Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!
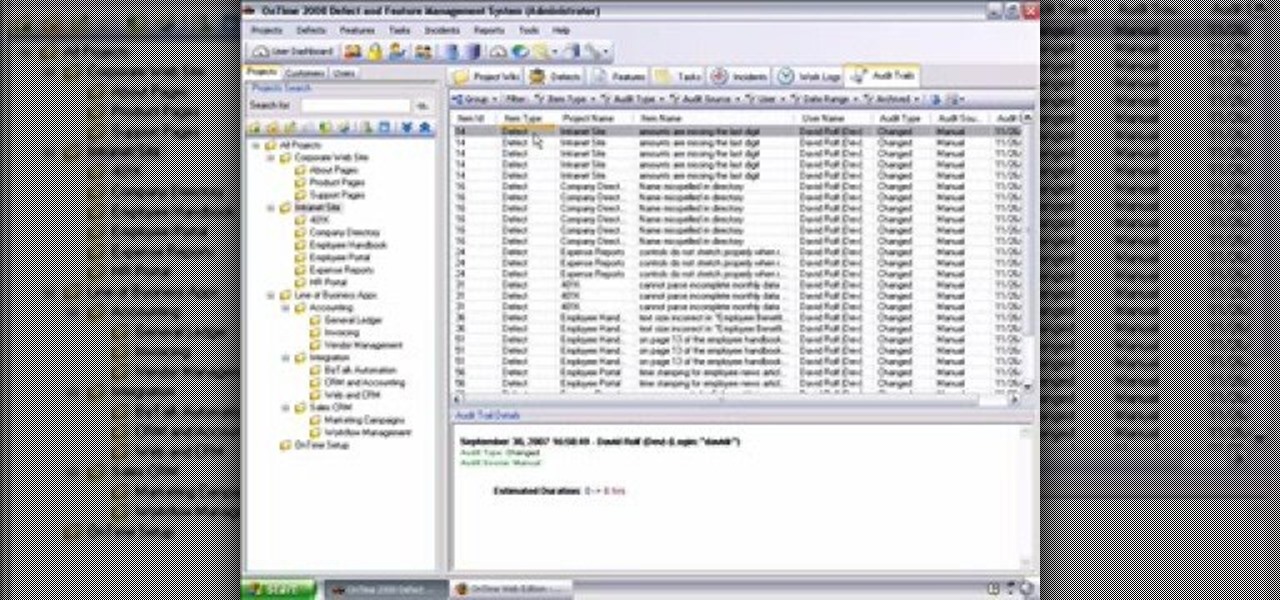
This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite focuses on how you can see the history of your defects, features, tasks, and incidents, as well as project wiki pages. For more information, as well as to get started using the history and audit trails features in Axosoft OnTime 2008, take a look.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.
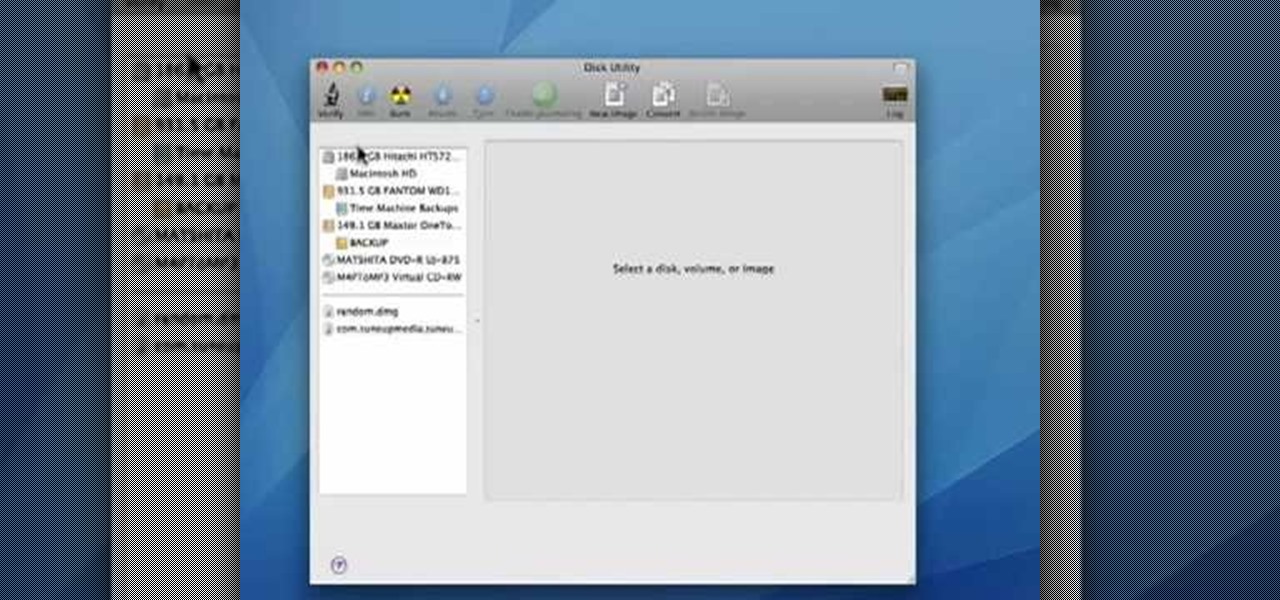
In this video tutorial, viewers learn how to verify a drive on a Mac computer. Begin by opening Finder and select Applications. Open Utilities and then select Disk Utility.app. Now select a disk drive that you would like to verify. Make sure that you are in the First Aid tab and check the Show Details. Then click on Verify Disk. Now wait for the drive to be verified. Once finished, it will display all the items that were checked. This video will benefit those viewers who use a Mac computer an...
See how to audit a live website for broken hyperlinks in a matter of minutes. With Xenu's Link Sleuth tool, it's easy. So easy, in fact, that this home computing how-to from the folks at Easily can present a complete (and somewhat talky) overview of the process in just over two minutes' time. For the specifics, and to get started checking your own website for broken links, just watch this handy how-to.

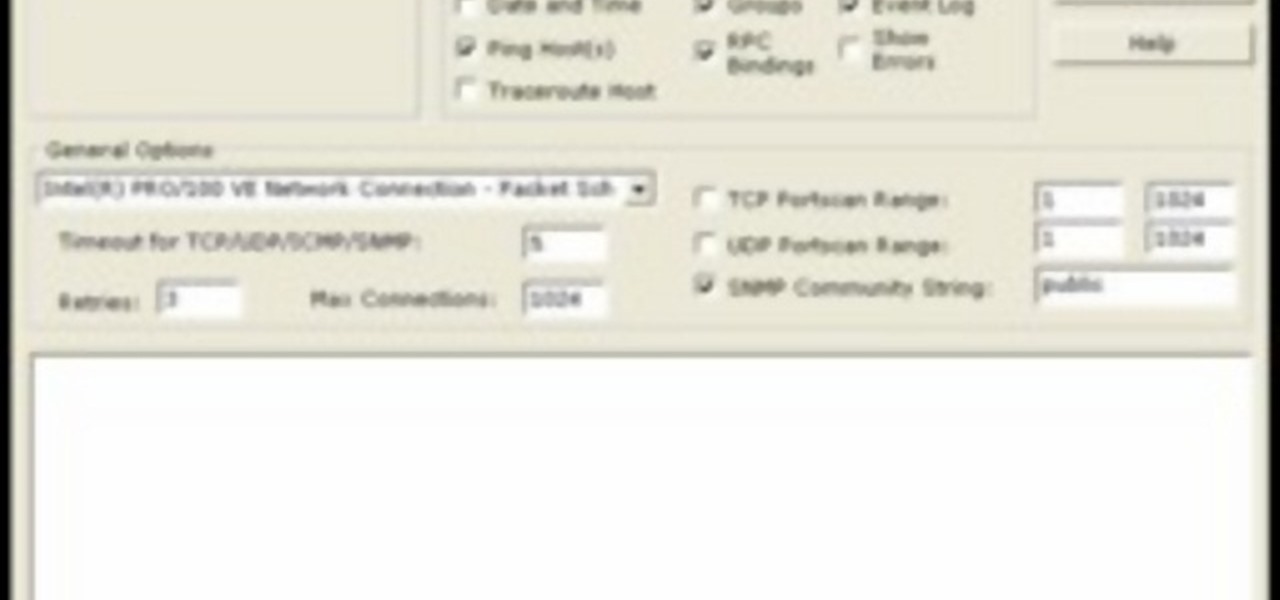
The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

This tutorial demonstrates how to use Disk Utility to verify and repair disk permissions and how to verify your hard drive.

In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

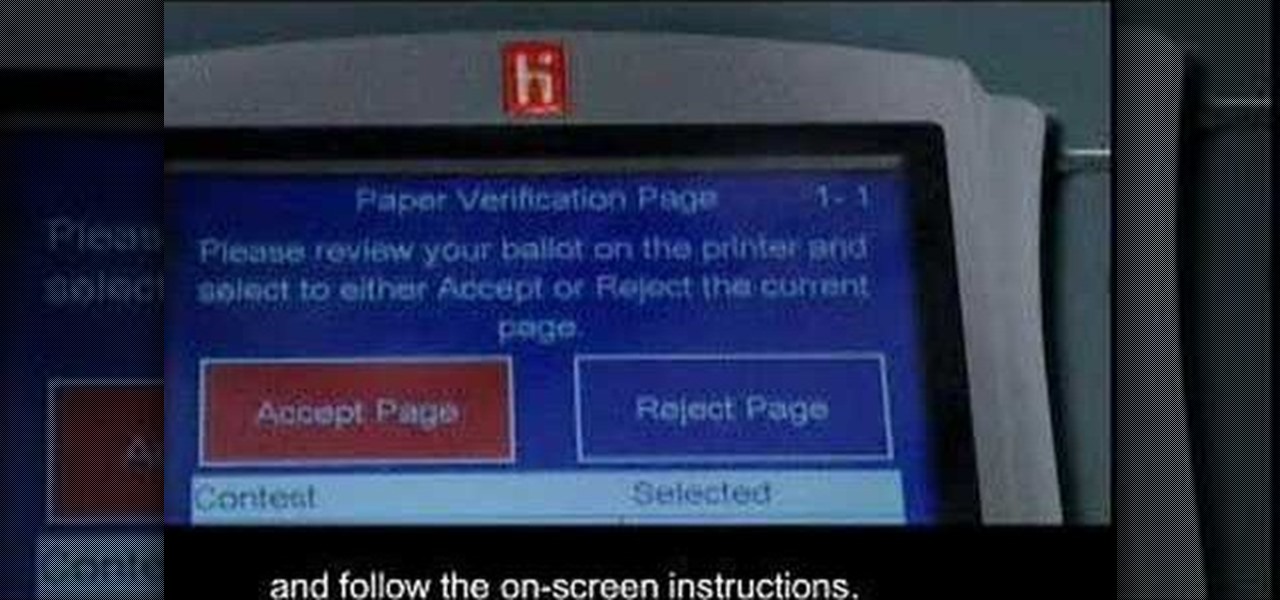
This is an instructional video on how to vote using the popular eSlate electronic voting machine with VVPAT (voter verifiable paper audit trail). eSlate is an electronic voting device made and distributed by Hart InterCivic.

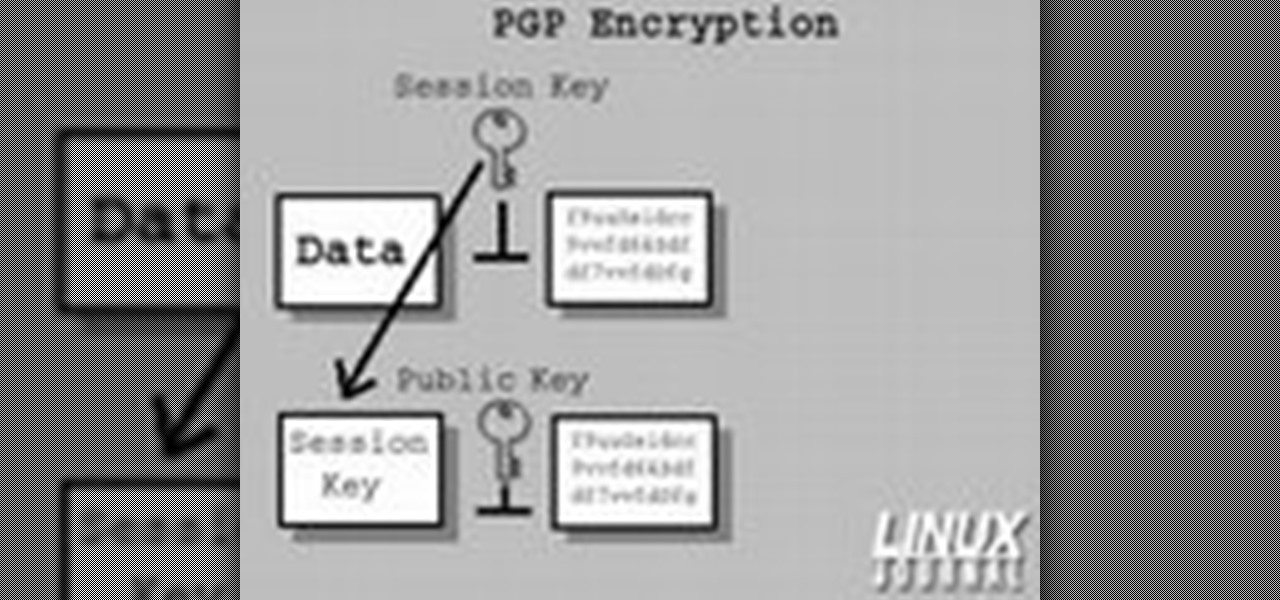
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

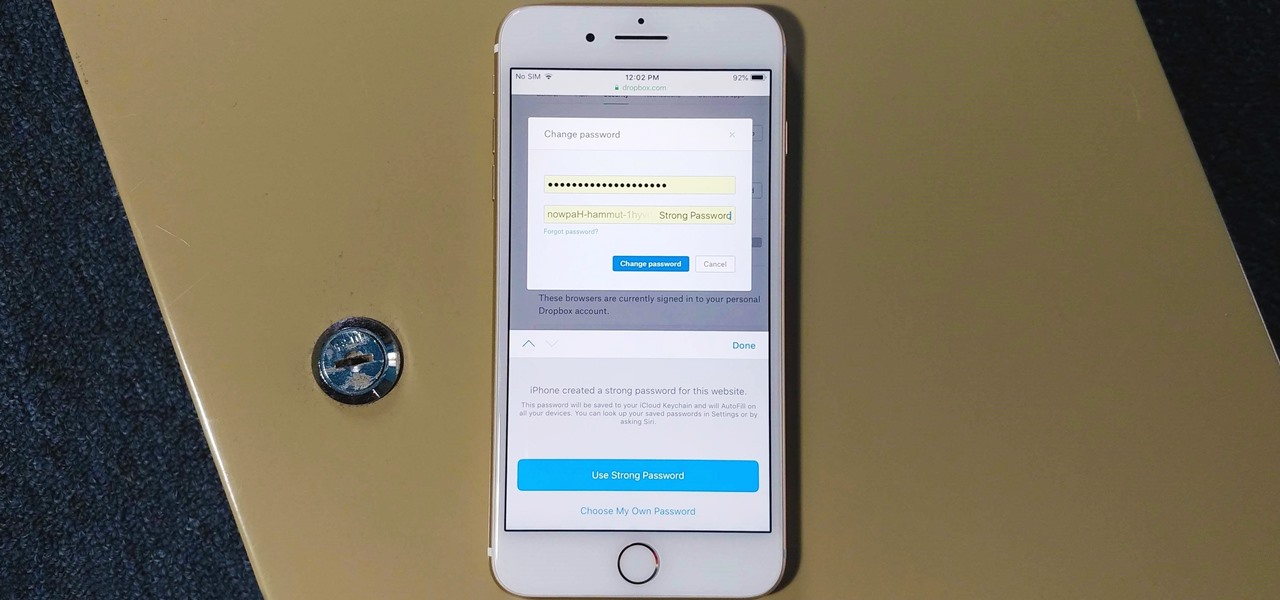
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

If you've received a spam message in Signal Private Messenger, you know that anyone can contact you as long as they have your linked phone number. But when it comes to the people you're actually trying to have a private conversation with, how do you know it's really them?

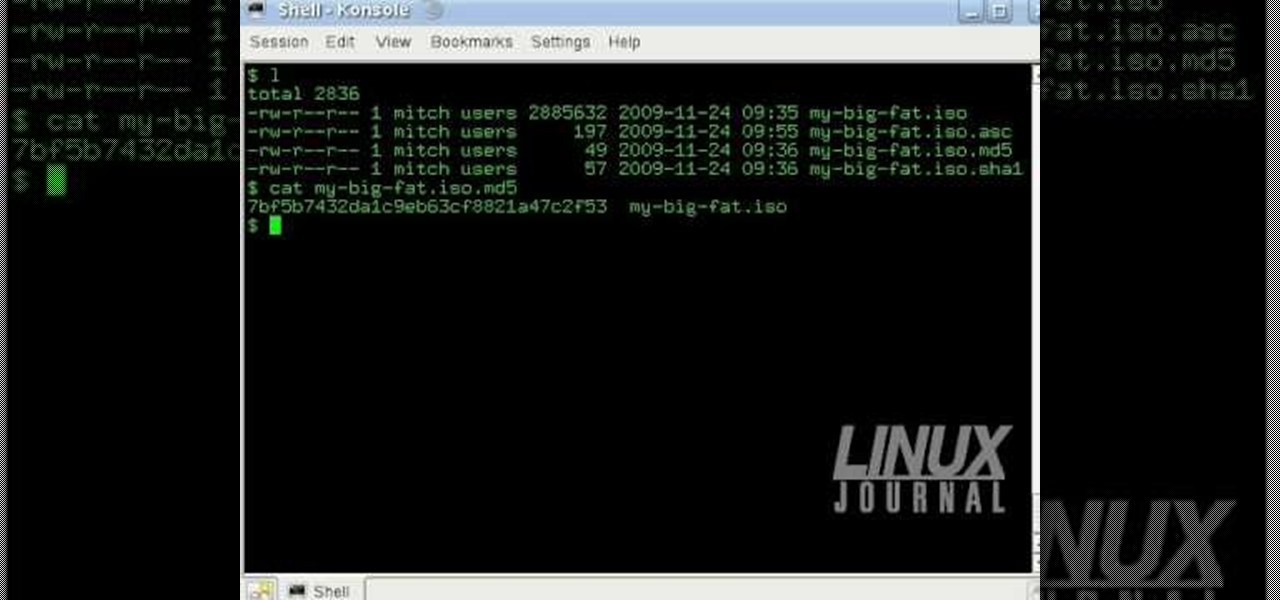
In this tutorial, we learn how to verify your ISO images before burning them. First, download the MD5 or SHA1 sum files. These will be able to verify your files are successful before you burn them to a CD or DVD. You can look at the different files to see what is inside them by typing in the name of the file and wait to see if it says it's okay. If it has something wrong with it, it will tell you something is wrong, then you can avoid downloading this and burning it for a CD or DVD. This is a...

Have you ever wanted to be famous? Of course you have! Now you can make your Twitter profile look like it's verified, just like professional skater Lil' Wayne. With Twitter's new header, you can now upload a cover photo onto your profile to be seen online and on mobile devices. Just click here and change your header with the images below to get "verified" in seconds! Note that this will not work on the newer Twitter profile designs, since the verified symbol is located outside of all images.

I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.

Preserving the environment is not only the right thing to do—it can result in significant cost savings for your business.

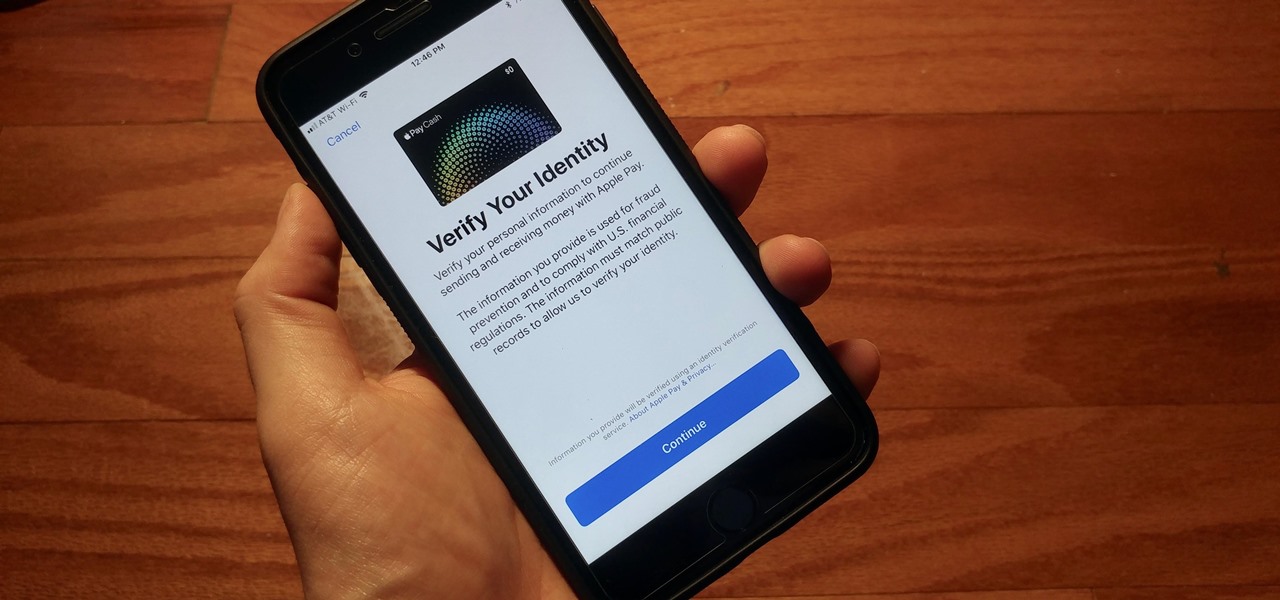
With iOS 11.2's introduction of Apple Pay Cash, you can send and receive money to others directly through iMessage, using the convenience and security Apple Pay is known for. However, if you want to make sure your efforts go uninterrupted, you'll want to make sure you verify your identity with Apple.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

In this tutorial, we learn how to optimize a PDF document in Adobe Acrobat 9 Pro. This will adjust the size of the PDF to better adjust your need and work flow. Fire, go to file and then go to properties, then you will be able to see what size the file is. If you would like to change this, go to the PDF Optimizer, which has an "audit space usage" button. From here, you can change the compatibility level and also change the compression and the color bitmap resolution. After you are done editin...

Are your electricity and water bills comparable with that of Raging Waters? Then it's probably the right time to consider how to save on your energy and water bill by taking small steps like assessing where you're at in your home, having an energy audit, and eliminate leaky faucets.

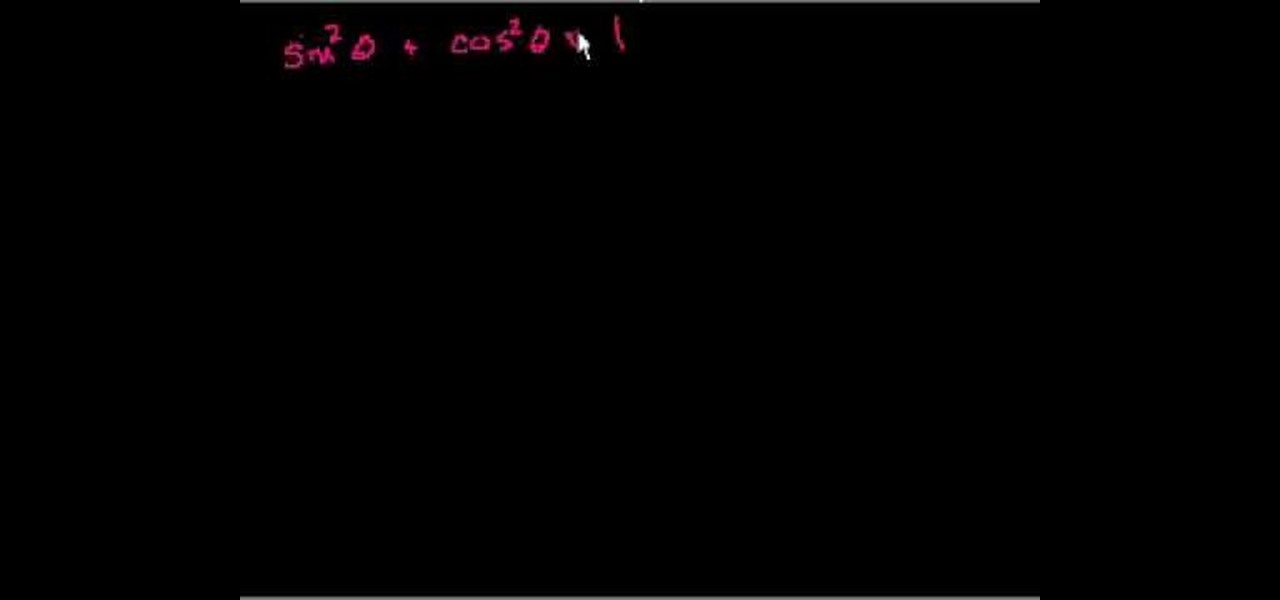
Need help wrapping your head around trigonometric identities? Watch this free video trig lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll l...

This video is about burning a DVD using Nero. On menu bar choose create/edit. Select audit, edit and capture video in dialog box. Nero vision 5 appears. Go to DVD dialog box. Choose where you will import video from. Drag video into open screen. For best quality keep video size to 1 GB. You can add titles, edit or create chapters. Click next. Choose a category which are choices of how the video will appear. You can customize text and audio in this screen. Click next and view the final product....

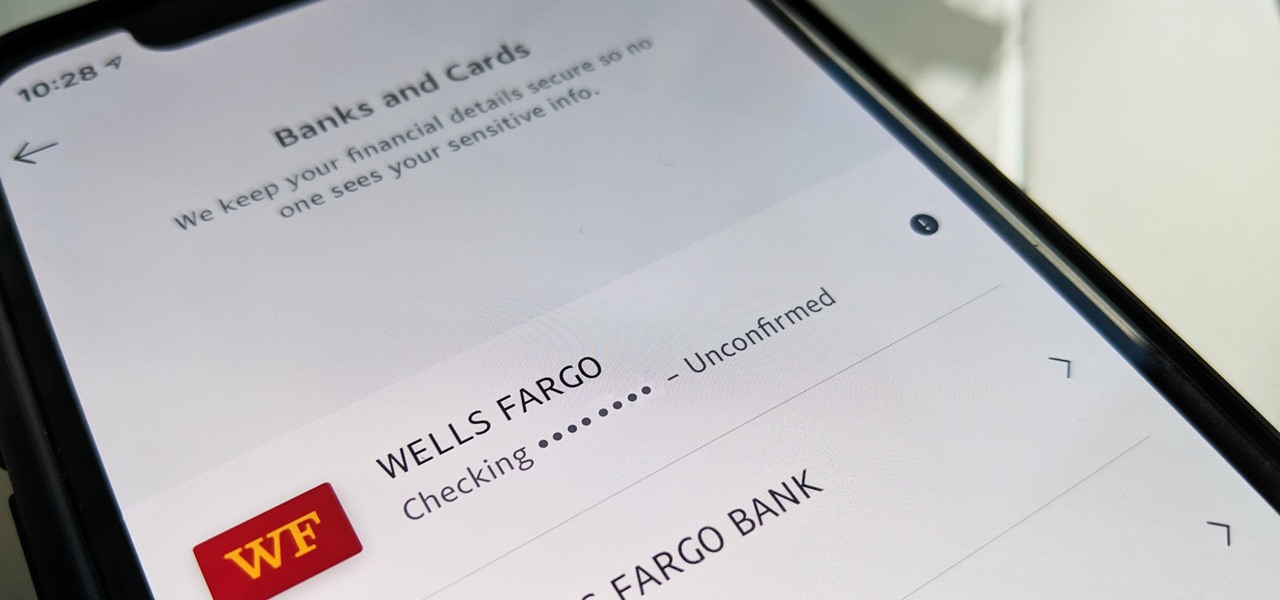
PayPal is one of the most popular payment systems across the globe. It makes payments fast, easy, and secure, and with 250+ million users, it's not going anywhere. If you're new to the online service, one of the first things you should learn is how to add your bank account, credit card, or debit card to PayPal, and make your life easier when it comes to online payments and withdrawals.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

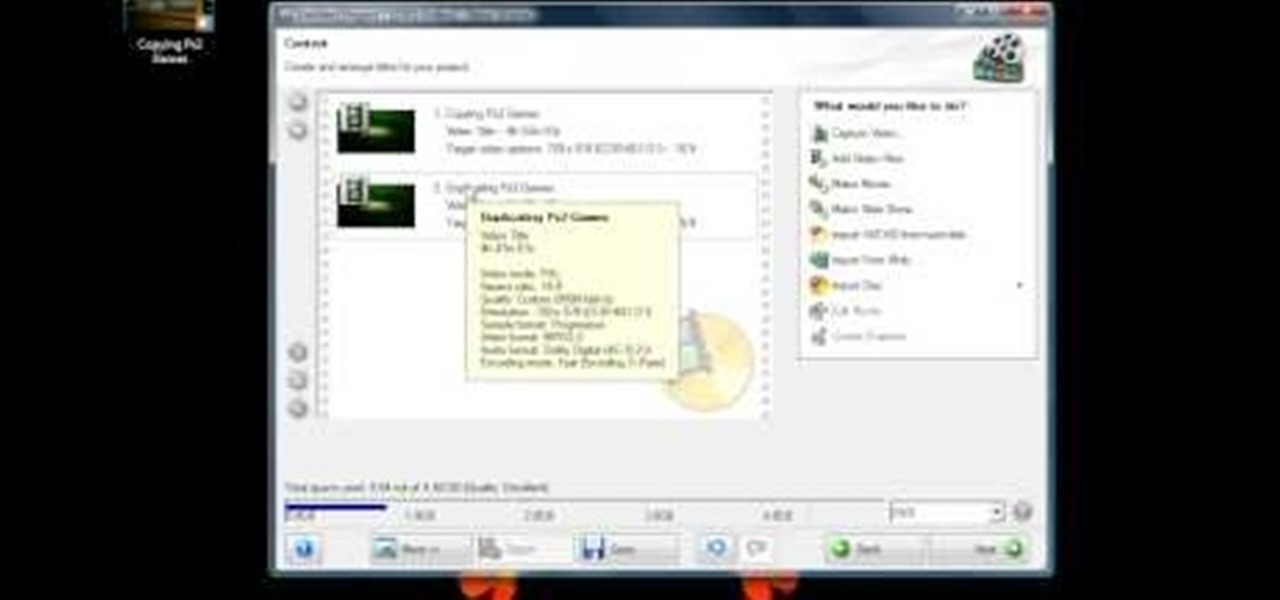
In this tutorial, we learn how to burn .iso image files to a CD in Windows XP. To start, you will need to first burn the image with Image Burn 2.1. Decide if you are going to use a CD, DVD, or multiple CDS. If you don't already have Image Burn 2.1, you can download it from this site: download.imgburn.com/SetupImgBurn_2.4.1.Â0.exe. Once it's installed, you can make a copy of your image and then verify it when it's finished. It will go through the burning process, which will take from 2 minute...

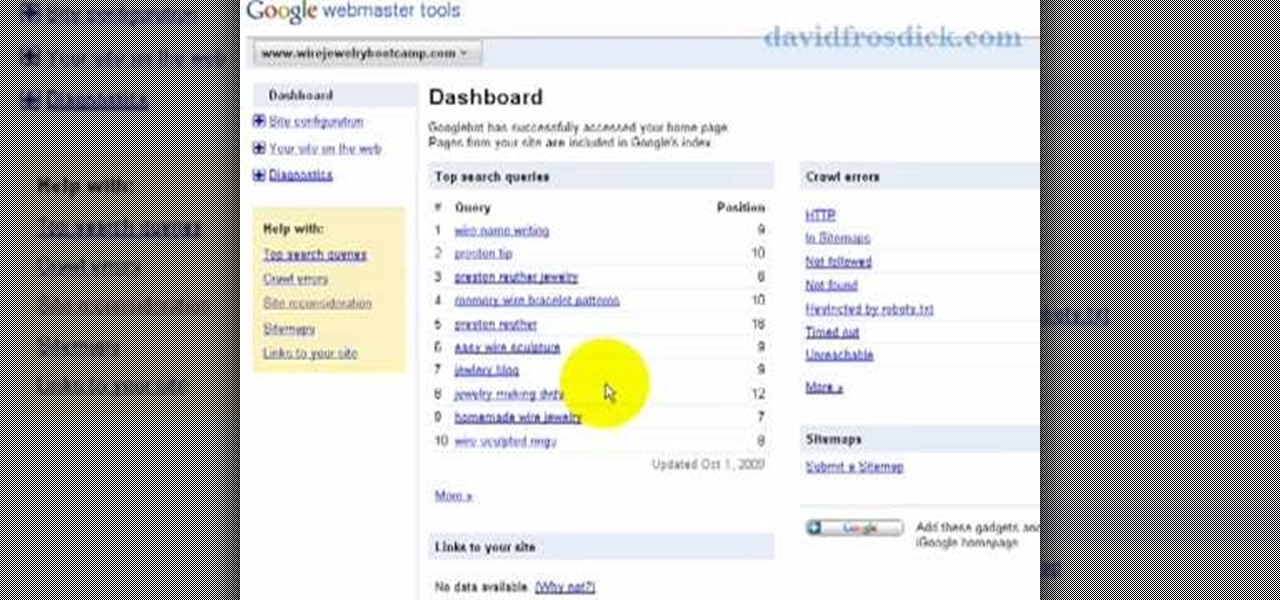
In this video tutorial the instructor shows how to submit your website to Google and its search engines. To do this first you need to have an account with Google. If you do not already have one go ahead and sign up for an account with Google. Now search Google for the webmaster tool. Then it opens the Google webmaster website which you can enter with your Google user name and password. Now inside there is an option to add a new website. You can type in the URL of the website and submit. Now G...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 311th installment in their series of digital spreadsheet magic tricks, you'll learn three different methods for determing whether a Produt ID prefix matches a second specified prefix.

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to add your site to Google Webmaster Tools.

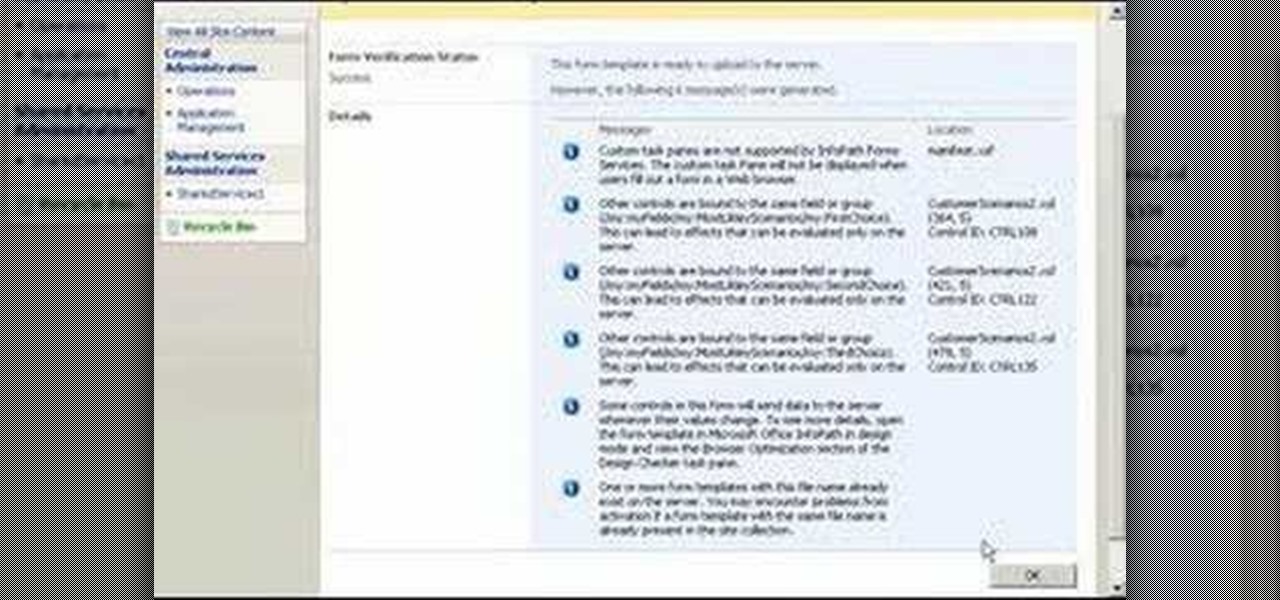
Now you can enable users to fill out Microsoft Office InfoPath 2007 forms by using a Web browser, which makes your forms more accessible to a wider audience. This instructional video shows you how to go through the process an IT Administrator can use to verify, upload, and activate an administrator-approved form template on a Microsoft Office SharePoint Server 2007 site.

Estimates say that there are roughly 441 million Apple Pay users in the world, but with almost a billion active iPhones in the world, some of you have yet to jump on board the digital payment method. But once you're ready — or if you just need a refresher — adding your debit and credit cards to Apple Wallet is simple.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

As you're probably well aware by now, the Apple Watch isn't just for sending text messages and checking Instagram—you can also use it as your wallet. With Apple Pay compatibility, you can use your Watch to make purchases at any retailer that accepts the payment service.

Netflix releases monthly reports on major ISPs relating to how well their service works on each provider. The purpose is to educate the public on their choice of service provider, but since many of us hardly have any choice at all when is comes to an ISP, it backhandedly works to shame them (if they're even capable of feeling shame under all those millions of dollars).

For the longest time, the only clickable link you could throw up on Instagram was in your profile's bio, and that's still true for a lot of users. The only way to add a clickable link aside from the aforementioned one is in an Instagram story, where users checking out your story would swipe up to load the webpage before going back to finish your story.

Okay, so this doesn't exactly teach you how to audit as a Scientologist... but I think it is the closest to an explanation we are going to get. So, listen up & try to learn.

In this clip, you'll learn how to utilize the ISO Verifier application to verify your disc image files. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

In this ten-step video tutorial, you'll learn how to quickly copy keys using a camera, printer and Dremel tool. With this ten-step process you'll learn the necessary steps to copy almost any key... even if you only have access to it for a brief period of time.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!