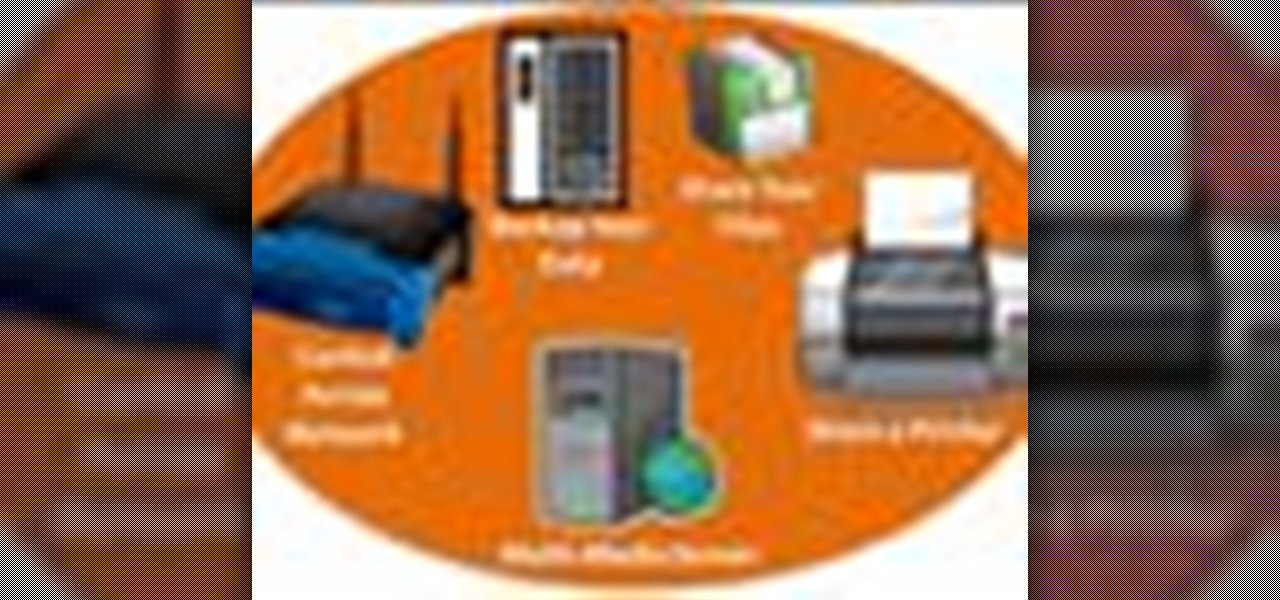
Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.
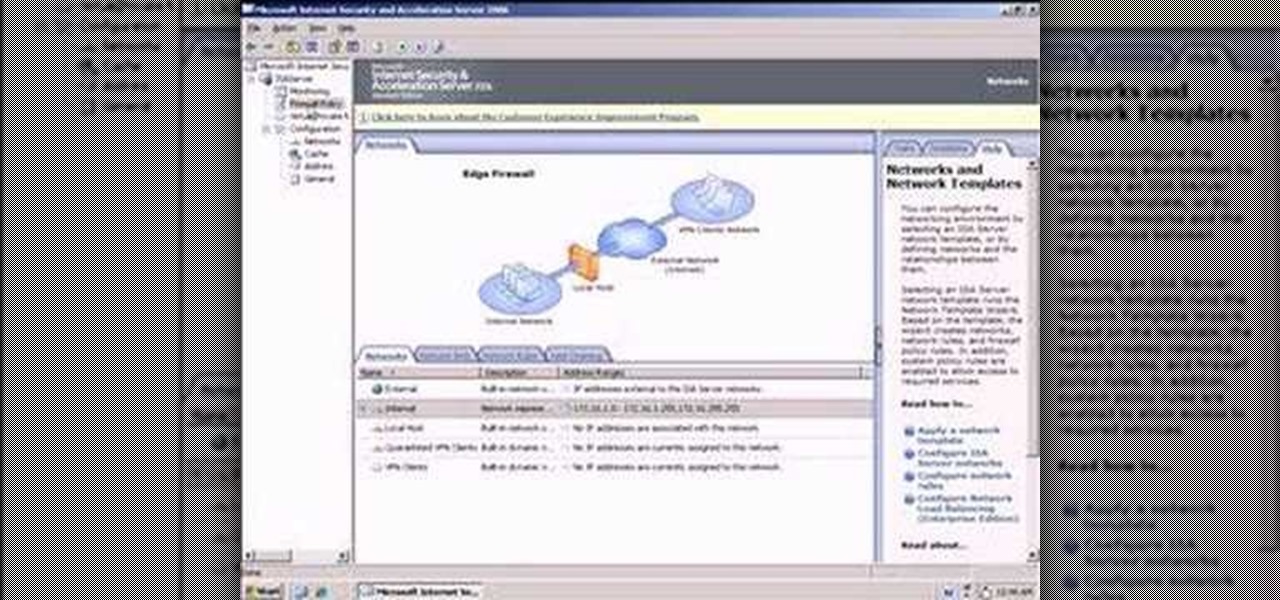
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.
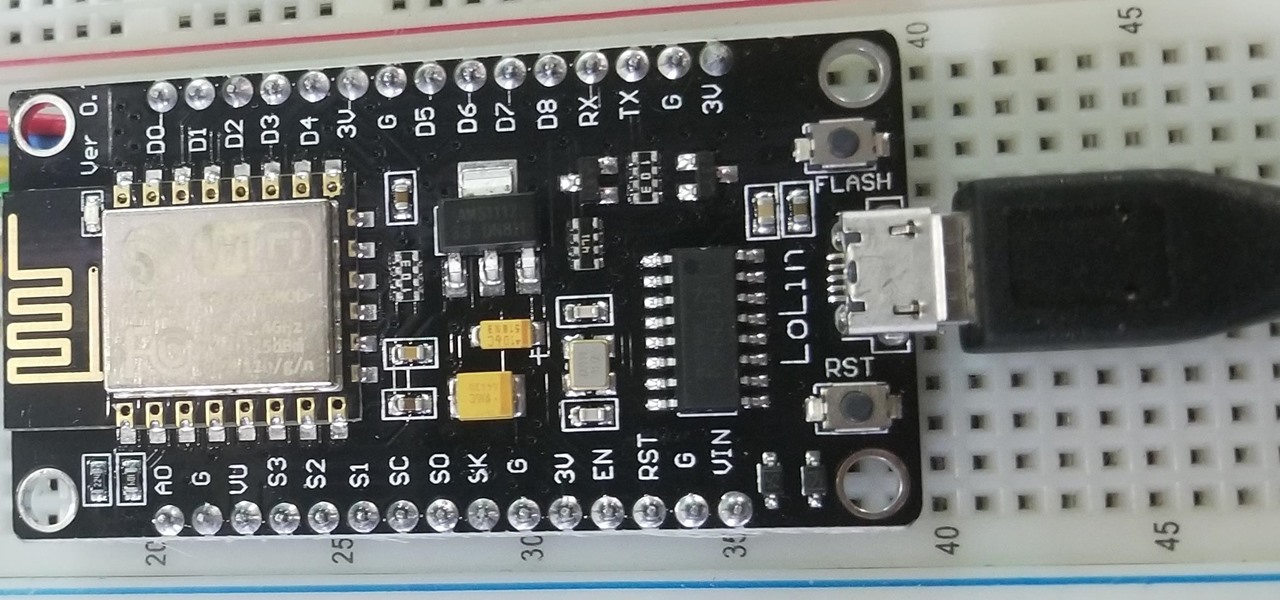
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.
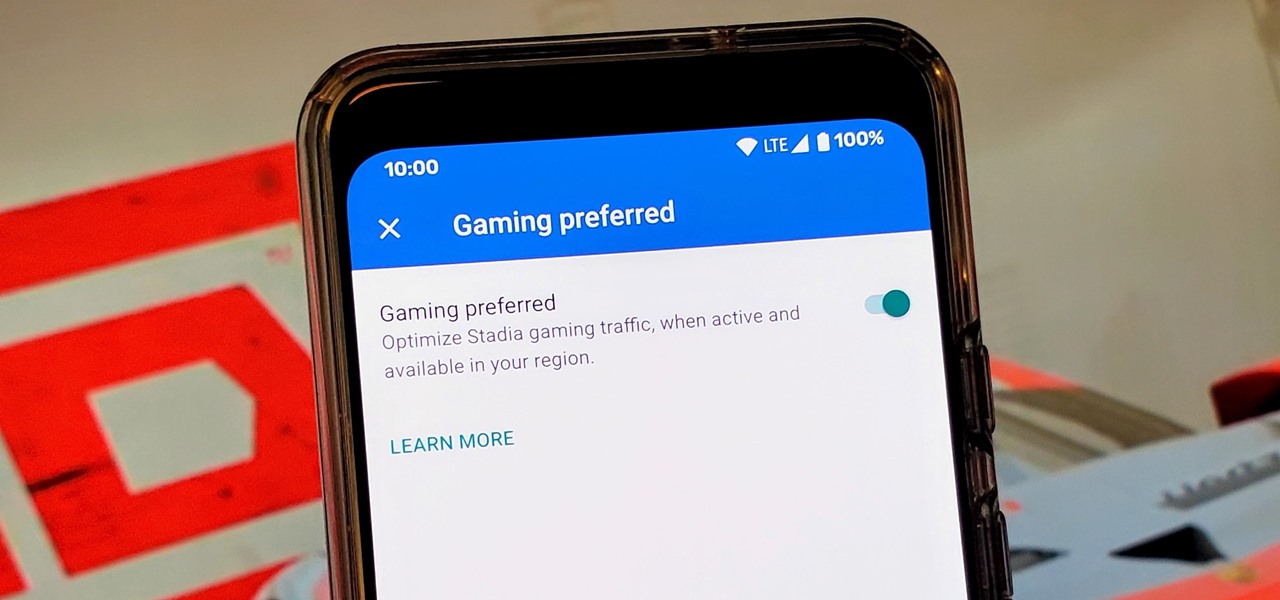
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

Most of us don't get the opportunity to see election coverage first hand, but with virtual reality, we're not as restricted. AltspaceVR has teamed up with NBC News to let you log in on your computer or VR headset and actually take part in the action—just not physically.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

In this video, we learn how to connect to Xbox Live with a laptop & Ethernet cable. First, connect your computer to your Xbox using an Ethernet cord. After it's connected, you will have to change the wireless network setting to 'shared'. To do this, go to the start menu and then go to 'my network places'. Now, go to 'view network connections' and then you need to highlight the connections. After this, right click and then bridge the connections. From here, right click and go to 'properties' g...

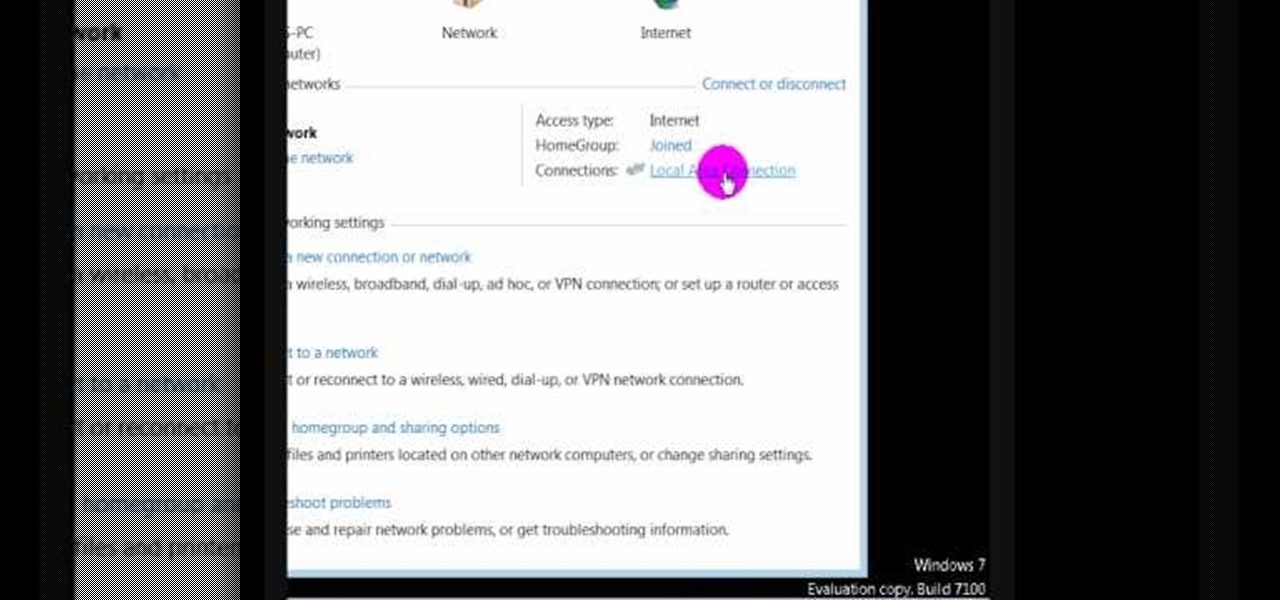
In this video we learn how to find the IP address of your computer. First, go to your desktop and click on the network in the lower right hand corner. The network and sharing center will now pop up on your computer. Click on the link that says "local area connection". Then a new window will pop up, click "details". Once the information comes up you will be able to see your IP address along with a ton of other information about your network. Another way to find your IP address is to go to the ...

In this tutorial, we learn how to unlock the iPhone 3G to work on other carrier networks. First, purchase an ATT Universal unlock SIM card and cut it so it is the same size as the SIM card in your phone. Don't cut any important parts off the back of the card. Now, remove the card from the iPhone and install the Universal unlock card. This is all you have to do and now you can run your iPhone on a different network. This is the most simple way to use your phone on another network. You can rese...

Firefox is one of the most customizable web browsers available. In this browser, you are able to install multiple add-ons and toolbars, all of which do something different for the performance level of your program.

This video tutorial tells you how to create a free VPN with the website itshidden.com. The first step in creating your VPN on itshidden.com is to make an account on itshidden.com. Register with your own username and password. Then when you've made an account log in to it so that you can use the rest of the website. Next you go to control panel, and then network setup. Then you will have to click through the instructions in order to create a new network. Next you will have to create a new conn...

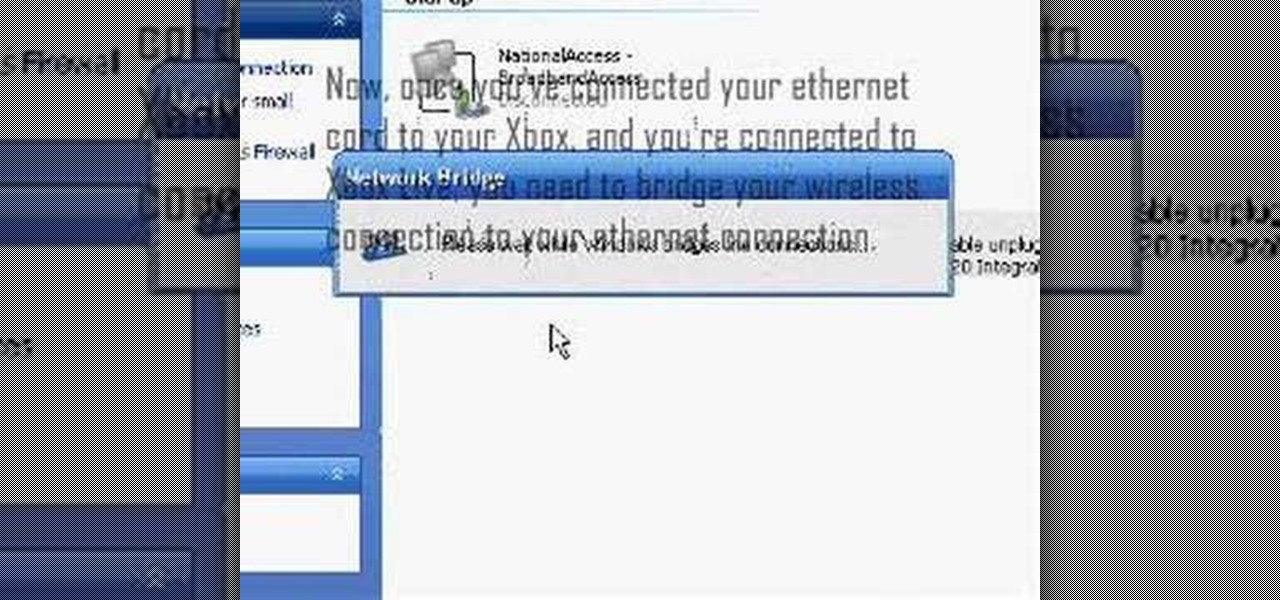
This is a video games tutorial where you will learn how to connect to XBox Live with your laptop for Vista and XP using a wireless network. Go to the Control Panel -> Network and Internet Connections -> Network Connections. Click on XBox Live. Once you have connected your Ethernet card to your Xbox and you are connected to XBox Live, you have to bridge your wireless connection to your Ethernet connection. Give the connection a name you want, plug the Ethernet cord into the Xbox and laptop and...

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

For a health conscious change of pace, try a tuna burger! They are so easy to make, all you have to get is some canned tuna, which you probably already have in our pantry. This cooking how-to video is part of Quick Fix Meals with Robin Miller show hosted by Robin Miller.

It can be hard finding fellow singles in the suburbs but it can be done! Keep your eyes peeled and make sure you are out and about meeting new people in public settings. Don’t forget about your online or in print options.

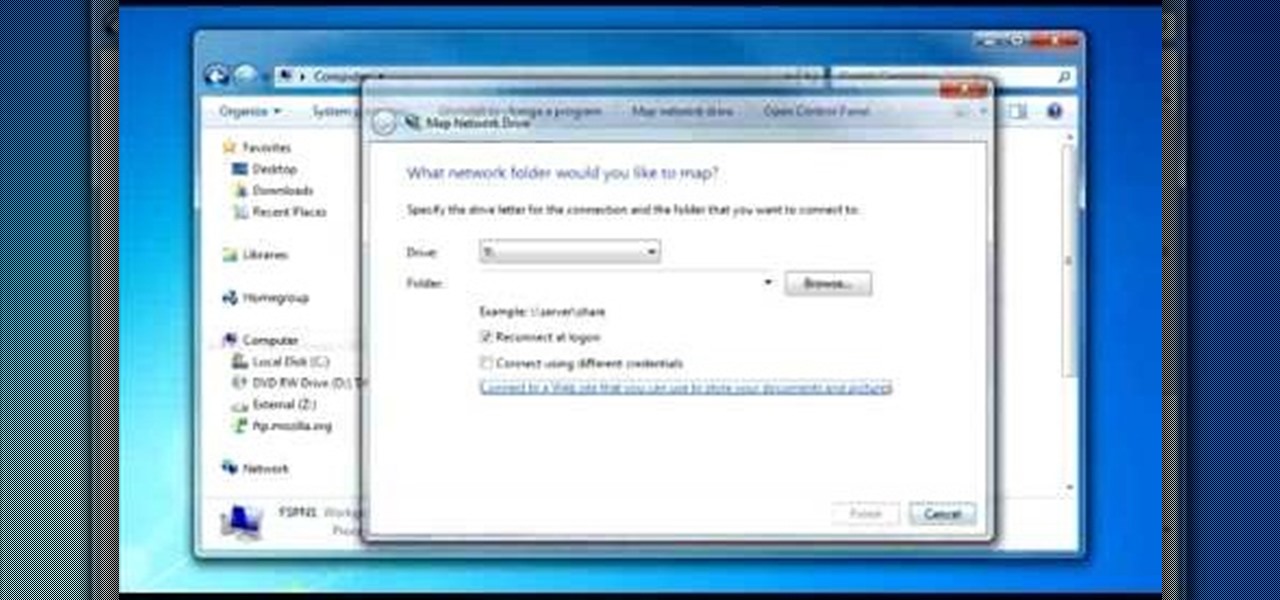
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

Now you can find your IP address if you need it and you don't know it, it very easy. Or if you have problem with a person on the internet, now you can discover who that person is. You can find her/his IP address and after that you can find her/his real name. But after you find the IP that you were looking for, you have to check if the person who own this computer is in your network, because if you want to find his/her name, the program works only if the owner is on your network. So if you are...

In this clip, you'll learn how to find and connect to WiFi networks on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Not only can your T-Mobile G1 phone get Internet access by itself, you can also use it as a router or modem for your home wifi network. All you need is to download a single app from the market, install it, and you're ready to set up your home wifi network!

Google G1 users, want to switch your phone network? In this video, learn how to unlock the Google G1 HTC Dream Phone. All you need to complete this tutorial is your phone and a SIM network unlock pin code.

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.

Throwing a block party is a great way to meet your neighbours! Block parties are perfect for hot summer nights when no one wants to be stuck indoors. These parties are fun and easy to throw, even on a budget. Check out this video for information on how to throw a rockin' party for your neighborhood without spending much money.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

In this video tutorial, you'll learn how to use the WiFi Radar application to find wireless networks while running the Ubuntu Linux distribution. For more, and to get started finding and using wireless networks in Ubuntu for yourself, take a look!

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.