Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

There are more ways to finding your missing iPhone than using Apple's own "Find My iPhone" tool in iCloud. If you just need help tracking down your iPhone in your home or at a friend's house, Find My iPhone isn't necessarily the most convenient thing to do when you've got these other options to try out first.

When you leave your iPhone on a table or anywhere within somebody else's eyeshot, a private message may pop up on your lock screen that could be read by anyone who sees it. But there's a way to keep others from reading your possibly sensitive text messages and emails without giving up the convenience of lock screen notifications entirely.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

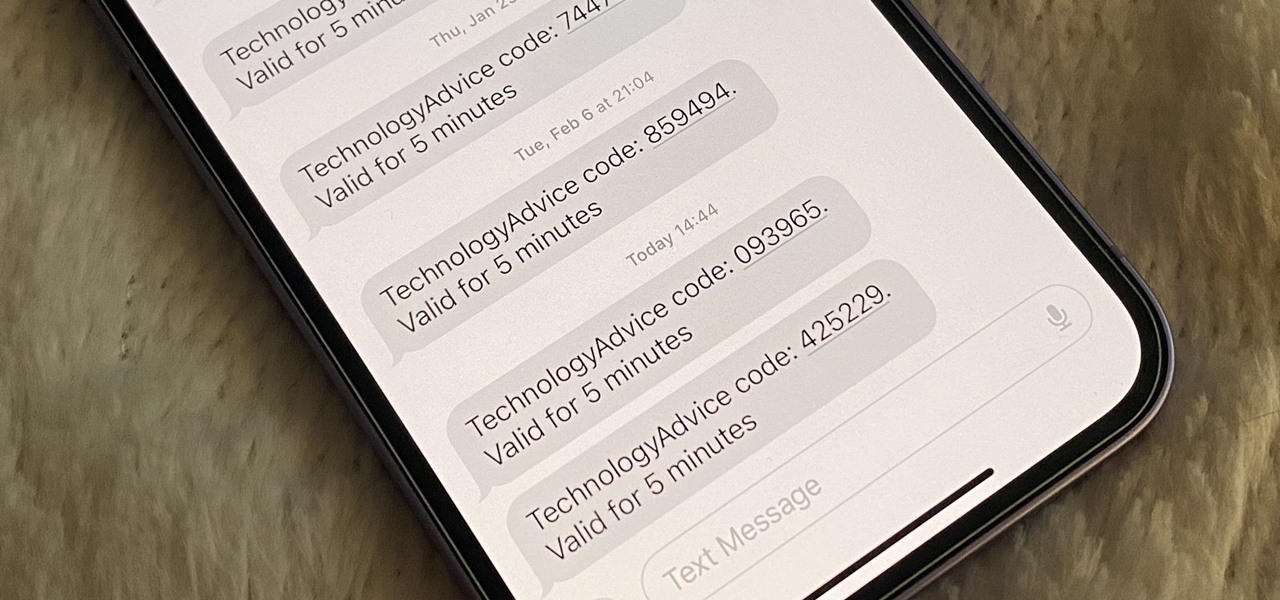
Many of your accounts online likely require two-factor authentication (2FA) or two-step verification (2SV) to confirm your identity when logging in, and there's a good chance the second factor or step for each is a one-time email or SMS verification code. If you get a lot of email and SMS codes, it can clutter your Mail and Messages apps with junk if you don't delete the messages after signing in.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

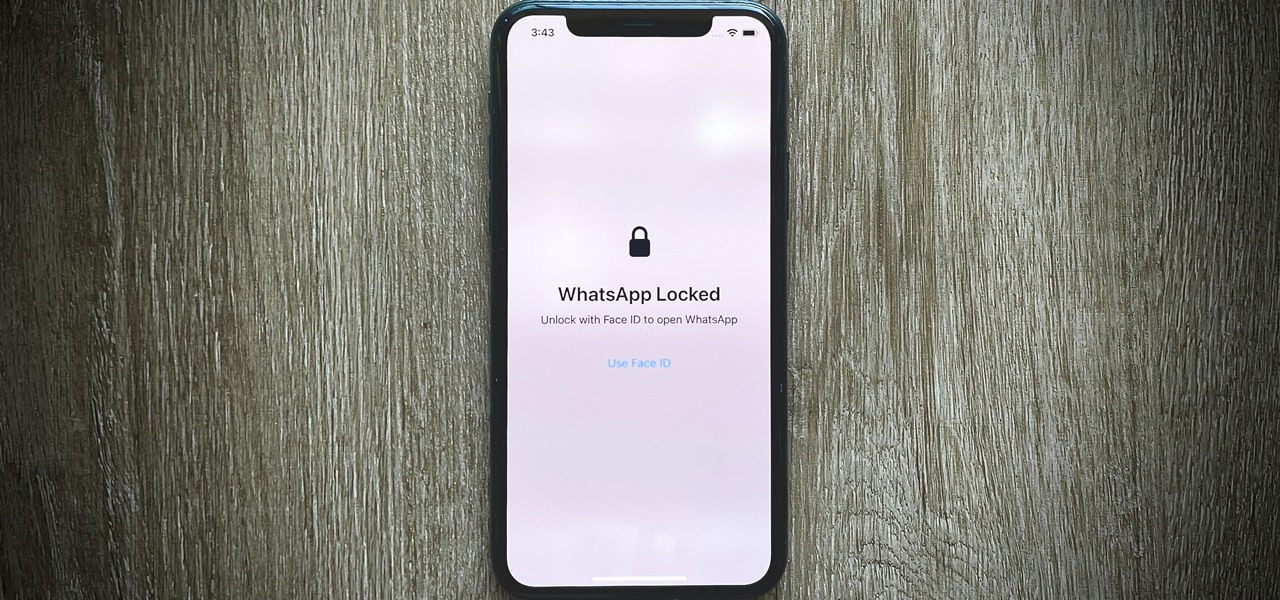
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

The Moto G7 Power is a phone that screams battery life. From its display resolution to the massive battery, it was designed for those who hate to recharge each night. But unlike other battery-focused smartphones, it comes at a price almost anyone can afford.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

You can send and receive money from your iPhone using Venmo, Square Cash, Facebook Messenger, and even Snapchat. There's also Zelle, which offers quick-pay solutions in major banking apps such as Bank of America, Chase, and Wells Fargo. However, Apple has a built-in system to transfer money, with person-to-person payments being available in the Messages app ever since iOS 11.2.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

If you use Apple's Mail app on your iPhone for iCloud and third-party email accounts, install the new iOS update ASAP if you haven't already. While there's not a colossal number of new features, the latest tools and improvements are powerful enough to make the update feel like Mail's biggest ever — and there are features we've been waiting for for years!

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

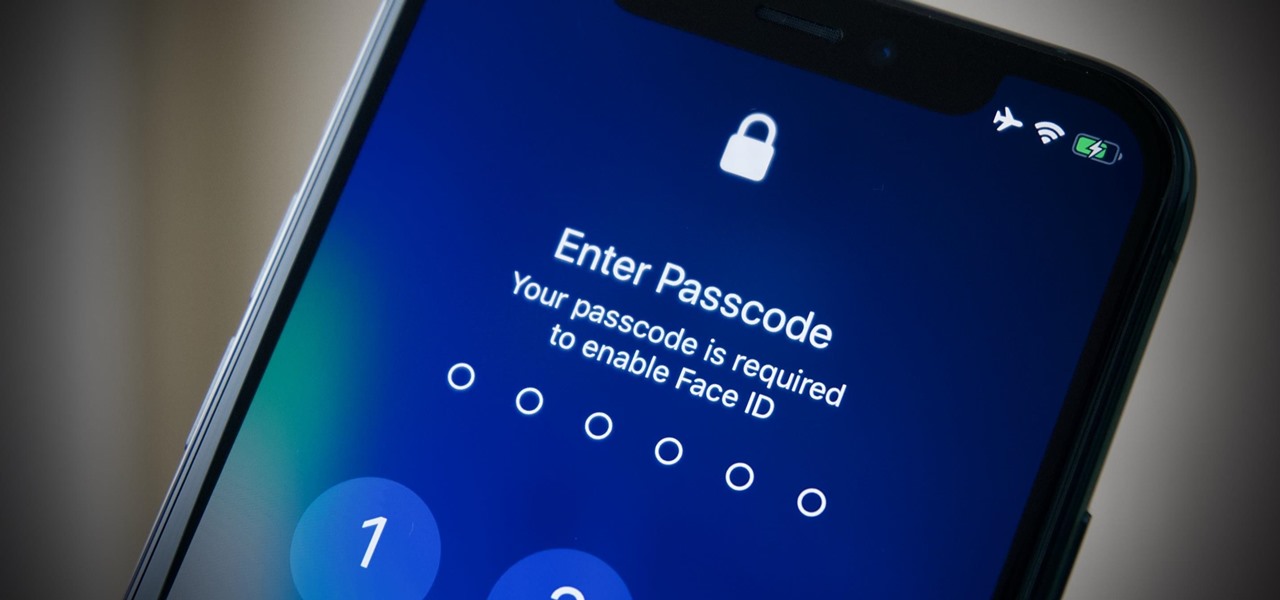
Here's the situation: you need Face ID or Touch ID disabled, yesterday. You don't have time to dig around in your settings, slowly working through an authentication reset. If you find yourself in a place where you think your own face or fingerprint will be used against you, use this trick to instantly protect your iPhone.

Sorry, Galaxys S11–19, Samsung's jumping straight to Galaxy S20 this year. They're also going with essentially three base models before accounting for niche variants. Of these three models, it's clear which one's the best: the Galaxy S20 Ultra.

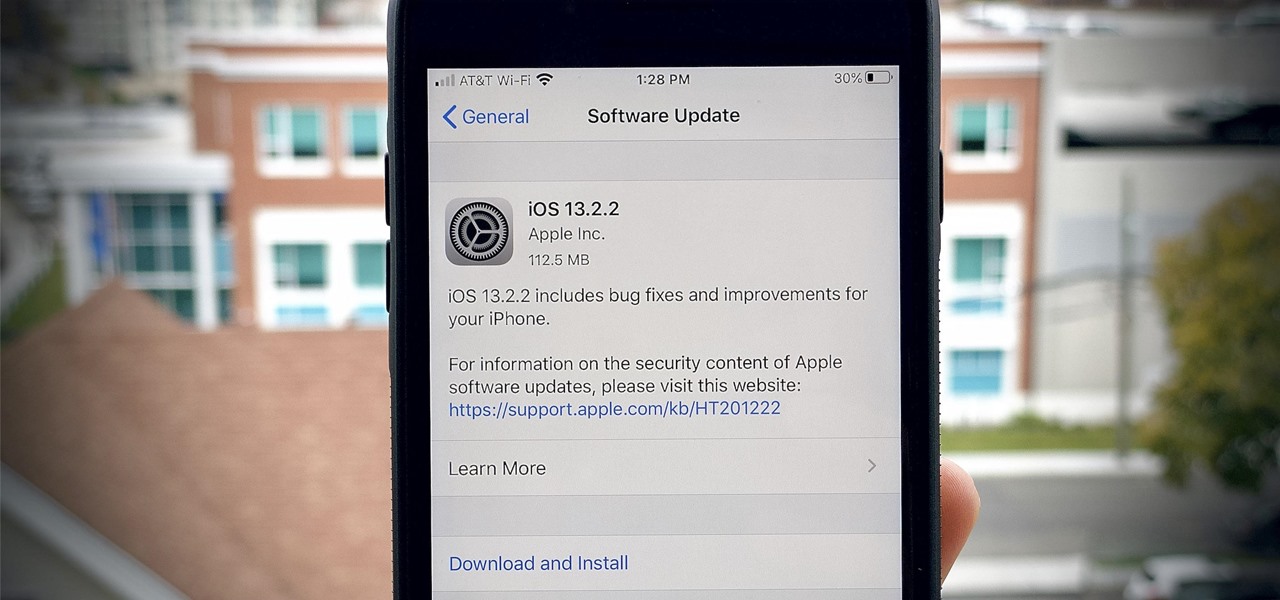
If you're a beta tester, you know Apple released iOS 13.3 this week, bringing with it stability for multitasking as well as minor changes throughout the OS. It seems Apple doesn't want the rest of us to go without this critical patch, as the company releases iOS 13.2.2 today, Thursday, Nov. 7.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

It's always great to see a company pull off a bit of augmented reality magic, but what we see is not always what it's cracked up to be.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

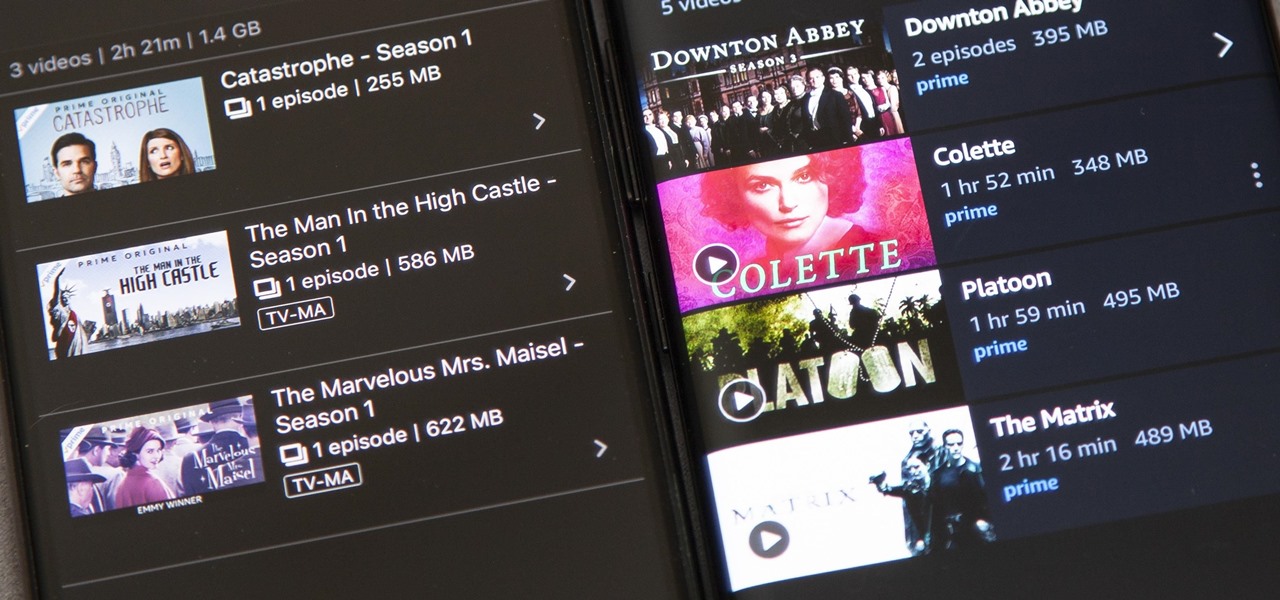
Back in 2015, Amazon Prime Video was the first subscription-based streaming service to introduce the ability to download movies and TV shows for offline viewing on mobile devices. For travelers and users with limited data plans that like to watch films and episodes on the go, this was a godsend. Amazon has updated its apps many times since then, but the process remains relatively the same.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

With the best selling phone on Amazon in 2018, Lenovo had big shoes to fill when making the successor of the Moto G6. Fortunately, Lenovo was up to the task. The Moto G7 continues to provide a high performance-to-price ratio, offering a worthwhile upgrade for G6 users while remaining budget friendly.

Get ready for more software testing. Just two days after the official release of iOS 12.1, Apple seeded public software testers iOS 12.1.1 — one day after developers received the update. While the rest of the iOS world is just getting to know all of the cool, new 12.1 features, testers are now sinking their teeth into what the next iteration of iOS has to offer.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

For Apple Pay users, the iPhone X, XS, XS Max, or XR will be an adjustment. Gone are the days where you could rest your finger on the Home button and hold your device within range of a contactless reader. Without Touch ID on the iPhone X, this isn't possible. But have no fear, Face ID is here.