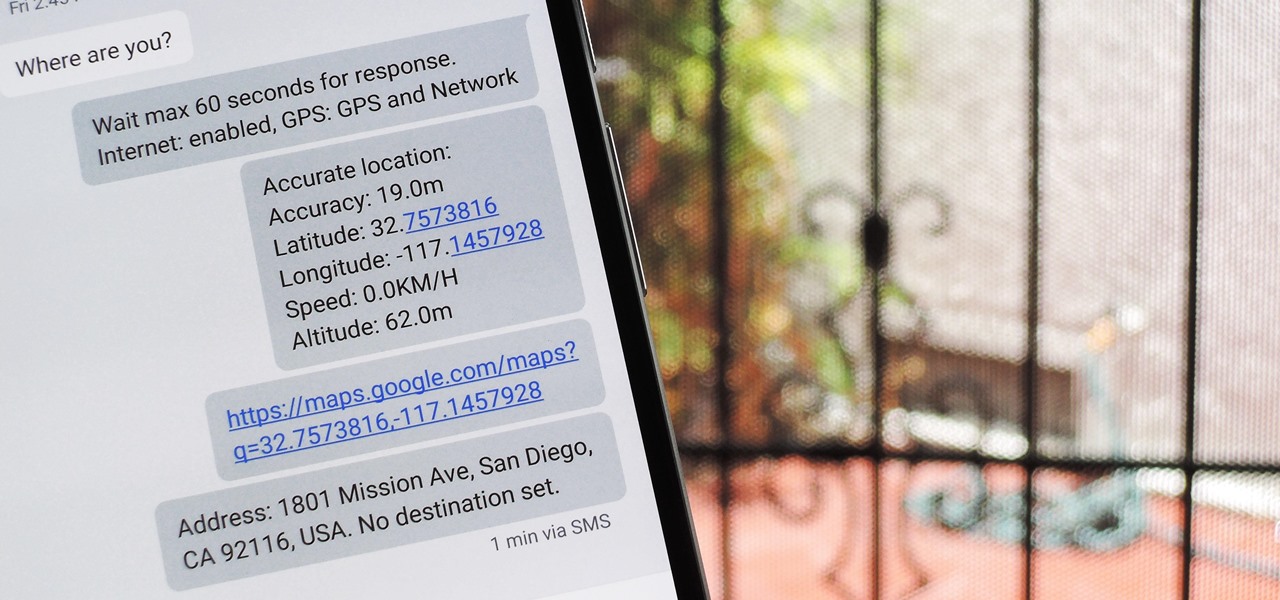
When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.
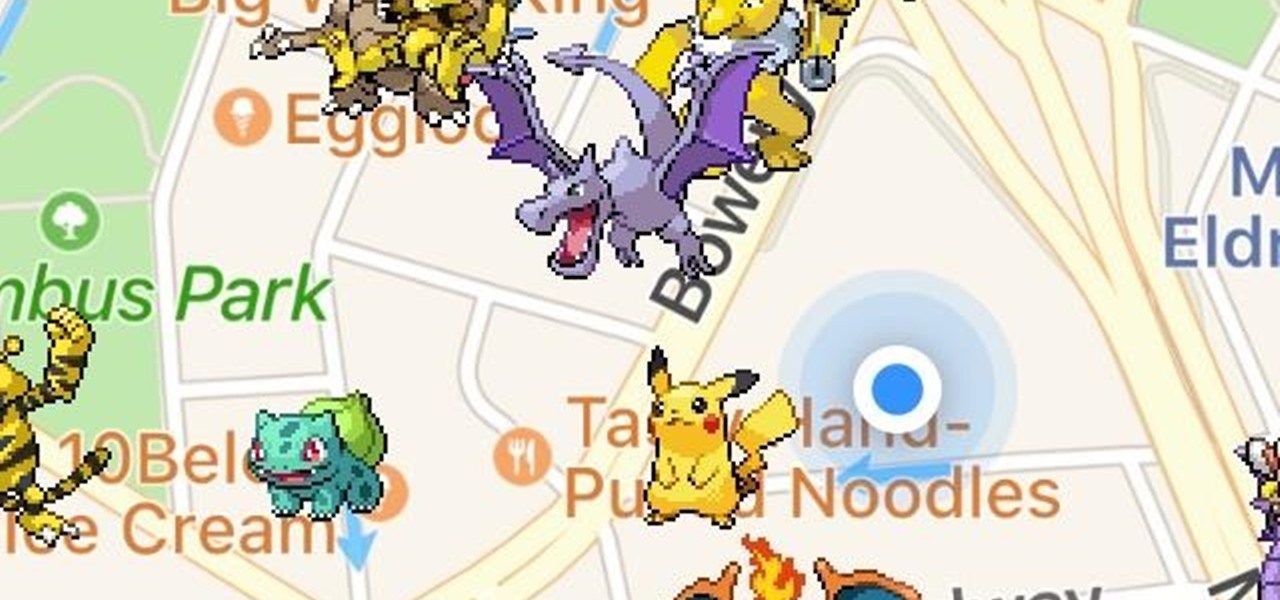
The only way to know which Pokémon are in your area in Pokémon GO is the cryptic "nearby" list, which sometimes doesn't work—and also doesn't tell you which direction to head off to hunt that Pokémon you're looking for.

Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Look)

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

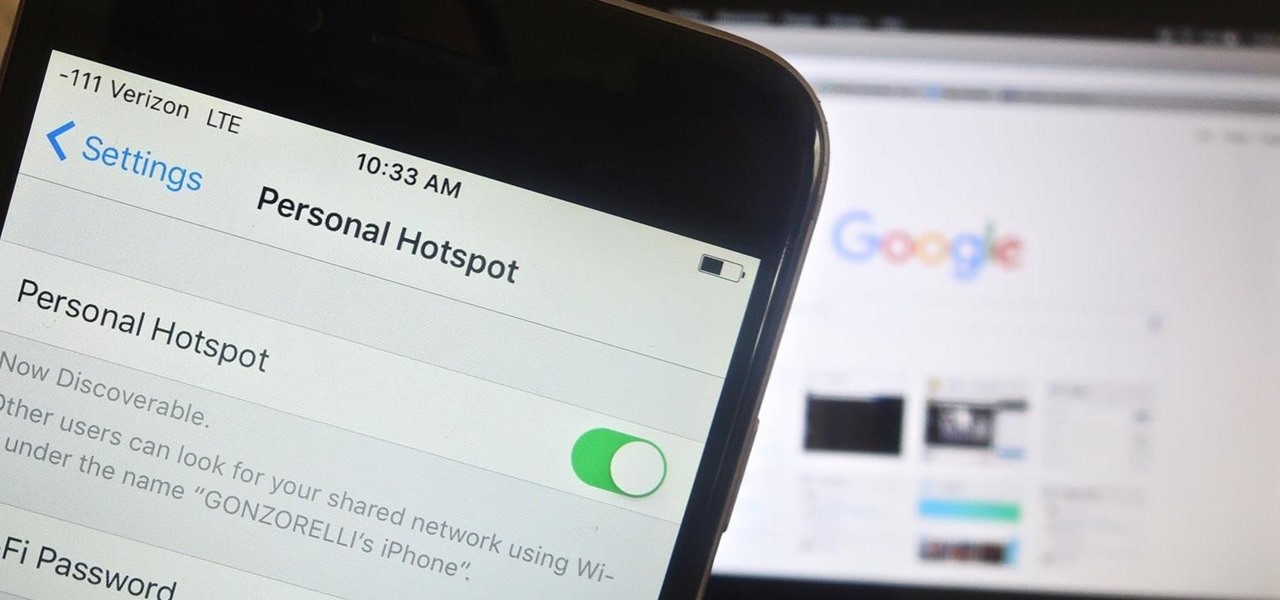
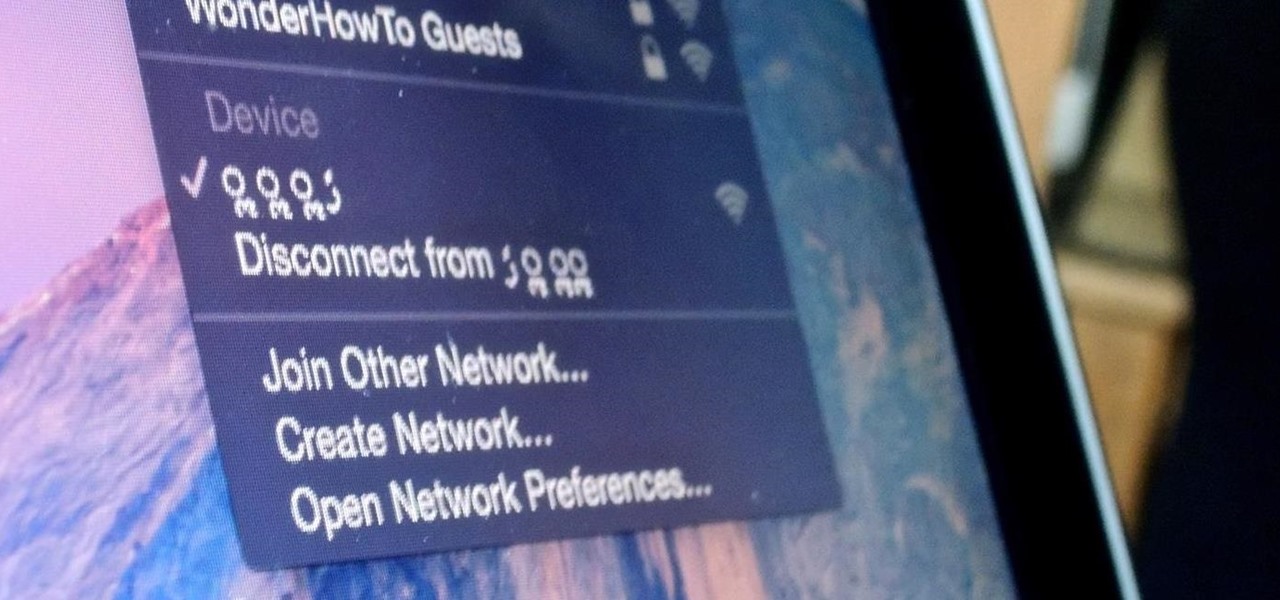
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

Whether you choose the sassy face of someone like your inner Disgust from Inside Out, or you're the happy-go-lucky Joy, chances are you're well-versed in expressing your inner "ew." So for this Halloween, take pride in your judgmental self by donning a DIY Disgust mask.

Apple just sent out a new update to their iPhones, and while that normally wouldn't have any impact on Android users, the fact that they included 184 new emojis means that the text messages you receive from friends and family members with iOS devices might come across with blank or missing characters.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

Relentless in its fury, the iOS text messaging exploit that exploded onto the scene late last week seems to do more damage than initially reported.

Emojis, smilies, emoticons—whatever you prefer to call them, these fun little guys can bring a text-based conversation to life. If you're worried that someone's sarcasm meter might be broken, just toss in a wink at the end of your message. Or perhaps you can't quite put your sentiment into words, but one of these little graphics suits the moment perfectly.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Finding the motivation to make a change can be tricky. It's difficult to resist the urge to procrastinate, or even give up when goals seem distant and difficult. If you wish you could stick to your New Year's resolutions, or maybe even just commit to pursuing smaller goals, you might want to consider making a small change to start: just create a new password.

Garlic: almost every cuisine in the world considers it a staple, and for good reason. Its pungent flavor gives depth and character to food. Dishes made without it seem bland and forgettable. And on top of all that, it's been studied for its potential anti-cancer properties (and don't forget: it's been mythologized for warding off vampires).

The "Smart Keyboard" on the LG G3 has received a lot of praise for its ability to adequately analyze user keystrokes, provide adjustable sizes, and customize key placements, among other things. These features, combined with predictive text, swipe gestures, and autocorrect make the Smart Keyboard one of the most powerful typing tools available for Android. Now, it's easy to get it installed on your Samsung Galaxy Note 3.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

The bootloaders on the AT&T and Verizon Wireless variants of the Samsung Galaxy Note 3 still cannot be unlocked, despite the $1,400+ bounty that arose late last year. Nine months later and still nothing. But just because we can't "unlock" the bootloader doesn't mean we can't get around it.

Sometimes when non-Asians go to ramen bars, they're mildly weirded out by watching the patrons eat. To the uninitiated, the eating behaviors can seem kind of extreme. Why are people hovering over their bowls like animals at a feeding trough? Why do they let endless lengths of noodles dangle from their maw as they slurp—very, very loudly—over their bowls of broth?

One of the most feature-packed camera suites out there resides on the Sony Xperia Z2. Along with the regular camera and video modes, it comes with Motiongraph, AR Effect, and Social Live.

Text input on a touchscreen device is constantly evolving. From early beginnings of pecking out each individual character to today's predictive text and gesture keyboards, we've already come a long way.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.

There are a lot of instances where we find ourselves typing virtually the same phrase that we've typed many times before. Whether it's the standard spousal reply of "I'll be home in a few", or a work-related phrase like "I'll have that to you by the end of the day", typing phrases like these can feel very redundant at times.

There's more to earning someone's trust than simply shaking their hand, especially if you're not particularly trustworthy. Your body language doesn't reveal your thoughts, it reveals your intentions, and sometimes intentions are better left unrevealed. Psychopaths, take note...

How do you begin to explain the nostalgia that's felt when you play a game from your childhood? You can't. The only thing that will alleviate this feeling is experiencing it again.

With only a few days left until Halloween, your options might be rather limited if you still don't have a costume. You may have laughed while some people spent the entire month of October painstakingly crafting their ridiculously detailed costumes, but now that the big day is so close, the joke's on you because you still have nothing to wear.

Last summer, Universal Pictures released the sequel to the popular 2010 animated film Despicable Me, bringing back everyone's favorite characters—the Minions. They're adorable, yellow, and they speak a gibberish "Banana Language." What's not to love? If you're planning on dressing yourself (or your kids) as Minions for Halloween this year, you'll be in good company. There are tons of costumes out there you can buy or make, and here are five of the best DIY options for you.

2011's The Artist was the first silent film to win an Academy Award since 1927. It was old school versus new school, and it won in unprecedented fashion.

Welcome back, my greenhorn hackers! I've been writing these Linux tutorials in an attempt to fill the void in the education of some aspiring hackers into the Linux operating system. There is a lot to know, and in this tutorial, we'll look at Linux file permissions. Step 1: Checking Permissions

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

In the Harry Potter world, there was a character by the name of Beedle the Bard, who told a story about witnessing the three Peverell brothers building a bridge out of magic and successfully crossing a very dangerous river that had claimed many lives.