In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from their initial release. That is, until now.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

When you're not using your phone, it doesn't make much sense that it would be wasting power by maintaining an internet connection for the inside of your pocket or purse. Well, perhaps you need a little bit of intermittent data here and there so that apps can update themselves in the background and still post notifications, but it doesn't need to be constant.
With AirPlay for iOS, Chromecast Screen Mirroring, and even third-party PC-pairing apps to play around with, getting your devices to interconnect could not be any easier than it is today.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.

As I've said before, slowing down is not an option for me. At one point, I realized that there were plenty of files on my Mac that I didn't need any more, but too many to delete individually. In other cases, your Mac can be experiencing some major malfunctions: constant crashing, locked controls, slow boot times, missing files, etc.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

3D has been all the rage for the past few years. It seems like every other film has a 3D aspect to it, our TVs have 3D capabilities, and we can even print functional objects using increasingly affordable 3D printers. And after some trial and error (ahem, Evo 3D), it's finally taking shape on mobiles.

Welcome back, my greenhorn hackers!

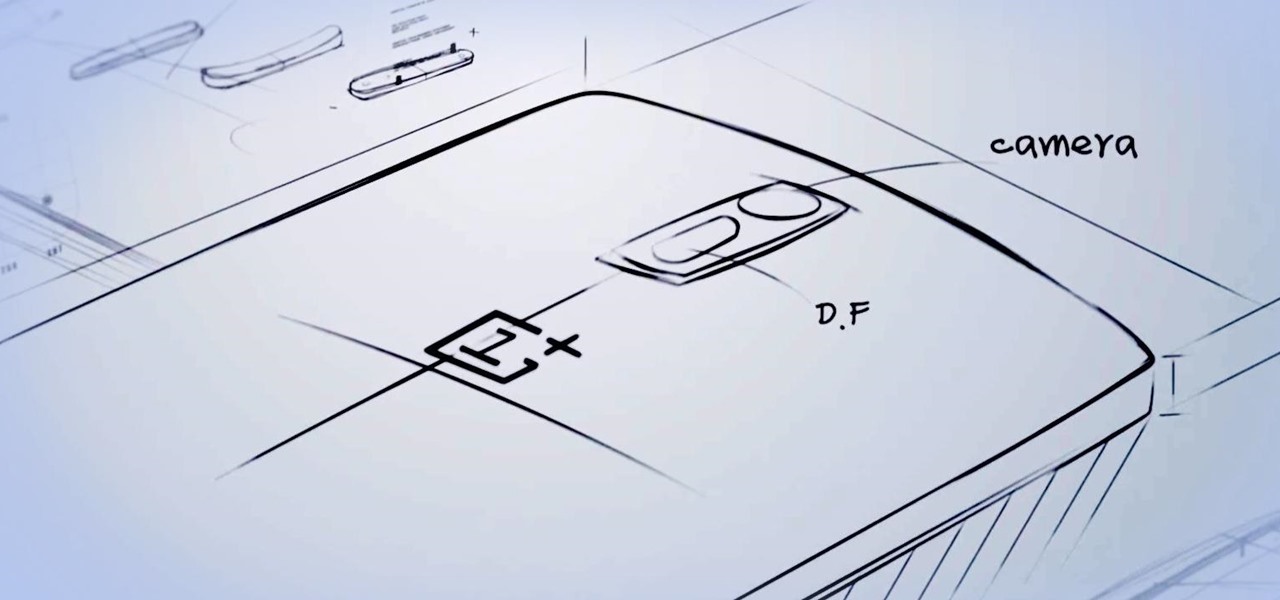
After lots of waiting and anticipation, the OnePlus One Android smartphone has been unveiled, and it's ready to take down the Nexus.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

The list of streaming services is pretty vast, from HBO GO to Hulu to Netflix, these subscription-based services have never been so popular, and have never been easier to watch now that they have Chromecast support.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

You probably use your smartphone to mostly surf the web, play games, and communicate with others, but there's so much more it can do. Thanks to integrated features and third-party apps, you can seamlessly control things around your home, including your TV, tablet, Bluetooth speakers, and even lighting fixtures.

What do Hulu Plus, Pandora, and YouTube all have in common? Ads—and lots of them. Sometimes, an advertisement or two isn't a big deal, but when you're bombarded with them daily on your iPhone, they can get old really quick, and might even lead you to delete the apps entirely.

The advent of the Google Nexus 4 seemed too good to be true—high-end hardware, unlocked and contract-free at a low price. As time went on, however, we began to see the compromises. The camera was "meh" at best, and most egregiously, it shipped without LTE functionality.

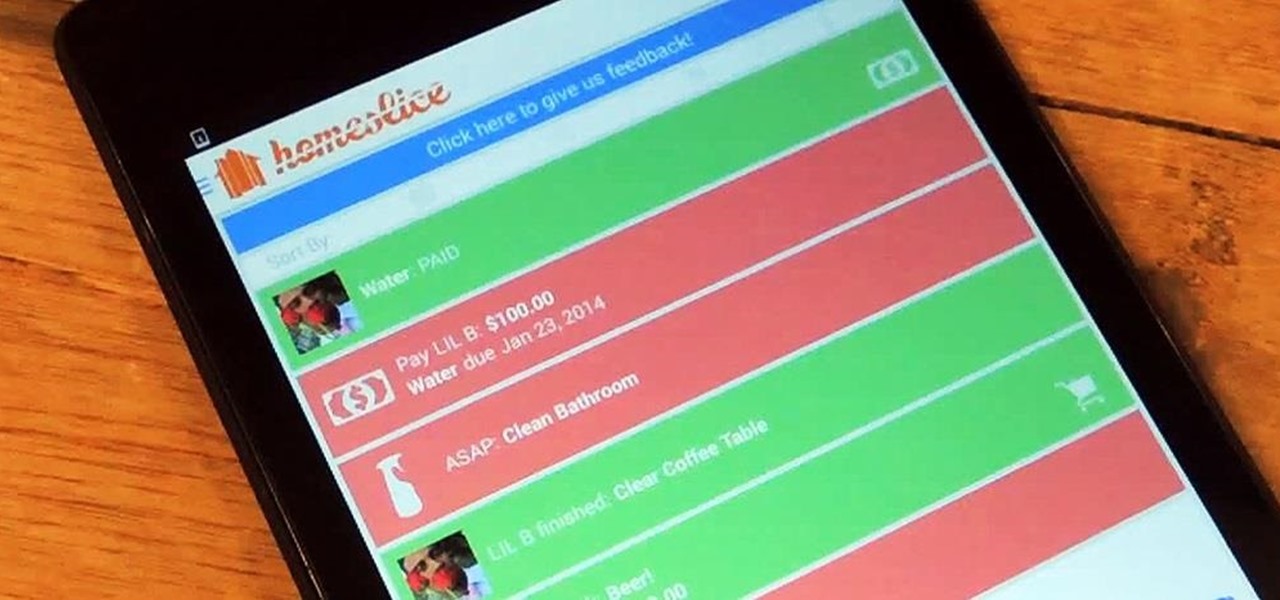
We've all heard our fair share of roommate horror stories, or have some of our own, because we never truly know who someone is until we've lived with them. Cohabitation issues generally revolve around things like bills, chores, cleaning, and groceries. Approaching a roommate, especially an adult one, to remind them to do their chores can be an anxiety-ridden and daunting task. After all, we're roommates, not parents!

Toast notifications are a type of pop-up alert built into Android, letting us know when an app has performed a certain action. Whether it's Gmail saving a draft or Firefox opening a new tab, toasts are meant to be informational while not being totally intrusive.

Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

One of the coolest features that Samsung built into the Galaxy S4 is the infrared (IR) blaster and WatchON software to control your television. I've been using my GS4 for the past few weeks to control my DirecTV setup and it works great. Smartphones are truly becoming all-in-one devices these days.

If you're a dedicated Instagrammer, you're probably well aware of the humblebrag hashtag #NoFilter, which expresses to other users that your photo is just so damn awesome that it looks like you added filters to it, even though you really didn't.

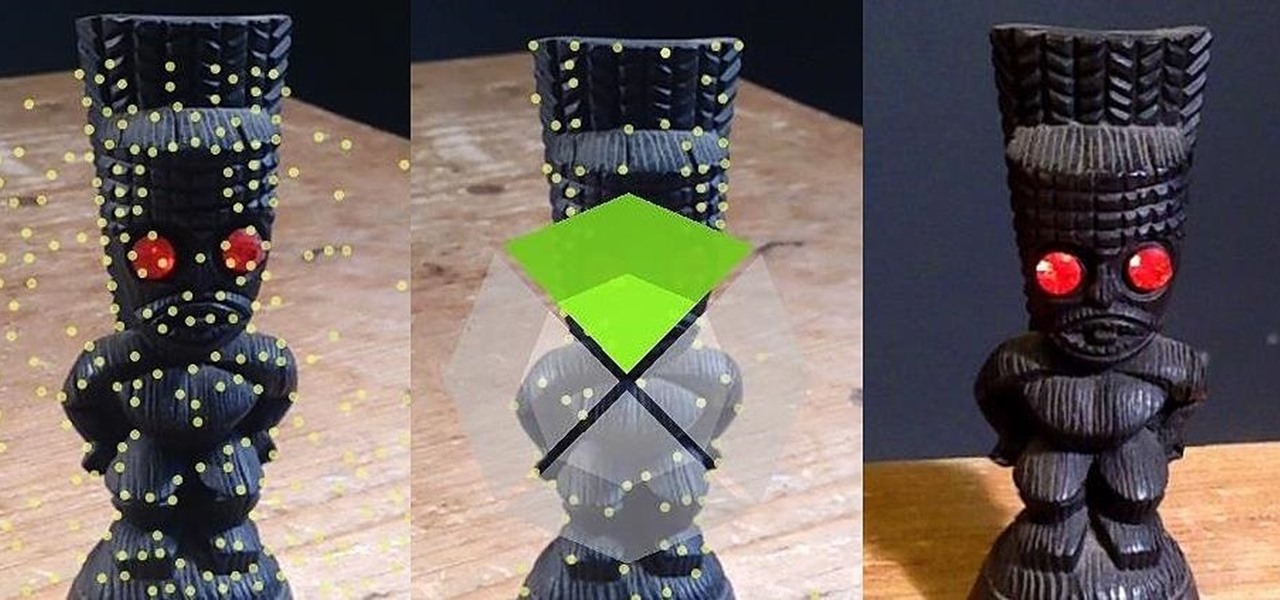
Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

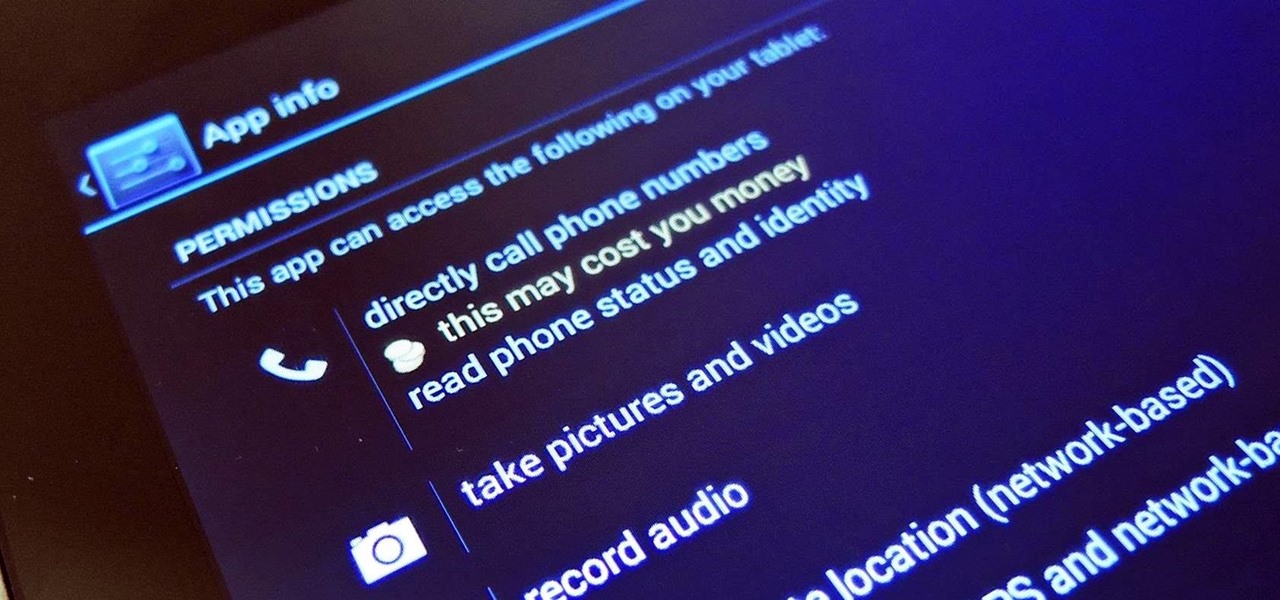
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Don't always believe the marketing hype. "PlayStation Certified" does not mean anything to a softModder. All this indicates is that a smartphone or tablet labeled as "PlayStation Certified" has met the guidelines and hardware requirements issued by Sony to display PlayStation Mobile (PSM) content from the PlayStation Mobile Store correctly. No Nexus 7 here.

Every time Apple releases a new version of their mobile operating system, it comes packed with an assortment of bugs, issues, and other hindrances.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

If you're always on the go, the Nexus 7 is a godsend for having everything you need at the tip of your fingers—music, videos, text documents, photos, and more. Unfortunately, as good as that is, it also means one hell of a messy tablet.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

The battery in the Samsung Galaxy S4 may pack 500 more milliamps per hour than the old S3 battery, but that doesn't necessarily mean more battery life. High-powered devices need lots of juice, and the S4 is definitely more powerful than its predecessor. The new battery can handle a third more in standby days, and over twice as much in talk time hours. But, when you live on your phone all day long, that means nothing. You're battery is still going to have a hard time keeping up with you.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

Video: . Optimize your Marketing with a Mobile Website

I love my Mac just the way it is. Well, minus the fact that I accidentally deleted iPhoto and would now have to pay $14.99 to get it back. Other than that, my Mac is pretty sweet.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

With Sprint already rolling out their Jelly Bean updates to Samsung Galaxy S III owners here in the United States, international users have already had a chance to check out Android's newest OS on their S3, but all is not gravy.