The Sharknado franchise is, somehow, releasing a fifth movie "Sharknado 5: Global Swarming" (groan) next month. In anticipation of the film's release, the company has decided to create an augmented reality mobile game called, prepare yourself, "Sharknado: ShARkmented Reality".

I don't know how I feel about this. On the one hand, Futurama: Worlds of Tomorrow has charm. The original writers are attached to this project, and that shows in the humorous dialogue between characters.

A patent from Universal was filed today looking to improve the visual experience at Universal Studios Parks.

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.

The way we tell stories is about to change. Imagine you're hearing a story when suddenly characters and images from the tale start to appear in your world. This immersive way of storytelling is in the not-so-distant future thanks to the Microsoft HoloLens and Rémy Martin.

If you're a tech enthusiast, there's no way you're not watching HBO's Silicon Valley. So you surely know the Pied Piper crew's latest shenanigans involve an app that uses a phone's camera to find facts about food items — a sort of Shazaam for food, if you may.

Futurama: Worlds of Tomorrow has finally touched down as a soft launch for Android. Join Fry and his lovable band of interstellar misfits on a quest to rebuild New New York, traveling the stars, fighting aliens, and delivering packages while doing so. As with any city building and quest game, progressing through the game equals leveling up, which in turn unlocks new buildings and outfits to further beautify your characters and the city they live in. And the best part of all, Futurama's creato...

Blizzard's Hearthstone was a rousing success with more than 10 million downloads on the Google Play Store. Not taking things lying down, Bethesda, the creator of The Elder Scrolls, has come up with a card game based off its popular fantasy franchise. The Elder Scrolls: Legends is now out in the wild, though, officially only available for select Android tablets. But with a little creativity, there's a way to game the system and play Legends on any Android device. The Elder Scrolls: Legends is ...

In addition to trying to give Pokémon a life on the HoloLens, Sky Zhou, a founding member of mixed reality studio Matrix Inception, won Microsoft's Actiongram Fantasy Contest Quest last month for his video concept on slaying dragons. But fantastical creatures aren't the only thing Sky can whip up on the HoloLens.

Super Mario Bros. is one of the most renowned games in history. It helped resurrect a dying video game industry in the mid-'80s and still remains one of the best-selling video games of all time—one reason why the new NES Classic Edition is so popular and impossible to get these days. Its simple story of a plumber trying to rescue a princess resulted in a video game empire for Nintendo.

Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can type or rely on predictive swiping.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Ideally, wine would stay as perfect and delicious as the day it was first uncorked forever. But, thanks to a pesky process called oxidation, re-corked wine (no matter how you do it) pales in comparison to a fresh's bottles original magic.

Hello there Nullbytes, In my previous tutorial found here,

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

Star Wars season is definitely upon us. No matter where you turn, you can't go a day without being bombarded by merchandising and co-branding advertisements that attempt to draw a parallel between some character from a galaxy far, far away and a galactic cruiser like the Dodge Viper, or a midichlorian-laden power source like Duracell. Yep, it's kind of annoying, but at least we can get some fun out of it here and there.

Starting a few months back, you might have noticed that some text messages you received from certain friends or family members had blank or missing characters. This was because Apple included all of the new Unicode 8.0 emojis in an update to their iPhones, but Android devices didn't have some of these just yet, so they weren't capable of displaying them.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

Whether you've watched Game of Thrones or read the A Song of Ice and Fire series by George R. R. Martin, you probably know the White Walkers (aka the Others) all too well. They're creepy, otherworldly humanoids shrouded in icy white skin and ice-blue eyes. They are not to be confused with the wights, the reanimated corpses that the White Walkers control.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

In an attempt to increase advertising revenues, Snapchat introduced Discover back in January of this year, a feature that brought a handful of prominent media partners, such as CNN, ESPN, and Vice to your feed, along with their tailored news stories and videos.

Saying that I was obsessed with Pokémon as a child would be a serious understatement, and even though I'm not the Pokémon fanatic I once was doesn't mean I don't love playing still. However, I do often find myself dumbfounded by all of the new features and characters in each generation.

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

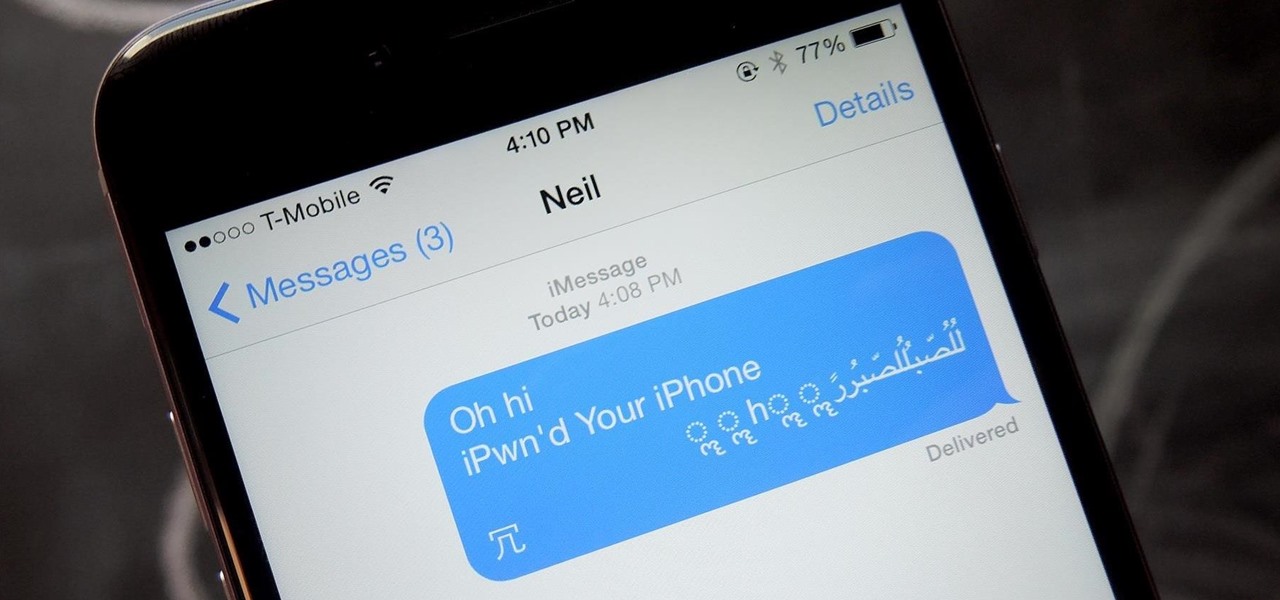
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

With the release of the Nexus 5 back in 2013 came the Google Now Launcher, which has become the go-to choice for many Android users, especially those who prefer the Nexus line. With its integration of the Google Now page and the always-listening hotword detection, you'd be hard-pressed to find a more complete and useful launcher.

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

When you send an emoji from your Android device to someone that uses an iPhone, they don't see the same smiley that you do. And while there is a cross-platform standard for emojis, these don't work the same way as unicode-based smilies or dongers, so not every operating system displays these little guys the same way.

With the advent of text messaging, our communication habits have changed drastically. Social niceties are still there, but we budget our words a little more since they have to be typed out rather than spoken. After all, SMS stands for "Short Message Service," so this is the nature of the beast.

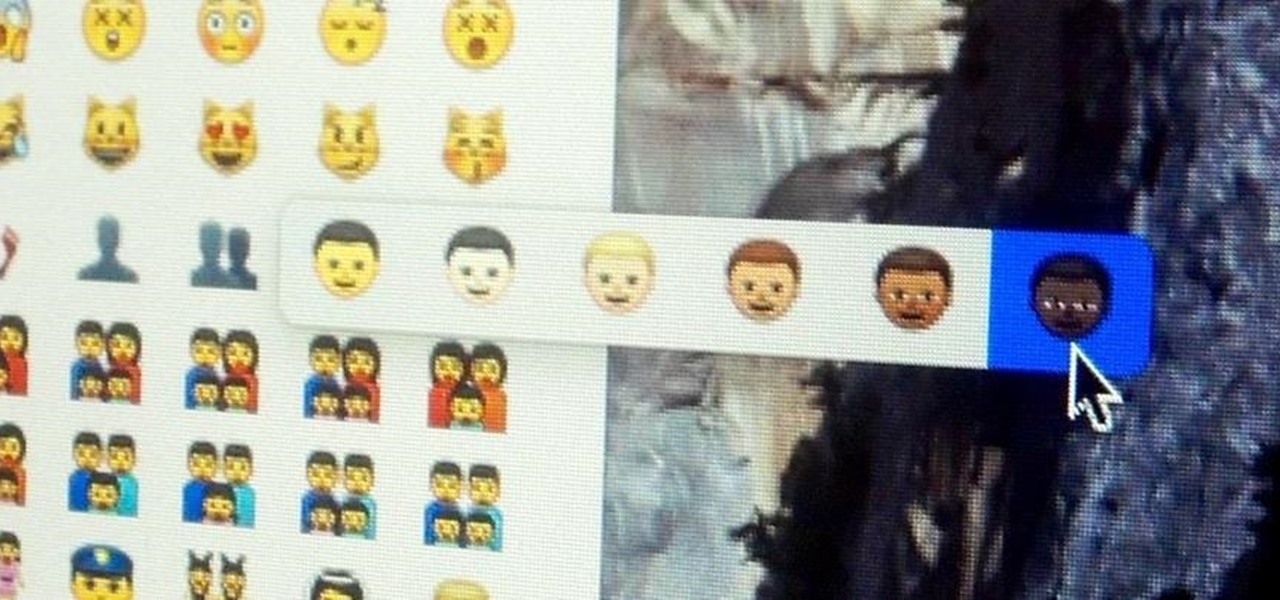
Apple just recently launched its 10.10.3 Public Beta for Mac OS X Yosemite, and while it comes with mostly bug fixes for 10.10.2, it also includes a brand new Photos application that's meant to replace iPhoto and Aperture, as well as the inclusion of more diverse emojis.

Lollipop brought a complete visual overhaul to Android, and while the vast majority of changes have been met with praise, some UI tweaks missed their mark.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

Marmite: either you love the stuff or hate it. ("Love" meaning you are British and grew up eating it, and "hate" meaning you are everyone else.)