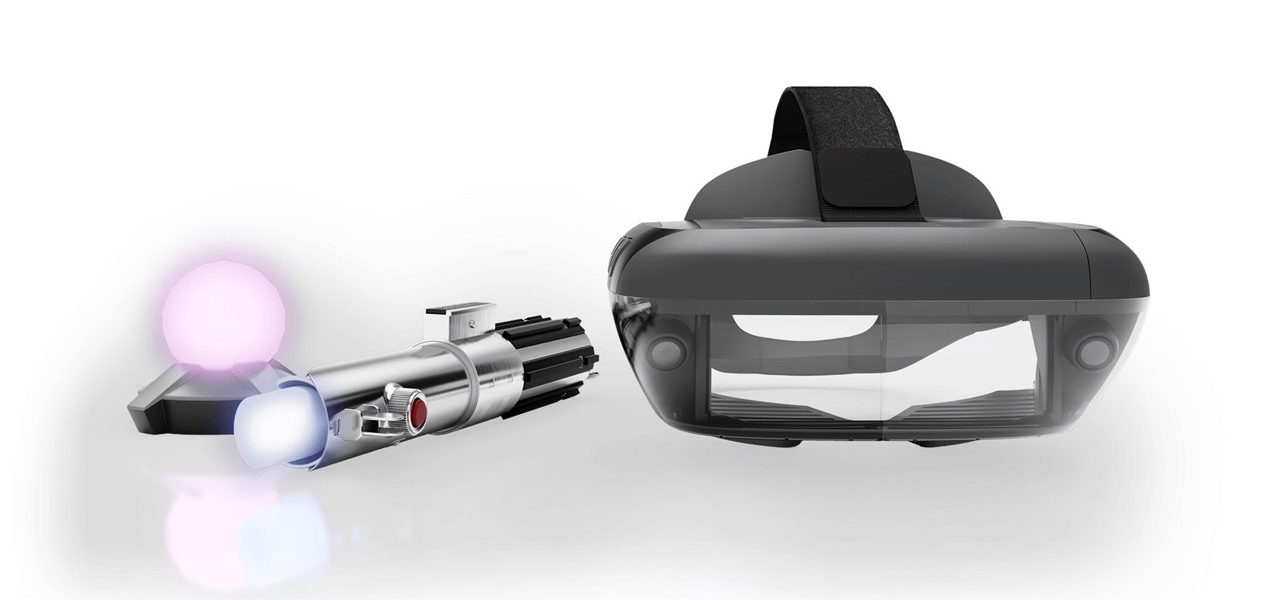
On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

The Oscars are fast approaching, which means that all the most talked about films are getting a second dose of heavy promotion in hopes of winning an Academy Award.

The release of Avatar Chat for Magic Leap One and Spatial for HoloLens during the fourth quarter of 2018 appeared to revolutionize video calling via augmented reality.

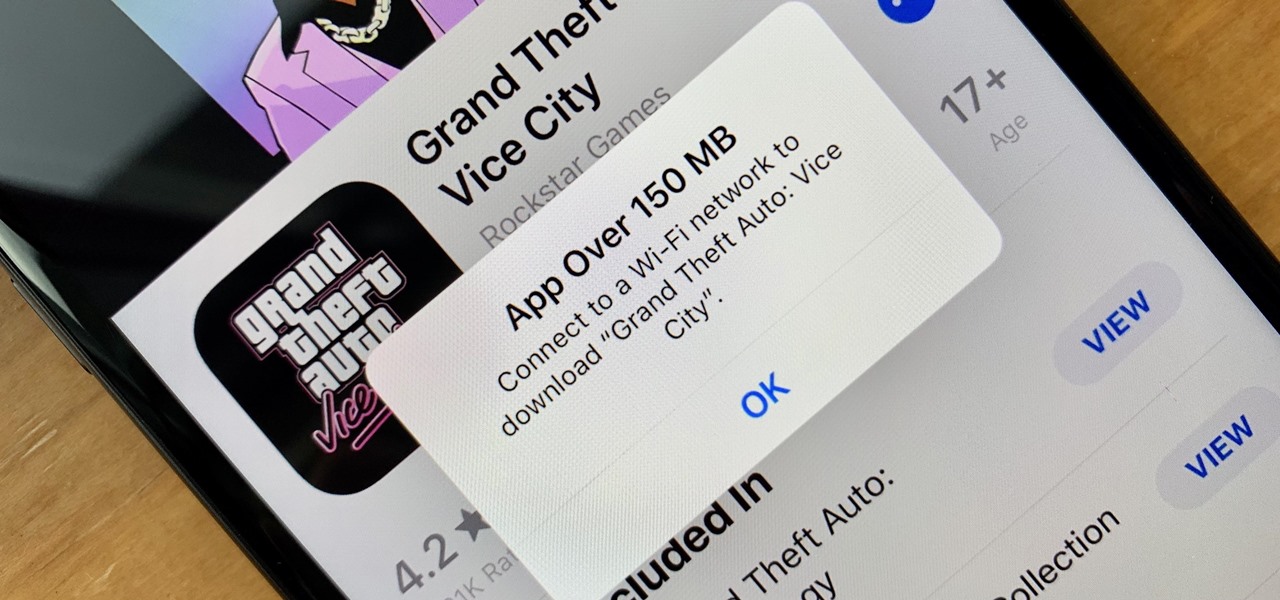
These days, cellular connections can be just as fast — if not faster — than traditional internet providers. That, coupled with the prevalence of unlimited data plans, means less worrying about hopping on a Wi-Fi network to download something. However, try to install an app or update over 150 MB, and your iPhone will insist you switch to Wi-Fi. We don't think this is very fair, so here's a way out.

The team at Magic Leap just got a millennial-style boost with the announcement that financial news network Cheddar is coming to the Magic Leap One.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

The company behind augmented reality's first real gaming hit, Pokémon GO, is quietly making moves toward supporting the rapidly growing smartglasses space that may one day move its content away from smartphones and tablets and onto AR lenses positioned on your face.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Earlier this year, Samsung released the Galaxy J3 and J7 to select markets. These two devices are the latest in the J series, Samsung's super-budget series that tries to rewrite what it means to be a budget phone. Now, starting September 14th, you will be able to get them GSM unlocked.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Magic Leap shows up in the weirdest places. Last week, right at the start of World Cup fever, for some reason, the Magic Leap One appeared on a Brazilian television show.

Upon Google's release of ARCore in February, the platform wasn't only playing catch-up with Apple and ARKit in terms of downloads, but it also lagged in capabilities, as Apple already had vertical surface recognition and image recognition on the way with ARKit 1.5 for a March release.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

When the Super Bowl airs, every other TV network puts on reruns because no one wants to face that juggernaut for ratings. The launch of a new iPhone is the Super Bowl of the tech world, with the launch of the iPhone X being the biggest one yet.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

General Motors (GM) seems to have gone to great lengths to avoid lawsuits as it launches its first hands-off driving system in its soon-to-be-launched Cadillac CT6.

Tesla founder and CEO Elon Musk offered some insight into how hackers might seek to turn driverless cars into zombie fleets, but remained upbeat about what can be done about it.

The new battlefield AR game announced by Skyrocket Toys today is similar to the childhood game "Tag", except the stakes are much, much higher.

Isn't it everyone's dream to be a sticker? No? Just me? Well, if you've ever felt like emojis just aren't conveying the exact emotion you want and you feel like your face would do a better job, have no fear. Prisma has released a new app called "Sticky AI" that allows you to transform your selfies into stickers that you can use for your messages.

Now that Fyre Festival co-founder Billy McFarland is charged with fraud, this is the perfect time to list off those top 15 influencers who promoted tickets to the disastrous event to their loyal followers, right?

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

Verizon launched the $80 unlimited prepaid plan this week and we've found that it actually isn't as limitless as they would have you believe.

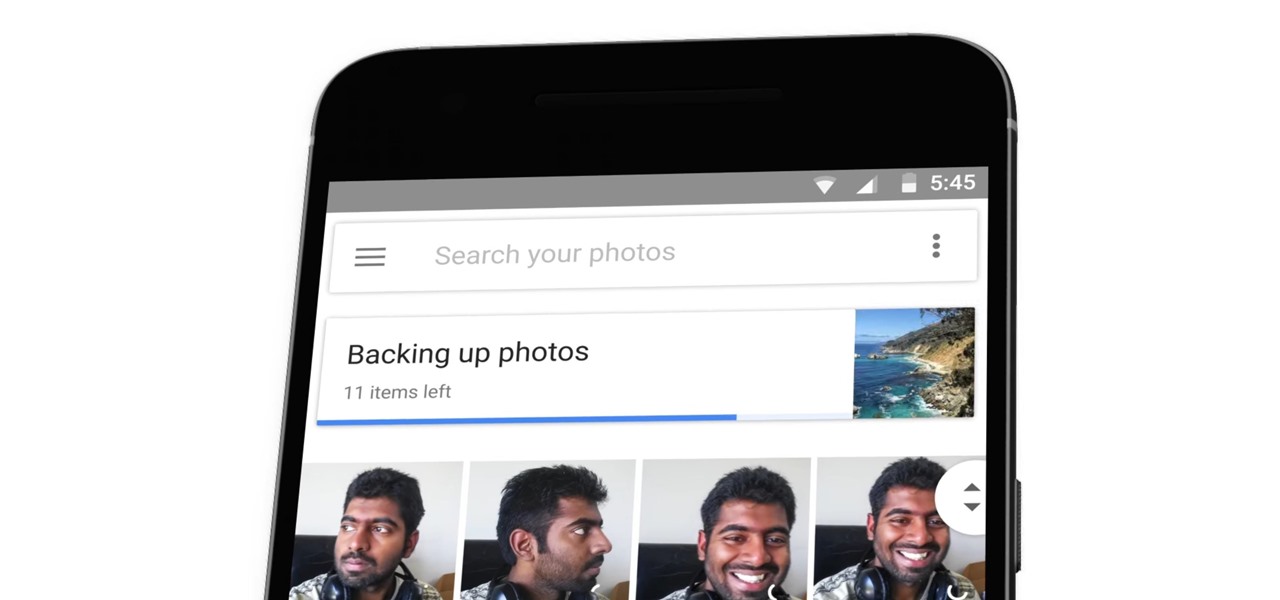
The latest Google Photos update for Android has added a number of cool new features, like video stabilization and a rumored Google+ integration. The latest update started rolling out to devices on April 11, 2017, and includes the video stabilizing feature we've been waiting for.

Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

Apple has yet to create a successful social networking app, but that doesn't mean they want to be left out of the social video conversation. Case in point: Today they announced a new video app set to debut for iOS in April called Clips.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

We like to have a variety of cupcakes on hand when we're entertaining, but we don't want to spend too much time making separate recipes. No one has the time or the money for that—especially when you're hosting and you've got a bevy of other dishes to prepare.