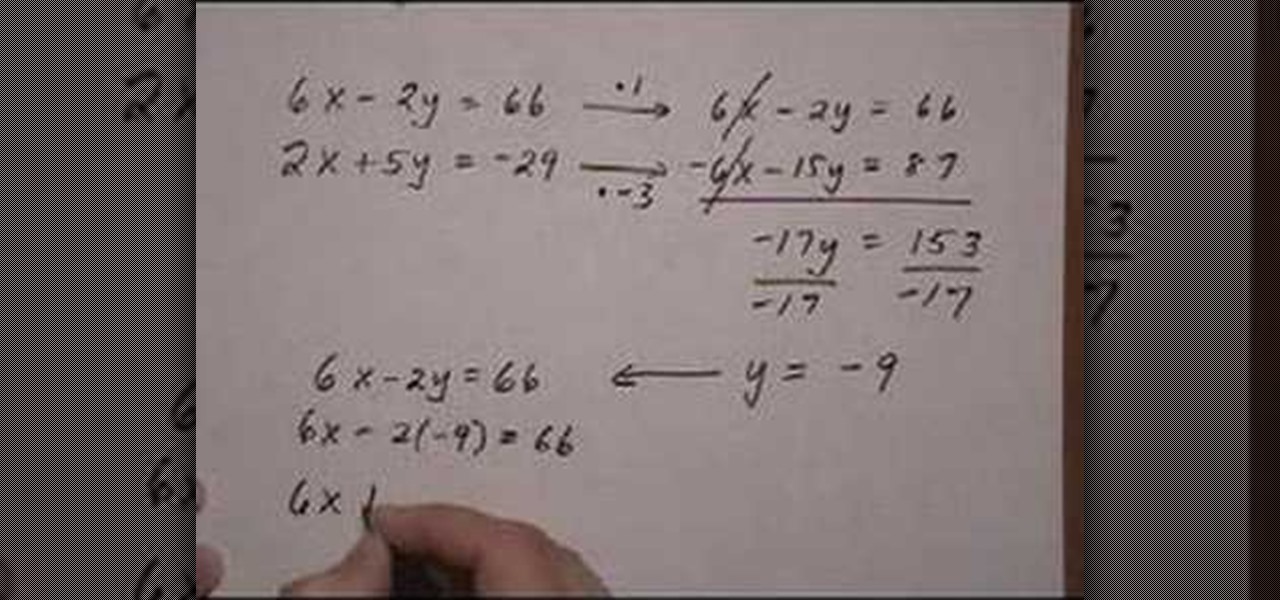There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.
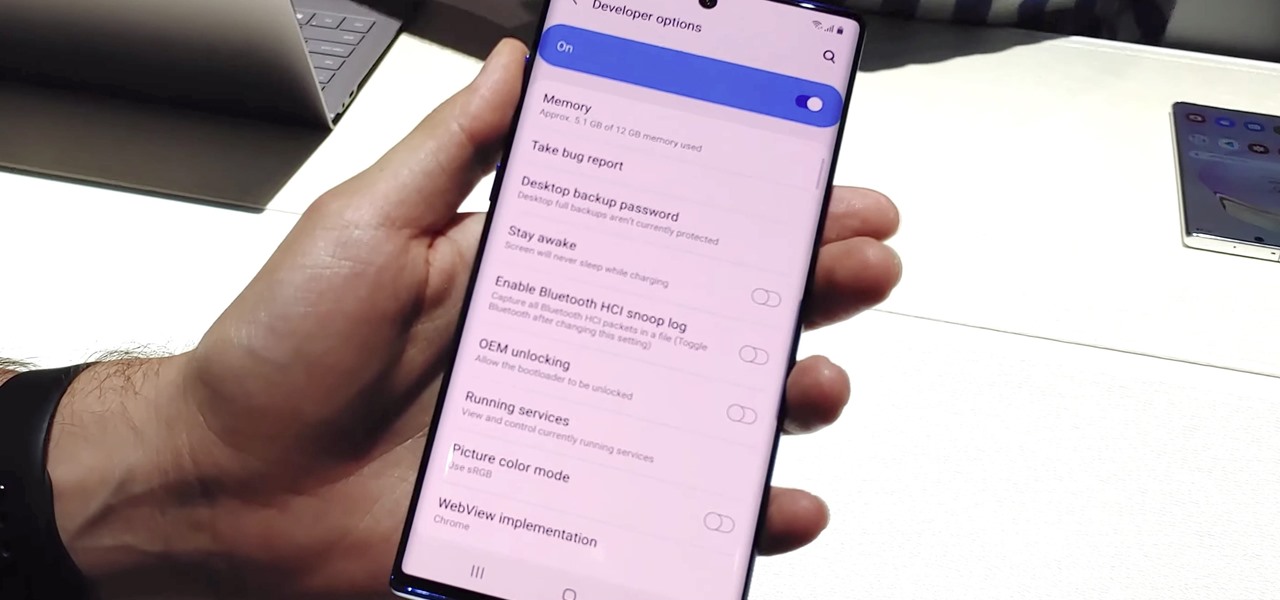
You may note be able to root your Snapdragon-powered Note 10, but thanks to the hidden Developer Options, you can still tweak low-level settings like custom codecs for better audio quality on Bluetooth headphones and faster animations to enhance your experience. Best of all, you don't need to be an expert at modding to take advantage of this menu.
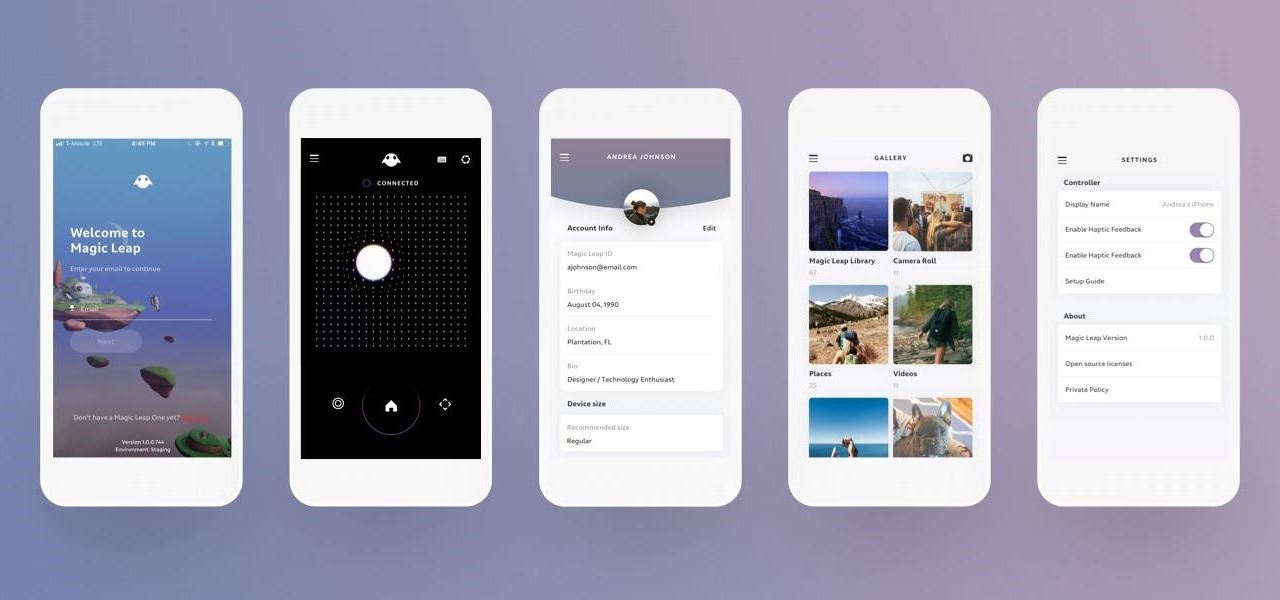
Among a treasure trove of new developer information on the Lumin OS that Magic Leap recently published on its Creator Portal appears to be the official confirmation of the Magic Leap Mobile Companion App.

For Apple Pay users, the iPhone X, XS, XS Max, or XR will be an adjustment. Gone are the days where you could rest your finger on the Home button and hold your device within range of a contactless reader. Without Touch ID on the iPhone X, this isn't possible. But have no fear, Face ID is here.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Facebook, you either love it or you hate it ... or maybe you're indifferent. The point is, Facebook is everywhere, and the debate is still raging over whether or not it's actually, well, good. That debate may not exist for the various personalities of Facebook much longer, however, as Facebook announced a new app geared directly towards improving how they broadcast their content to their audiences.

Update 6/20/17: Olixar, a smartphone case manufacturer, has released images of an iPhone 8 case design. While at first glance this might seem to confirm the iPhone 8's final design, 9to5 Mac reports that Olixar admits they produced these renders based on "information and schematics they've acquired through their factories and contacts in the far east."

This is probably one of the coolest Instagram hacks I've come across. I never knew that there could be an actual formula for creating the perfect feed, but the fact that someone thought of it is really awesome.

According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.

Samsung's Galaxy S7 is an incredible piece of technology, but the Skype app that's preinstalled on some models may have some nasty issues, such as video and audio that freezes. Luckily, the fix for these problems is a simple one, although somewhat buried in the phone's Settings app.

Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate.

Google has begun the testing phase for its new Hands Free app that lets you pay at participating locations without having to even take your phone out of your pocket.

Similar to the feature that lets you dim the light on your PS4's DualShock controller, your Playstation 4 is filled with useful tricks that you may not know about, especially when all you want to do is pick up and play. One of these useful tricks is the ability to turn your TV on using the PS4 controller.

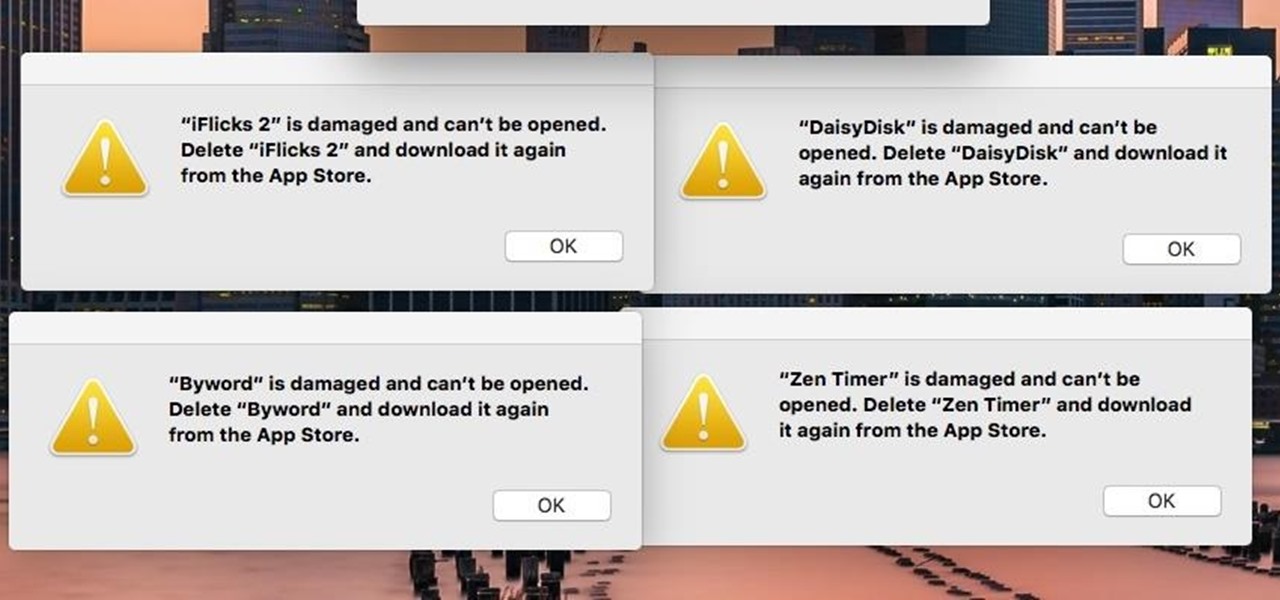
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed:

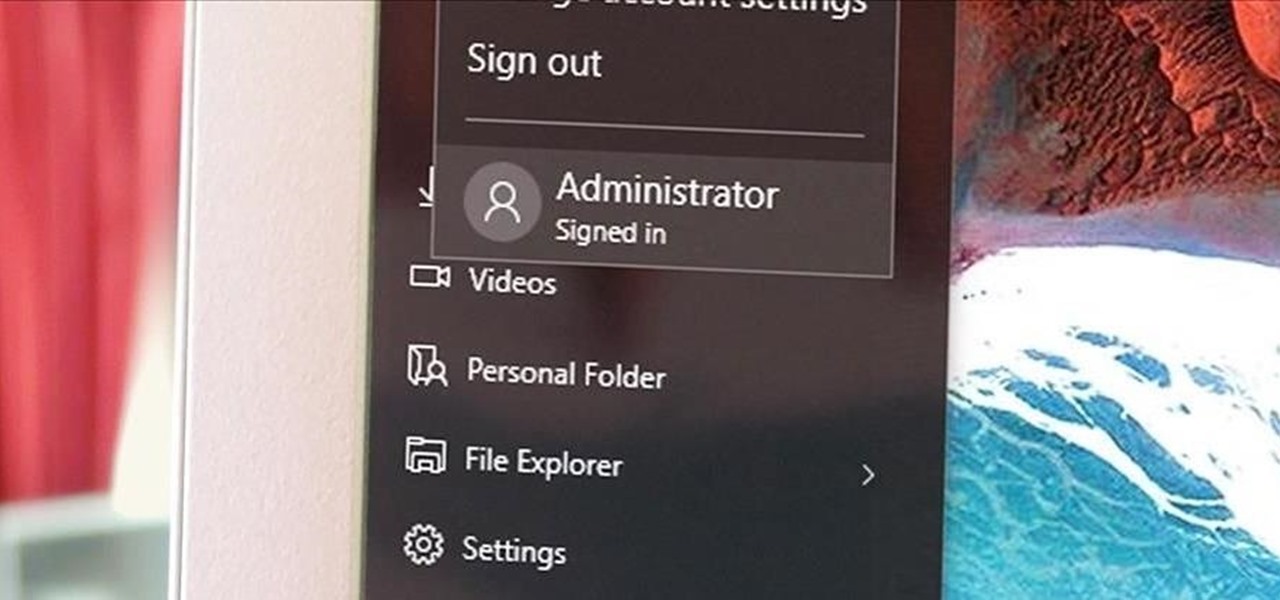
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

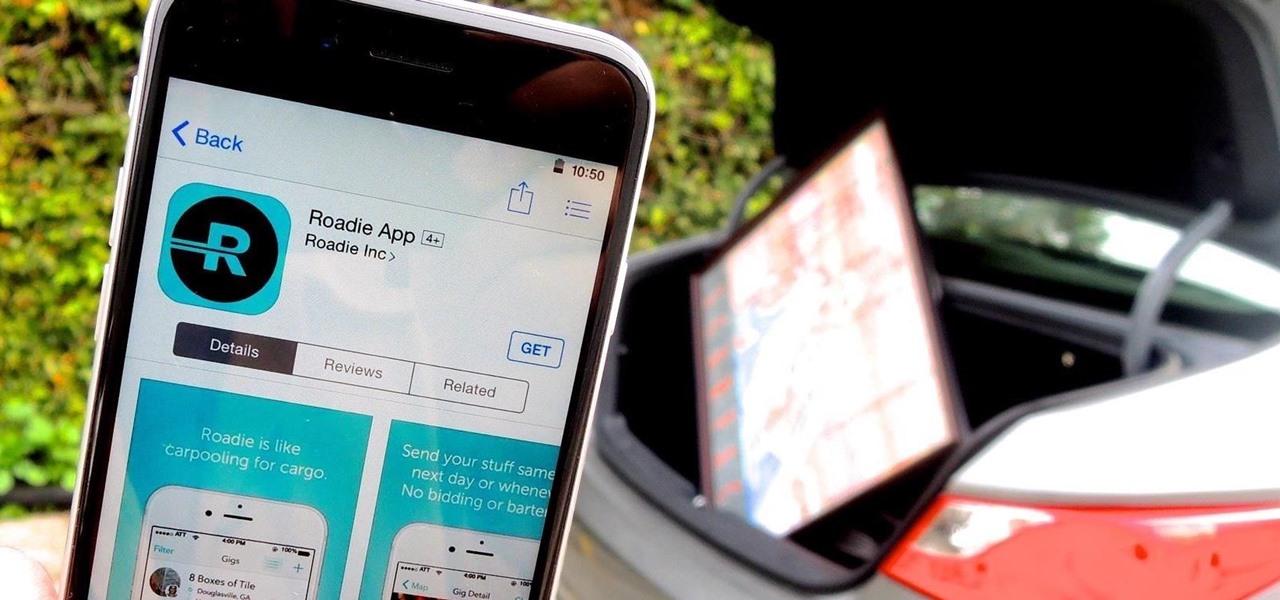
The next time you plan on going on an adventurous road trip, get paid for it! With the the new mobile app called Roadie, from developer Marc Gorlin, you can get paid to go where you're already going.

Our dog has tons of energy and always wants to play. However, play time can be exhausting to the humans of the house. We found out a few months ago that the dog loves to play ‘chase the red dot.' Boredom leads to creativity, so we attached a laser pointer to her head with a bandana and small piece of tape. This kept her continuously occupied until we removed it after 20 minutes. I assume you could try this with a cat if you were daring enough – good luck with that. Caution: Laser pointers (ev...

This past year, Facebook spent $19 billion purchasing the popular messaging app WhatsApp, and for good reason. Mark Zuckerberg isn't going to spend that type of money on just any application. WhatsApp is widely popular and frequently used by more than 500 million users worldwide, which is almost twenty percent of the Earth's population.

Video: . How can you tell if the Louis Vuitton handbag that you are about to buy online is not a fake? Follow these 6 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping. Step 1: Branded Dust Bag

UPS gives you all the tools you need to take away the complications and confusion of international shipping. UPS provides simple, step-by-step online instructions and helps guide you through the required documentation to reduce the likelihood of customs delays.

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

Remember TwtRoulette? TwtRoulette was an online app that turned you into a so-called Twitter spy, letting you peruse someone's own timeline feed exactly how they saw it themselves. So, if you wanted to see what tweets Ashton Kutcher was seeing in his home timeline from the 700+ people he follows, you could.

Tons of iPhone 5 users with Verizon Wireless hit the message boards last week complaining about their phones sucking down massive amounts of cellular data when they were actually using a Wi-Fi connection. Of course, that means Verizon customers could have been getting charged for cellular data they weren't actually using.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

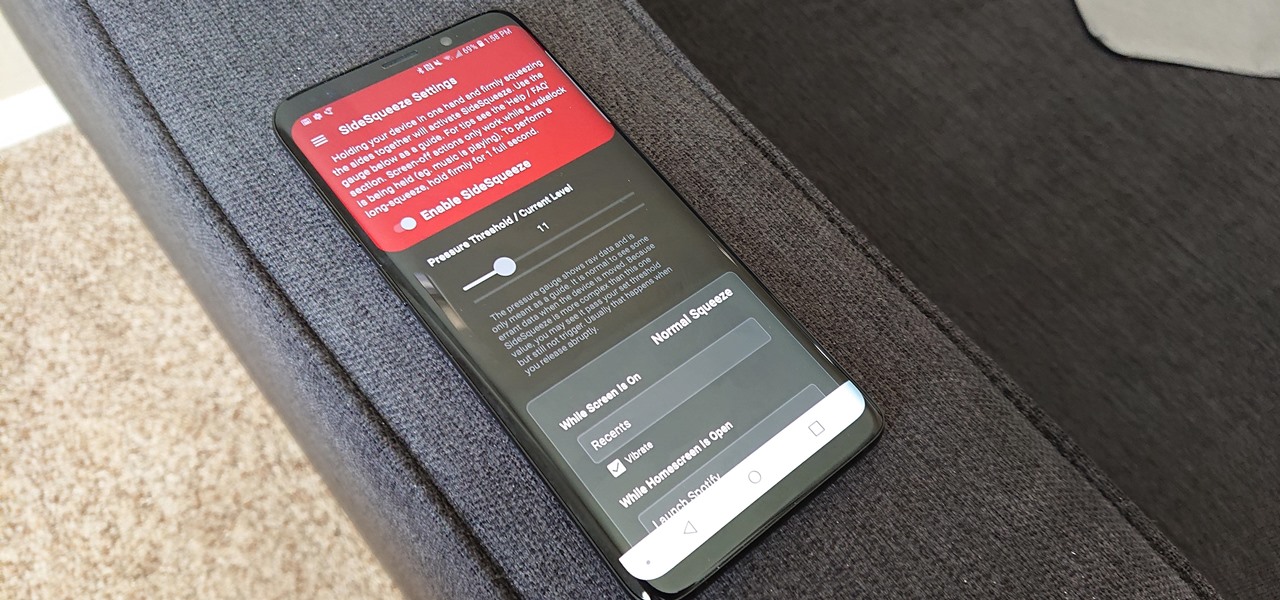
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

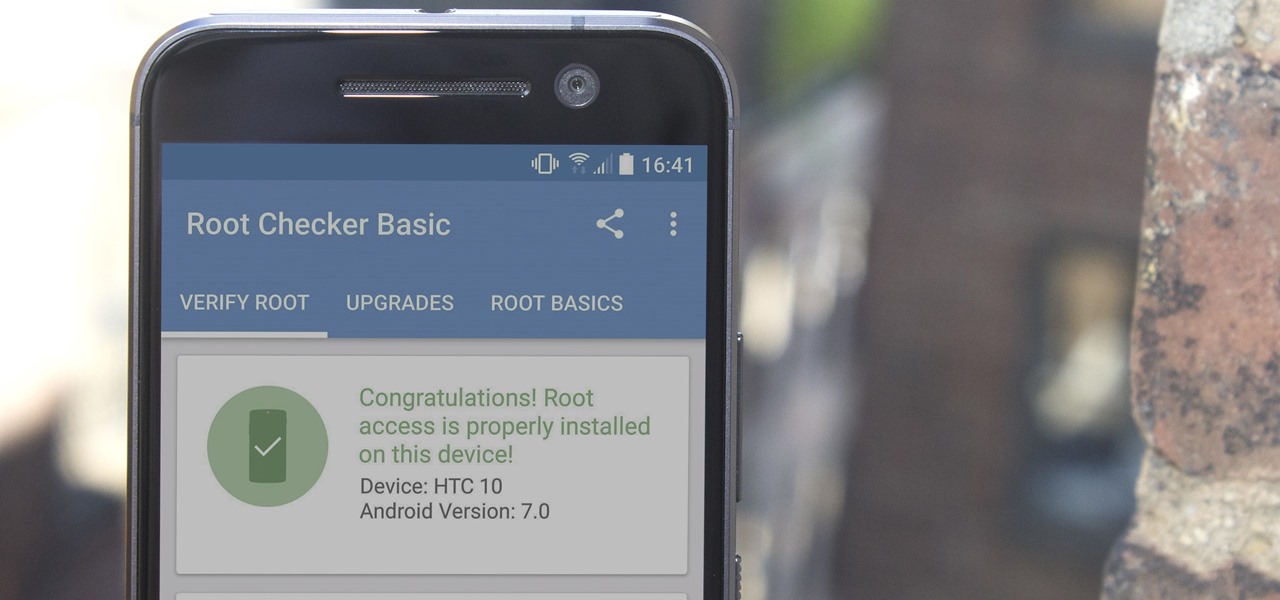
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process.

It just keeps getting harder to enjoy all of the benefits of root without sacrificing features. Thanks to SafetyNet, we've lost the ability to use Android Pay, Pokémon GO, and even Snapchat to an extent. But the most recent news on this front is perhaps worst of all: Netflix has already stopped showing up on the Play Store for rooted users, and soon, it may refuse to run even if you've sideloaded the app.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

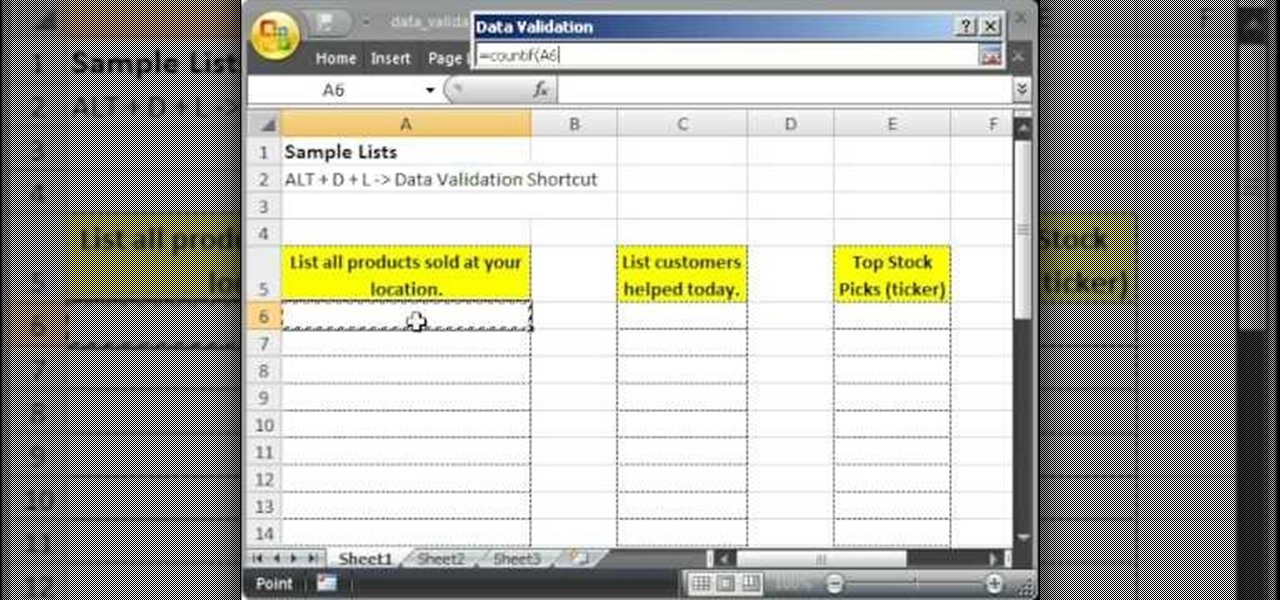
This tutorial describes how to make a list with unique values in Excel.This procedure makes the defined cells in a column (called as list) NOT to accept repeated values, which makes the list more simple, readable, easy to manipulate when preparing a worksheet.

It truly is hard to sleep tight when the bed bugs bite, since these insidious creatures are very real, and very nasty. You’ll have to be persistent to get rid of them.

This video is about using the elimination method to solve a linear system. The lady presenting this video says that elimination method means that one of the two variables has to be eliminated while adding up the two linear equations. She then explains the example equations 6x-2y=66 and 5y=-29-2x. She asks you to first line up x and y. So the second equation is rewritten as 2x+5y=-29. Then she says that, to eliminate a variable, we should have their variables equal in value but of opposite sig...