This week, Google showed off some wild new and innovative AR experiences that showcase the WebXR protocol for browser-based AR content, while 8th Wall applied its own web-based AR platform in service of Captain Morgan.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.
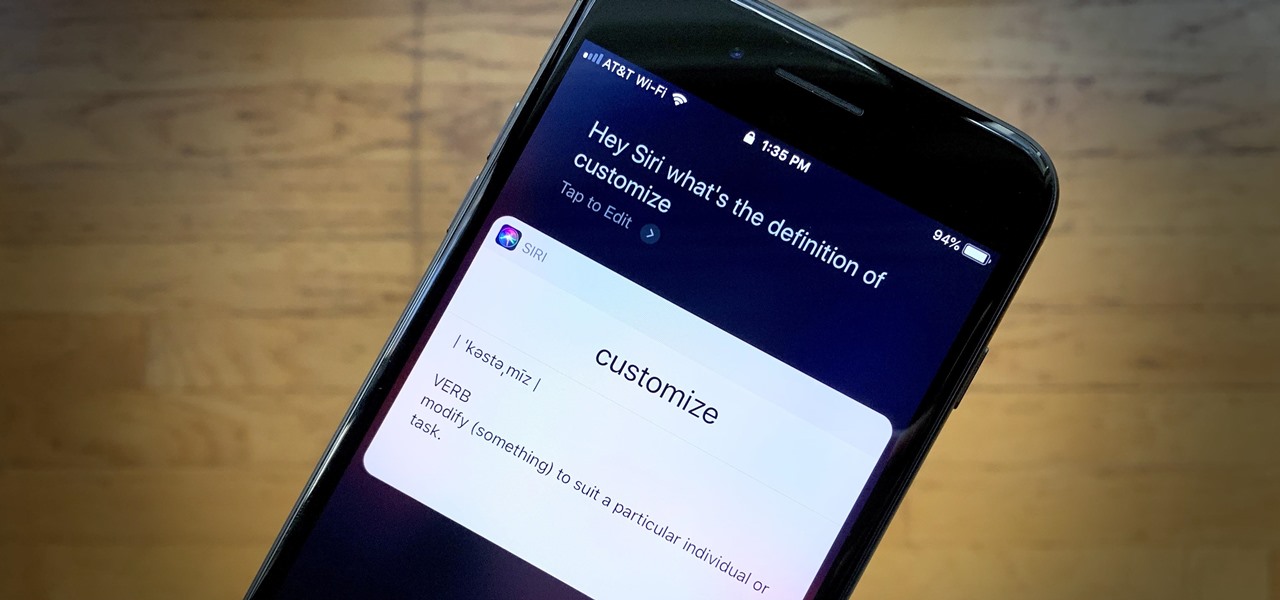
Out of the box, Apple's digital assistant could be a godsend or a nuisance, depending on your daily interactions it. No matter which camp you fall into, Siri can always be better suited to your personal needs with a little customization. You can make Siri a powerhouse not to be reckoned with, or you can minimize its presence if you only need Siri help sometimes — all without any jailbreaking.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

It's easy to start panicking when you delete an important email, but it's even easier to undo the mistake on your iPhone or iPad. You can retrieve an accidentally deleted email instantly on iOS and iPadOS with the help of a hidden gesture, and you'll be much more efficient with the Mail app once you learn how to use it.

Google Maps tracks everywhere you go with your smartphone, even when you're not using the app. Even if it's as mundane as your weekly grocery trip, Google Maps has it saved for you to see in its Android and iOS apps. And while it's mostly used for recommendations and your reference — you may not want Google Maps to keep such a rich location history.

Amber, emergency, and public safety alerts on an iPhone are loud — startle-you-to-death loud even. They can happen at any time, day or night, and sometimes back to back when you're in a big city. Those blaring sirens can wake you from sleep, interrupt an important meeting, or disrupt an entire movie theater mid-movie, but you can turn most of them off if you're tired of hearing them.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

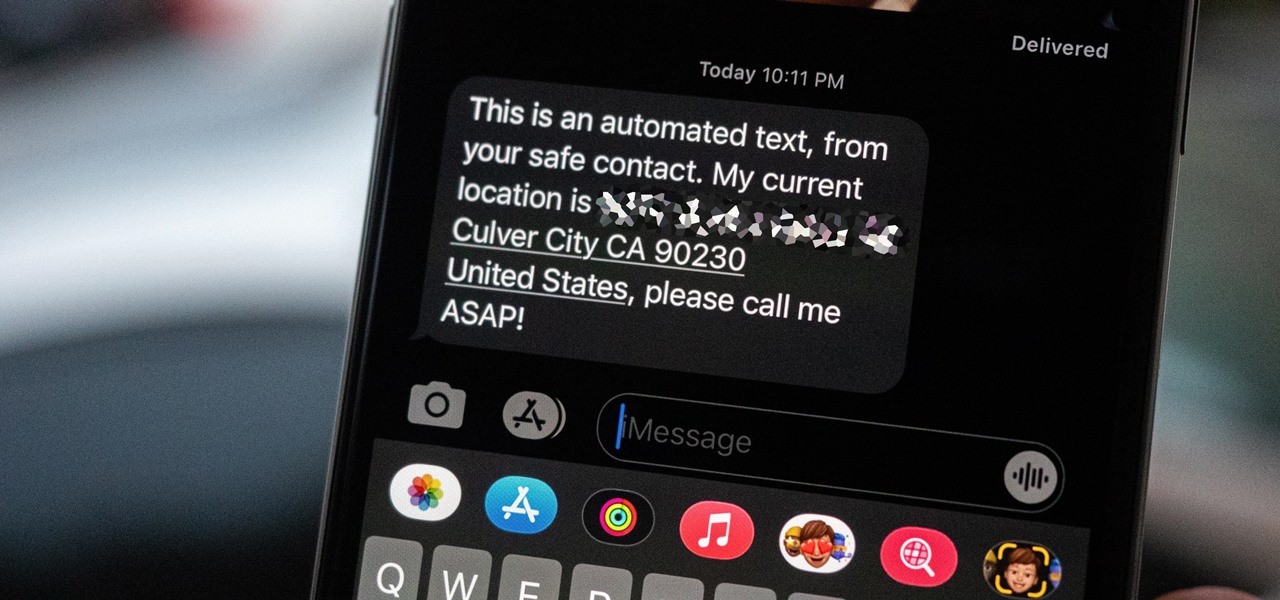
Strange or uncomfortable encounters can be difficult to get away from sometimes if you're overly polite and don't want to hurt anybody's feelings. Thankfully, your iPhone can help save the day, providing you with a plausible excuse to exit the scene without having to conjure up some last-minute reason on the spot.

ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone.

Apple Watch owners know there's a built-in way to remove water from the device's speaker. However, even though modern iPhones are IP67 and IP68 water resistant, there's no official way to deal with water-clogged speakers that can muffle audio and cause prolonged damage if not ejected. Older iPhone models have it even worse, but there are some easy things you can do to get that water out.

The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we could find so you know exactly what to expect when updating to iOS 12 on your iPhone.

Tomorrow's the 1st of April which means it's the one day of the year you can put aside the daily grind, and go at it Dwight Schrute and Jim Halpert style. Yes, there are easy apps to do your dirty work, but if you're old school and you like to do it the old fashioned way, here are 10 simple pranks for torturing your co-workers.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

After an update on Sept. 22, 2020, the Checkra1n jailbreaking tool expanded its compatibility to include iOS 12.0 to iOS 12.2, as well as iOS 13.5.1 to iOS 13.7. More importantly, however, it now can jailbreak iOS 14 on select iPhone models, with more support coming soon.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

The biggest problem with Netflix (which is hardly a real problem) is the overwhelming amount of content available for streaming. Browsing through profile-specific categories might help narrow down your search on something to watch, but some of those categories come and go without warning, and it's impossible to find them again—but not anymore.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Help Someone Having a Panic Attack. We show the best measures to take to relieve someone suffering a panic attack. Come to the support of friends, family, and other members of the community. Help someone having a panic attack.

Make roasted Australian lamb chops with yellow tomatoes marinated in sour cream and mint. Make roasted Australian lamb chops.

The Australian government has a dysfunctional history with video games. Any regular Yahtzee Croshaw follower can attest to that. The Parliament has established a series of unfortuante regulations that make games both highly taxed and overregulated in price. Bringing any goods all the way to an island in the bottom of the world is expensive to begin with, and new games in Australia can tip the scales at $80 or more.

Everybody loves a good fair ground ride and so why not give them something to panic about more than a few bloody pranks?

iPhone 4 Hipstamatic: Helga Viking Lens; Pistil Film; Flash off

Produced for Australian TV show HungryBeast, "Anatomy of a Computer Virus" is an infographic-in-motion "dissecting the nature and ramifications of Stuxnet, the first weapon made entirely out of code."

A skateboarder pulls an inverted handplant in a distant, upside-down land.

People grumbling their way through the grimness of winter have better recall than those enjoying a carefree, sunny day, Australian researchers have found.

Pen & Paper is an e-magazine published by WhiteSpac3, an online community for Australian artists, galleries and art lovers. This zine showcases their artist's latest works. Every two months it is distributed to all registered individuals including galleries and collectors across Australia. Register for FREE now and grab a copy!

An Australian Liberal senator has slammed the use of Lego to promote creativity among ABC staff as a "bizarre" waste of money, suggesting finger painting would have been cheaper and just as effective.

Massive bouncy ball installation by Australian artist Nike Savvas. Entitled "Full of Love and Full of Wonder", each bouncy ball "represents the very atoms that are the fundamental structural units of all things".

When you spill coffee on a carpet, your first reaction might reasonably be PANIC. However, removing annoying coffee stains is not as hard as you might think. Here's a quick and easy way to really lift that coffee from your carpet. Clean coffee from a carpet.

This prank/stunt pays tribute the original Happy Days episode that started the phrase, "Jump the Shark". The elaborate prank involves setting up a ski ramp to an ocean buoyed caged (a la Happy Days). The shark is a realistic animatronic rental (I looked into it...they do exist and can be used for ocean shoots). The unsuspecting skier (of your choosing) dresses like "The Fonz" ...except his leather jacket features chum-filled pockets with large chunks of fresh tuna attached to the jacket. As t...

An original musical composition created by cutting together existing sounds from within David Fincher's films. There is NO outside audio, sound effects, or music. David Fincher is an Academy Award nominated director.