Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an open-source software, was originally designed to connect to your TV so you could control your media from up to ten feet away, and the core functionality still shines today. All of this is what makes Kodi so popular today...

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Google I/O is like Christmas for Android enthusiasts. Every year, this conference showcases new and upcoming features for the world's leading mobile operating system, and this year's was no different. Shortly after announcing Android M, Google released a preview version of the upcoming firmware for Nexus devices.

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

Apple is widely known for keeping a tight grip on iOS, disallowing open-source and third-party downloads. While there are many reasons for this, the three most frequently referenced are quality control, malware prevention, and of course—money.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

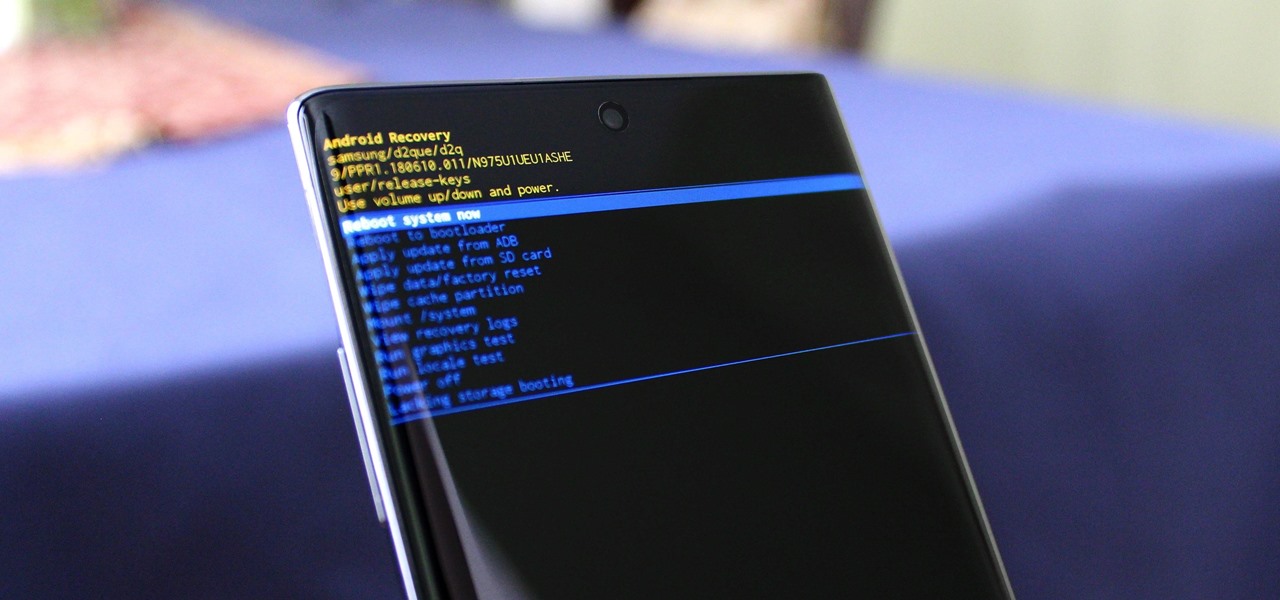
You can't call yourself an Android pro without knowing about Recovery or Download Mode. These menus are critical to do more advanced tasks on your phone, include sideloading software updates and un-bricking a device. But this year, Samsung changed the button combinations that will get you there.

As you might know, Tidal differentiates itself from the competition with its audio quality. Unlike Spotify and Apple Music, it aims to give its subscribers studio quality audio from any device. However, before you sign up for Tidal, be aware there are few steps you need to take in order to stream such high-quality music.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

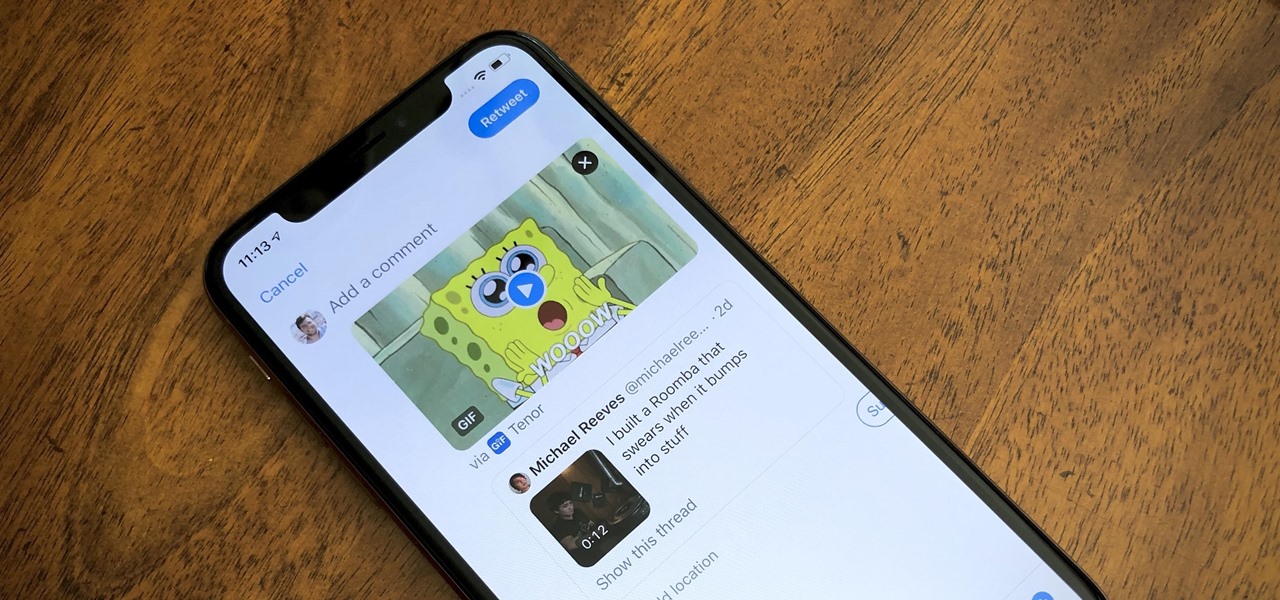
On Twitter, quote retweets are a great way to share someone else's tweet with your view of their message. Twitter has expanded on this idea by giving us the ability to attach images, video, and GIFs to quote retweets. With these extra options, you should have no problem adding your own unique perspective on that funny, serious, or professional tweet.

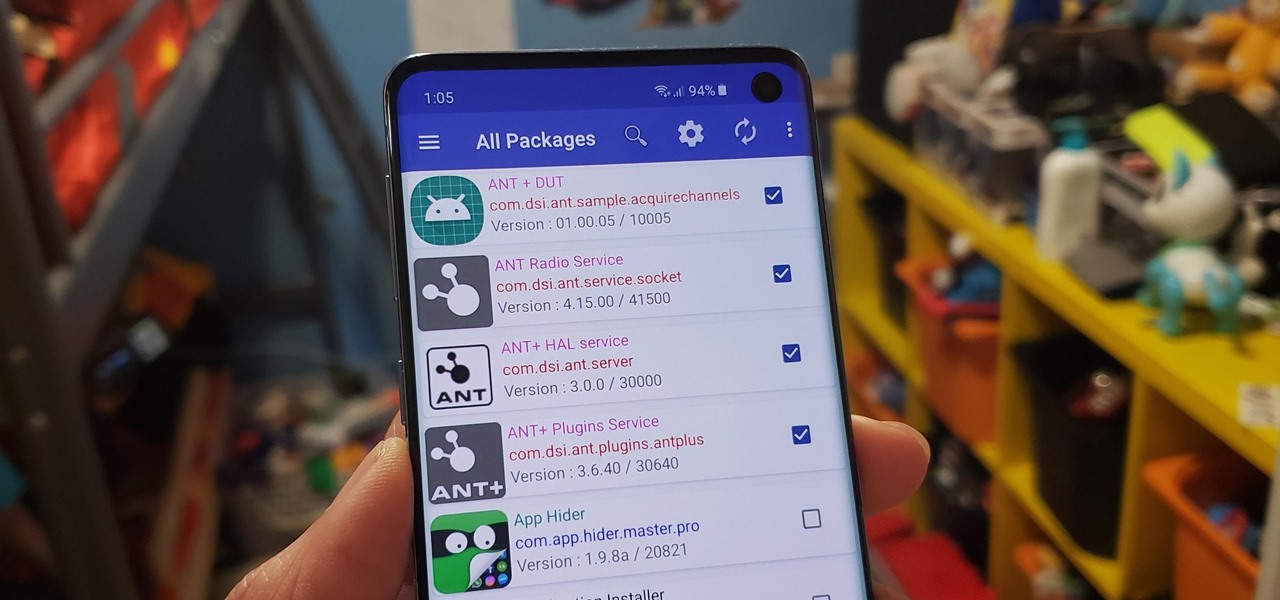
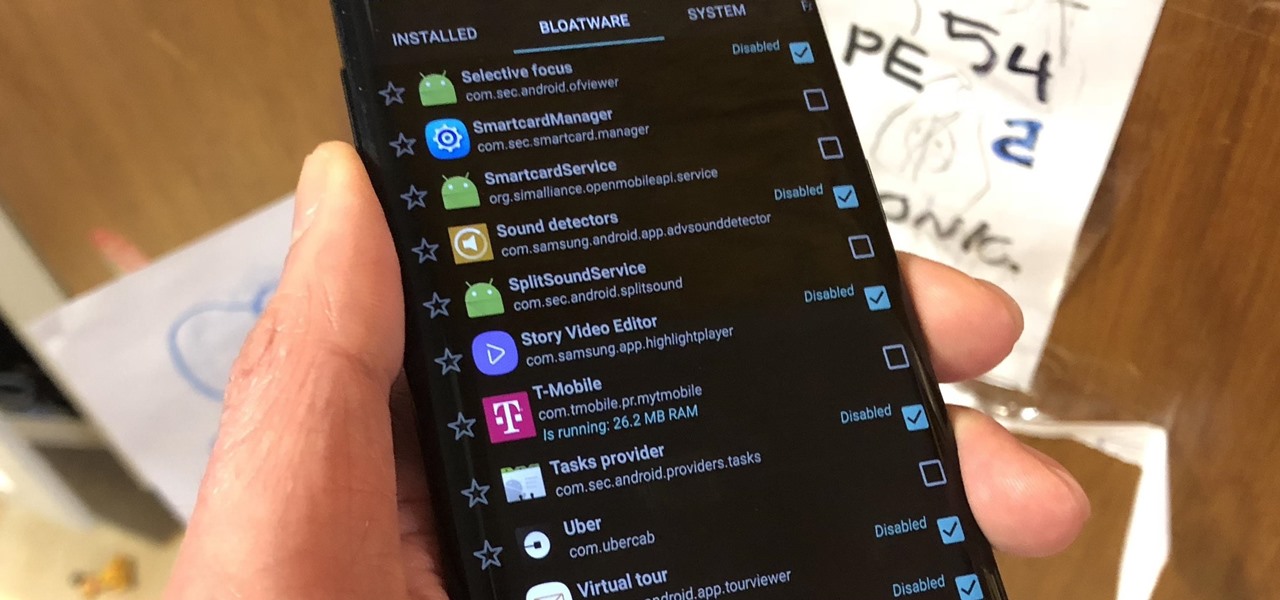
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Sometimes we need to share screenshots, but don't want to reveal the entire screen. This usually requires some editing that isn't typically easy to do on a smartphone. BlackBerry recognized this issue and created a tool called Redactor that makes it easy to hide your data before sharing.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

It appears we're in the midst of an augmented reality art boom, because in the same month that the famed Christie's auction house launched its mobile AR app, leading art gallery and art seller Saatchi Art has also announced its entry into the AR space.

Carrier-branded Galaxy S9 models come with a ton of bloatware that you usually can't get rid of without rooting. With a little digital elbow grease, however, there is a way to disable bloatware on your S9 or S9+, and it's a lot safer that attempting to root and modify you precious device.

While millions eagerly await the arrival of the Galaxy S9 and all the new features it has to offer, we can actually get a glimpse of its capabilities right now — if we know where to look. The S9's home screen, in particular, is one such area that has new features we can preview now.

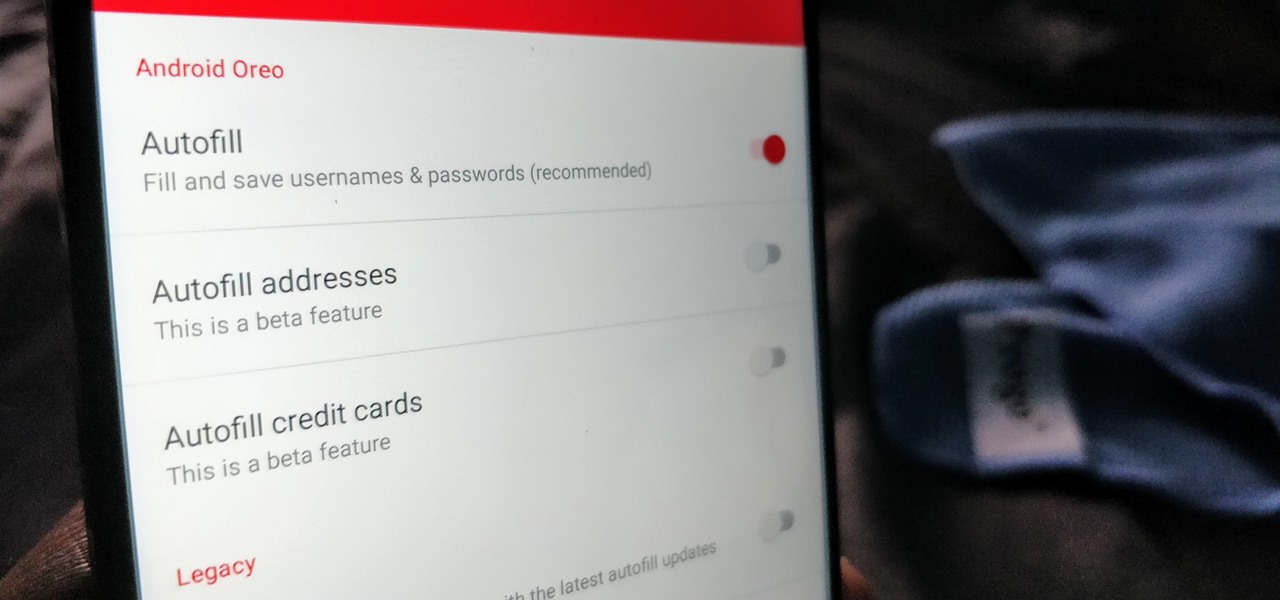
One of the more exciting features in Android Oreo is the Autofill API. With this tool, third-party password managers can autofill login information into other apps. LastPass added this feature to their beta app a while back, but now, Autofill is finally available in the official stable version of LastPass.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Apple Music's name reveals a lot about itself — it's made by Apple, and it has a lot of music. 40 million songs, in fact, if the iPhone-maker is to be believed. With that many songs, you may find a gem before any of your friends or family do. How can you share that song with them?

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

While it's easy enough to take a screenshot of an end-to-end encrypted Telegram chat thread using an iPhone, it's an entirely different story on Android phones. Telegram disables screenshots for Secret Chats by default on Android, and not everyone can turn it on.

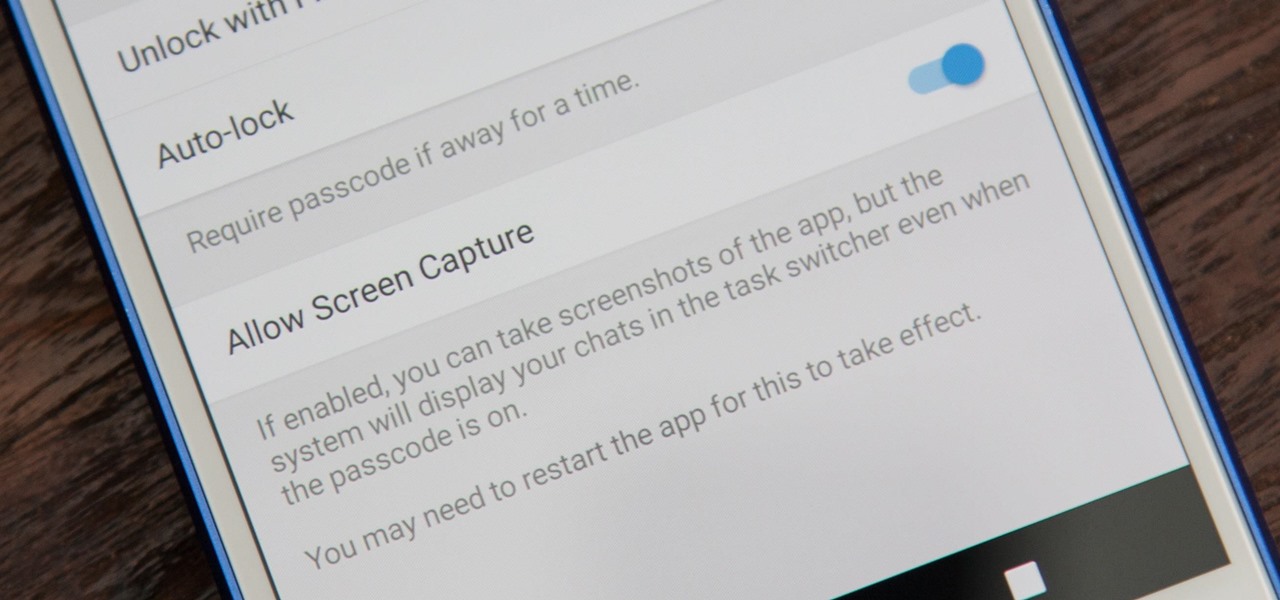
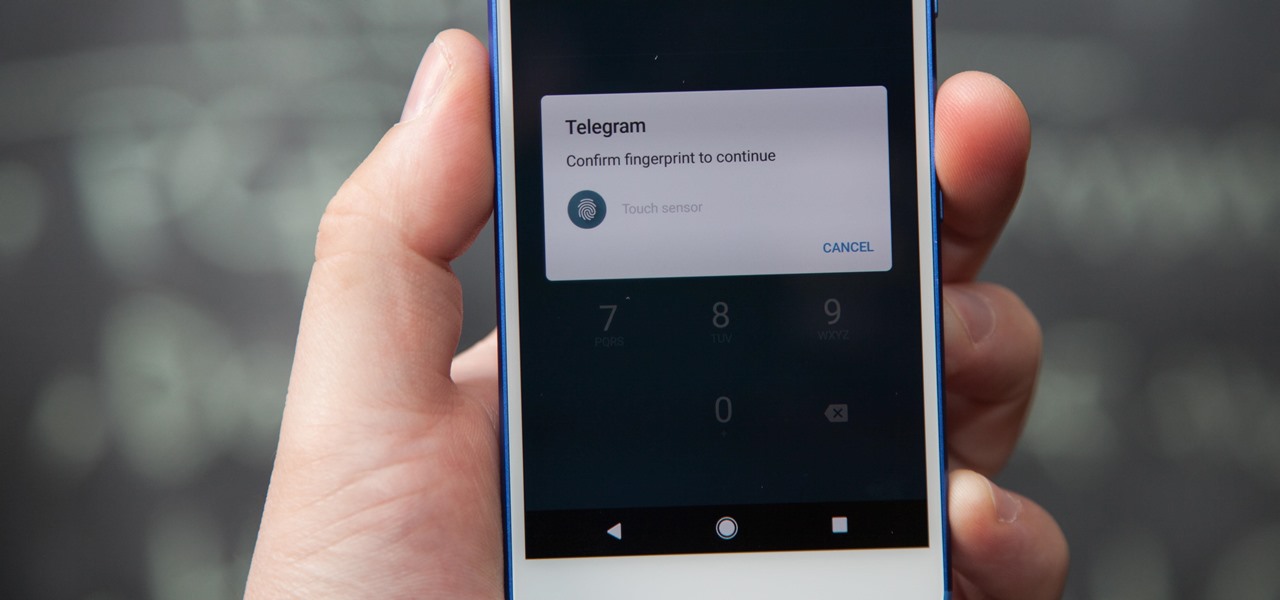
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

This may not matter to you if you only FaceTime from your iPhone occasionally, but if you're FaceTiming every day on a limited data plan from your cellular provider, you're going to want to conserve as much data as possible by making sure that you're connected to Wi-Fi only — especially if they are video calls.

When Chan Mei Zhi Alcine chose her senior project, she thought outside the box by thinking inside the bottle. Along with a research team at her university, she found a way to combine health and enjoyment, while meeting a challenge not so definitively met before in alcoholic beverages. She and a research team at her university claim they've created the world's first probiotic sour beer.