Zika is a threat to unborn babies — the virus can cause neurological damage if it infects a mother during pregnancy. But as with many things, our solutions to the problem aren't always all that much better than the problem itself.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

Our quest to find new antibiotics has taken a turn — a turn down the road, that is. A team of scientists from the University of Oklahoma is scooping up roadkill and searching for bacteria on them that might yield the world's next antibiotic.
Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.

Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corresponding with and want to make certain they are where they say they are. Or, maybe you are a forensic investigator tracking down a suspect who wrote a threatening email or hacked someone's company.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Apple's latest update for iPhones, iOS 13, introduces over 200 new and exciting features. Many of those changes come to Siri, resulting in a better, more useful version of the digital assistant we've known for years. If you simply look at iOS 13's webpage, however, you wouldn't realize just how much Siri has changed this time around. We're here to fill in the blanks.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

A deadly type of brain tumor and Zika-related brain damage in developing fetuses are devastating brain conditions that, at first glance, may seem unrelated. However, thanks to new research, their paths seem to cross in a way that could benefit patients. A new study has shown that Zika kills brain cancer stem cells, the kind of cells most resistant to treatment in patients with glioblastoma, a deadly brain tumor diagnosed in about 12,000 people in the US each year.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

Food is both a necessity and a joy. Many people enjoy exploring, cooking, eating, and learning about foods from around the world. But the picture isn't always rosy. A new report from the Centers for Disease Control and Prevention (CDC), highlights the ways and whereabouts of food that make us sick.

HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?

Bacteriotherapy sounds a lot more amenable of a term than "fecal transplant," yet they're both treatments that use bacteria itself to cure or treat infections. Fecal transplants, specifically, are an up-and-coming treatment option for a potentially deadly and difficult-to-treat diarrheal infection called Clostridium difficile.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing auroras. The solar storm that produced the electromagnetic pulse and caused all this mayhem is known as the Carrington Event, and storms like it happen about about once every century.

I consider myself a master of emoji, crafting complete sentences and paragraphs using strictly ideograms and smileys. However, everyone seems to have their own interpretation for each little image, so my elaborately clever emoji-only sentences can get lost in translation. But there's an easy way to translate emoji into their exact meaning, as well as decode everyone's mystifying emoji talk.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

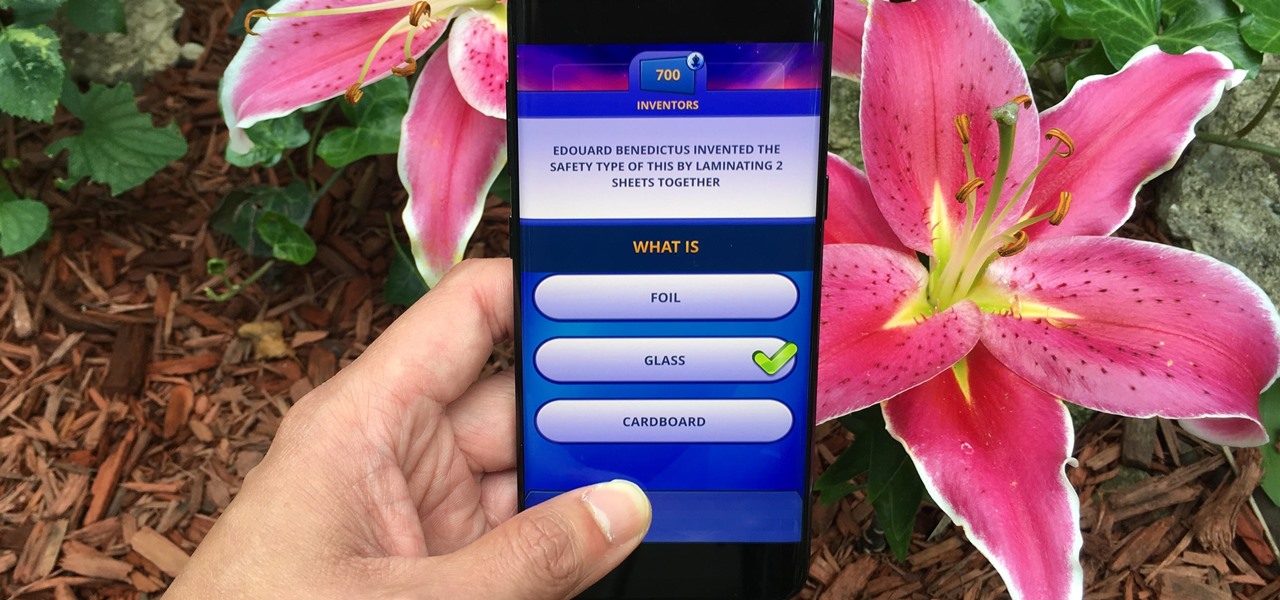
Trivia games are a great way to test your knowledge and learn about people and things you never knew of before. They're ideal in a group setting because they can serve as the perfect conversation starter when you're enjoying time with friends, family, or even complete strangers.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.