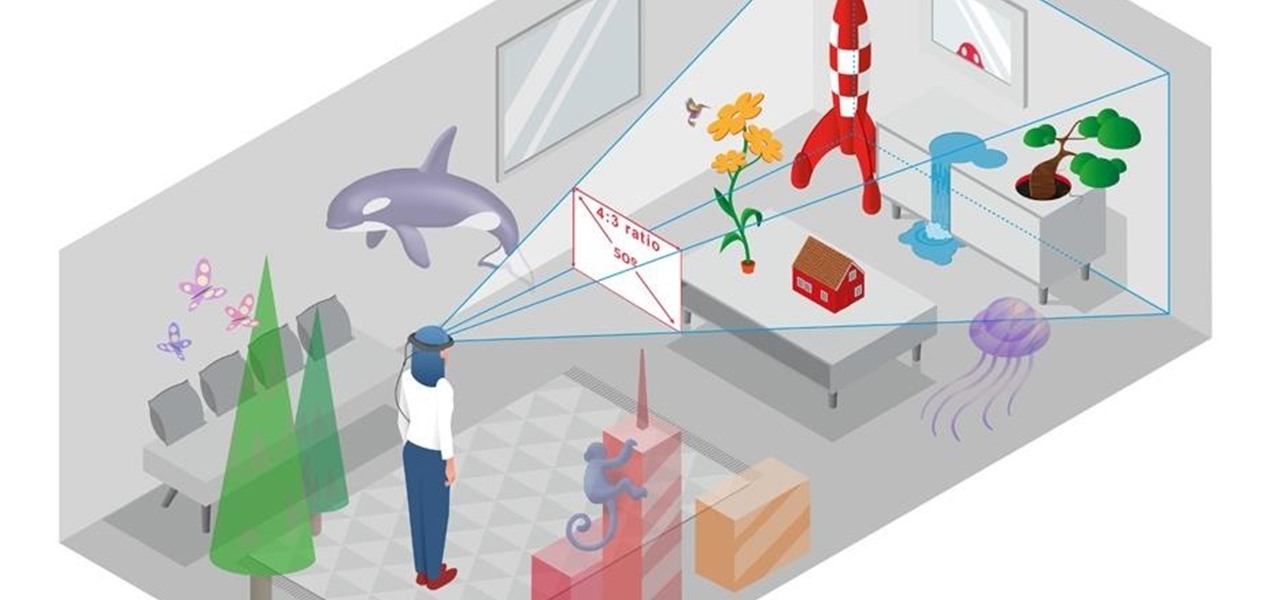
News: Magic Leap One Field of View Specs Finally Uncovered
In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.


In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.
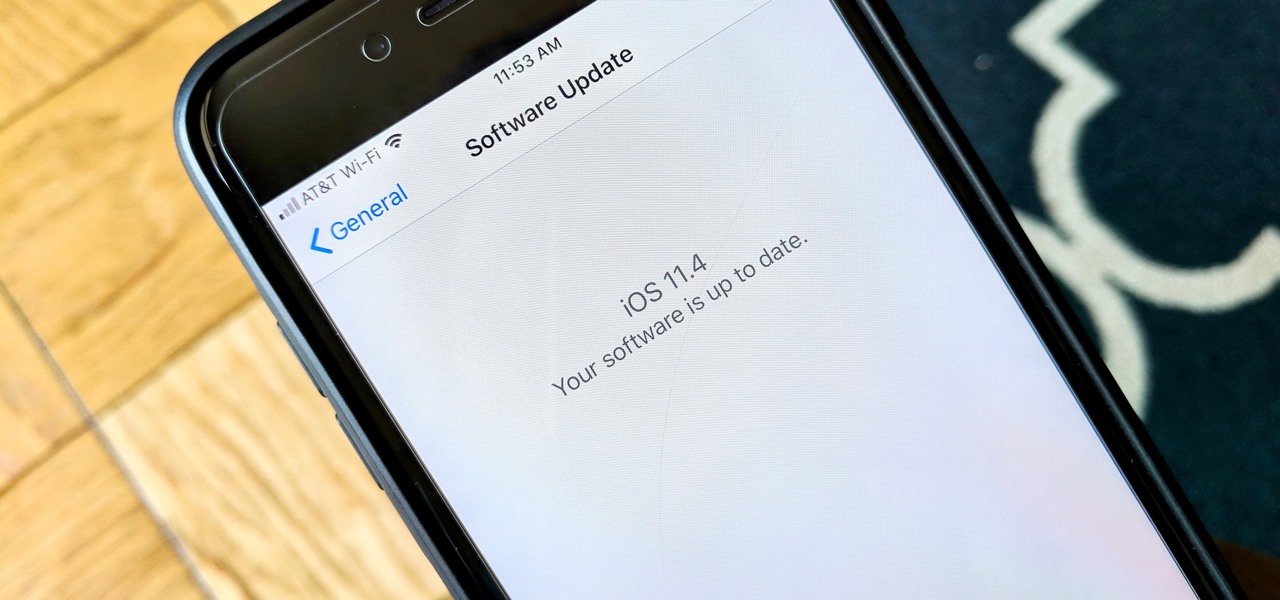
After six betas, iOS 11.4 was officially released to everyone with a compatible iPad, iPhone, and iPod touch. Some features are ones that Apple promised over eight months ago when iOS 11 was first pushed out. This update makes sense since iOS 12 will be announced at WWDC on June 4, and you can't announce a new version like that without first delivering on promises made for the one before it.

Apple's next big developer event happened on June 4, and it was the first glimpse of iOS 12 that anyone's seen. While there were lots of rumored features to be unveiled at WWDC 2018, Apple concentrated mostly on squashing bugs and making iOS work as seamless as it did years ago. Still, we had hoped that Apple would have added these features in iOS 12, but only a few made the cut.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Getting new loot can be challenging in Fortnite Battle Royale. Whether you decide to pay for the Battle Pass or stick with the Free Pass, you still need to put in 50+ hours to unlock all the items. For those of us with Amazon Prime subscriptions, there's another way to unlock free items, and it won't cost you an extra dime.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.
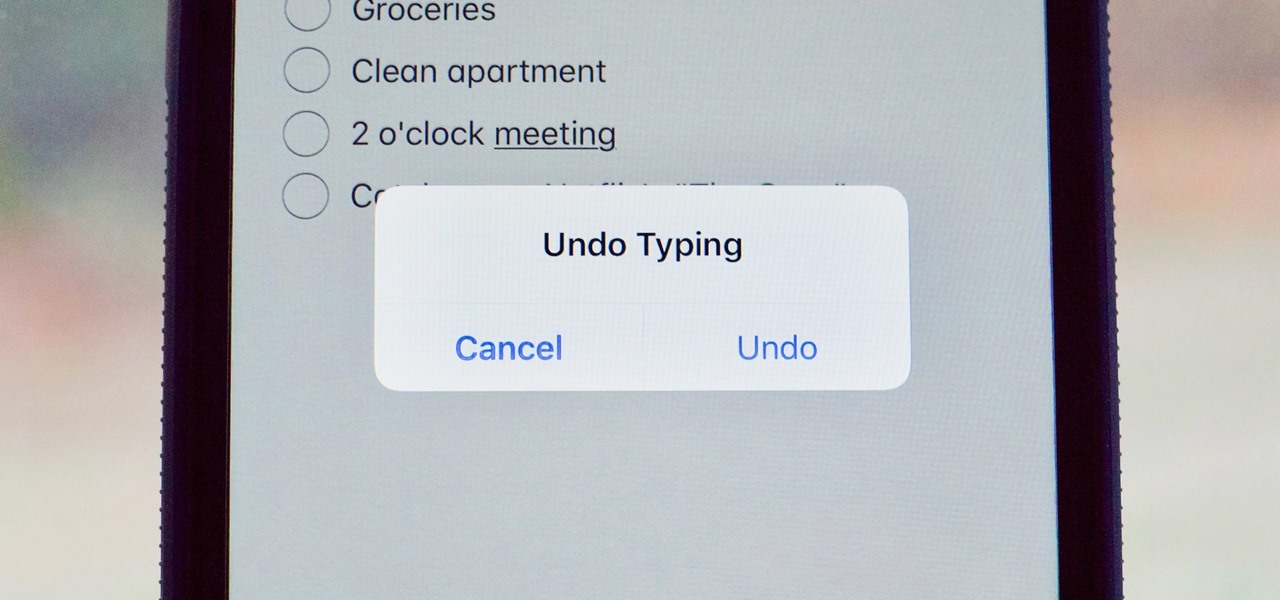
Many of us use the Notes app to jot things down in a hurry. Most of the time, that's no big deal. However, the faster the typing, the higher the chance of error. If you happen to make a typo, or if you accidentally delete that chart you worked so hard on, there's an easy way to undo the changes.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in time for the HomePod launch on Feb. 9.
Google just rolled out a revolutionary feature to its Pixel devices — Google Lens. Previously, Lens had only been available in the Photos app, but now, whenever you want to learn about something in the real world, you can just bring up Google Assistant, turn on the camera, then let Google's famous AI analyze the scene.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

New research explores how the bacteria on the penis can leave men more susceptible to infection with HIV.

Bitmojis are not only a good way to personalize your Snapchat account, but also a really fun Snap addition to play around with. A bitmoji is basically like your little avatar, letting you design your mini-self whichever way that you desire.

If you're someone who loves to read, you've probably read a book that made you want to hop into the story and live in the world that wasn't your own. Reading has a way of letting us escape into other worlds and experience things that we normally wouldn't be able to. Augmented reality is similar in that way. Which is why it makes sense that the two would be combined to create an incredible, immersive new way of reading.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

As headlines focus on melting glaciers and rising water levels caused by global warming, climate change is quietly taking its toll on the nearly invisible occupants of this planet, the microbes.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.
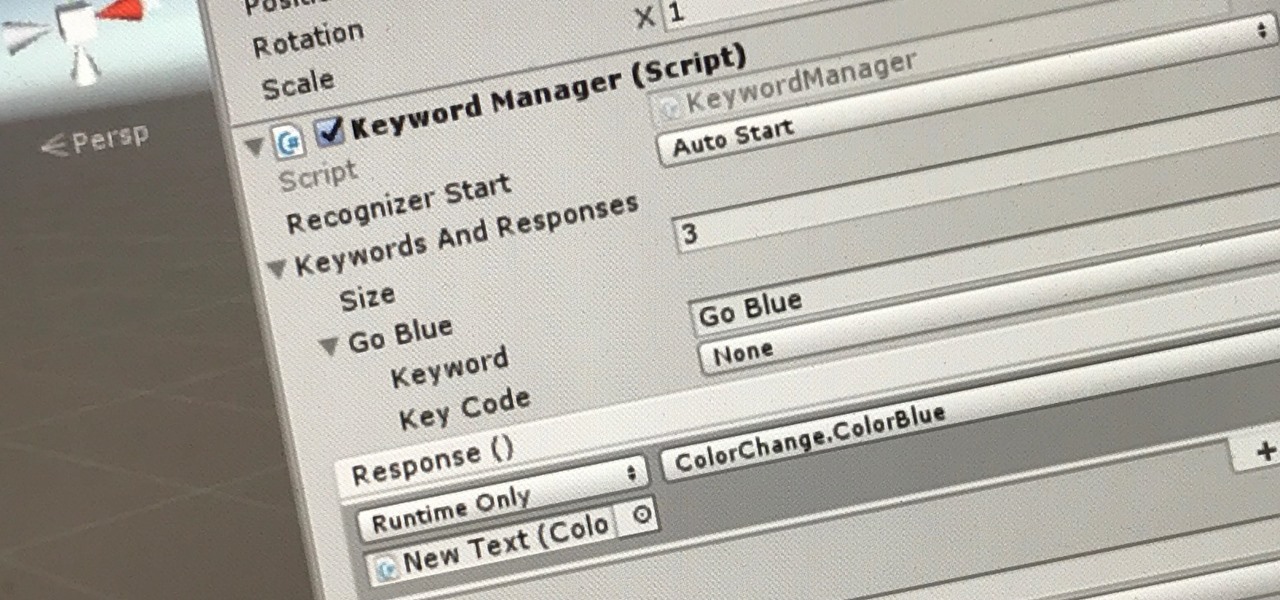
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

In Pokémon GO, having an in-depth understanding of your Pokémon's stats and abilities is crucially important to becoming a better player. Not all Pokémon are created equal; as such, it's critical that you look at each of your Pokémon—even duplicates—with a keen eye.

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

We love standing around a barbecue with an icy cold beverage in hand, enjoying the delicious smell of smoky food and chit-chatting with pals. Grilling season — it's our favorite time of the year.

Why, for the love of God, do people keep inventing ridiculous devices that make the simplest things more complicated in the name of convenience? This may be a rhetorical question that will forever go unanswered—because these crazy gadgets just keep rolling out, one after the other.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.
Welcome back Null-Byters! You finally have the pre-basics of CSS and we can begin with styling our web page. If you did not read our last adventure, I suggest you go and read it.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules: