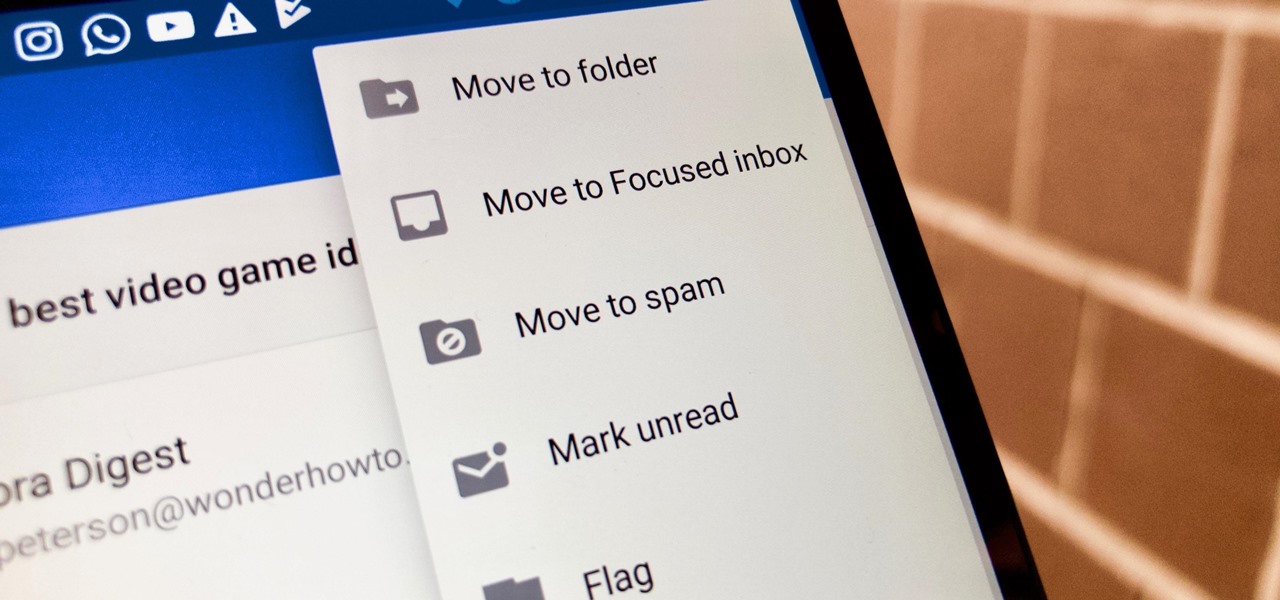
Nobody likes spam, and that's why email apps continue to vie for your digital attention by boasting about new ways to filter and reduce unsolicited messages. Outlook, an already fantastic client for focusing your cluttered inbox, has now joined in on the action, giving its users new, simple tools to fight against junk mail.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.
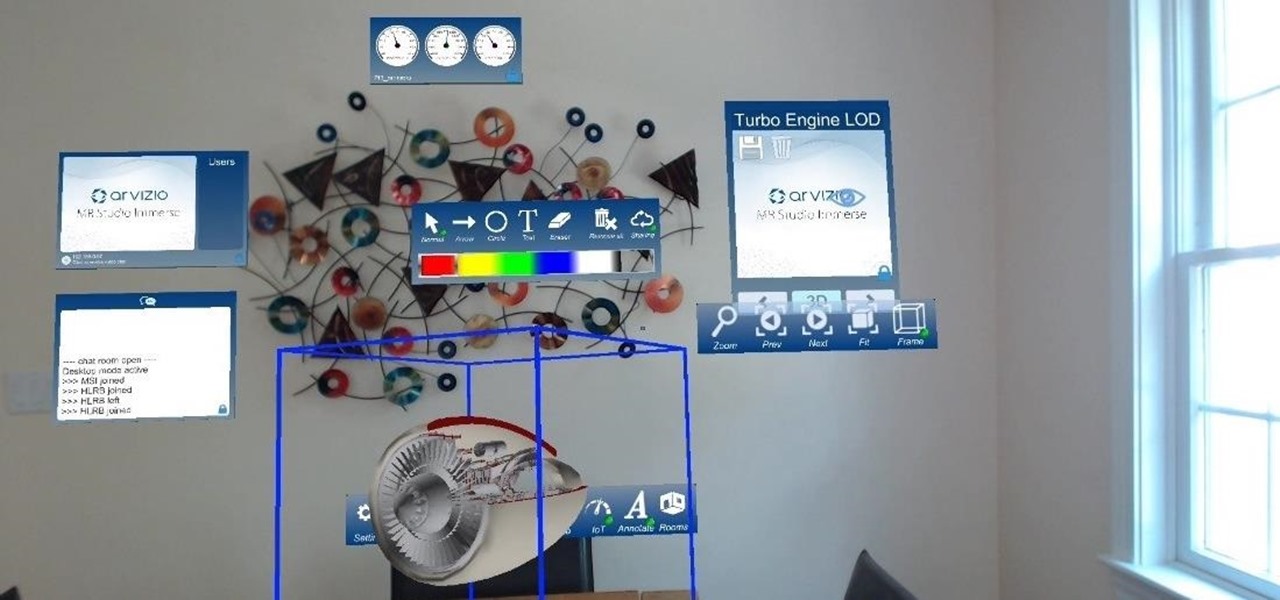
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

Augmented and virtual reality motion tracking leader Leap Motion, Inc. announced that it has secured $50 million in Series C funding to fund expansion into new territories and industries.
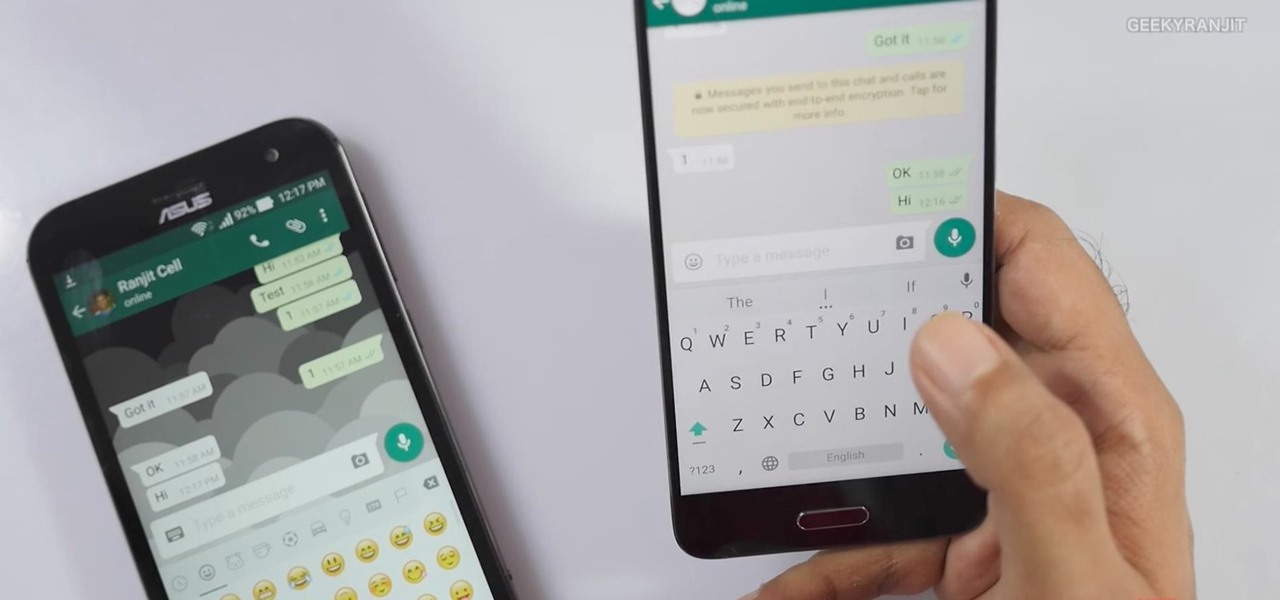
Cell phones have advanced rapidly since their inception. However, one frustrating aspect of our handheld computers is that we sometimes expect more than they can handle. We want smartphones to do all our PCs can do, but in many cases, that just isn't possible; especially when that comes to viewing and sending certain file types. WhatsApp is taking steps to bridge that gap now, by allowing users to send whatever kind of file they want, with one or two restrictions ...

A proof of concept for an overhead crane training simulator is in the works. Using Microsoft HoloLens and an industrial-style controller, trainees can pick up holographic loads and transport them throughout a warehouse setting.

A 5-year-old girl was injured after the battery in another Samsung phone exploded in China. The Samsung Note 4 was reportedly charging next to the sleeping girl when it blew up in her Guizhou-based home.

Kazendi, a London-based HoloLens development and rapid prototyping studio, just released a new iOS app in Apple's App Store that lets developers stream HoloLens applications live from the headset to an iPad or iPhone. It's called HoloStream, and is the first iOS/HoloLens crossover app we've seen so far.

Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

CyanogenMod has been building upon open-source AOSP apps for many years now. They've made improvements to apps like the stock SMS client, the stock Audio Mixer, and a whole slew of others.

In a long-awaited move, the popular messaging platform WhatsApp has finally made its official web debut. Desktop and laptop owners will be happy to know that they can now message their favorite contacts directly from their computers, without the need to install additional apps.

If you're a user of Google Play Music, but not a fan of being relegated to a browser tab, I've got you covered. Developer Sajid Anwar has created a desktop client for Google's music service, but since he made no attempt to hide logos and trademarks, it may not be long before the app vanishes completely. So get it while it's hot...and before Google takes it down.

Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

NPC's can be quite helpful in the world of Terraria. If you are wondering how to get one to move in with you, then this is the video to watch. Getting an NPC to move in is a lot easier than getting a girlfriend to move in, that's for sure.

Taking up fishing anytime soon? The first thing you'll need to learn is how to bait a hook. Different types of bait require different methods of getting them onto the hook. Follow these steps.

Researchers have found that there are simple things anyone can do to appear more appealing. You Will Need

Doing a shot is more art than science. Here's one way to hone your barroom style. You Will Need

Ant problem? If the ants have come marching two by two—or, God forbid, 10 by 10—it’s time to put an end to the parade. Here’s how. How to get rid of ants, a guide by Howcast:

Increase your odds of meeting Mr. Right with these tips. Learn how to meet men if you are single. You Will Need

It's already easy, but we'll help you make it even easier. Watch this video for tips on getting guys to buy you drinks in a bar. If the guys are going to hit on you, might as well get some free drinks out of it.

SyncVue announced at NAB that they would be offering a new version of their remote collaboration software for editors and producers. Well the long awaited update is finally here and all existing SyncVue users will definitely want to grab it. The functionality is improved and the new features are killer. So check out this quick little video tutorial on setting up and using the new version of the software, This walks you through the newest features and how to basically get around.

In this how to video, Martin Fish from Garden News explains how to prune the Butterfly Bush or Buddleia. The Buddleia is also known as the Butterfly bush because of its colorful flowers that attract butterflies. Pruning this plant is important because it encourages more flowers in the next blooming season. With the tips from this tutorial you will learn how to prune the Buddleia.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

A new dating app has arrived, and it'll finally land you a date with your celebrity crush ... kind of. The app — Dating AI — uses face search technology to help you search for potential love interests that resemble a celebrity you're attracted to.

Mosquitoes are a big problem, and citronella candles are not the solution. There are a lot of mosquito species. The American Mosquito Control Association reports there are more than 3000 mosquito species in the world, and about 200 of those occur in the US. The most common are the Aedes, Anopheles, and Culex species. These are also the three mosquito species most likely to transmit serious illness, and all of them live in the US.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Coffee beans are one of my favorite things in the entire world. They smell intoxicatingly perfect. And when ground up and steeped in hot (or cold) water, they somehow taste even better than they smell.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

While we've already covered several good ways to tame the itch of a mosquito bite, you're much better off preventing them from biting in the first place than dealing with the itchy aftermath.

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.