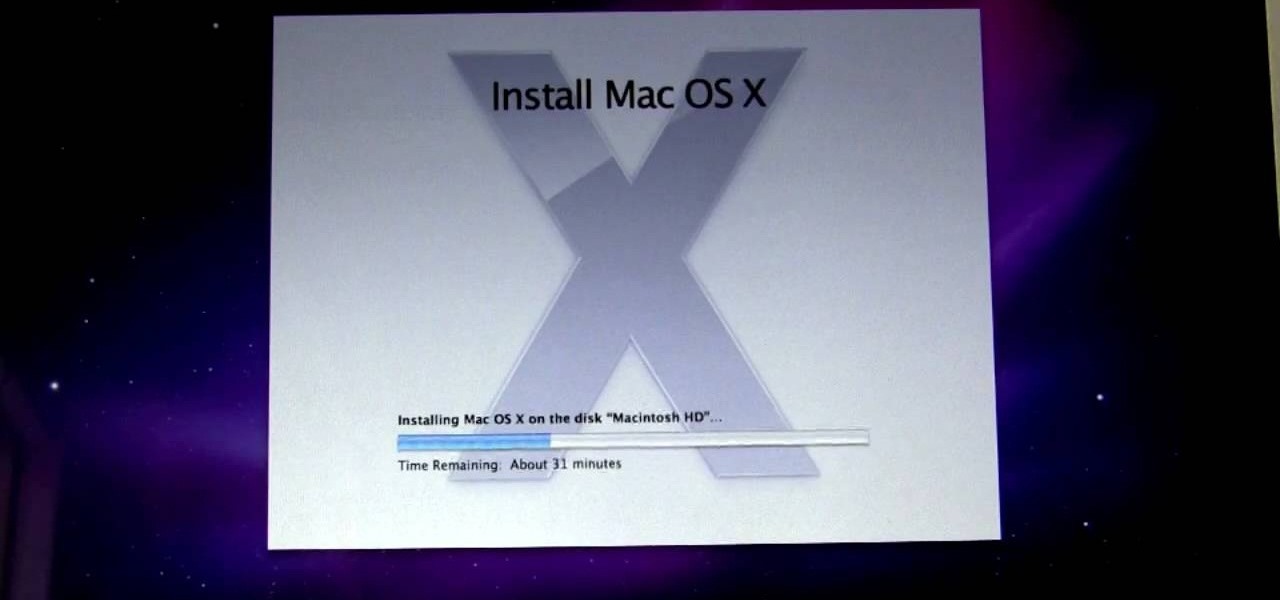
Michael of michaelsherlock.com demonstrates the installation of Mac OSX Snow Leopard onto a Mac with an Intel Core2Duo processor. We're reminded from the very beginning of the importance of backing up our entire system before beginning the installation. Once that's taken care of, it's time to insert the Snow Leopard disk. Once the disk is loaded, and we've agreed to the End User License Agreement, we are presented with a number of options to customize our operating system, including options s...
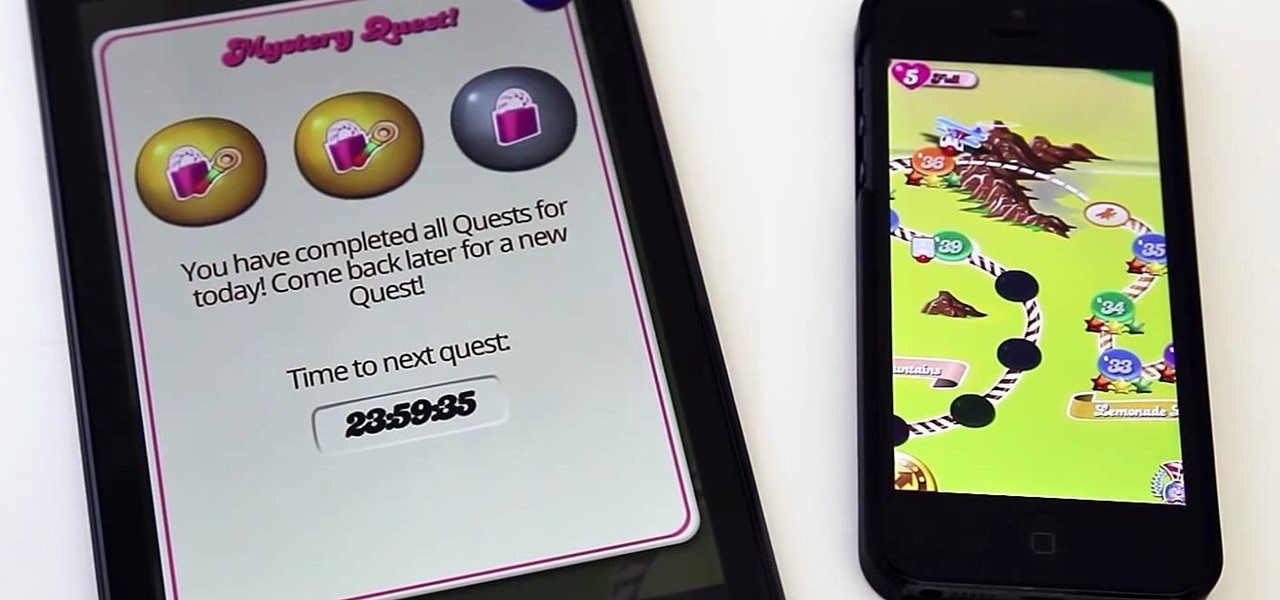
There's an easy time hack available for Candy Crush Saga that let's you bypass the time restrictions to you can play more games faster, and this video guide from KiboshGaming will walk you through it on both Android and iOS devices.
In this video, we learn how to make a blog website on Blogger. First, go to Blogger and set up your account. Make sure to enter in all the correct information, then at the end you will be sent a confirmation e-mail. Once you verify your e-mail and information, you can get started with your blog. You can set up a layout and change the font and colors as you prefer. You can start to type in all your daily blogs and have other people start to bookmark yours. You can also watch other people's blo...
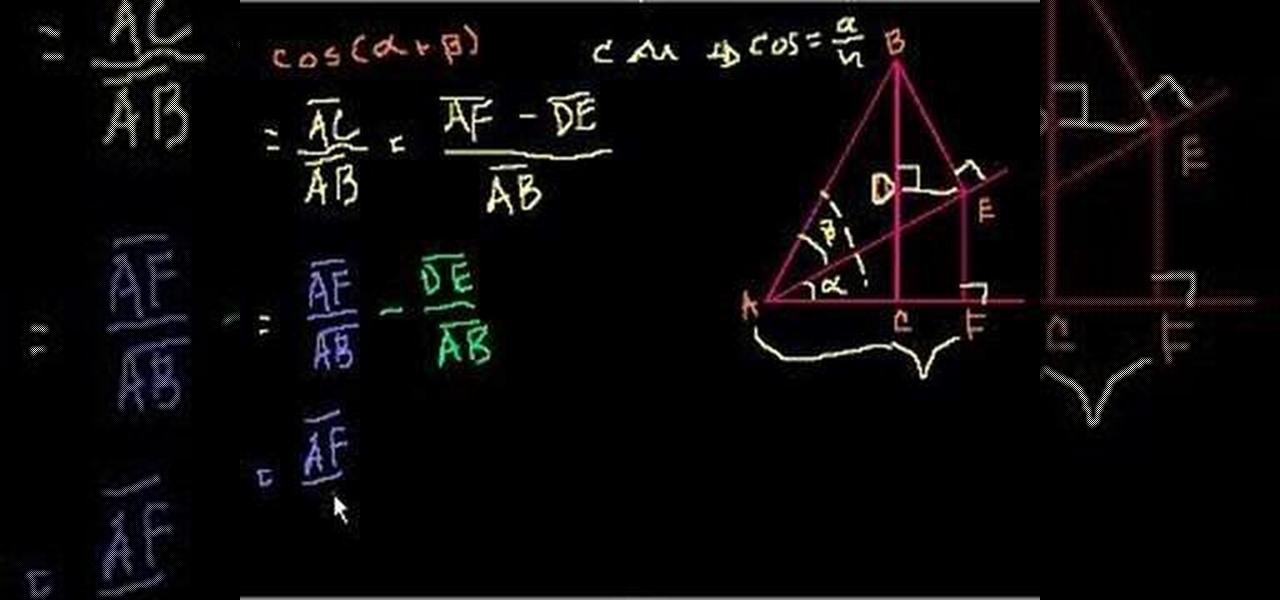
Need help proving the cos(a+b) = (cos a)(cos b)-(sin a)(sin b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series ...
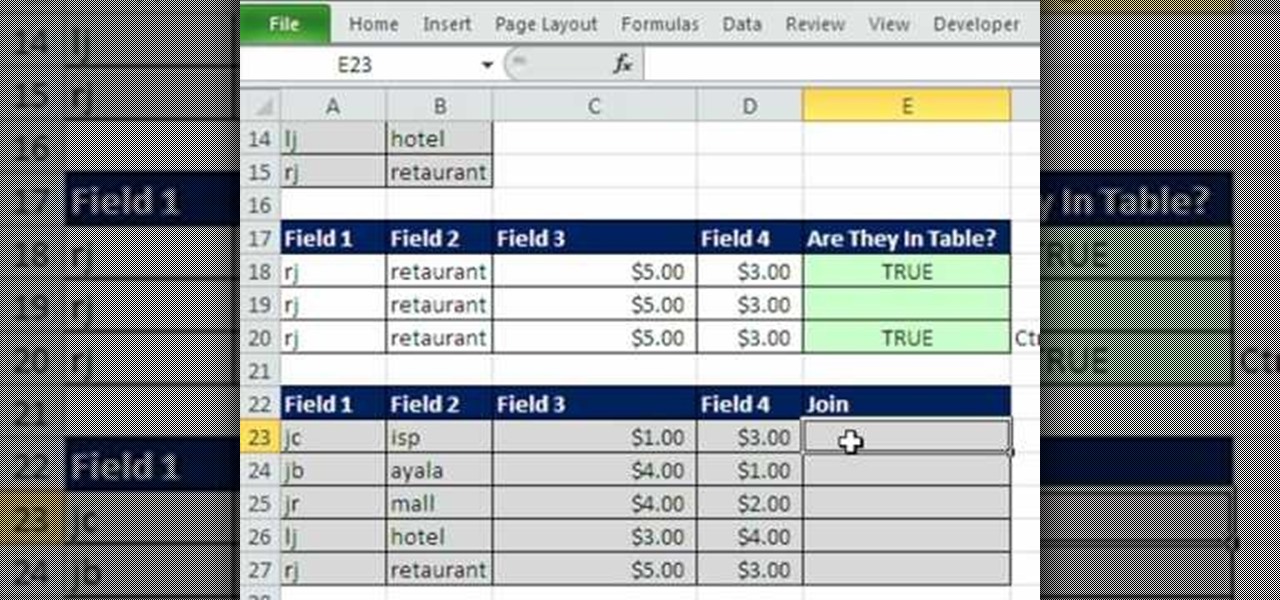
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 558th installment in their series of digital spreadsheet magic tricks, you'll learn how to check if a record is in a table using VLOOKUP. See how to do this for a 2 column (field) table and a 4 column (field) table. See also how to add a concatenated column and concatenate lookup_value in VLOOKUP function.
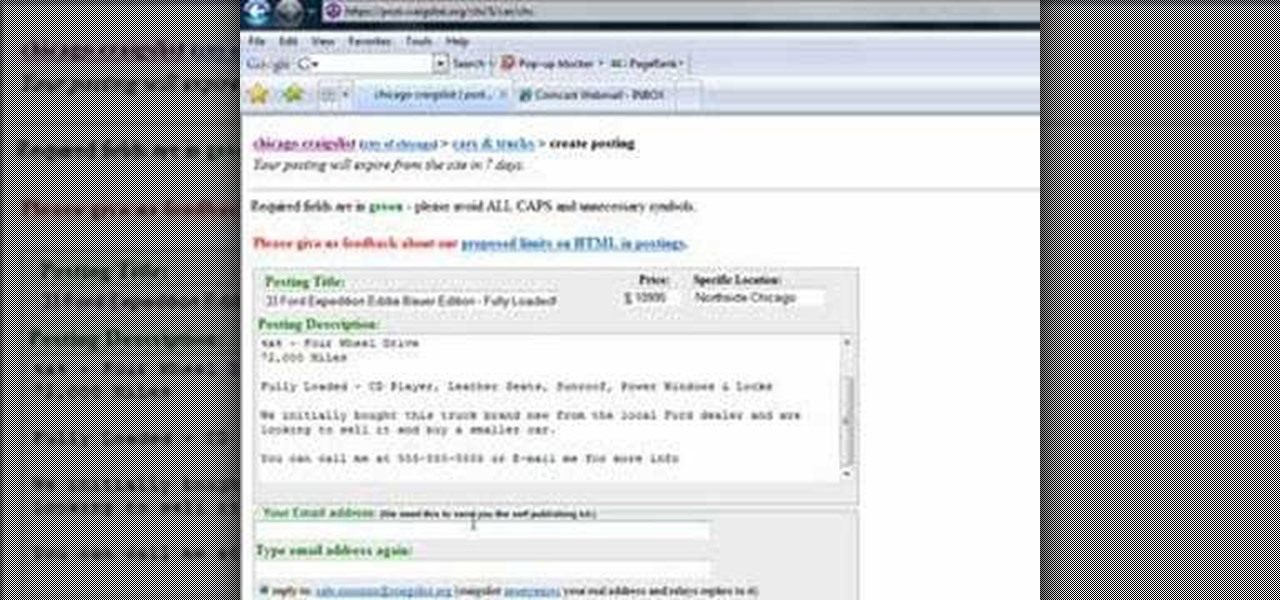
This six minute video shows you how to sell your car on craigslist. First, go to craigslist.com and click on the nearest city (or country). Follow the links to list an ad for a car for sale. You will want to put the kind of car in the posting title because that is used in sorting search results. In the posting description it is important to be as specific as possible - again describing the car, giving some history of the car like if it has ever been in an accident and if you have had any work...

When using face unlock on the Pixel 4, your lock screen notifications are bypassed by default to help you unlock your phone instantaneously. This is different than Face ID on the iPhone, which shows the lock screen until you swipe up, but only shows notifications when you've been authenticated. If you want to do it Apple's way, there are settings you can adjust on your Pixel.

The latest Google Play Services update has somehow broken major functionality in both Titanium Backup and Substratum. Titanium Backup has suddenly become stuck at zero percent while restoring, and Substratum simply fails to apply themes anymore. Both of these apps do require root, but they've slowly become essential to rooted users, especially since apps like these come into play when you're deciding what your next phone should be.

One of the biggest hits this past fall wasn't a movie, television show, or book—it was an unassuming podcast called Serial, which centered around an unsolved murder from 1999 of a high school student in Maryland.

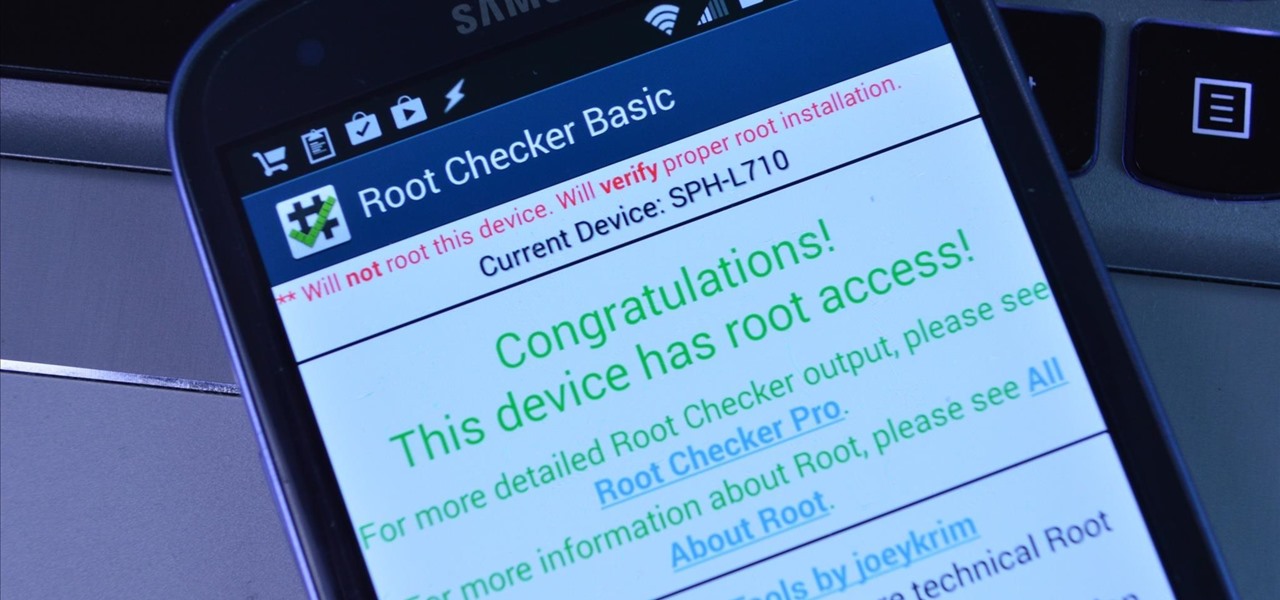
Rooting an Android device used to be a nightmarish labyrinth of .zip files and command prompts, confusing seasoned modding veterans and newbies alike. Thankfully, the process has gotten simpler over the years, with various "one-click" rooting tool kits surfacing and working for nearly every major Android flagship on the market.

Want to test whether the soil sample or a water sample contains boron, watch this video. As shown in the video, the first step is to create test specimens of various concentrations using a simple turmeric and ethanol solution as a base for comparison. The basis of this experiment is the fact that curumin present in turmeric reacts with boron to form a reddish compound and so the result of this reaction can easily be verified visually.

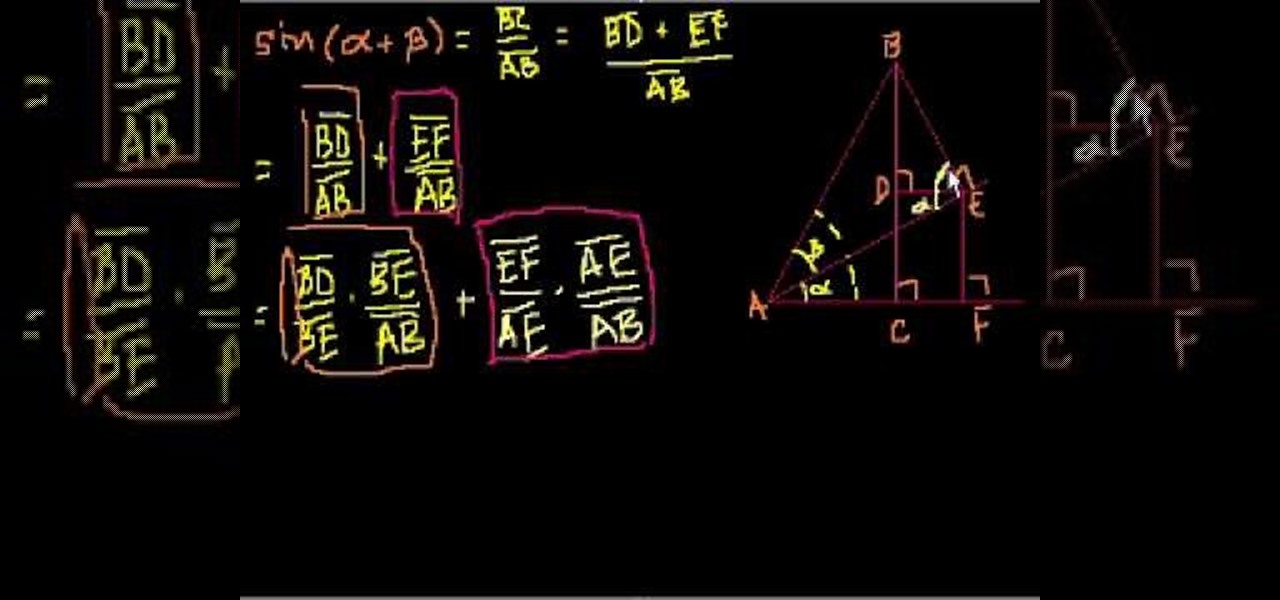
Need help proving the sin(a+b)=(cos a)(sin b)+(sin a)(cos b) trigonometric identity? This free video lesson will show you how. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of...

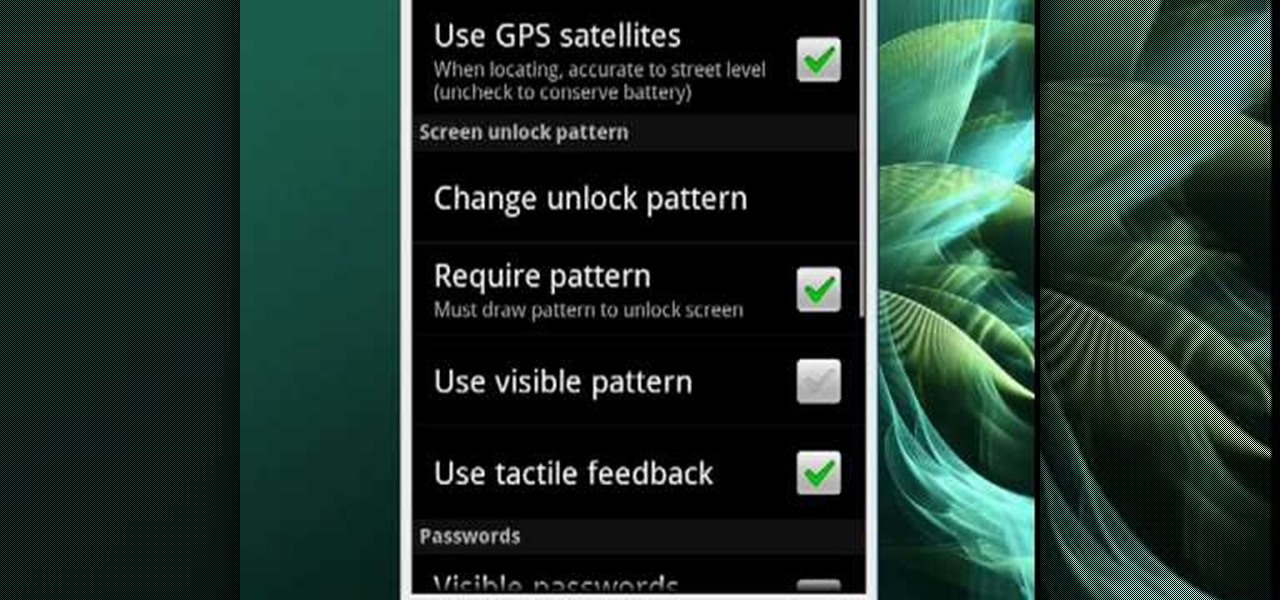
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

With iOS 12, iCloud Keychain has become a more useful password manager for your iPhone with strong password suggestions, password reuse auditing, and Siri support. However, before you jump ship from your current password manager, you should consider all the reasons why iCloud Keychain doesn't make sense as your primary password manager.

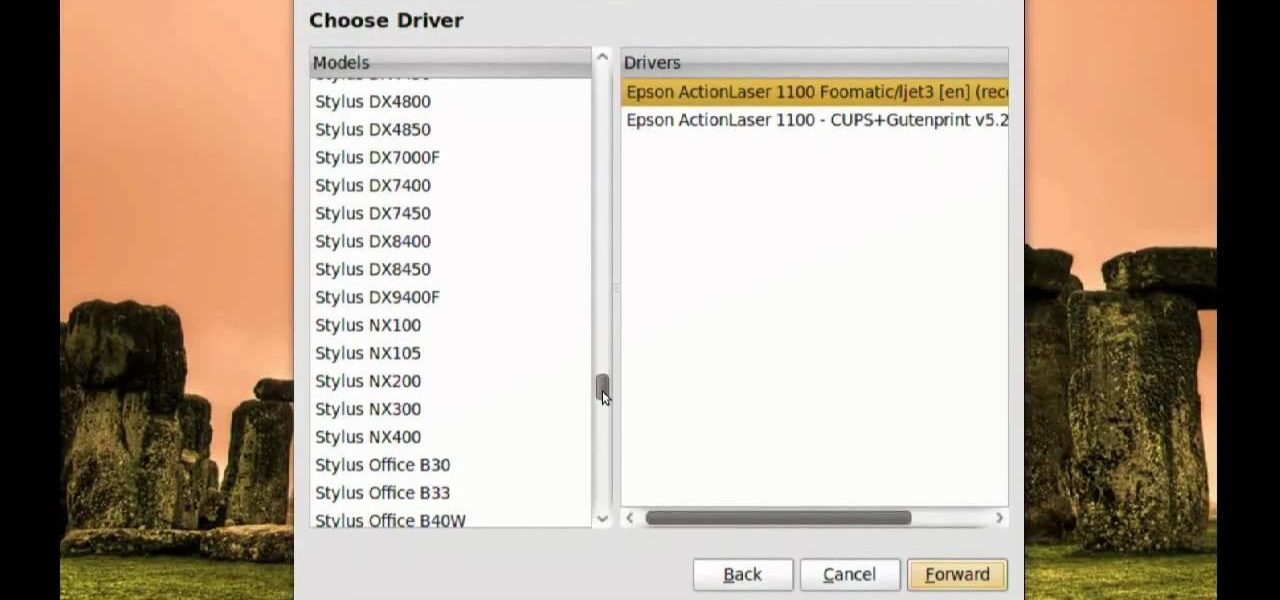
In this video, we learn how to print from a shared printer in Ubuntu. First, turn your computer on and then go to your system. From here, go to admin and then printing. After this, you will get a pop up window. Click on 'new' and then it will search for the printer. Next, you will click on 'network printers' and then go to 'windows printer via samba'. Then, click on browse and expand the workgroup. Then, expand the name of the computer and you will find the name of the computer as well. Now, ...

Solving equations involving fractional powers of a variable are not that hard to solve as they sound. In fact, just watch this video to learn a few tips and solving these type of equations will become a little bit easier.

In this tutorial, we learn how to password protect your folders on a Mac computer. First, use the spotlight tool to type in "disk" and then click on disk utility on the drop down menu. From here, go to the save as menu and enter in the name for the volume. After this, change the size of the desktop and change the encryption choice. Use the one that is recommended and then click on 'ok'. Form here you will be asked for a password, then you will need to verify that password. From here, click on...

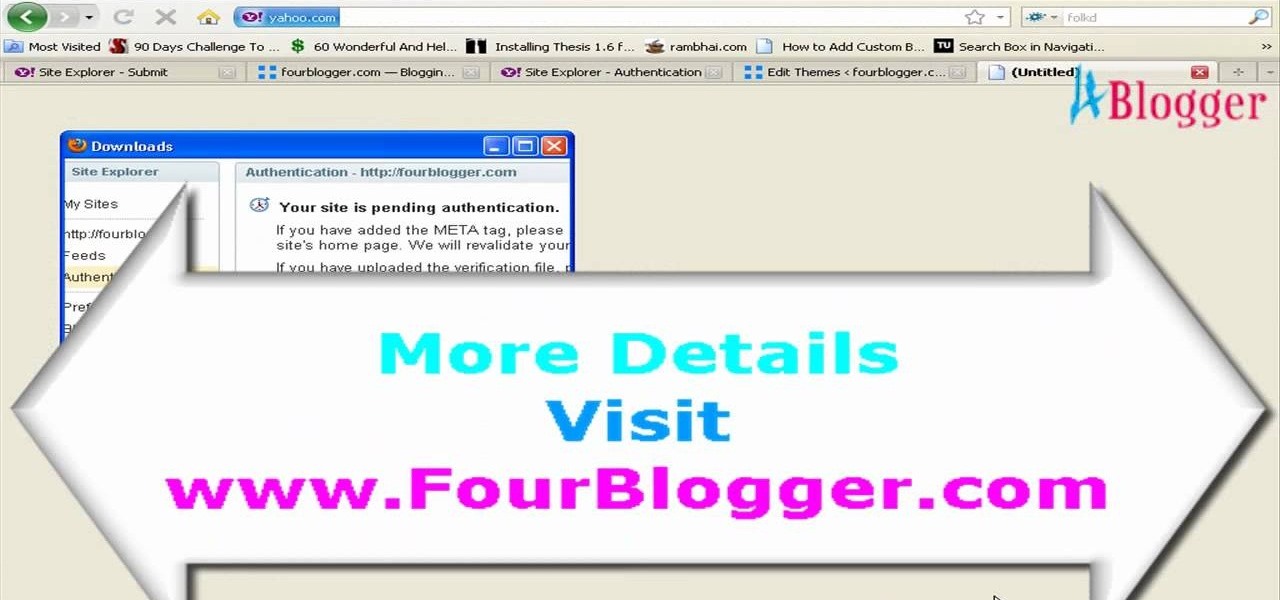
In this video, we learn how to submit your site to the Yahoo search engine. First, go to site explorer. Once here, submit your website or web page in the appropriate box. After this, enter the full URL of the site feed you want to submit. After you do this, go to the side bar and verify your site, or add a META tag, then go to your site. Now, copy the code that Yahoo gave you and paste it into your website. After you do this, your site will be submitted and you can search for it through the Y...

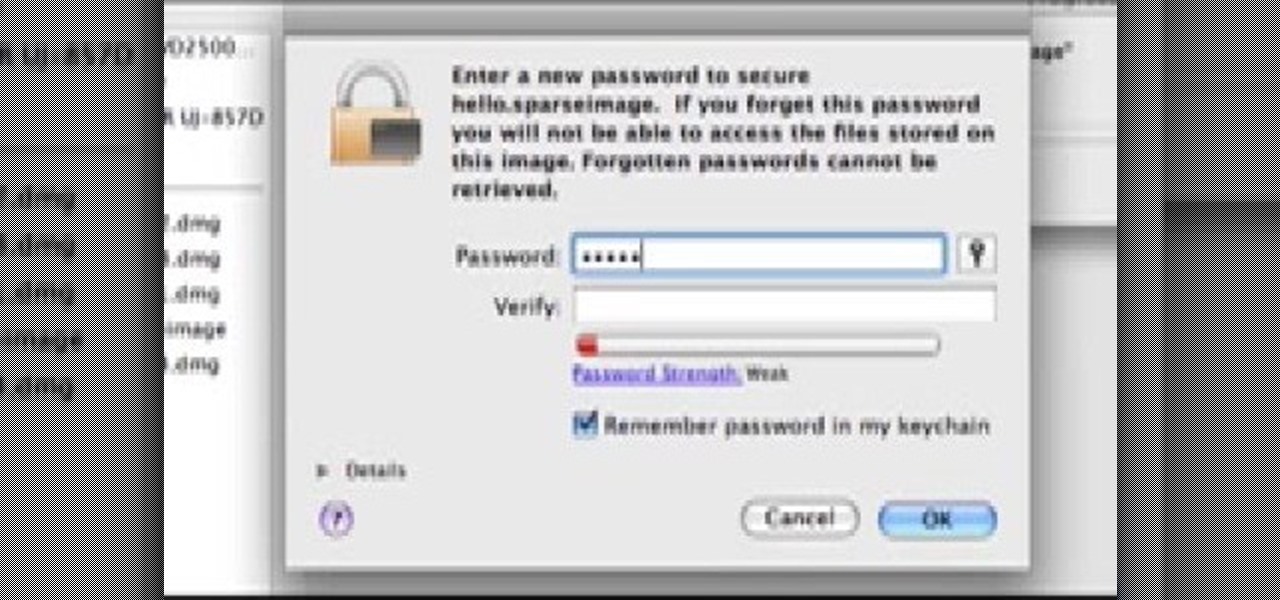
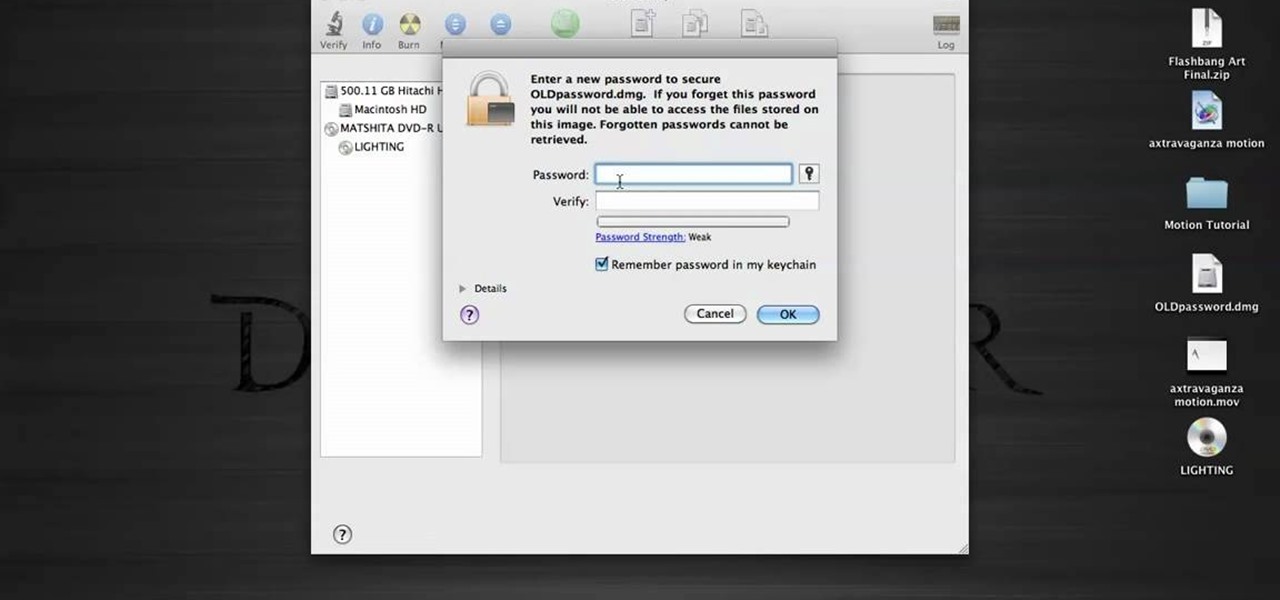
In this tutorial, we learn how to password protect a folder in Snow Leopard on your Mac. First, go to the finder and click on "utilities". Now go to "file, new, disk image from folder". Now, you can select the folder you want and then click "image". Make it a read/write folder so you still can edit the files and enable the encryption. Save this, then it will ask you for a password. Create a password and then verify it. When finished, uncheck the "remember my password", then click on "ok". Now...

In this video, we learn how to get credit when you don't have any. Most credit agencies are now gathering information about younger people to figure out if they are allowed to get credit cards, which will help them build a credit score. There is a website, PRBC, where you can start a file and enter your information, and it can verify all the information you report. This information will be given to credit reporting agencies, and give you more of a chance to get credit. Next, you can get depar...

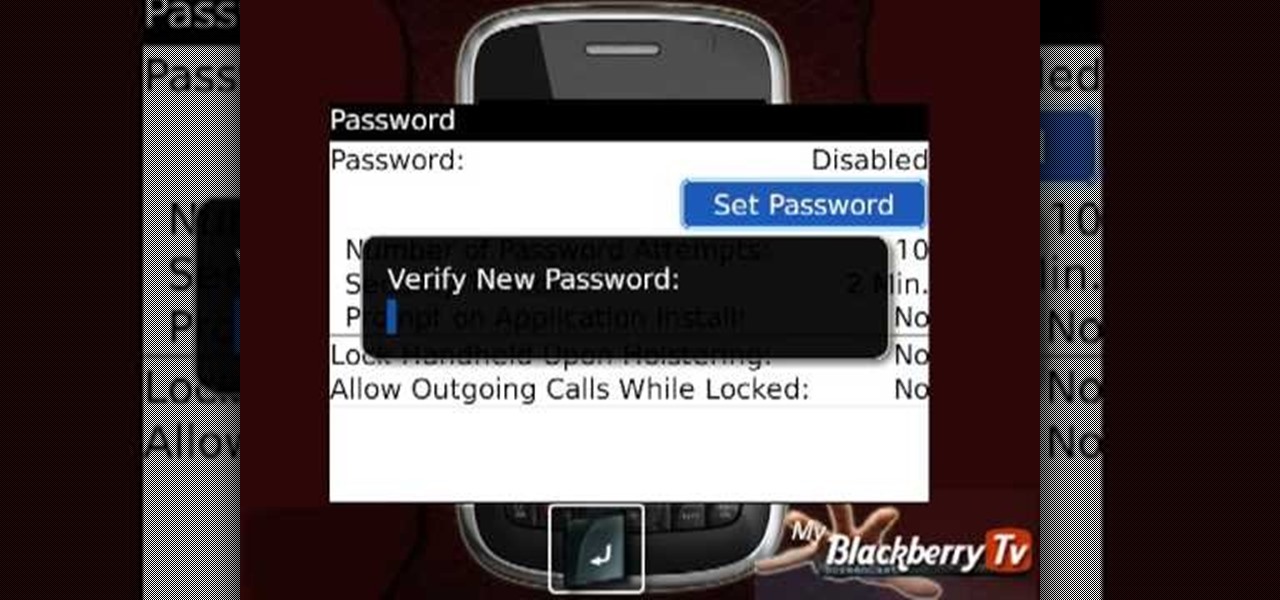
My Blackberry TV demonstrates how to protect your Blackberry device with a password. Protecting your Blackberry with a password will help to stop people from accessing your personal information on your device. From the home screen, press the Blackberry menu key. Then, select the options choice. Next, scroll down to the password choice on the options menu. Select password and then select the set password button on the password screen. Enter your desired password and then press the enter key. V...

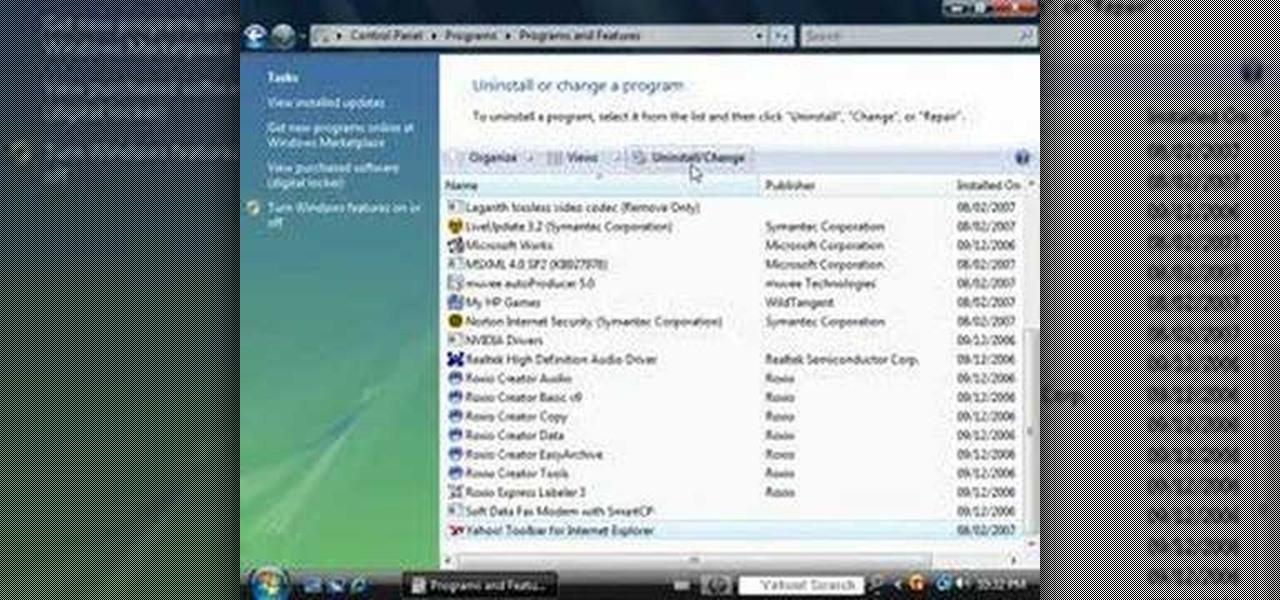
1. Go to Control Panel from the start menu and select Uninstall a program. 2. Start Menu>Control Panel>Uninstall a Program

To get autotune on Audacity, you will need to have the 1.3.10 beta version from Audacity's website. Verify that you have autotune or G-snap in the plug-ins. You may need to download G-snap from the internet. First, open up Audacity. Then, go to edit and select preferences. Go to effects and click rescan BST effects next time Audacity is started. Then, click the okay button. Close out of Audacity and then reopen it. The program will then import your new files. Your new files will then show up ...

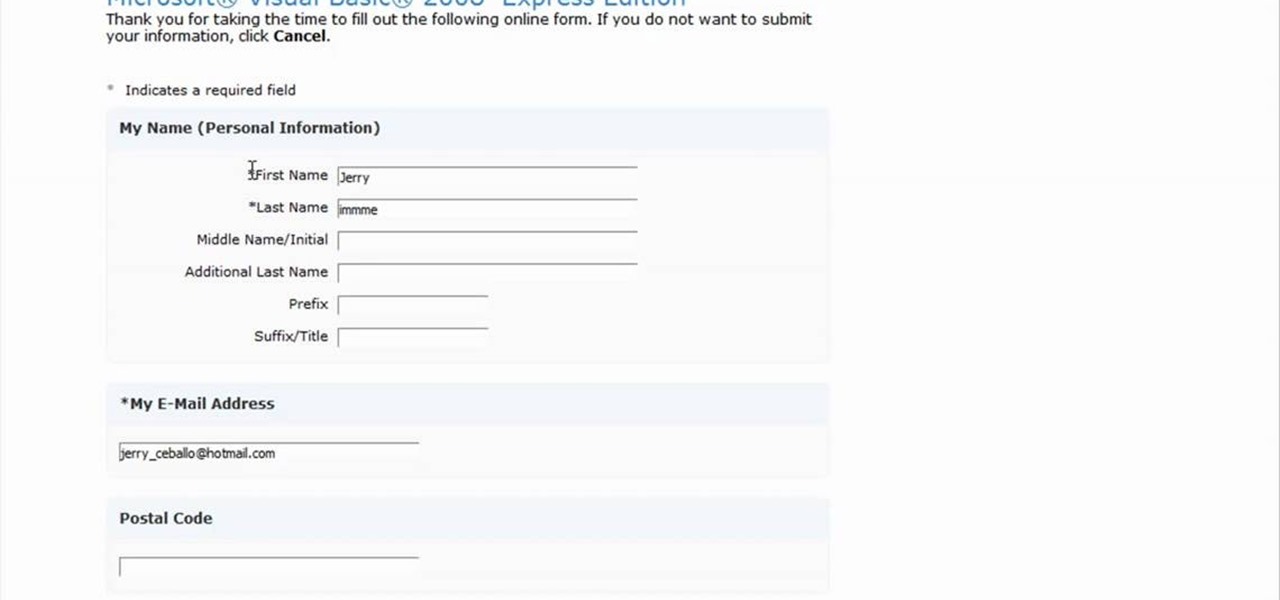
Registering Visual Basics 2008 express edition is quite simple. It is a free registration. First open visual basic then go to the help option. Register the product and click on register now. It will ask you to sign into Microsoft email using your Hotmail account or if you do not have one you can create one and use it there. Use your user name and password where it asks to verify. Fill out all the form information, it may be real or fake, it does not matter. Then you will come to a registratio...

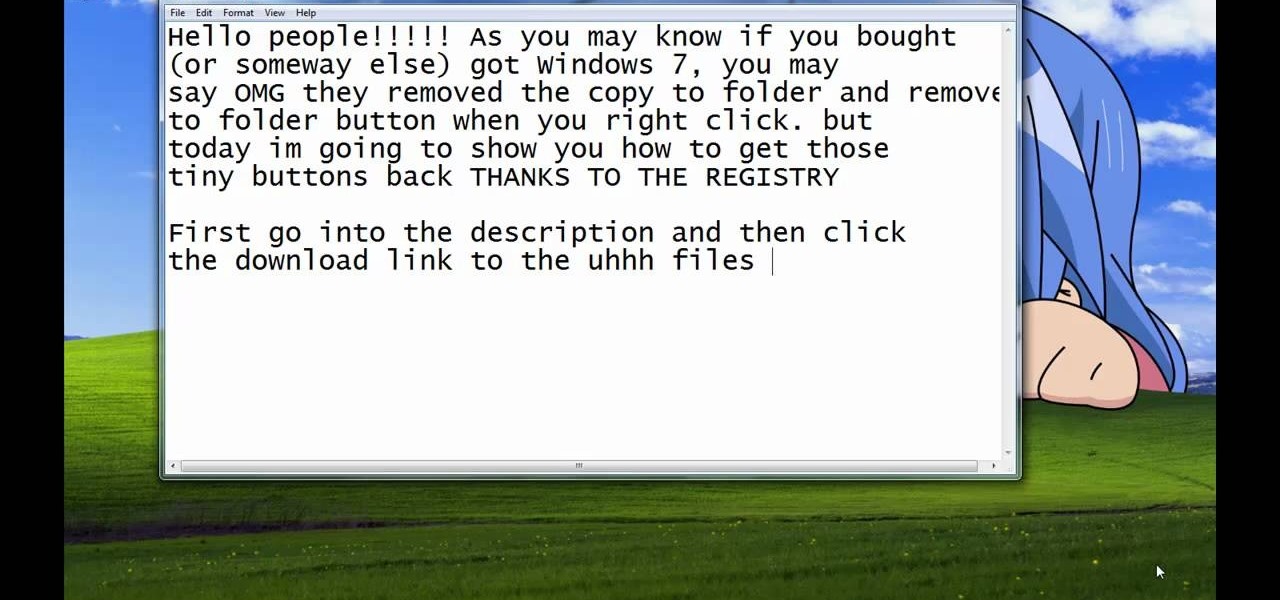
Steps taken to get the Copy to and Move to folder function in Windows 7 are:1. Go into the description and click the download link, to download the files2. After downloading the registry file you will see a zip file, which you need to extract using the software called Win Zip.3. After extracting the zip file, you will see two registry file (copy to and move to) execute both the registry file and give Yes, so that the file gets installed successfully.4. After successful installation, it is rec...

This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:

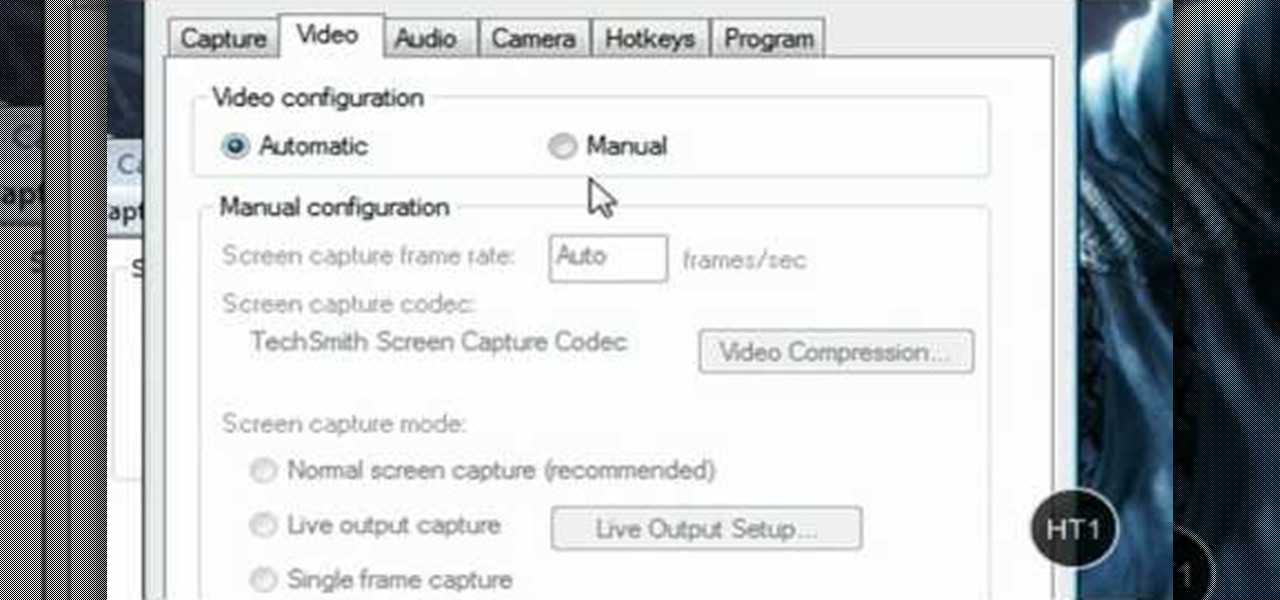
HelpTube1 teaches you how to improve video quality when recording with Camtasia. The reason some videos don't have the HD version is that it takes 30-40 minutes for YouTube to verify whether the video is in high definition or not. In Camtasia 5 there is a Tools tab at the top of the program window. Click on that and then go to Capture. Check the box that says Save as AVI. Then go to Video, change Manual and change the frame rate to 80. Then click Ok and you will get these options every time. ...

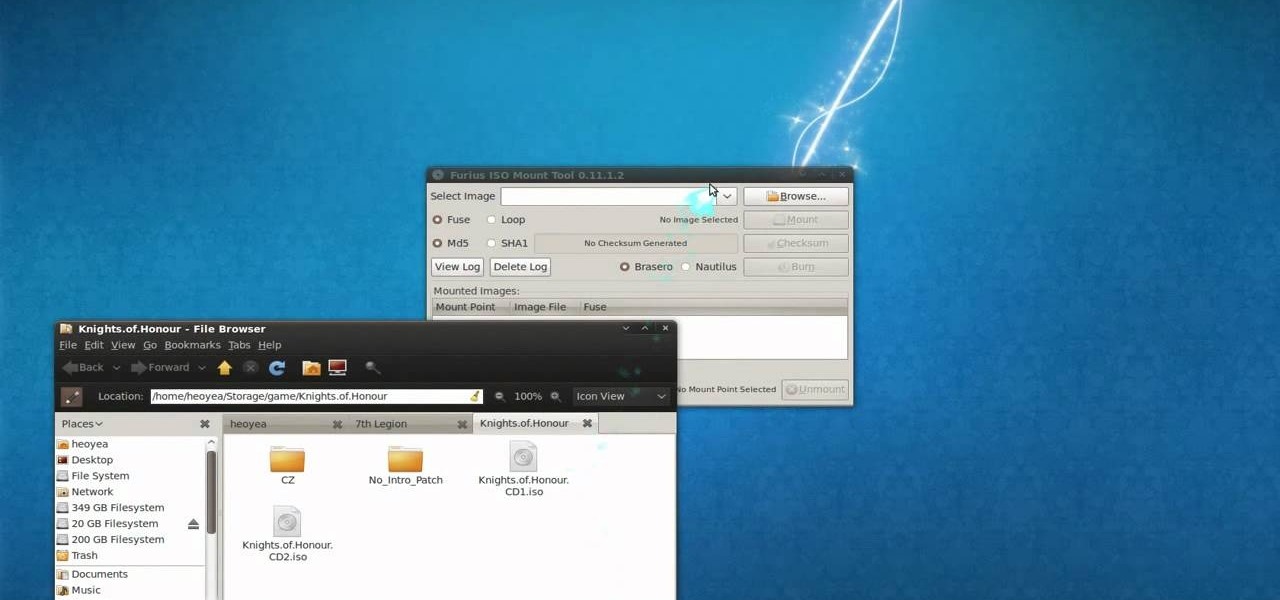
This is a tutorial video on how to use a virtual CD/DVD drive software tool called Furius ISO Mount. Furius ISO Mount is an .ISO, .IMG, .BIN, .MDF, and .NRG image management utility, that allows you to automatically mount and unmount disk image files. This utility application will allow you to mount multiple images at once, burn image files to optical disk, and create MD5 and SHA1 checksums to verify the that the image files are not corrupted. This program also automatically creates mount poi...

mybigleftnut90 teaches you how to burn Wii backup games for Mac. After you get a backup game for the Wii, you need to make sure the DVD you'll be burning it too is DVD-R as these work best. Also make sure that the size of the backup game is not larger than the blank DVD you have. Right click on the image and click on "Open with-Disk utility." In the new program window, you click your image file name and click the button "Burn" at the top. Your speed should be 2x or 4x. Unclick verify burned d...

After you've already taken your PS3's Blu-ray Disc drive apart and fixed anything necessary (or maybe nothing at all), you going to have to reassemble the drive (obviously). This video teaches you how to do just that.

Many people have complained about the lack of autofocus in video mode on the Canon 5D Mark II. Fortunately, this video demonstrates a solution by utilizing the live mode, thus enabling the still camera's autofocus features.

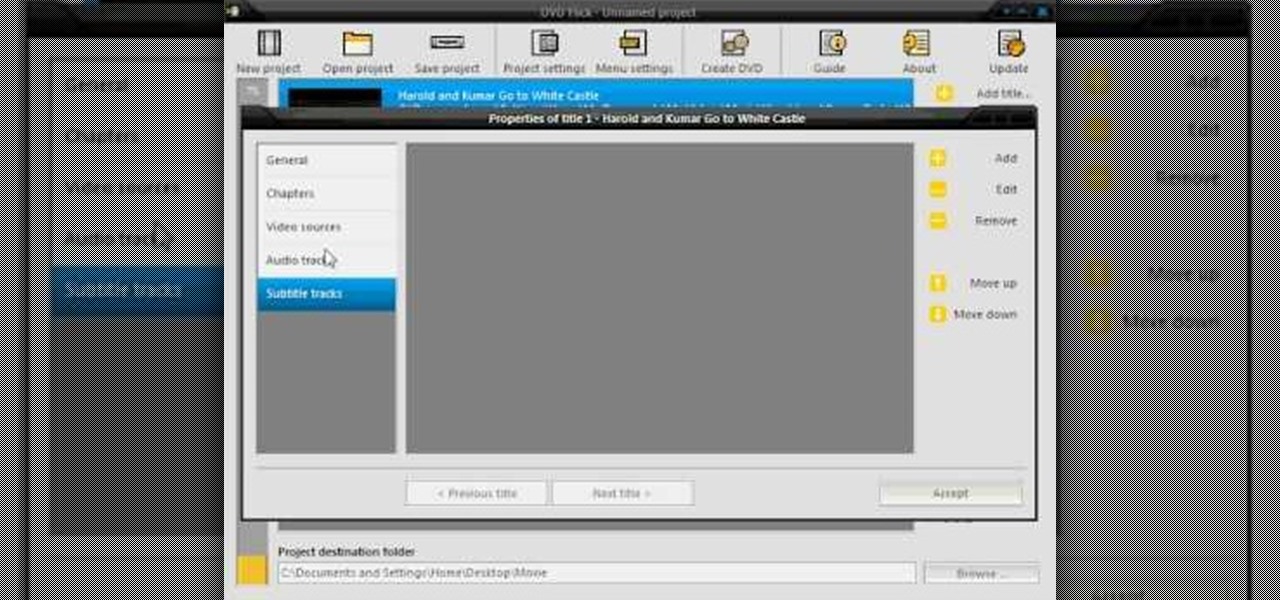
Burn downloaded movies onto a DVD. Open your browser, go to the Google website and type axxo torrents in the search bar. Then select the homepage of axxo torrents, and download the favorite video in to your computer. Then open the DVD flick, you select burn a DVD. In that you select the files to be burned on to a DVD, and then click ok. Then the general settings appear on screen, about the name of video. Then also select how to burn and writing speed, and check the box of verify the data on w...

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

In this chess video tutorial, Grandmaster Alexandra Kosteniuk, with guest star Almira Skripchenko, will show you how to checkmate in just two moves that the Fritz 10 software program doesn't even recognize. Fritz 10 just can't solve this mate in 2 chess problem.

Forex— what is it? Any investor could tell you a complicated description of what Forex is, but the basics of the FX currency markets is— an over-the-counter financial market for trading currencies. The foreign currency exchange market has no central exchanges like the stock market and little regulatory oversight. With this beginner’s guide, learn the trading basics.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,