
IRC Guide: Universal NickName
Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.


Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.
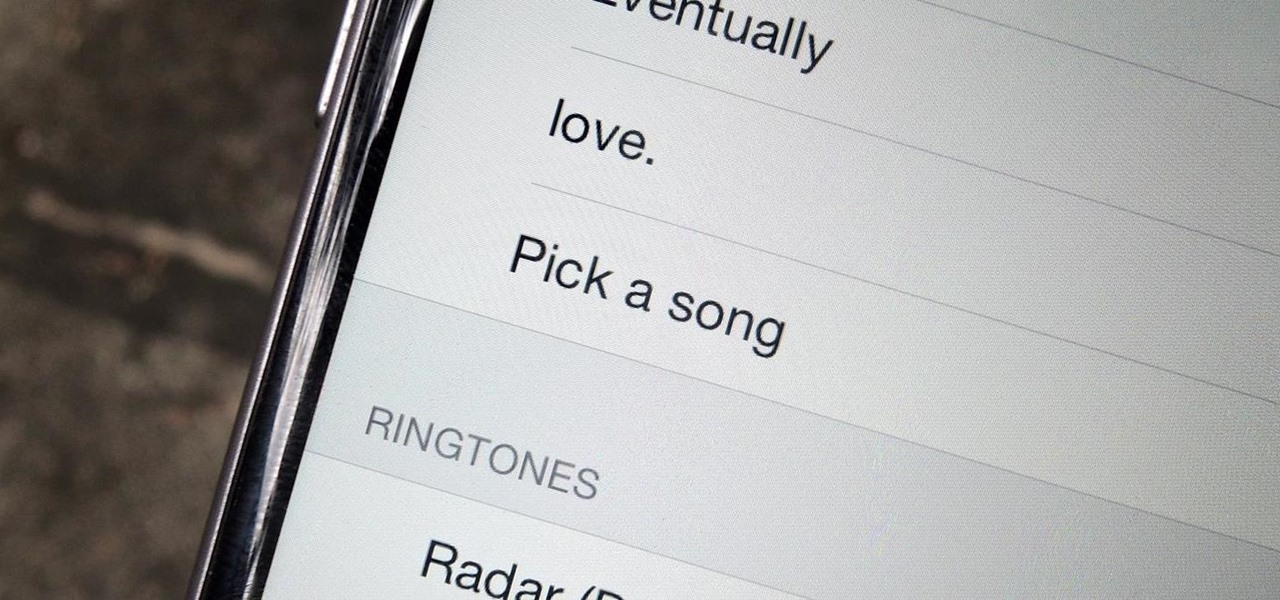
Don't like how Apple's default Radar ringtone — or any other tone — wakes you up in the morning? Then don't use them as your alarm sound. Instead, use your favorite song to get you out of bed. Whether you enjoy an acoustic tune or a heavy, energetic jam, you can choose any Apple Music song you want, or any track in your personal Music library, to get you going each day.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

A few years ago I went hog-wild trying to achieve a zero-waste lifestyle. I didn't succeed, but the experiment taught me that we throw away things we could—and should—be using more.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

When it comes to give away or sell your iPhone, you can't just power it down, take out the SIM card, and hope everything will be okay. There's valuable data on your iPhone, and you need to get rid of it. Plus, if you don't perform all the necessary steps, chances are whoever ends up with the device won't even be able to use it. If you're selling it, that could ding your seller reputation.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

UPDATE: The mod discussed below is no longer available for download. We are looking for an alternative and will update this page when we find one.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.
Alright, I'll admit it, iOS can be quite nice. Android loyalist that I may be, I'm not so stubborn that I can't recognize a good thing when I see it. Apple's iOS has a lot of strengths, and our Nexus 4s, god bless 'em, are growing a little long in the tooth.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

While it's not a highlight of the PlayStation 3, you can actually control the video game console with your smartphone. However, only certain aspects of the PS3 can be controlled from your iPhone, and it's not very obvious what you can and can't do — but that's where we come in.

It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Safari has a new feature that helps you discover the most beneficial aspects of a webpage without having to dig through the page or read the entire thing — and it works on iPhone, iPad, and Mac. It can make web browsing more efficient and websites easier to navigate while ensuring the visibility of important details.

As the iOS 18 beta continues, Apple's still investing time into fixing up iOS 17. Compared to iOS 17.4 and iOS 17.5, which both had over 30 new features and changes, iOS 17.6 is a relatively small software update for iPhone. But there are still some important things to know about.

Sure, you can remove apps from your iPhone's Home Screen without deleting them. But there's something satisfying about seeing them laid out and well-organized on the Home Screen, just a tap away, especially if you use user-selectable or custom icons for all your apps. Still, there may be days or situations when you want to hide apps without removing them entirely from the Home Screen.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

Apple's Podcasts app just got a big feature: transcripts. Before, you had to rely on third-party services or the off chance that podcast creators posted transcription links to each of their episodes. Now, you can view, read, and search show transcripts directly in Podcasts, whether uploaded from the creators or automatically generated by Apple.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

The volume buttons on the side of your iPhone can do more than just adjust the volume levels for media, ringers, alerts, Siri, and other sounds and voices. You can use them to perform different actions in certain apps and even create custom actions using the Shortcuts app. It's not exactly button mapping, but it's as close as you'll get without jailbreaking iOS.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.