Apple may have unabashedly lifted their upcoming "Control Center" from Android devices, but visually speaking, it's an awesome take on Quick Settings that would look pretty good on a Samsung Galaxy S3.
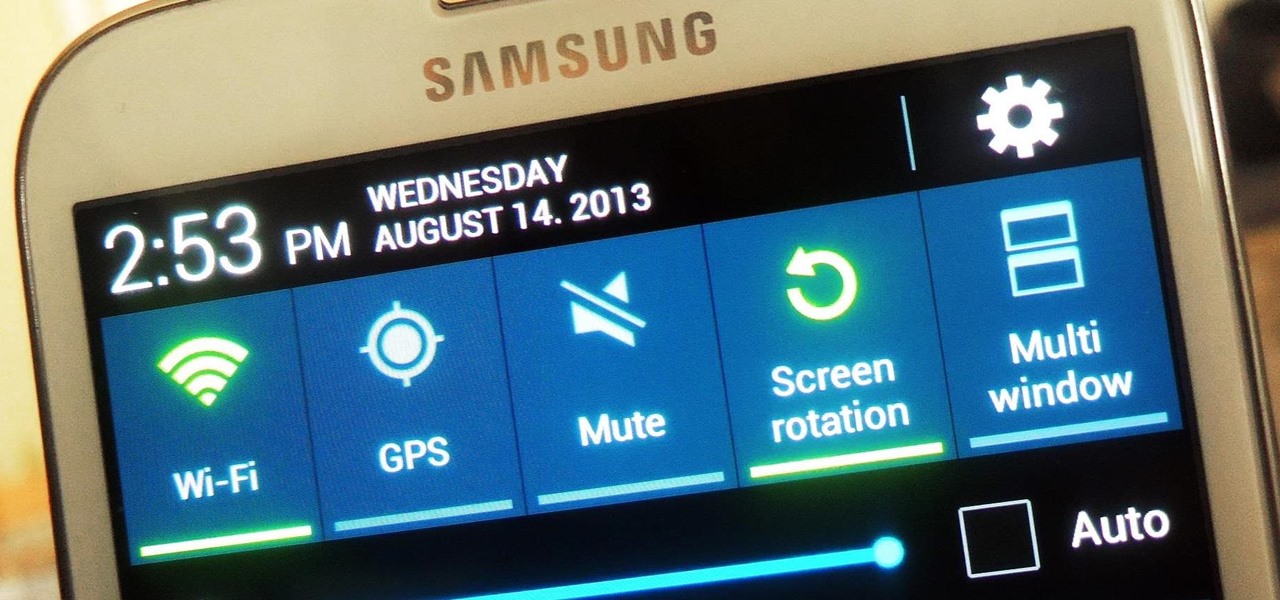
Controlling the screen rotation on your Samsung Galaxy Note 2 is one of the easiest things you can do. Just slide down the Notification tray and you have instant access to the Screen Rotation toggle in the Quick Settings menu. If you want your screen orientation to automatically rotate when you move from vertical to horizontal positions, just make sure it's turned on. To lock the current orientation, turn it off.

Google's long awaited 4.3 Jelly Bean update is officially out, only it has not been pushed out to some of our Nexus 7 tablets yet. Although there aren't really any new UI changes, most of Jelly Bean 4.3's magic is under the hood, meaning user's can expect better performance and battery life with the latest version.

While it may not always be practical, controlling your smartphone with air gestures can be pretty awesome. I would bet that if someone in public saw you using gestures to maneuver through your device, they'd be pretty impressed—and also kind of creepy for watching you.

A few weeks ago, Bluebox Security uncovered a bug that could potentially effect 99% of Android devices. Bug 8219321, dubbed the Master Key bug, works by allowing applications with modified code to pass Android's signature verification system, thereby bypassing security measures that normally wouldn't allow these apps to be installed.

There are a ton of options available to Android users when it come to messaging, but the problem is that with all of these options, where is the go-to app? The one used by most people? The one that can offer a more unified approach?

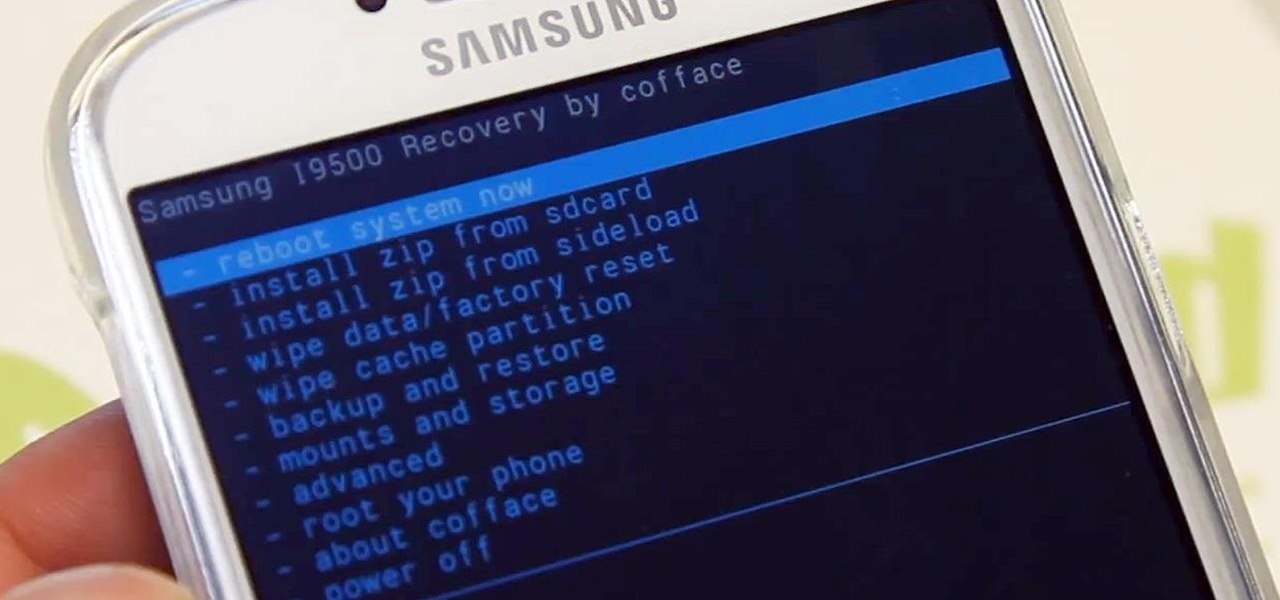
Ready to start rooting your Samsung Galaxy S4? For those of you with the GT-i9500 model GS4, this quick video will walk you through the entire rooting process using Odin and CWM.

Something went wrong and your Nexus 7 is freaking out on you. Maybe you flashed a bad ROM or ZIP file, or maybe it's just bugging, and it's time to restore your tablet back to a working condition. Thankfully, you've already made a backup of your Nexus 7!

WhatsApp is a very popular messaging app on the Play Store, but unfortunately, tablet users have been left out of all the fun because WhatsApp only works on smartphones—until now.

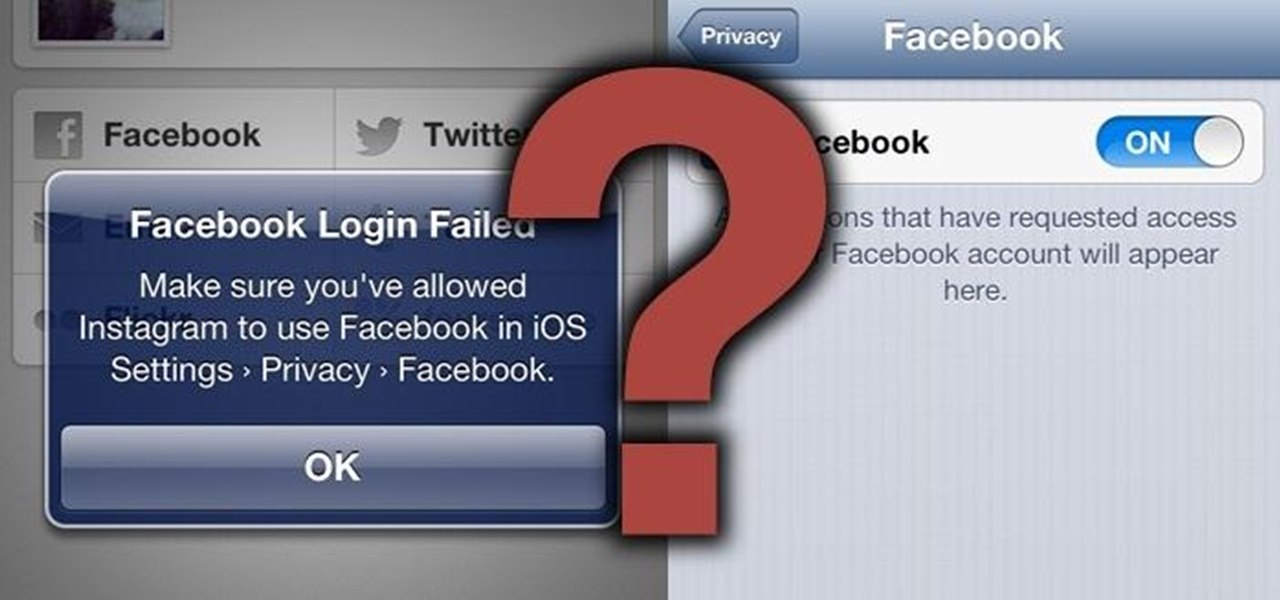
I recently ran into a problem connecting my Instagram app on my iPhone 5 to Facebook, and neither Instagram's or Facebook's help pages were as helpful as they claim to be.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

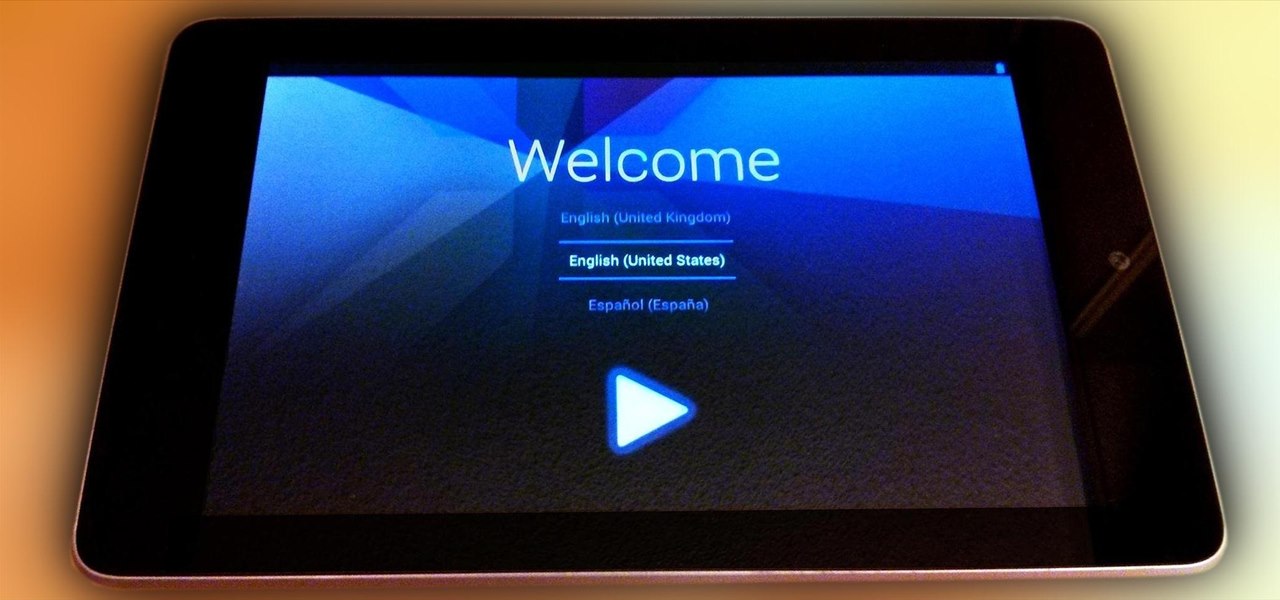
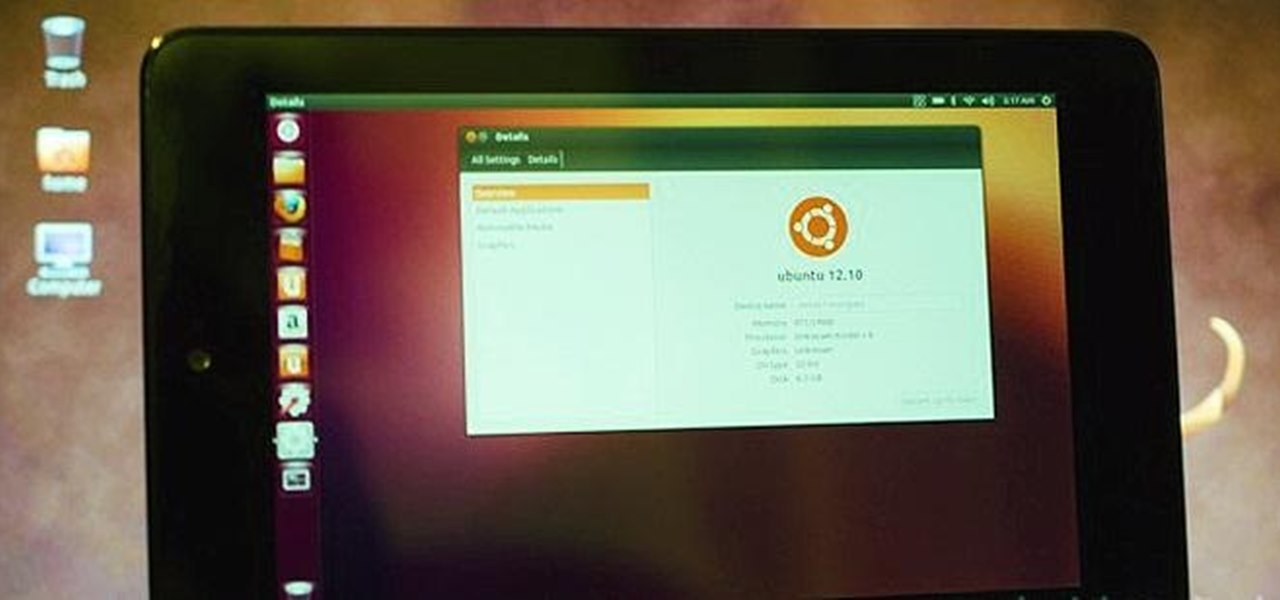
There's over 20 million people out there who use Ubuntu as their main operating system, and the number is steadily increasing due to its thriving community. While it's easy enough to download Ubuntu on your PC, the process to get it on your mobile devices can be fairly more difficult. Thankfully, it's not the hard to get Ubuntu onto your Nexus 7 tablet, but first you'll need to unlock it.

Here is how you can build a frame for your MEGA SOLAR SCORCHER in under an hour, and for less than $8!! This is effectively a 4 foot magnifying lens that concentrates insane amounts of heat from the sun. What would you do with all this free solar power? My design for this custom "Scorcher Frame" is easy to use, and incredibly cheap to make, as you can see in this step-by-step video.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

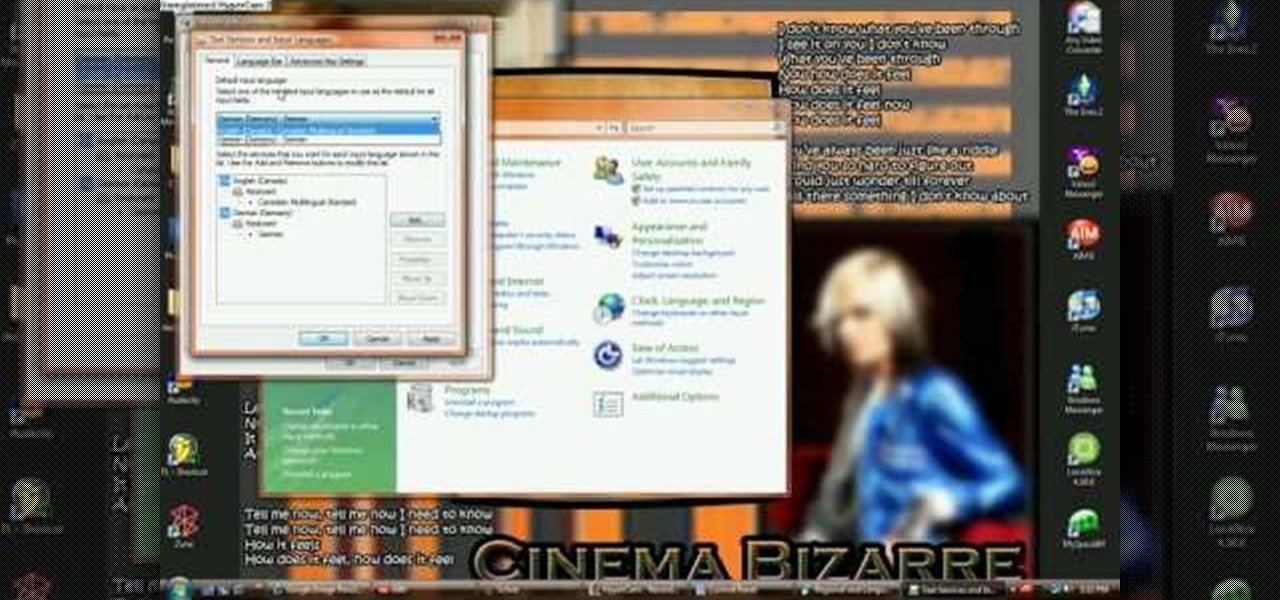
Mrs. Victoria explains us how to change the language on your Keyboard (Windows)1. Go to the control panel and select the option ‘Change keyboard or other input methods’ and a dialog box (regional and language options) pops up.2. Click on change Keyboard, and another dialog box pops up.a) In the new dialog box, click ADD Button, and select the input language you require and click OK.3. You have the feature to alter your language input whenever you want by coming to this (Change keyboard langua...

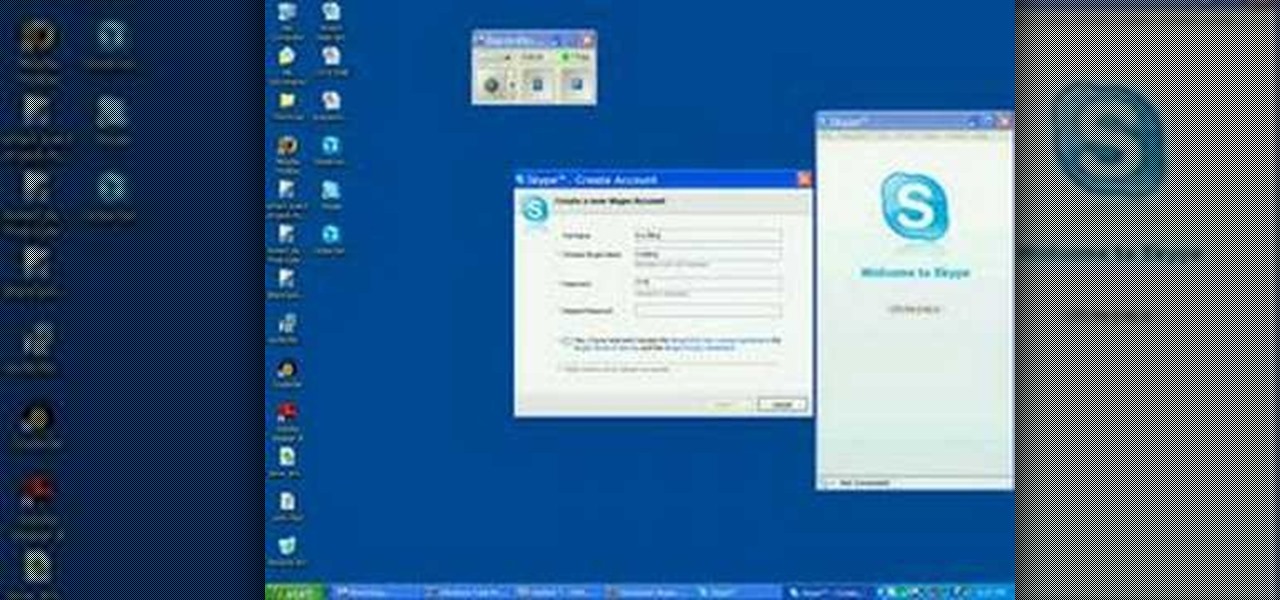
To first get a Skype account you will need to go to Skype and download Skype onto your computer. To download the program click on your operating system and download the proper program. Once it is download you can click on the downloaded file and click on install. It will take a few minutes to install onto your computer. Once it is installed you will be prompted to make an account. To make an account you will have to enter your full name, and your desired username. You will also have to type i...

With the prestige appeal of its original programming and relatively low subscription price, Apple TV+ is one of the more appealing streaming options out there — and you don't need an Apple device to subscribe and watch movies, TV shows, sports, and other Apple TV+ content.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

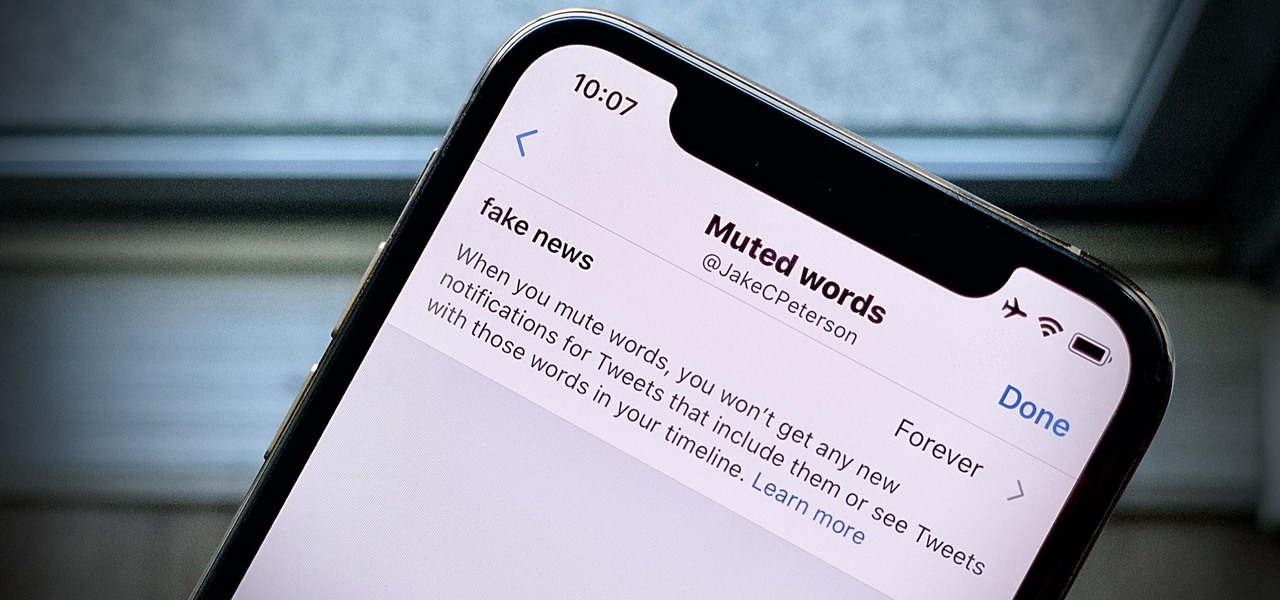
Fake news was one of the main driving factors for Google News taking its current form. It offers verified sources to ensure more accuracy in your news feed to help control the spread of false information. Something you may not know, however, is that you can view your favorite Google News topics from your home screen with a single tap.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

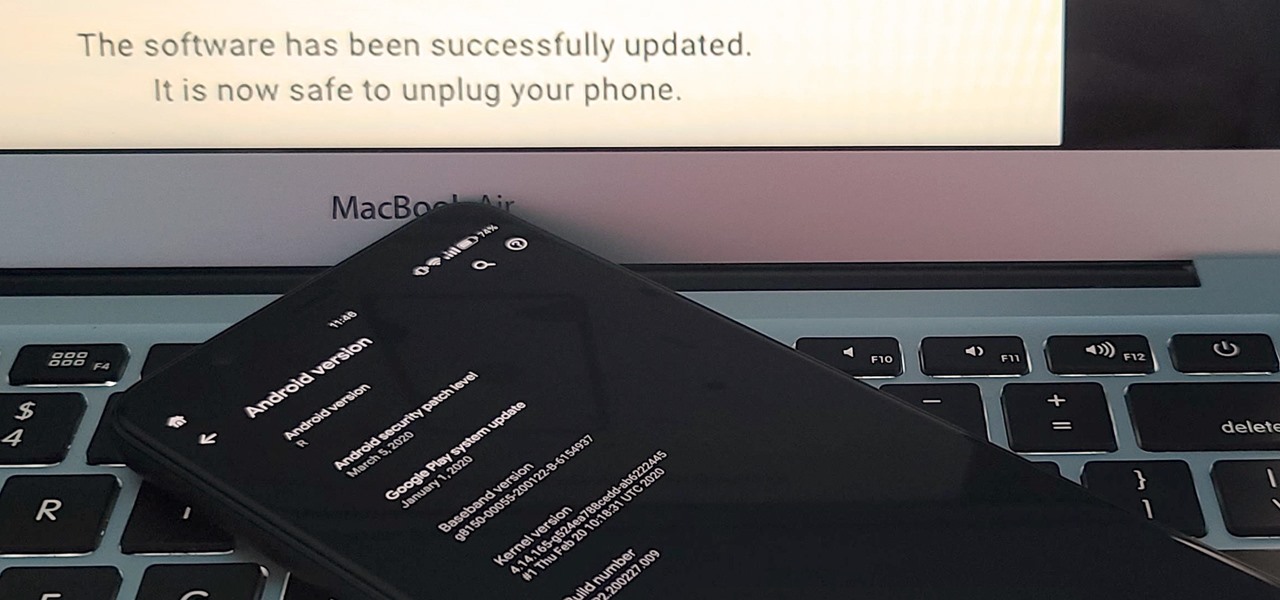
If you've ever tried to update your Android phone manually, you know the process can be unnecessarily hard. There are so many steps and parts, that if one thing goes wrong, the whole process doesn't work. Recognizing this, the Android team came up with an even easier way.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

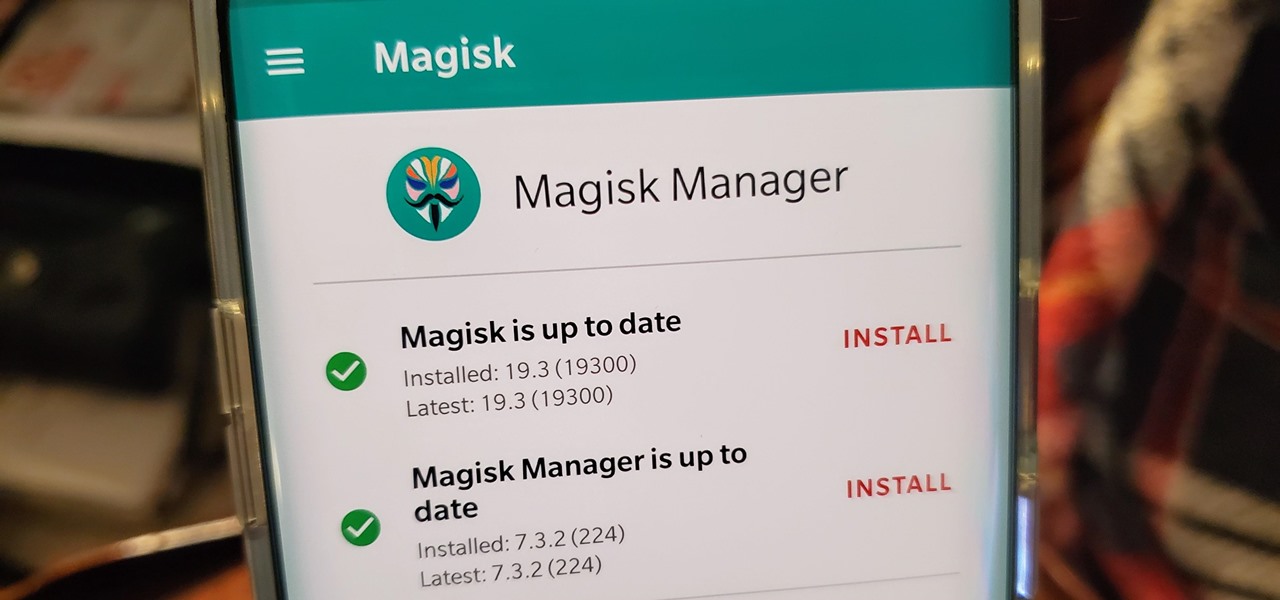
The Pixel 4 is one of the most talked-about phones of 2019, so you know there will be lots of third-party developer support. Mods are already popping up, so you'll want to get Magisk installed as soon as possible to get root access. The current method used to gain root is the quickest way yet, thanks to the recent TWRP custom recovery support for the Pixel 4.

You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

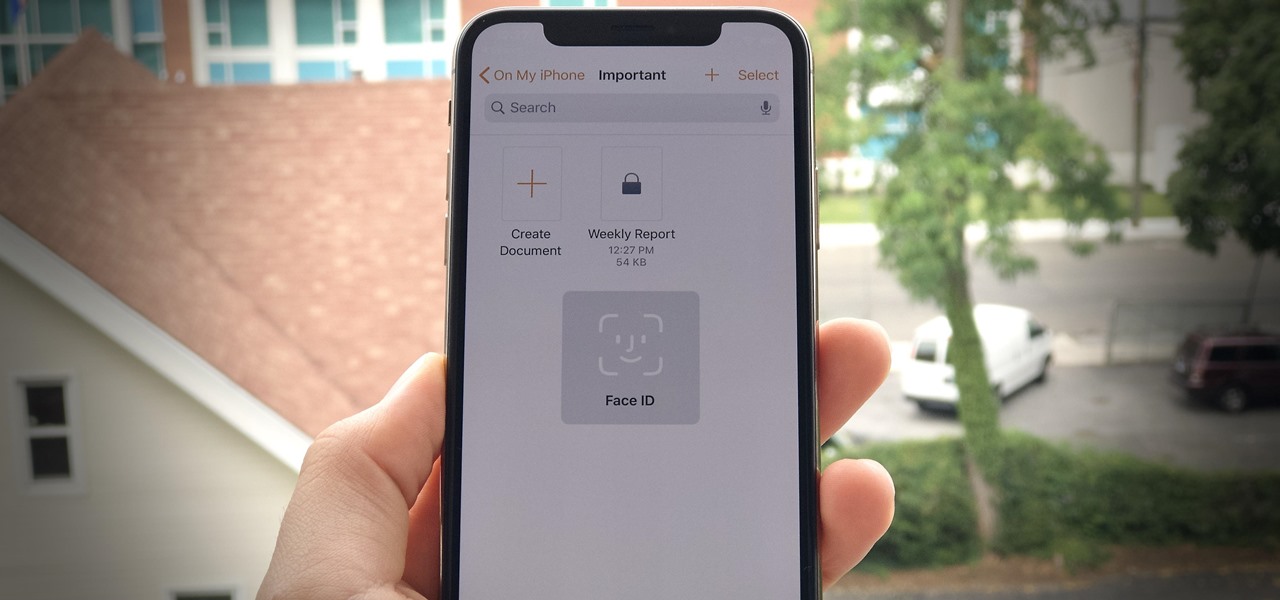
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.

OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.

The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.