
How To: Teach your dog to stay
When used together with the "sit!" command, "stay!" can form the foundation for more complex tricks.


When used together with the "sit!" command, "stay!" can form the foundation for more complex tricks.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.
This tutorial shows you the basics of employing animation in your Maya project. Set up a series of rigid bodies, like dominoes, and then have them fall, one after the other, using the techniques outlined in this video. Make sure you've assigned them the proper attributes!

Tim Carter discusses the different types of wood and how they are recognized and how their attributes are utilized. Informative video will help to make sure you use the proper wood for your build.

The paint bucket tool in Photoshop has many of the same attributes as the Magic Wand Tool, only the Paint Bucket fills an area with a solid color or pattern.

Unless you're a WhatsApp pro user, you may be surprised to know that there are text formatting options that you can apply to your messages. Markdown characters can help you emphasize certain words or phrases by making them italicized or bold, and it'll even let you cross out words and change the font. It's one of those nice touches that isn't available in most other messaging apps.
In order to make your own icons for free, you will use any bitmap program. You can use Paint, in Windows. Open paint. Click on Images. Then, go to Attributes. Change the width to 32 by 32 pixels. Click OK. You can enlarge the image, if you like, in order to make it easier to work on it. Draw the image that you like. Click on File and Save. Next, you will need to save the image. Click on File and Save As. Change it to a 24 Bitmap image. Name it New.ico. Save it to your desktop. You should see ...

First we have to do is to create a new file with the size we want. Then we go to the layer tab in the left and duplicate the existing layer how many times we want (how many frames we want to have the GIF). After this we deselect all the layers by clicking on the eyes on left. Now we click again on one eye to select the layer we want to work with. Be sure to have only one layer selected. Then we can start "playing" with the images and create shapes, faces and so on with all the layers we had c...

No matter who you are, a little self-confidence can go a long way toward making your dreams come true.

When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piece of identifying information. While not obvious, you can delete or even change this attribute.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.
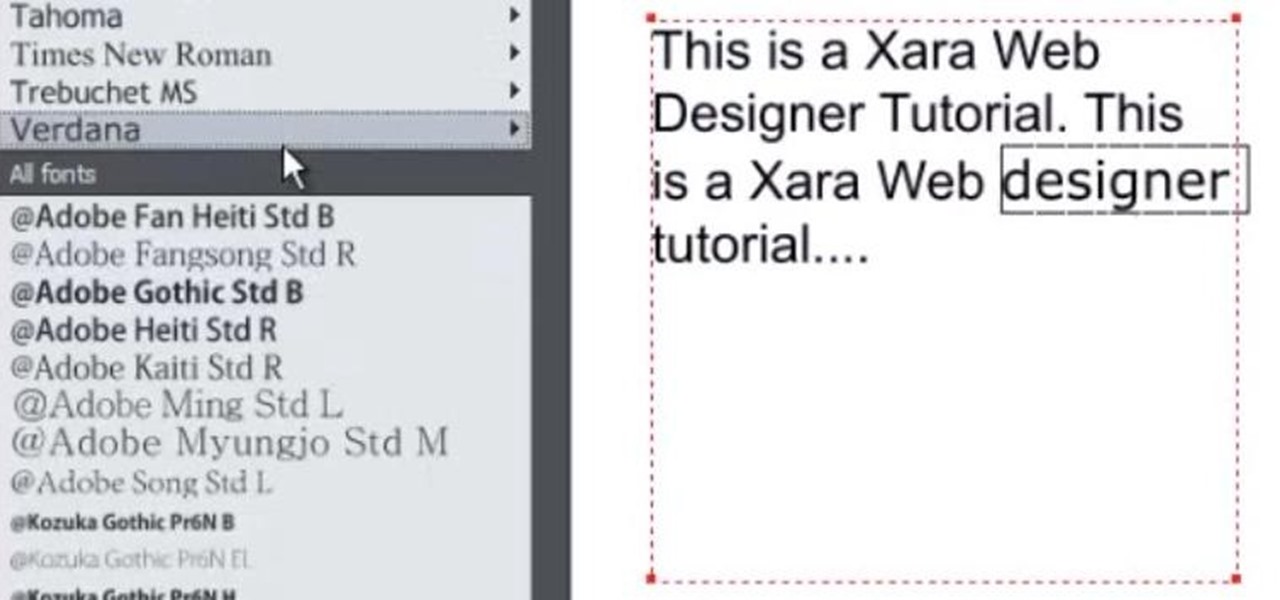
Learn to use text area, text column, spell check, dictionary tool, font-faces and font-size and text justifications. Many other text attributes are covered as well. Their are some other features available for the text tool but they will not be covered until a much later tutorial. If you have any questions or tutorial request just leave a comment.

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Signal, the encrypted messaging app, has seen 1.4 million downloads in just the first quarter of 2017—roughly twice the downloads it received in the same period last year. Rani Molla at Recode attributes this to Donald Trump's inauguration, as the private messaging service saw a 40% increase in US downloads between Election Day and the end of the first quarter of 2017.

On Tuesday, Unity released the latest version of its 3D engine, which brings improvements to the Scriptable Render Pipeline that the company introduced earlier this year.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Although it sounds like a foodie's take on Facebook, what Calabasas, California-based FaceCake actually offers is more about augmented reality fashion marketing rather than food selfies.

On Tuesday, Apple held a public conference call for its Q2 earnings report. During the call, Steve Milunovich from UBS asked Tim Cook about a recent 451 report, and how it reflects a pause in current iPhone sales. Cook's response was more than interesting, to say the least:

Looking to get seriously tatted up? Your best bet is probably to head Down Under. Meet Steve Butcher, a New Zealand native who is changing the tattoo game in a big way. While there are a lot of amazing artists out there, the level of detail Butcher is able to achieve is truly unbelievable.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.
Yep, Google just put in place a new thing called the dun dun duuuun .... "Device Catalog!" No, not like the Macy's catalog of your smartphone dreams. This is quite the opposite.

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.
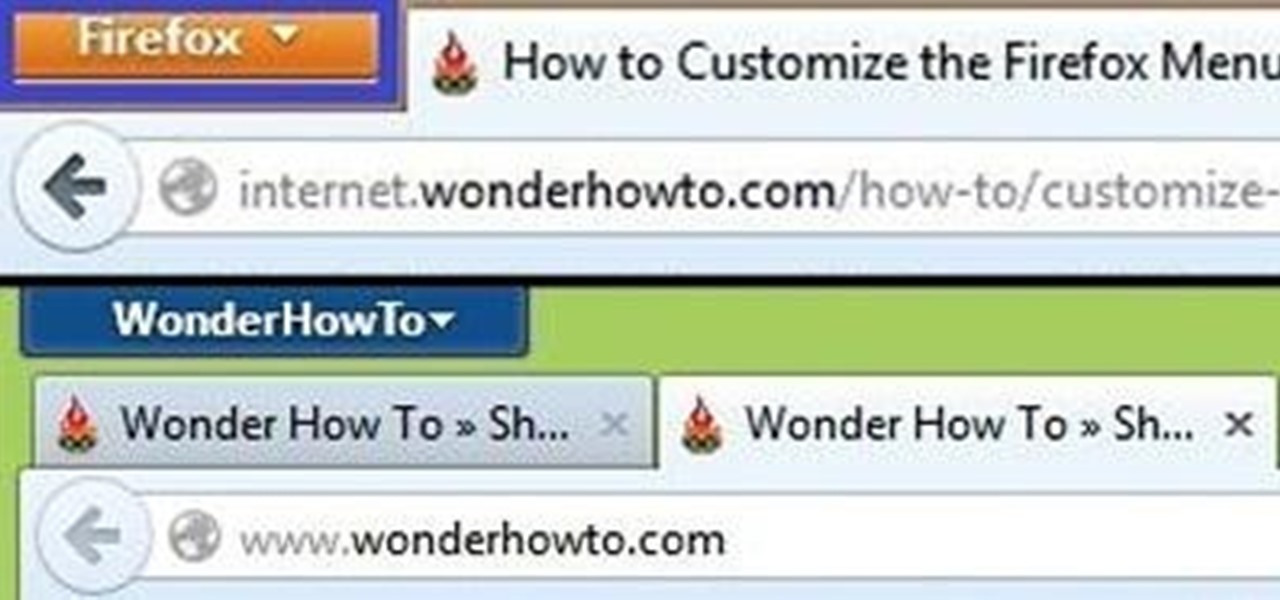
Browser customization is one of Firefox's best attributes. You can personalize your Firefox with extensions, add-ons, themes, and so on. And if all of that still doesn't cut it, you can even customize the Firefox Menu button to say whatever you want. To start off, you'll need to download a user file editor called ChromEdit Plus. Click Add to Firefox, then hit Allow when prompted and wait for it to install. You will need to restart Firefox afterwards.
The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

Despite its status as a hot commodity amongst emerging technologies, the augmented reality industry is not immune to the ebbs and flows that occur in every industry.
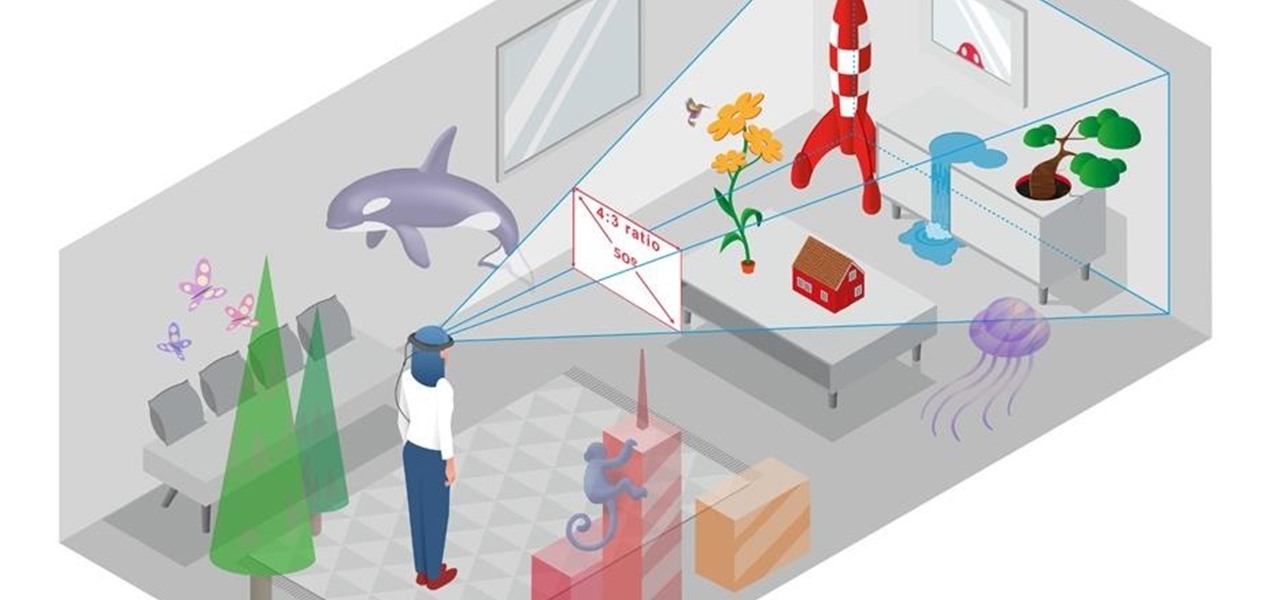
In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

Creamer, milk (whole or skim), sugar, or even butter—you've probably added at least one of these to your coffee to improve its taste at some point. If you're looking for something different, though, try a new twist with a dash of cinnamon. This sweet, sharp spice can do so much more than improve coffee's taste, and I've got 10 examples for you to consider.
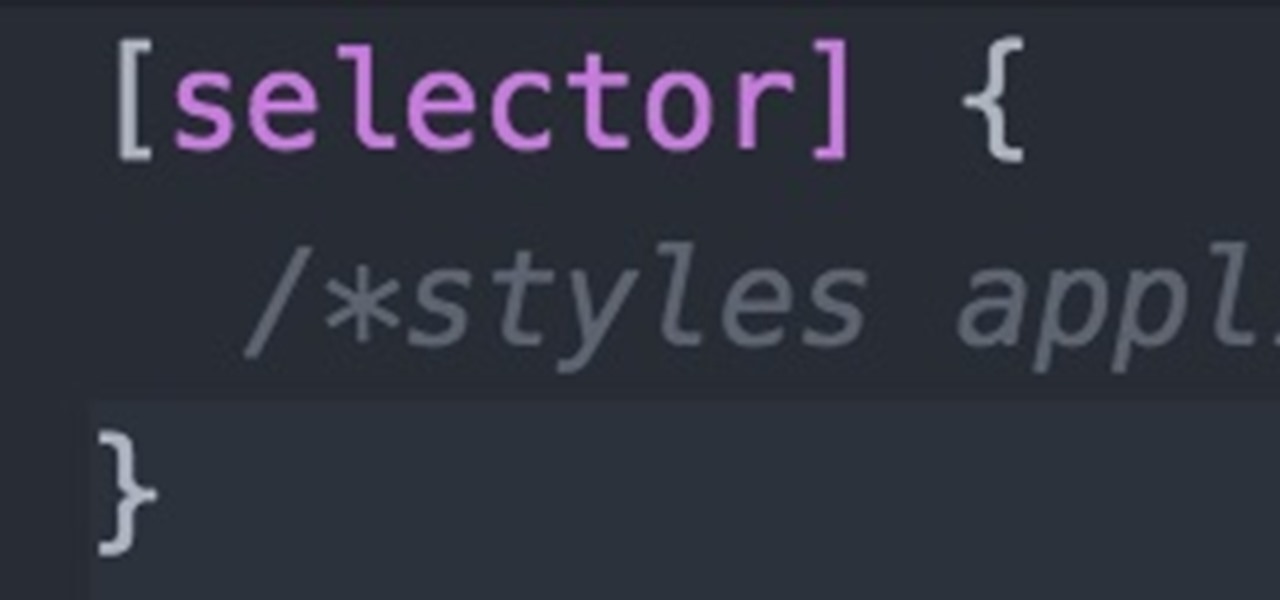
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.