Waymo claims in court documents filed yesterday in its lawsuit against Uber that ex-Uber CEO Travis Kalanick knew that former Google engineer Anthony Levandowski was in the possession of stolen documents while employed at the troubled ride-sharing firm.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

If you had to answer the following statement, which answer would you choose? Water is:

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

New images reveal that Microsoft is already well underway in fulfilling its $480 million contract to provide augmented reality headsets to the US Army.

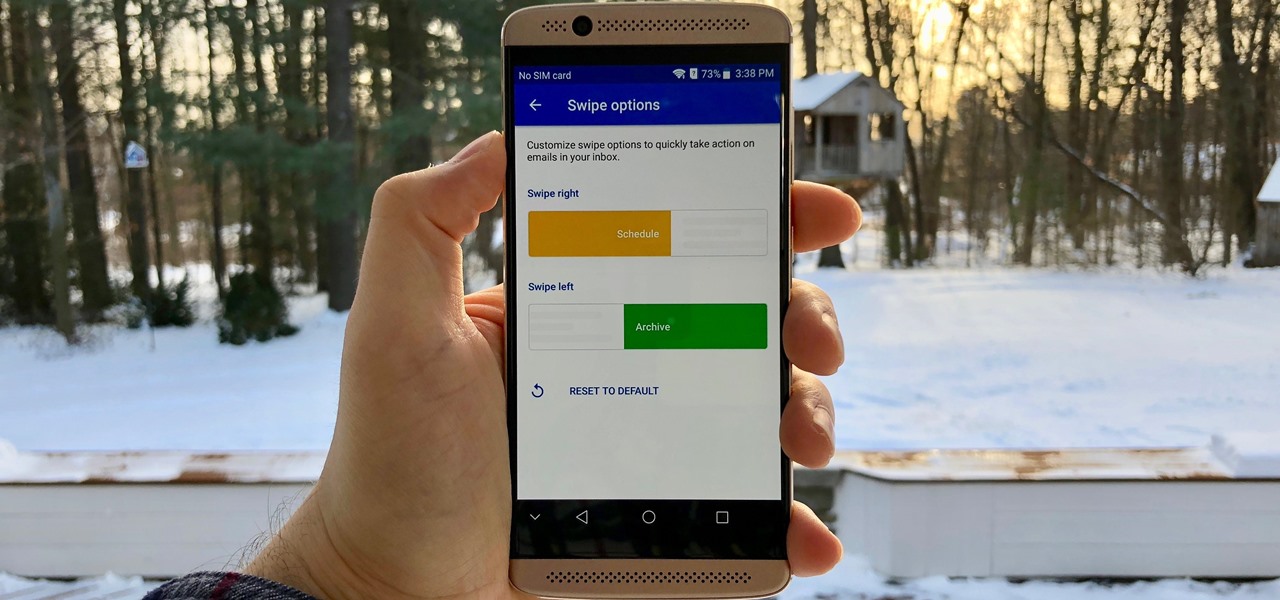
Swipe actions are an integral multitasking feature of any good email client, and Outlook is no exception. The application allows for two swipe actions at a time, but offers seven total options for those actions. We'll show you how to choose which actions go with which swipes to best tailor the app to your needs.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

If you've been longing since the '90s for the total Clueless experience of virtually trying on clothes, you missed out by not attending London Fashion Week earlier this year.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

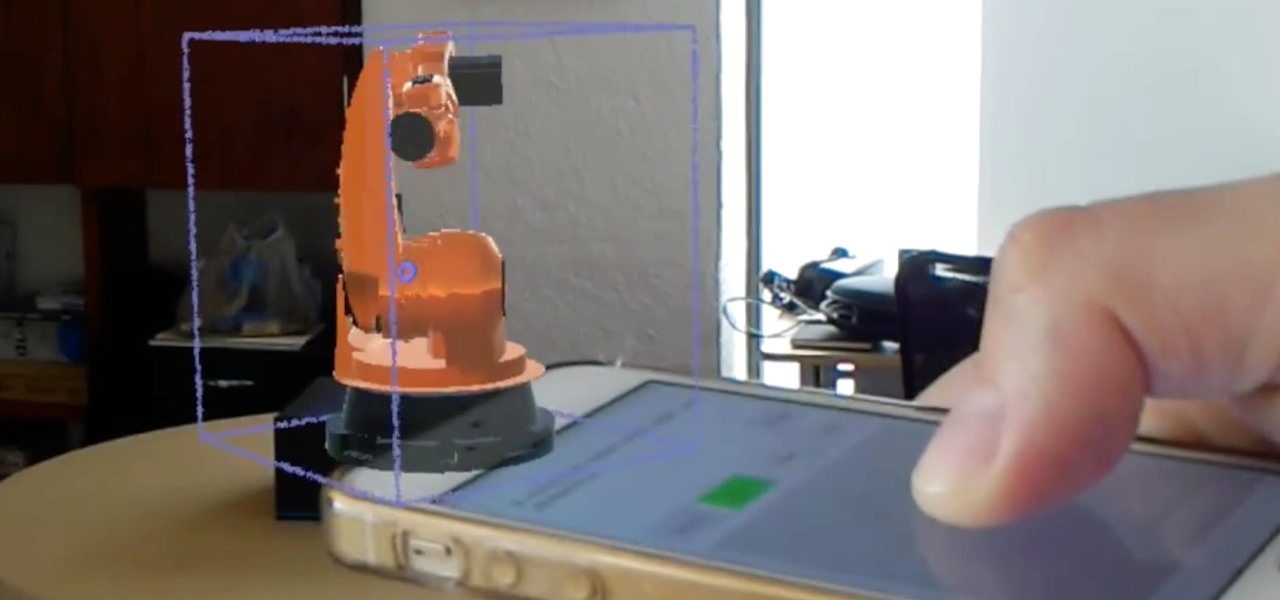
We've highlighted the projects of Wavelength Studios a few times over recent months for their work in the augmented and mixed reality space. Since receiving their HoloLens headsets, they've been hard at work on both development community projects as well as efforts for clients. This brings us to their latest work—a way to control holograms on the HoloLens with our pocket-based modern miracles, also know as smartphones.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

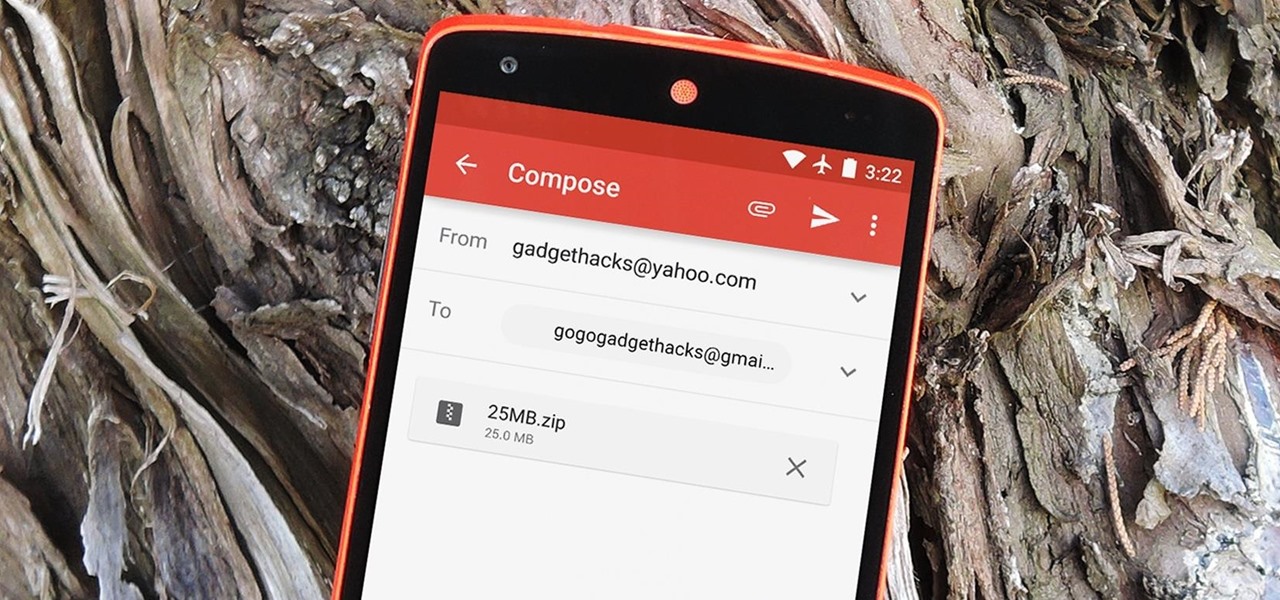
The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Most newer computers come with a webcam, but if you're using an older system, you may not have one. If you only need to use a webcam occasionally, it may not be worth putting the money into, so why not just use your smartphone? There are a few apps out there that can help you turn your phone into a super-convenient wireless webcam and save some cash.

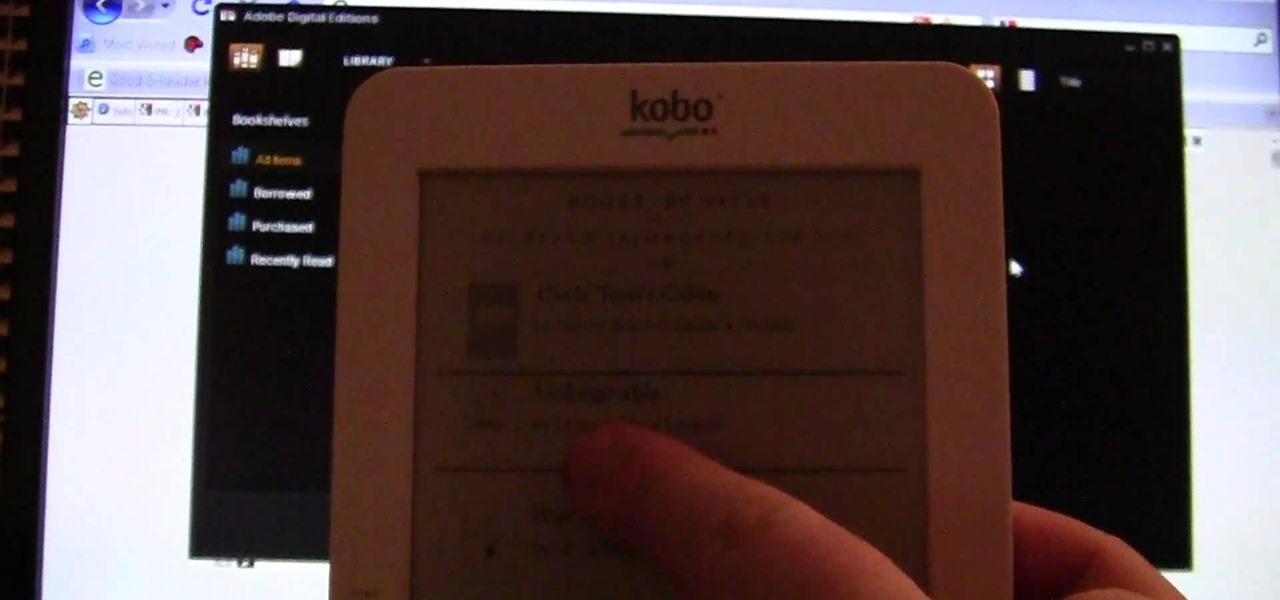
Through Thursday, January 19th, Borders is offering the Kobo Wireless eReader for $99 with coupon—that's $40 off its typical retail price of $139! Though the Kobo Wireless eReader comes preloaded with 100 out-of-copyright classics, new users will nevertheless be interested in filling their new eReaders with their own books.

Southwest Yard and Garden featuring John White, Dona Ana County Extension Agent, hosts a 6 minute clip with co-host Master Gardener Valois Pearce both of Dona Ana County, New Mexico host a short web show featuring plants that can easily survive on smaller amounts of water over typical plants. They begin by discussing the full sun Ice Plant, which comes in many species and colors as well as their hardiness, but unfortunately are easy targets for wildlife. They then move onto the Gopher Plant, ...

In this video, a man answer questions sent in by viewers, about various plants. First he covers how to braid a ficus tree trunk. To do that you must grow the trees close together, then trim off the bottom limbs, and braid the trunks. Next he talks about growing miniature roses indoors. Miniature roses must be carefully watches for mold, insects, and over-exposure to sunlight when grown indoors. Then he answers a question about carnivorous plants. He covers the Venus fly trap, and demonstrates...

Catching sight of a hummingbird floating from flower to flower is one of those rare gifts from nature. In this quick and easy guide, use a little bit of science and learn how to make a hummingbird feeder that will attract all the birds in the yard.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

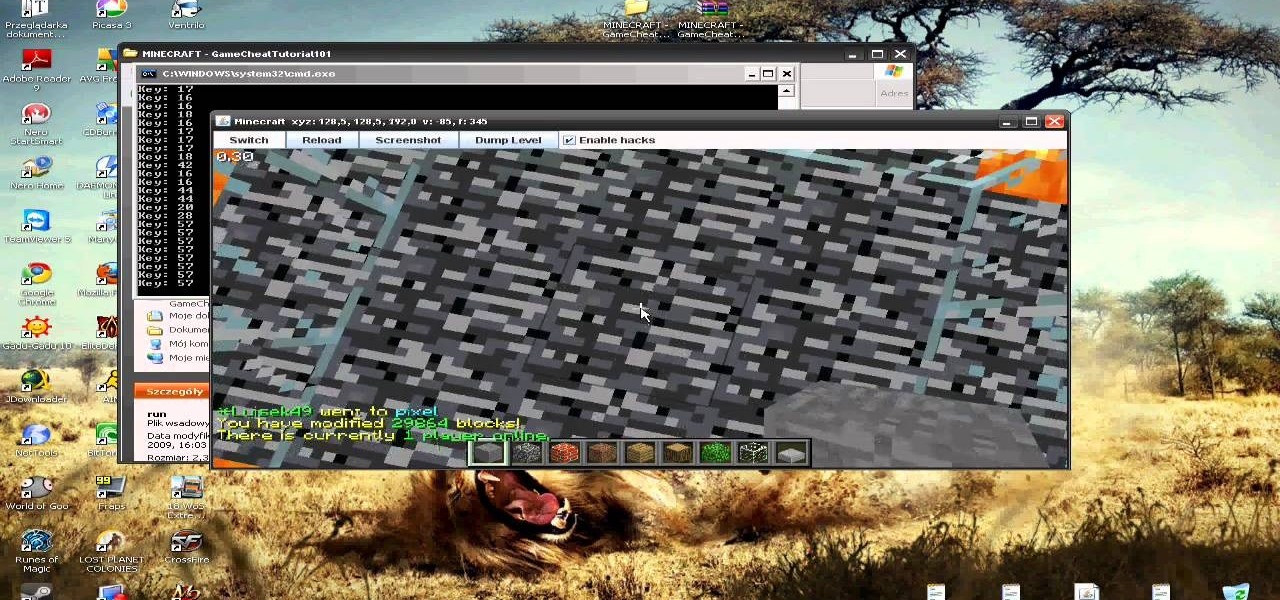
This is a super easy hack that anyone playing Minecraft on a PC can do. Hack a custom client for the game, which will give you access to things like noclip mode and fly jumps. You won't need a broswer loaded to use this, either.

In order to catch and gut a fish, you will need the following: a fishing pole, bait, a knife, and Begin by tossing bait into the water, in order to attract the fish to you. When a fish begins to tug on your line, slowly pull him in. Remove the hook from his mouth. Be careful. Bang the fish against a hard surface to kill it. Place the knife at the base of the tail. Run the knife up to his neck. When you reach in, you'll feel a cord. Pull it out. All of the guts will be attached.

A lot of people fear bats; in fact, bats rank third on America's most feared list behind spiders and snakes. Most people get nervous around bats because they are hard to see at night and can fly around undetected; not to mention that Dracula myth that hasn't done bats any favors.

How to remove a stain from a carpet

In this video Andrea Osterkorn demonstrates how to stage your home for sale. It is not a comfortable process to transform your home into a home for sale. The entry way should be inviting because first impressions are important. Closets should be cleaned out. Consider renting different furniture for the living area to make it more open and inviting, and move it around to create an impression of space. Add accessories and let natural light in. Try to depersonalize the room and remove clutter so...

You are never too old to meet a mate! Never! In this video, learn some great tips on how to socialize your life to meet men when over 60.