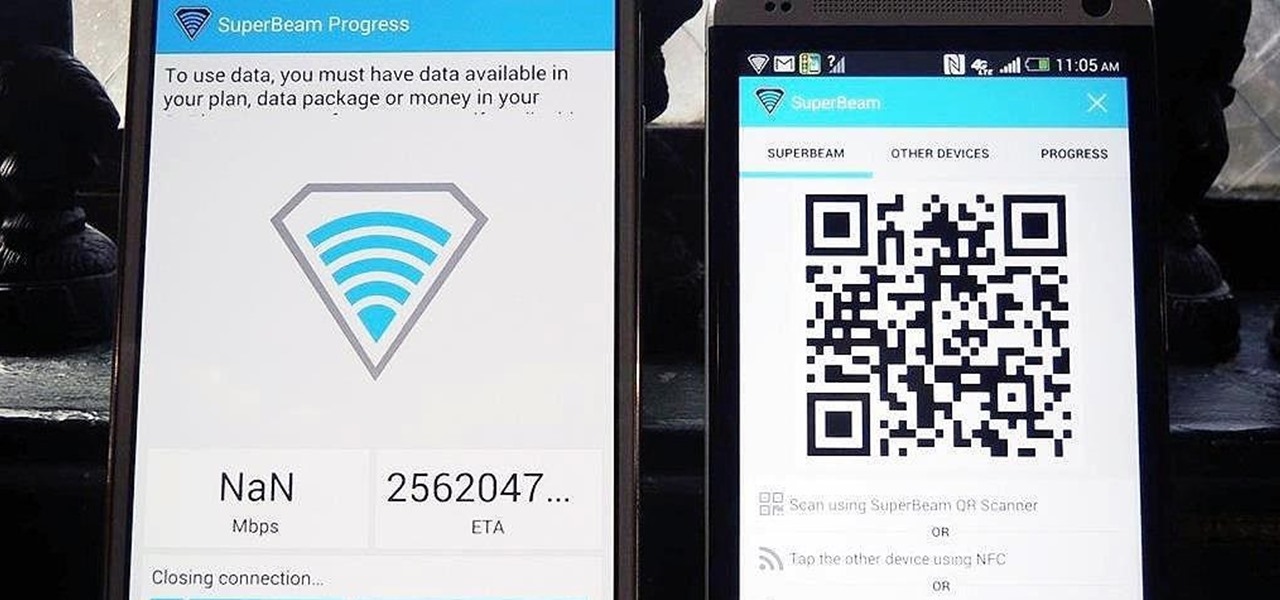
How To: Quickly Share & Receive Large Files from Other Devices Without Using Wi-Fi
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.


Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.
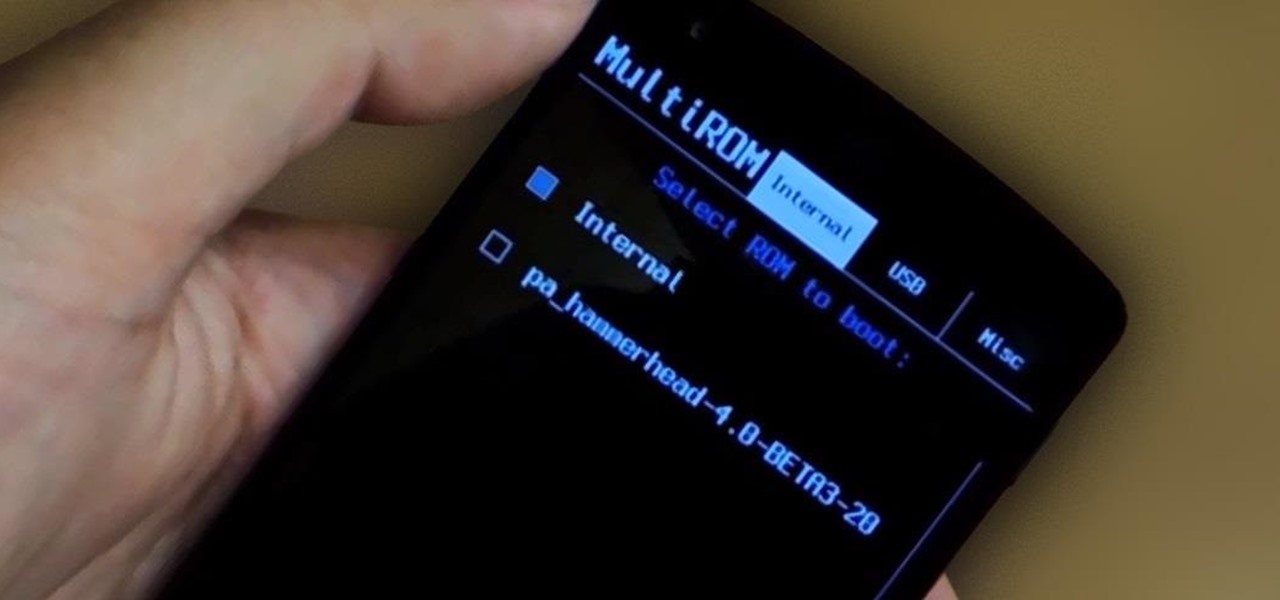
When you enter the softModder realm by rooting your Nexus 5, you open up an exciting world of possibilities and deep customizations for your device. Among other things, it gives you the ability to flash custom ROMs which, individually, act as entirely different operating systems that can vastly alter your user experience.
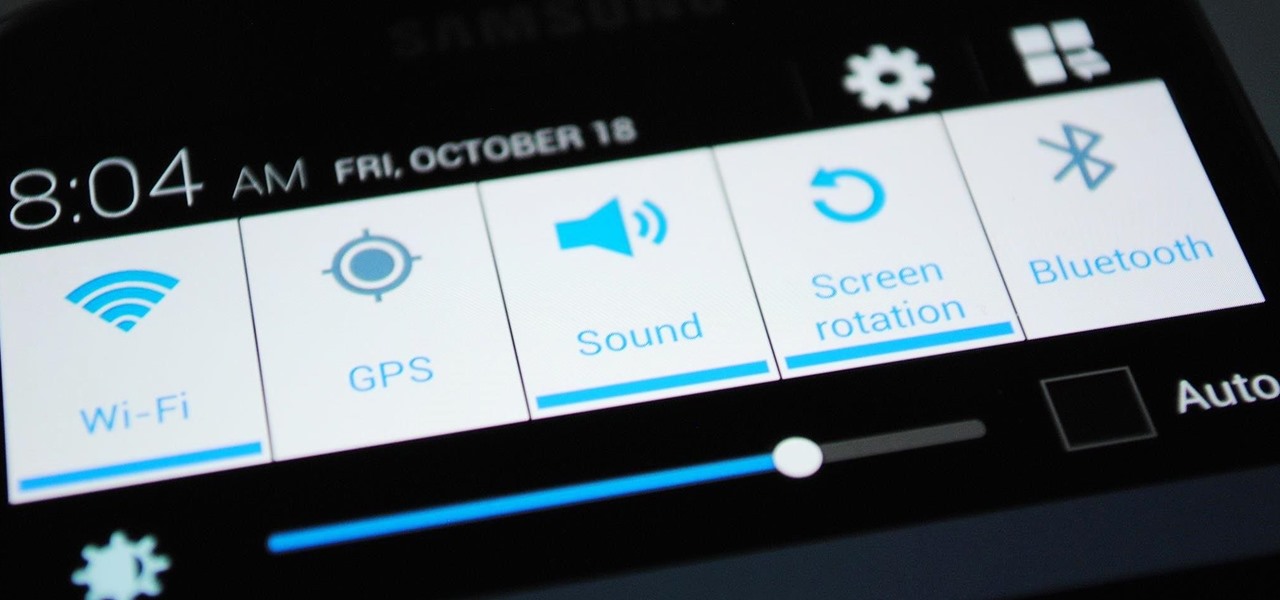
Samsung's quick settings toggles are insanely useful for accessing settings that you would normally need to dig into menus for. Definitely a case of function over form, though. TouchWiz's bright green on dark blue has to be one of the fugliest color combinations I have ever seen.

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.
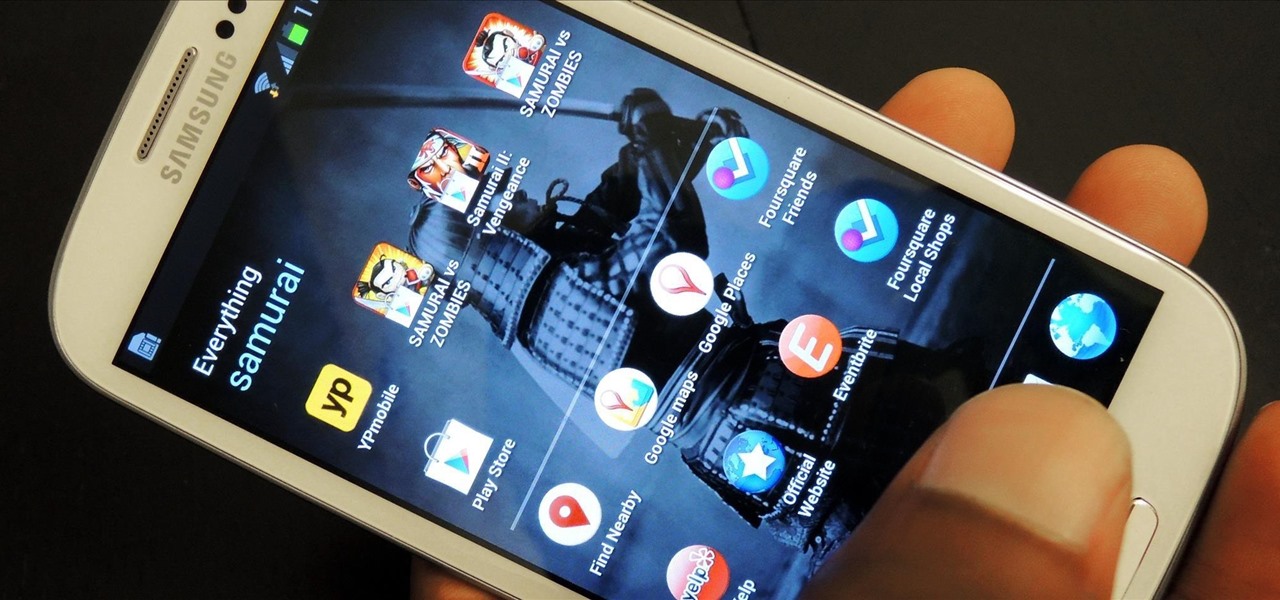
There's no shortage of cool customizations for my Samsung Galaxy S3, except when it comes to the launcher. Sure, there a ton of Android launchers out there, like Nova Launcher or Apex Launcher, that allow you to customize app placement, app grouping, infinite scrolling, etc. There's even Facebook Home for those who are Facebook addicts.
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.
Do you like Samsung's TouchWiz and the iPhone's user interface, but wish you could bring the best of both worlds together onto your device? You can! MIUI (pronounced me-you-eye) is a heavily modded custom ROM that brings a different UI experience never before seen on stock Android devices. Over in the Nexus 7 SoftModder forum, Shashou Jian mentioned MIUI as a ROM every user should try out. The interface is a fresh mix of Apple’s iOS and Samsung’s TouchWiz elements—with a large dose of customi...

The advantages of rooting have been covered before, and with rooting comes flashing ROMs and mods to your device. The easiest method for flashing anything is to do it through recovery.

In this video, Hotrod2693 demonstrates how to convert a Windows Movie Maker Video to a YouTube compatible format. First of all, he starts by opening windows movie maker. He imports the windows movie maker video. Next, he drags the newly imported video file to the bottom blue line. Once in place, he goes to File-Save Video As, names the video and saves it. After this is done, he goes to File-Save Movie File. He makes sure “My Computer” is selected and clicks next. In the next screen he names h...

The Holy Grail of chicken has just been found by an unsuspecting reporter of the Chicago Tribune. Yes, that's right: The secret 11 herbs and spices in Colonel Sanders' Original Recipe chicken has finally been revealed, and it looks legit as hell.

VR gaming has developed rapidly in the last few years, moving from a fantasy to a product you can actually afford. As the VR industry grows, so do the ways you can experience virtual reality. The Dragon VR Gaming 3D Stereo Headset with Bluetooth Controller is the ultimate in VR gaming, offering you top-of-the-line performance for only $99.99 while it's on sale for 50% off.

Coders are accustomed to working remotely. The beauty of coding is that all you need is a laptop and a WiFi connection, which makes working anywhere a fairly simple transition. If you're looking for a career change, now might be the perfect time to give coding a try.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

The results of Microsoft's $480 million contract with the US Army are on display and users continue to test the suped-up version of the HoloLens 2.

Amid the coronavirus chaos, two companies at the forefront of augmented reality technology took starkly different approaches to their upcoming developers conferences, as Facebook has canceled its annual F8 conference and Magic Leap plans to invite a limited number of attendees to its Florida headquarters for LEAP Developer Days.
It seems like all tech companies want to know where we are. Even Apple and Google have been caught abusing their location access on iOS and Android. Luckily, there are apps that can trick your phone into thinking it's somewhere it's not.

This time last year, Snap CEO Evan Spiegel and his company were faced with an erosion of its user base that cratered its stock price. This year, on the strength of Snapchat's AR camera effects, the company has reversed course. And that's why Spiegel tops the NR30, our annual list of the leaders in the AR industry.

Your Xbox Wireless Controller is a great way to play games on both Xbox One consoles and Windows 10 computers. However, you don't need to have any of those devices to enjoy your controller with your favorite games — you can seamlessly connect the Xbox Wireless Controller to your iPhone for an enhanced mobile gaming experience.
The first thing you'll always have to do before getting your customization game on with most phones is to unlock the bootloader. Doing so opens the true potential of the device, allowing you to root, install TWRP, Magisk, custom ROMs, and other mods. No matter your wants or needs, there's no way around it — the bootloader must be unlocked to modify the system.
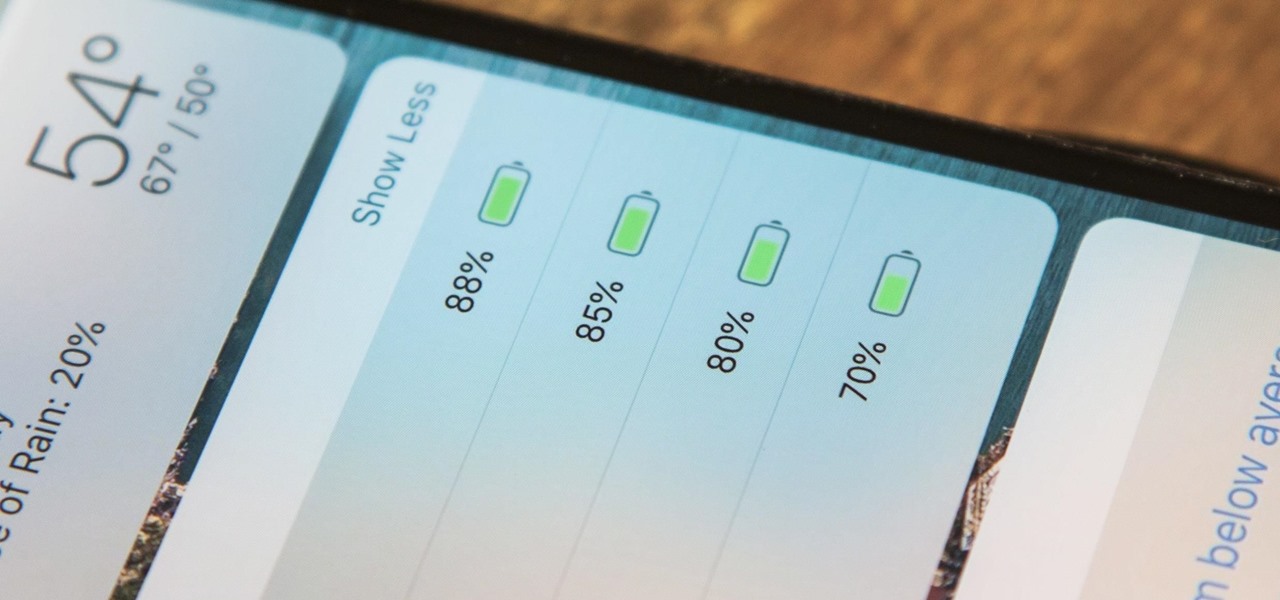
The battery icon in your iPhone's status bar gives you a visual idea of how much power is left, and there's a battery percentage option you can switch to or view in the Control Center, depending on your model. But what you may not know is that there's a way to view the battery percentage of every device connected to your iPhone, from AirPods to Bluetooth speakers and your Apple Watch.
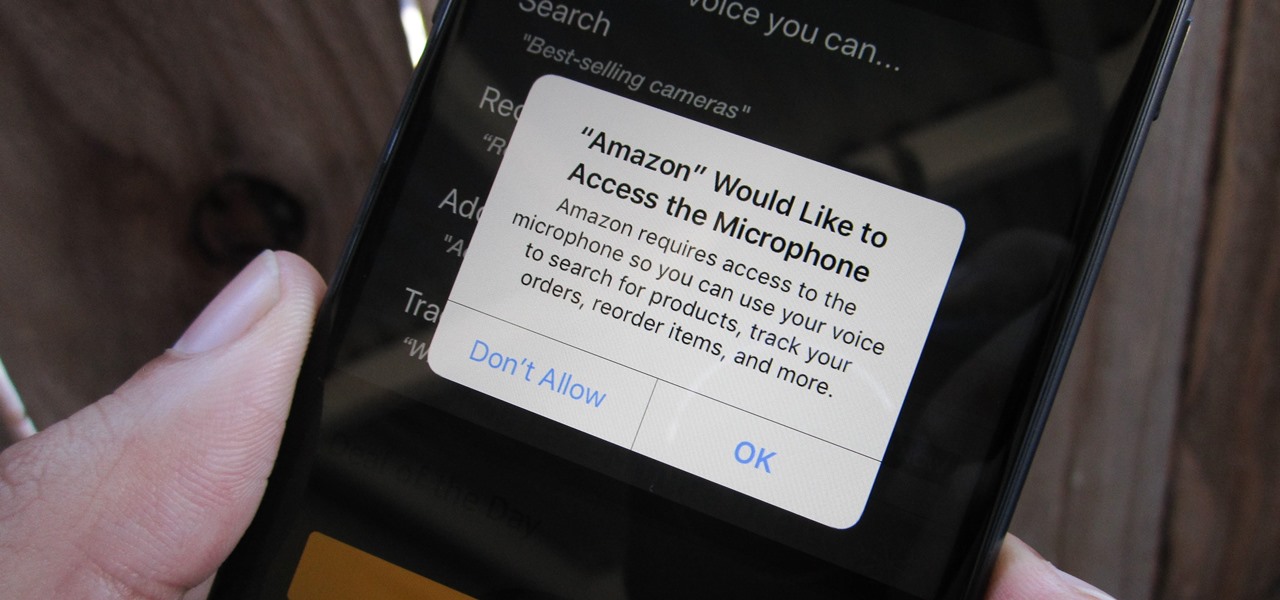
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.
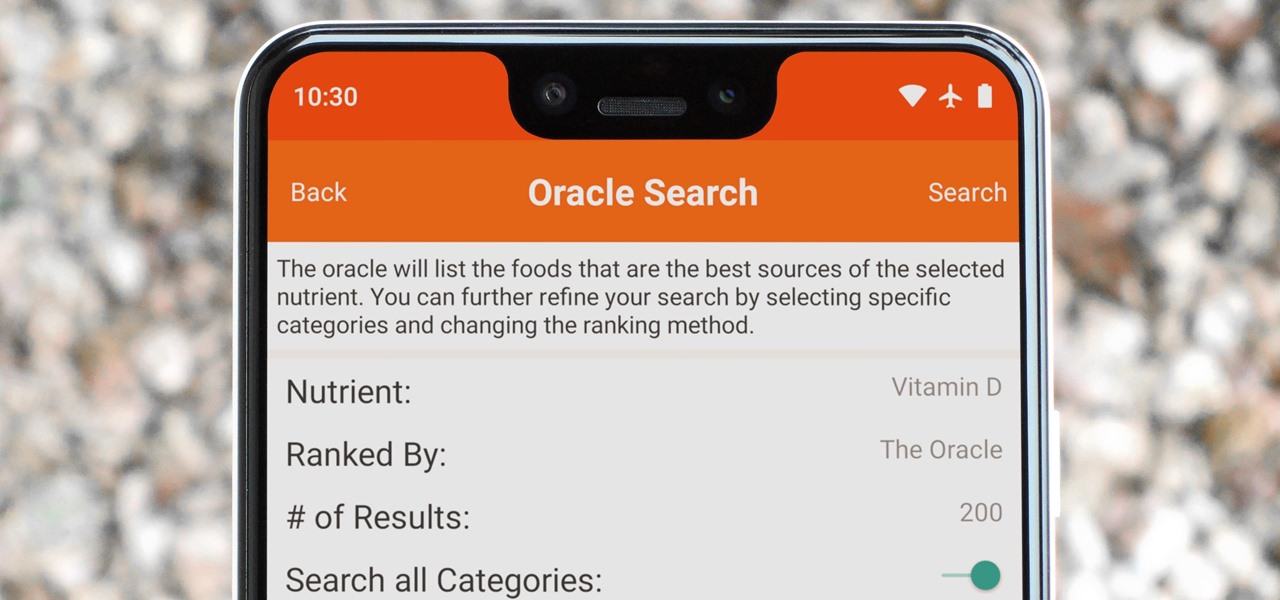
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.

Update February 25: The new Sony Xperia flagship has been announced, and it has a new name: The Sony Xperia 1. You can read all of the official specs and details at our full article on Sony's new model.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.
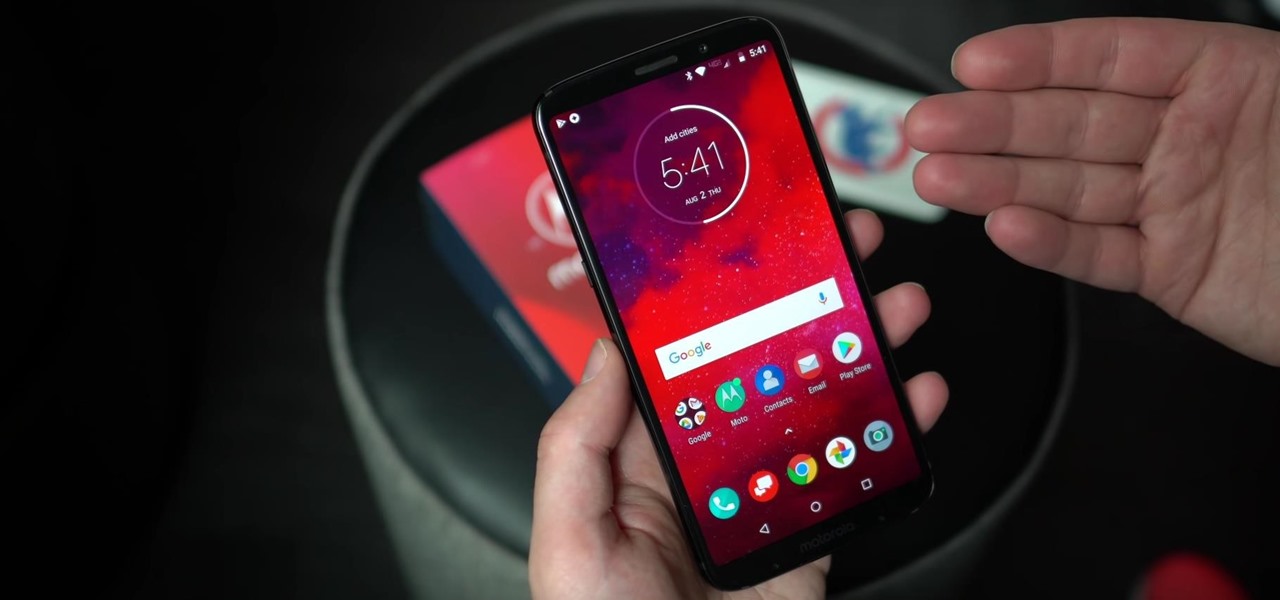
In 2018, Motorola is no longer the same brand that introduced the world to the Motorola Droid. The once iconic company is now part of the "Others" group, scrambling for fifth place. The newly-announced Moto Z3 perfectly embodies their current state with competitive specs ... if it came out last year.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

With Huawei's recent emergence as the second largest OEM in the world, the company was poised to finally make a big push into the US market. Instead, their efforts were derailed by an unlikely foe, the US government. As a result, American customers will miss out on the newly-released Huawei P20.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.