Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Valentine's Day is upon us, and it's the perfect time to show those you love (or like) how you feel about them by making them a homemade sweet treat.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...
There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

Students have been passing notes in class for decades, so what's the big deal about sending a quick text message? Everybody does it, even your teacher was surely guilty of covertly communicating with his or her peers back when they were in high school.

When anyone brings up Tasker, the first topic that always gets discussed is how powerful the Android automation app can be. But all of that power can be overwhelming for some people, so even if you're a Tasker pro, it's hard to share your awesome creations with friends that don't quite understand what's going on.

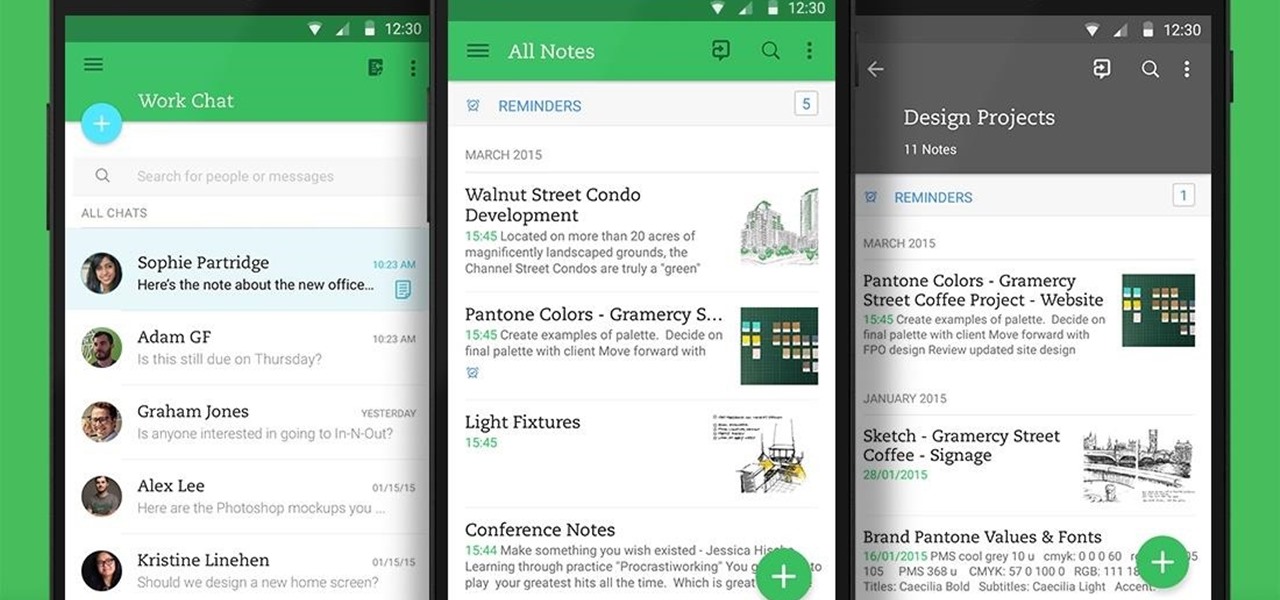
Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with won't satisfy most users. The good thing is that Google Play Store has a nice selection of productivity apps for every task. Below you'll find a list of apps that will help you gradually optimize and organize your digita...

When it's frigid outside, all you can think about is getting inside and shutting out the cold. But sometimes even the largest house can get a bit, well, stuffy.

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

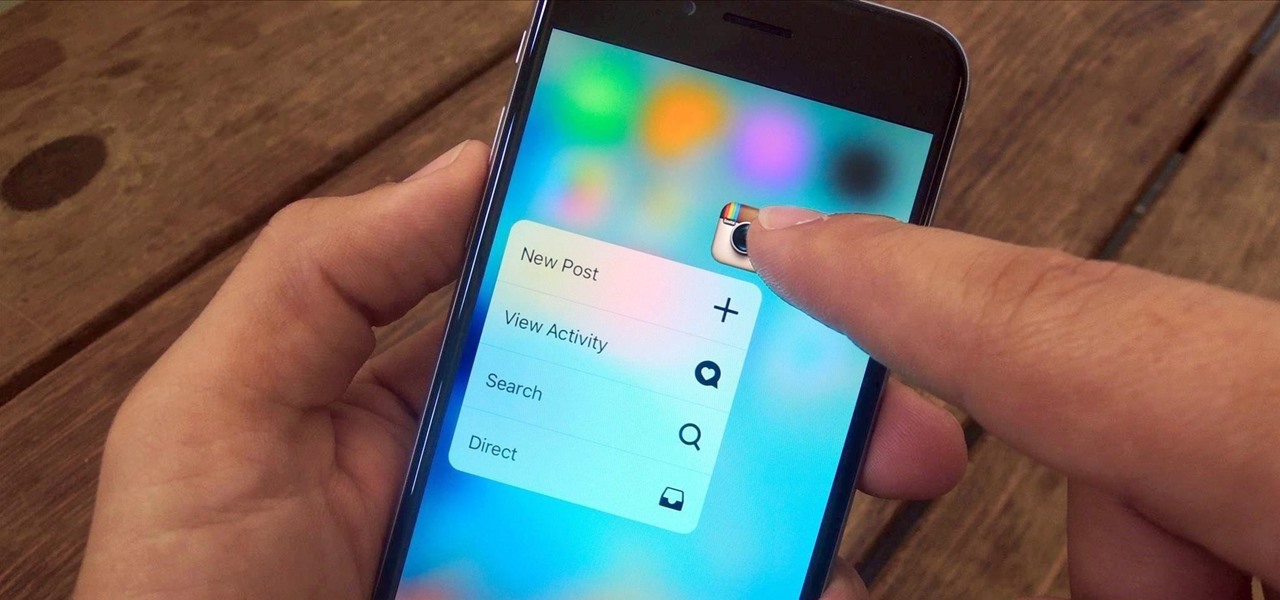
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

If you've been using Windows 10 for a while, you already know that Microsoft incorporated lots of new features into it. So you're probably familiar with Cortana (the new voice assistant), the Edge browser (their replacement for Internet Explorer), the newly resurrected Start menu, and all of the other big changes.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

I record close-cropped videos and take macro still shots with my smartphones on a daily basis, so as you would expect, I spend a lot of time cleaning these devices. Over the course of a couple years, I've fine-tuned my cleaning regimen, and at this point, it's down to a near-science.

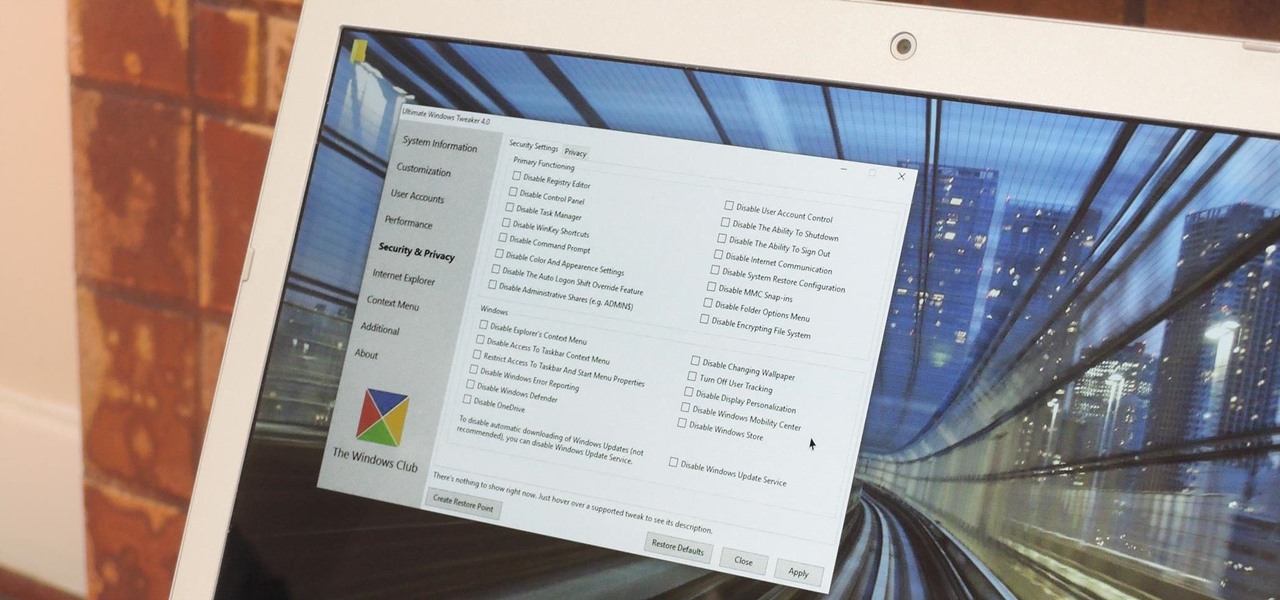
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

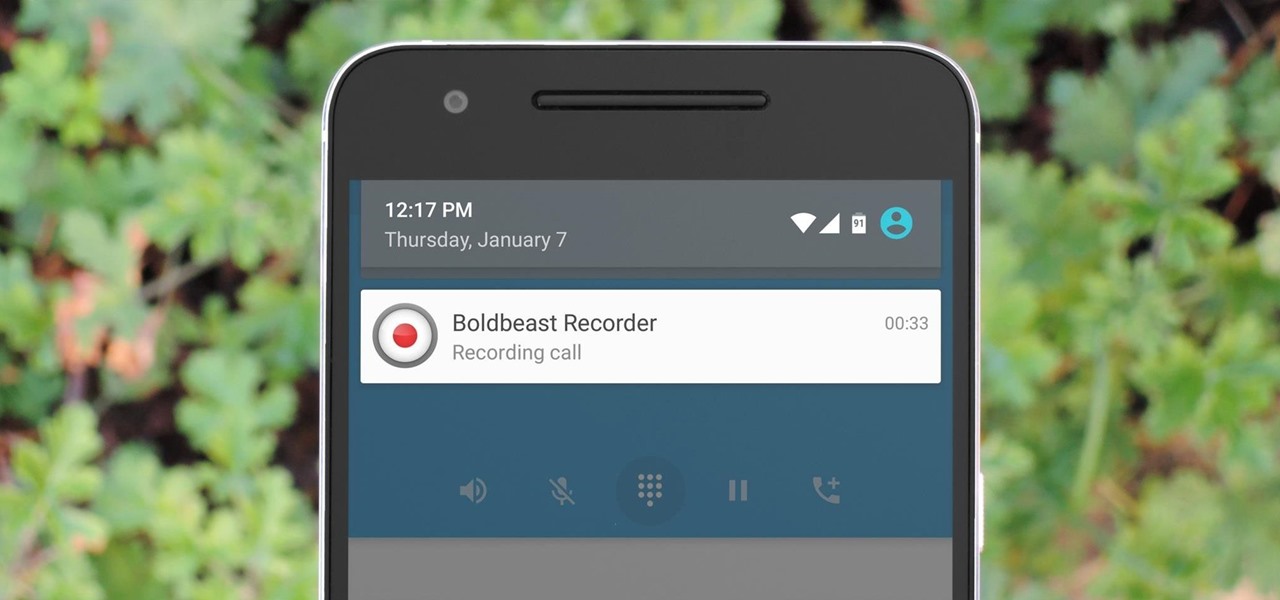
Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

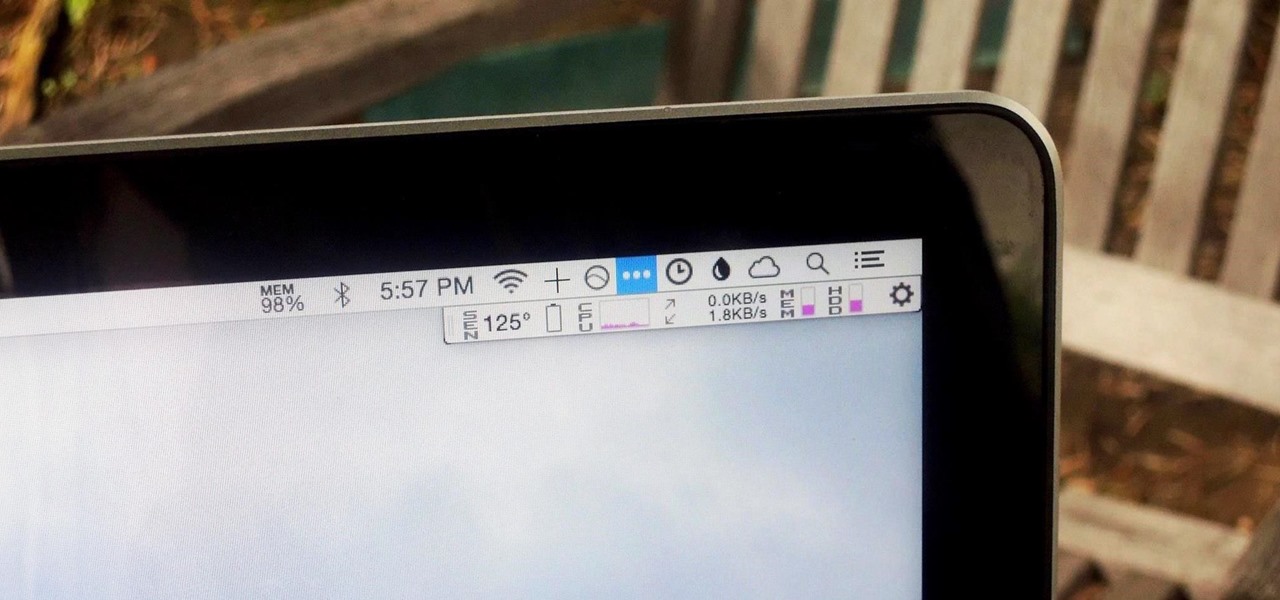
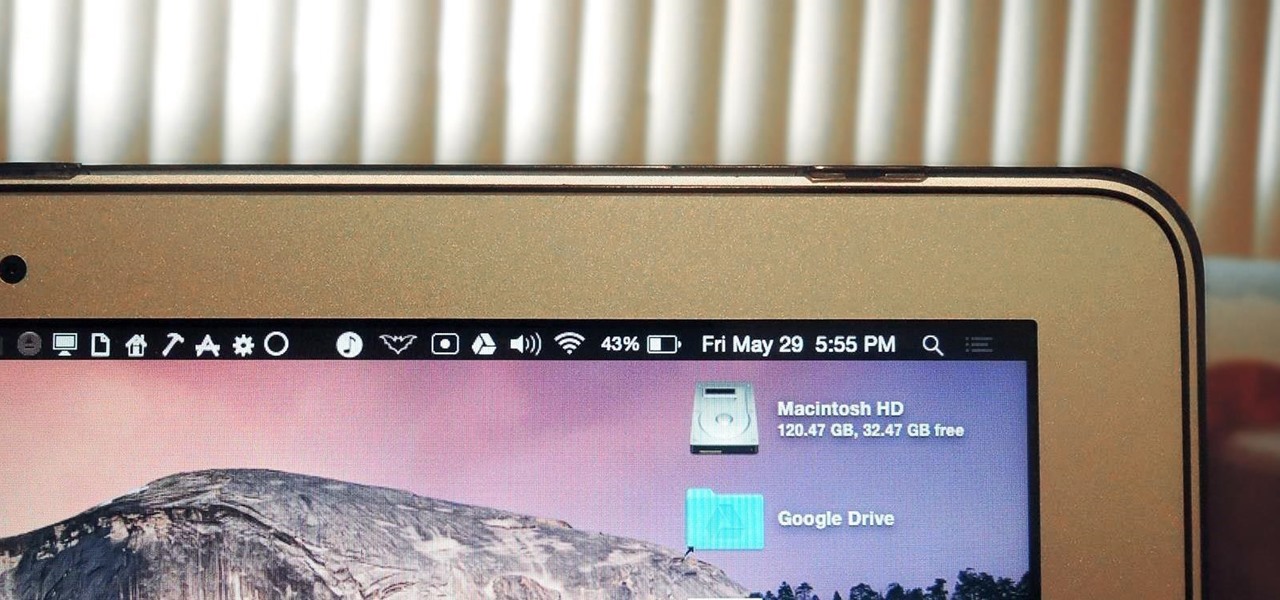
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen.

There are many reasons to root Android, but for me, the most important one is to have the Xposed Framework. Xposed gives you access to hundreds of modules, which take away the need to manually modify core system files to add new features and functionality to your Android device.

The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.

Part 1: What is Popcorn Time? Part 2: What is a torrent?

In the era of smartphones and cloud-based computing, it almost seems irresponsible to keep a stash of paper documents. Not only is a physical paper printout environmentally impractical, it's also a lot harder to organize and keep track of than a digital file stored on a hard drive.

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

The Nexus Player is one of the most robust set-top streaming devices on the market. This is mainly due to the fact that the base software it runs is a direct fork of Android, which is a very powerful operating system itself.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

We always want to find more ways to help brilliantly lazy cooks make great-tasting food and save money and time in the process. Luckily, our Facebook fans are invaluable sources of information when it comes to getting cool tips, behind-the-scenes info, and more.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

I've previously shown a few ways to make your iPhone a little more unique by customizing app icons on the home screen, and while those processes did not require a jailbreak, they were a pain in the ass. Thankfully, there's a better way to customize app and shortcut icons that's a lot less convoluted.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

The new iPhone 6 and 6 Plus are supposed to last a lot longer in your pocket with improved battery life, but that doesn't mean that iOS 8 will be that friendly on your older iPhone model. All of those awesome new features could be killing your battery, but with some simple tweaking, your battery life concerns will be a mere afterthought.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

If you're using iOS 10 or lower, there is no built-in way to record an iPad, iPhone, or iPod touch screen, and Apple doesn't allow any third-party apps to screen record either. If malicious, an app could theoretically continue recording even after you think it's off, allowing it to capture account and password information that you enter on your device. This changes in iOS 11, which introduces native screen recording, but what do you do if you're still running iOS 10 or lower?

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.