Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?

Welcome back, my rookie hackers!

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

Caller ID is great to have, but there are certain situations where you don't want the person you're calling to have your number. People who sometimes use their personal phones for work may not want clients knowing where to reach them outside of work, and anytime you're dealing with Craigslist, it's better to be safe than sorry.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Your iPhone's Mail app has a lot of fantastic productivity features, such as unsending emails, follow-up reminders, opening drafts from almost any view, the snooze option, bulk-selecting messages, and the formatting toolbar, but one of the most helpful ones might just be the one you're not using.

While the rest of Big Tech is still moving relatively slowly on augmented reality smartglasses, Snap continues to supercharge its own experimental AR wearable called Spectacles.

Snapchat parent company Snap has opened up its war chest to acquire yet another company that will play a role in its augmented reality ecosystem.

In these times of social distancing, video calling is becoming the technological substitute for face-to-face connections. For those who carry an iPhone, the art of video calling defaults to FaceTime, the native app on iOS that is exclusive to Apple devices. But what do you do if you or the other party is on Android?

The Paris-based technology conference Viva Technology, which hosted the likes of Apple's Tim Cook and Facebook's Mark Zuckerberg, is now over.

In the great smartglasses race, component makers, such as those that supply the crucial waveguide displays that make visualization of virtual content possible, have a vested interest in pushing the industry forward in order to ship units.

It's no secret that Apple and Spotify haven't exactly gotten along in the past, but things are looking better than ever in iOS 14.5.

Reddit has been pushing for more first-party content over the last couple years. So instead of just being a place to submit links, you can now upload photos and videos directly to Reddit's servers. But unlike Imgur, Gfycat, and other popular file hosts, Reddit doesn't give you an easy way to download videos.

San Francisco-based augmented reality company Scope AR has made building AR instructional content for mobile devices and AR wearables as easy as throwing together a PowerPoint deck, primarily via its WorkLink platform.

Roughly a year ago, Samsung demoed its AR smartglasses prototype on stage at CES 2020. Now, videos showing off a new smartglasses model along with the company's imaginings of future AR experiences have surfaced through unofficial yet reliable channels.

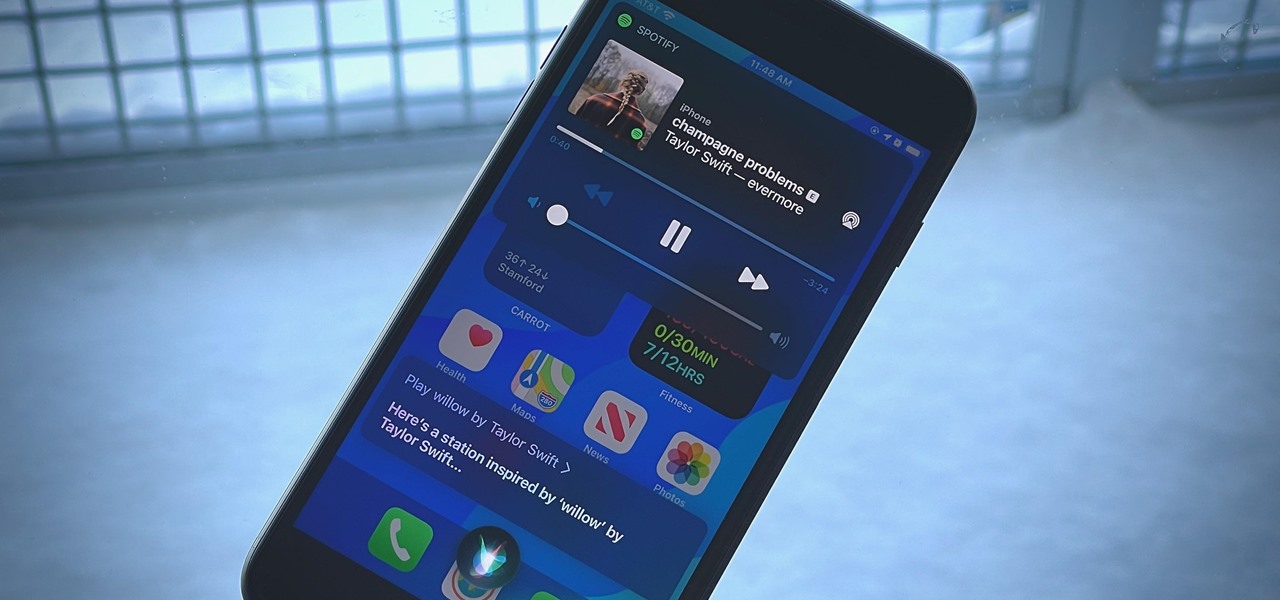
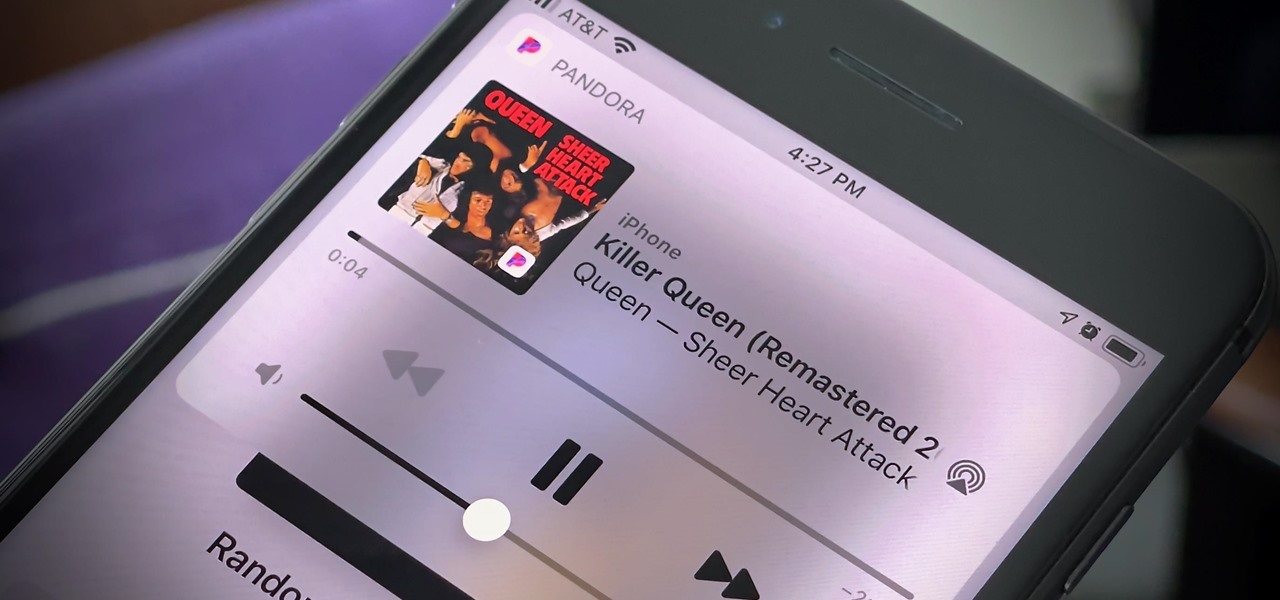
If Pandora is your primary music app on your iPhone, you know it can be frustrating to use with Siri. The digital assistant always wants to use Apple Music instead, so you need to specify that you want to play through Pandora with almost every request. That's now a thing of the past because iOS 14.5 allows you to set Pandora as your Siri's preferred music player.

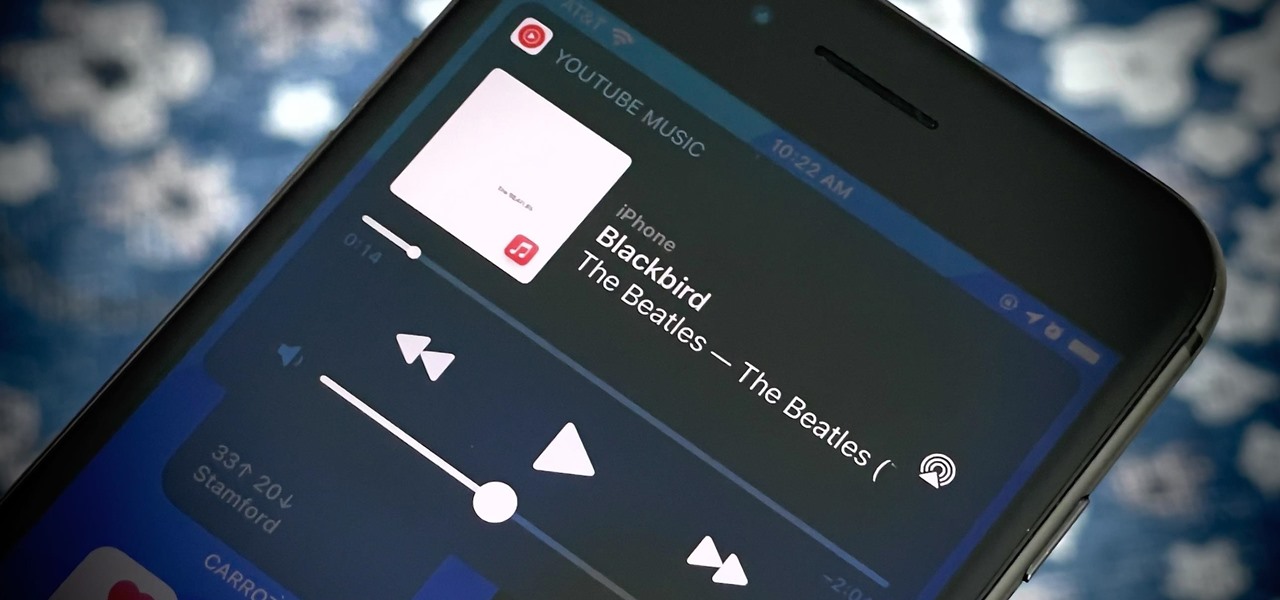
A new feature in iOS 14.5 lets you change your preferred music player for Siri requests. So if you primarily use YouTube Music over Apple Music and other services, Siri will learn so that you never have to tell the virtual assistant to play a song, artist, or album "on YouTube Music" again.

Despite the unfortunate social media-driven association of Corona beer with the virus behind a global pandemic, beverage maker Constellation Brands has pushed its marketing forward like a lime through the mouth of a beer bottle.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

I already know what you're thinking: this guide is blasphemy. I am showing you how to turn a Galaxy Note 10 or 10+ into an iPhone 11 Pro Max. And while I'd usually agree with you, hear me out. How can you know you don't like something until you try it? So here is your way of trying out an iPhone using your Galaxy Note 10.

Every year, Apple releases a new version of iOS. Each iteration promises new features to make using your iPhone that much better. This year, iOS 13 introduces over 200 new features and changes, including system-wide Dark Mode for the first time on iPhone. That said, you might want to pump the brakes before dashing to download and install the new update right away.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

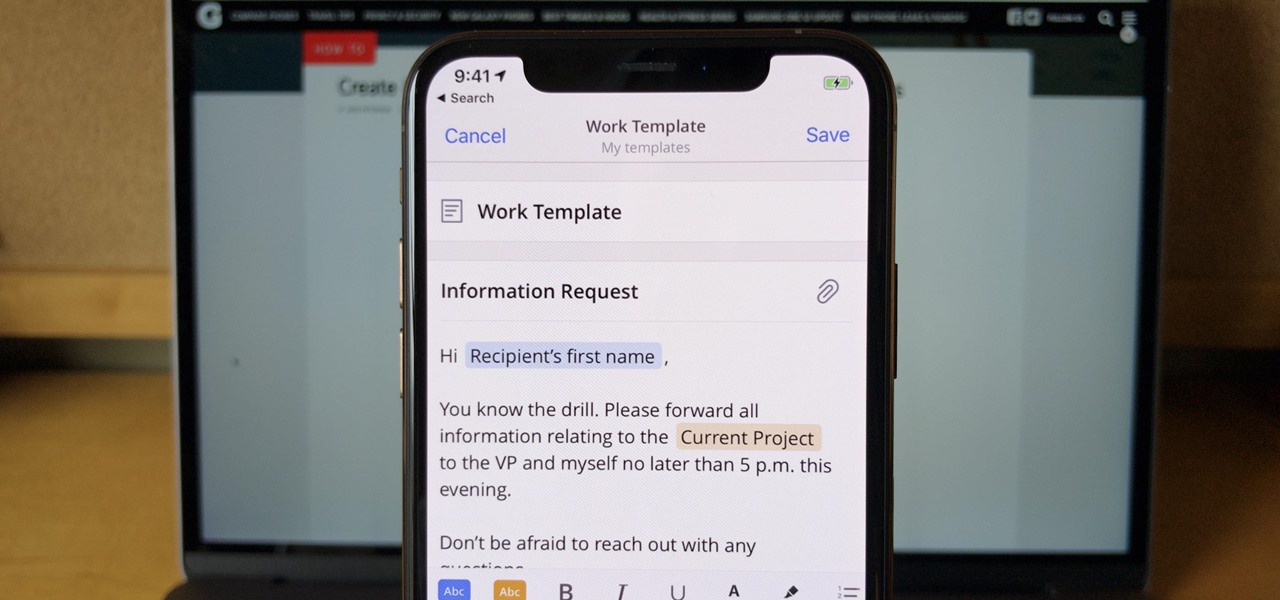
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

In recent years, many software publishers have tried to sell the business community on remote meetings via VR, but if social media chatter is any indication, it hasn't taken off in a big way just yet. However, for some, the notion of holding remote meetings using augmented reality, a medium in which you're still directly tied to the real world and not closed off in a blindfold-style VR headset, might be the better solution.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.