The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Among the many new changes ushered in by the iPhone 7, only one has the potential to completely change the way you interact with your smartphone—a new 3D Touch-enabled home button. Instead of the mechanical click we've grown accustomed to, your home button will now behave like the rest of the phone's touch screen interface.

Samsung's next Galaxy Note smartphone is expected to contain some nifty new additions that the company hopes will give it the long desired edge it has been seeking over Apple. One of those features that might make the difference? An iris scanner, which could make it the first major smartphone on the market to have that technology included.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Anything free is cool, but getting a fully upgraded operating system for the great price of nothing is downright awesome. A recent exploit was uncovered that allows users to get a free copy of Windows 8 Pro directly from Microsoft's own website. Seriously.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

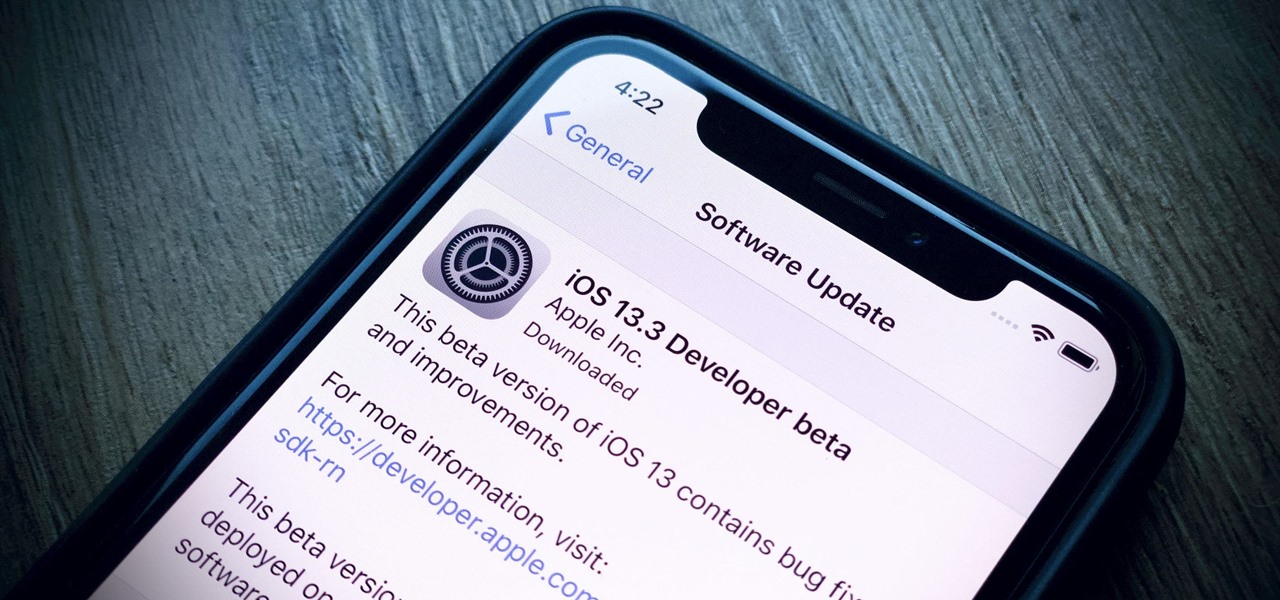
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta.

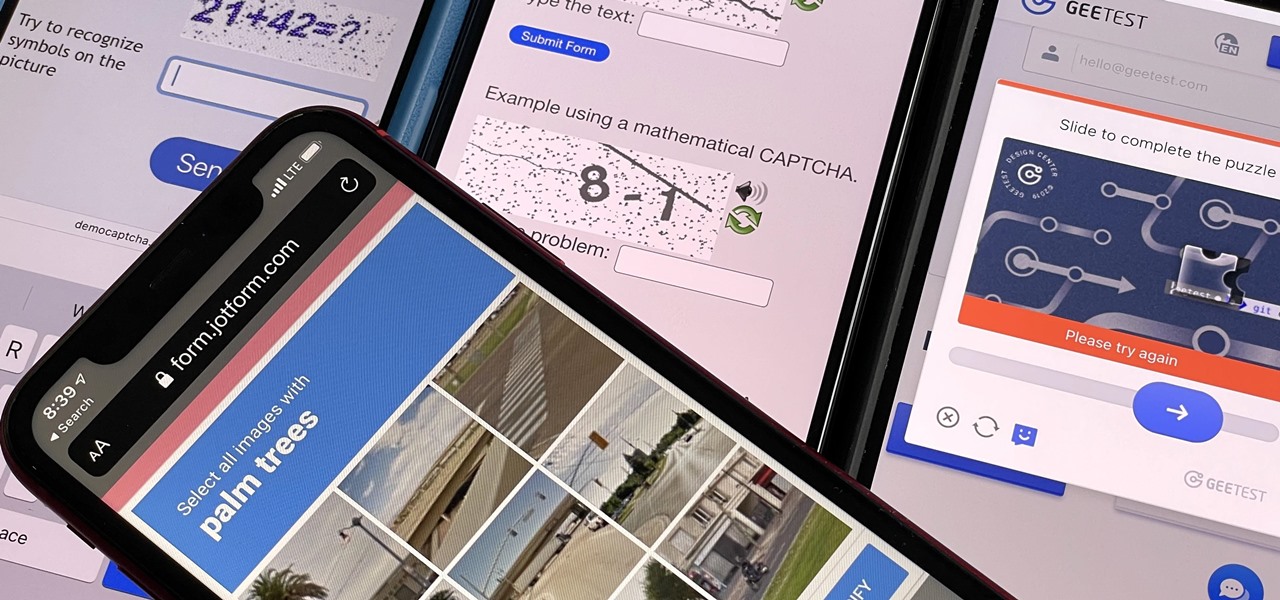
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.

Apple pushed out the second beta for iOS 14.3 to developers and public beta testers, which includes a few quick fixes for issues in Apple ProRAW for iPhone 12 Pro and 12 Pro Max and HomeKit. It also gives home screen shortcuts a more seamless transition. It is not yet known if the update addresses missing SMS texts that have been plaguing users across carriers, including us.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

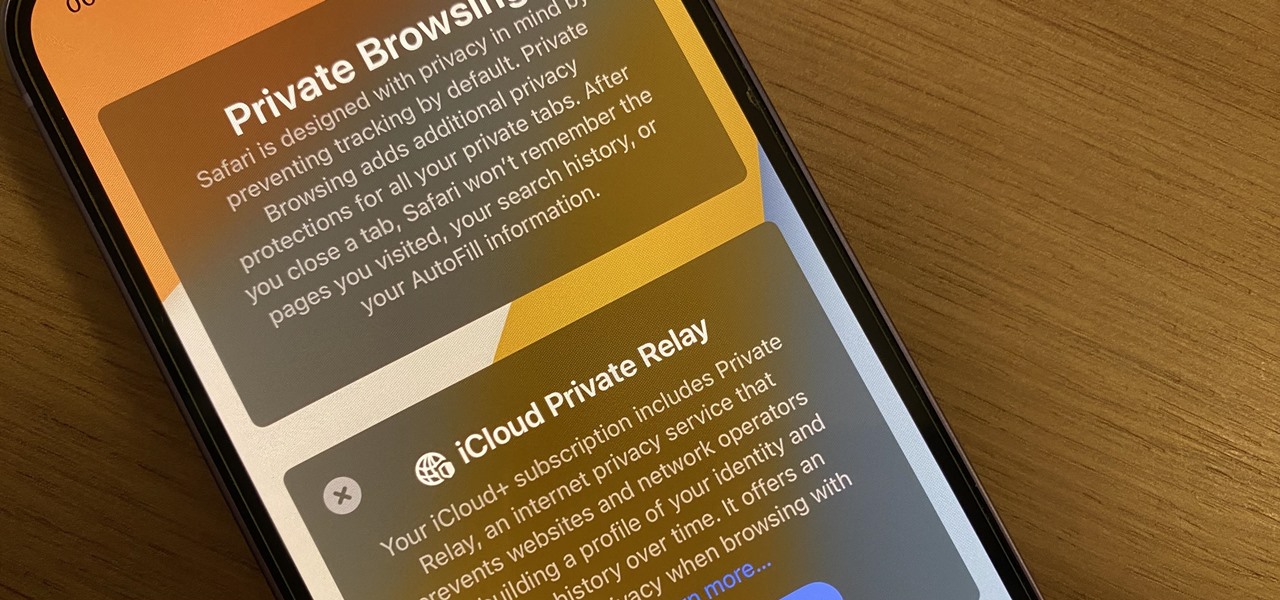
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Apple officially unveiled iOS 14 on June 22 at its first all-virtual WWDC. After months of beta testing, iOS 14 hit iPhones on Sept. 16, but that doesn't mean that Apple is done beta testing iOS 14. There will be new features to try out right up until iOS 15 comes out next year.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

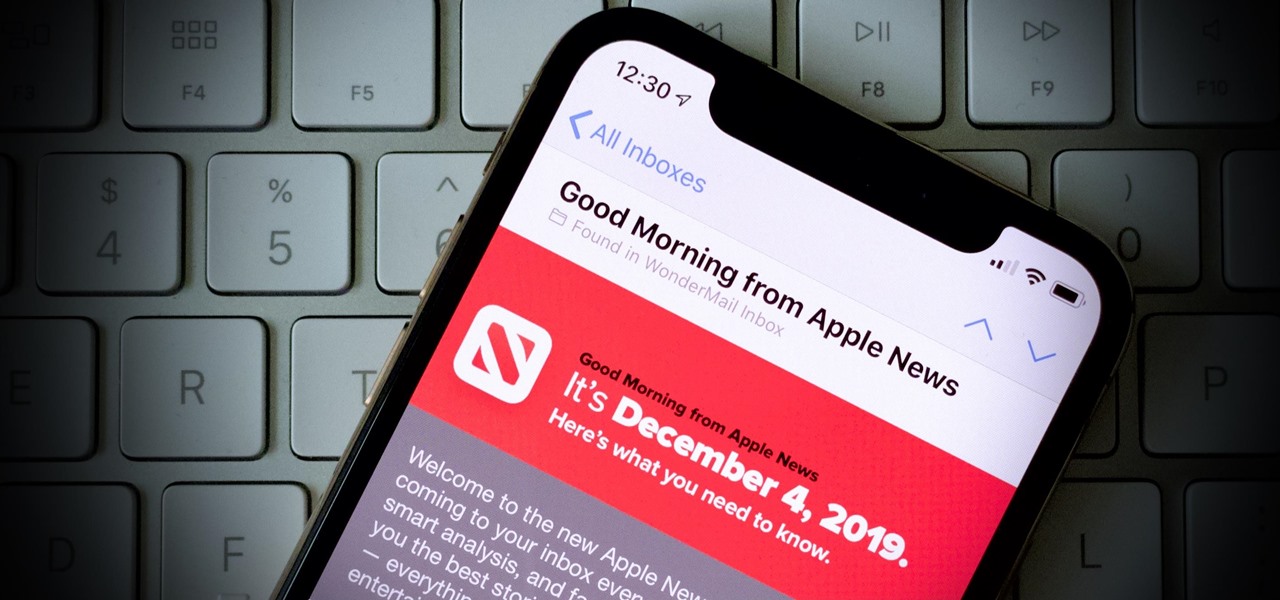
While the App Store is filled with news aggregators, Apple News is a solid choice when it comes to keeping up with current events. Apple recently made it easier than ever to stay informed, thanks to a daily newsletter sent straight to your inbox. The problem? It's unclear how to sign up for this newsletter, and it's equally unclear how to unsubscribe.

In a bold move, Samsung has decided to forgo the Galaxy S11 moniker and jump straight to the S20. Perhaps it's marketing for the new 20:9 aspect ratio and 120 Hz display, or maybe it's just the fact that it's releasing in 2020.

Despite the hype and potential of immersive computing, the augmented reality industry is showing that it is not invincible, as another AR hardware maker, this time Osterhout Design Group (ODG), is reportedly going out of business.

Apple wastes no time with betas. Right on the heels of the official release of iOS 12.1, Apple released the first beta for iOS 12.1.1 to developers on Wednesday, Oct. 31. The update comes just one day after iOS 12.1, which itself was in beta development for 43 days this year. The denotation for 12.1.1 indicates it's a minor update over 12.1, and there are only a few things in its release notes.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

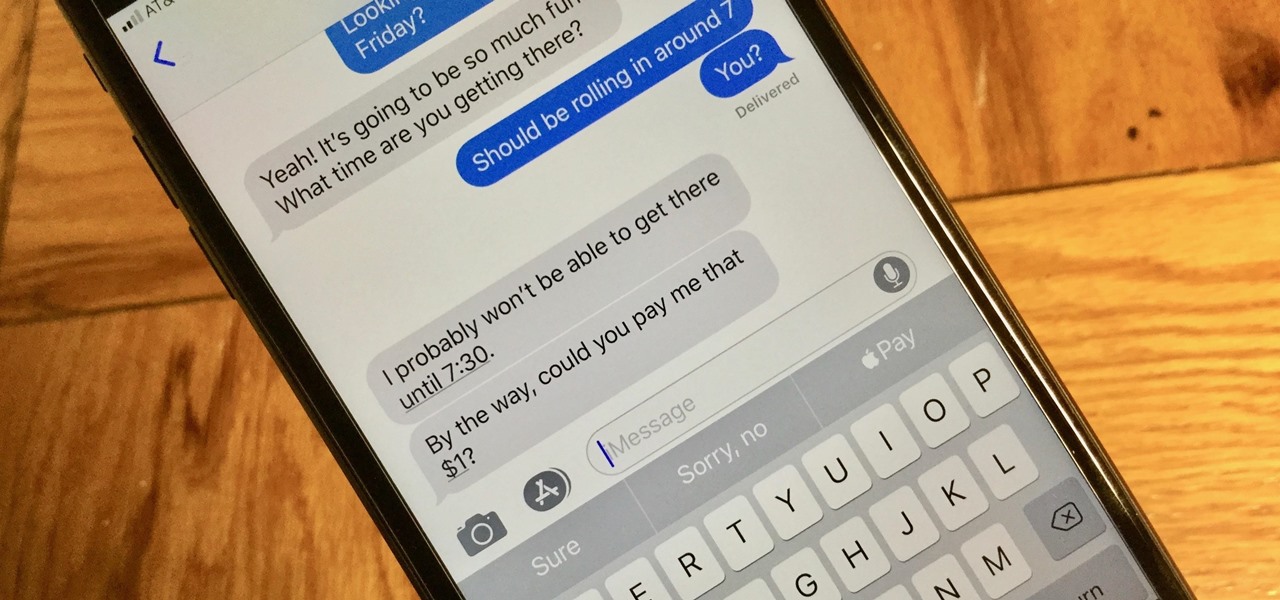
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

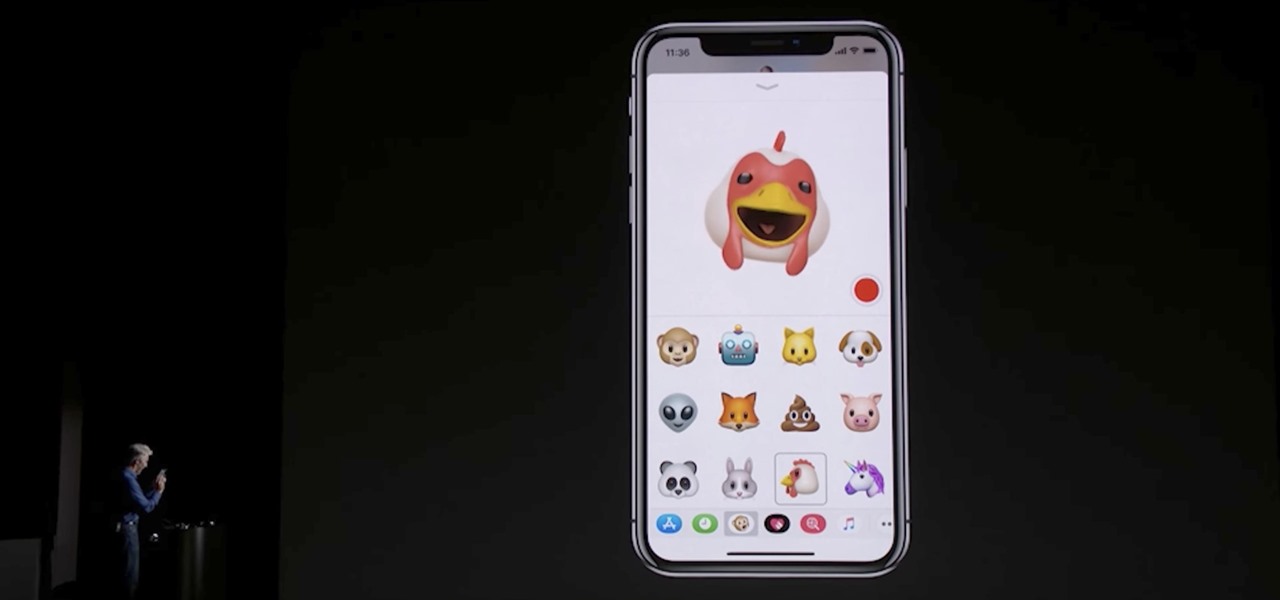
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis may seem at first, the tech behind them is undeniably impressive. In fact, it's possibly the most technically advanced feature of the iPhone X.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

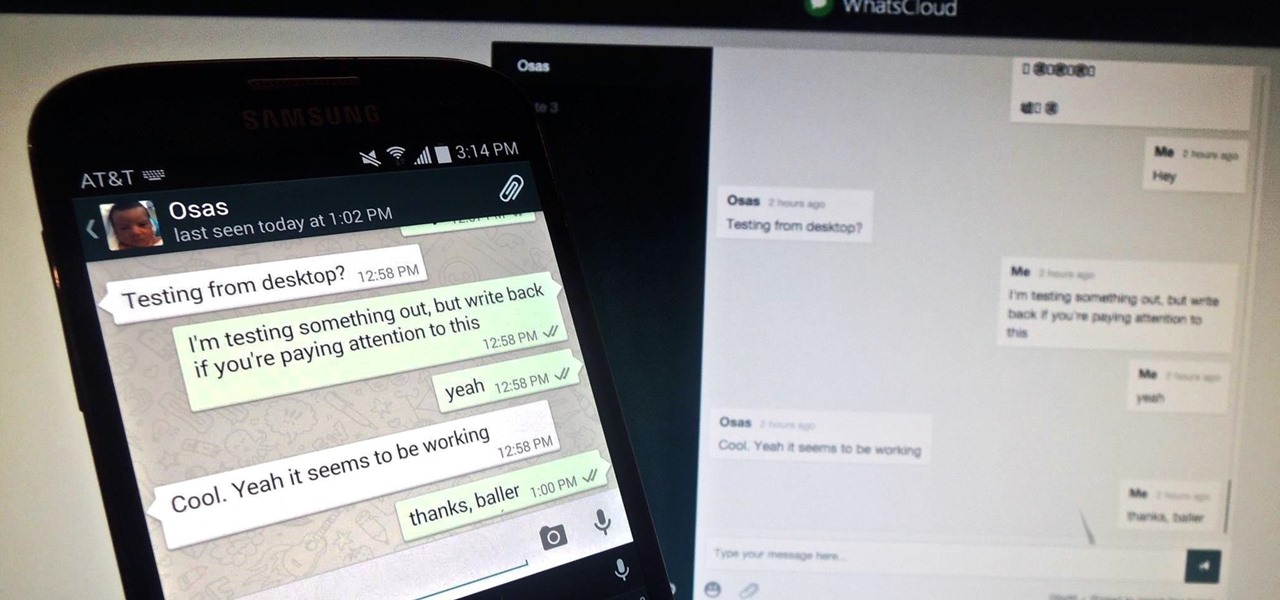
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.