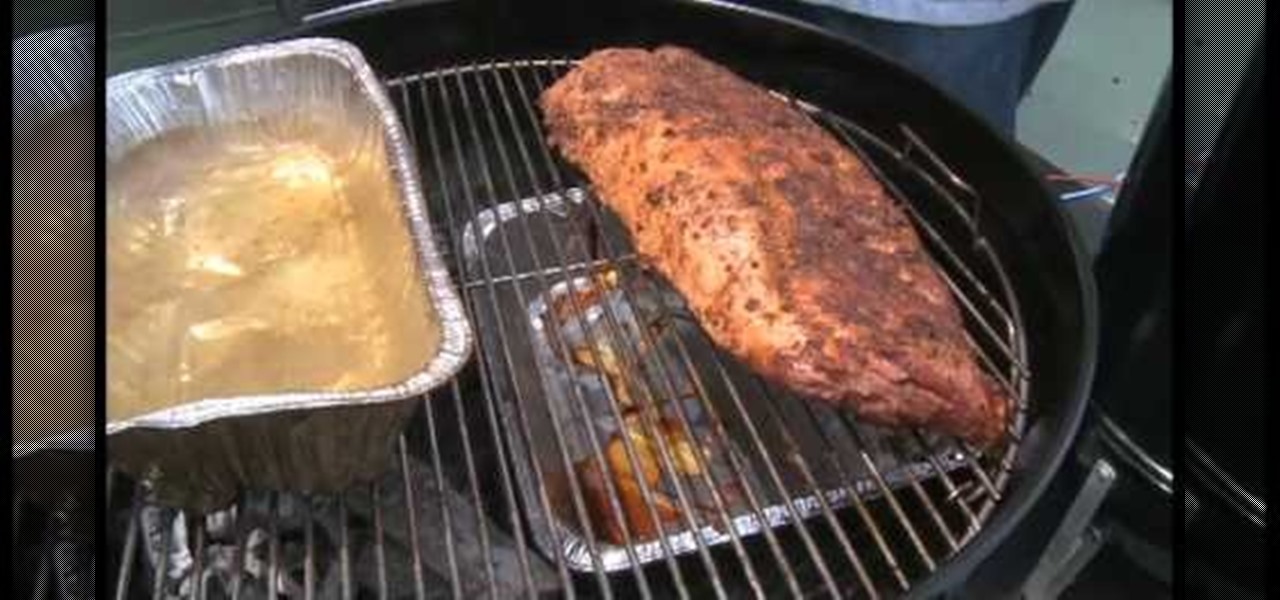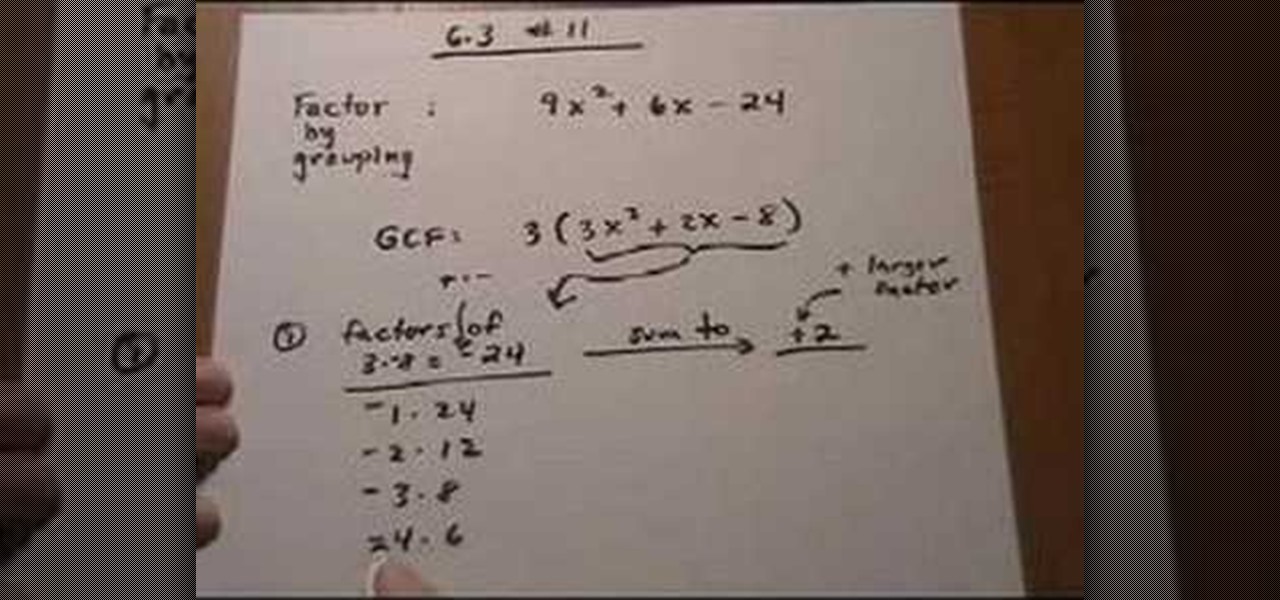While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

While Google isn't ready to commit to a wide release of the AR walking navigation mode for Google Maps, the company has begun testing the feature with members of its Local Guides crowdsourcing community.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Magic Leap has earned a reputation for overt secrecy, but as it nears the highly-anticipated launch of the Magic Leap One, the company is spilling some of the beans. This week, we get a heaping helping of information on the Lumin OS, as well as a couple of great demos.
Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

Apple is speeding things up in the iOS 11.4 development. The company released to developers the fifth beta for iOS 11.4 on Monday, May 15. Public beta testers got the update just hours later. The update comes just one week after the release of the fourth 11.4 beta, which introduced minor bug fixes and security patches to iPhone running the software. This beta version doesn't seem any different.

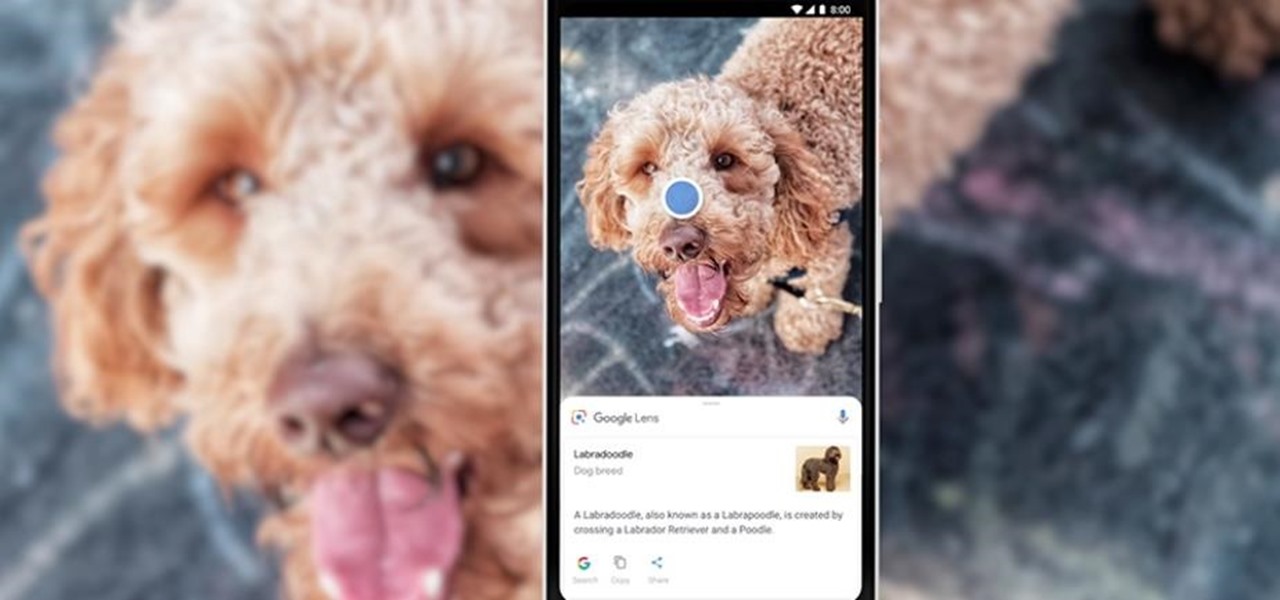
During Tuesday's keynote at the I/O developer conference, Google unveiled new capabilities for its Lens visual search engine and expanded the availability of the platform in smartphone camera apps.

Augmented reality is expected to eventually change everything, and the prevailing view is that those changes will be for the better. The converse view, however, is that the technology will further erode privacy.

Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

A new case of the still-mysterious Bourbon virus was confirmed in Missouri, likely originating within the state, local authorities said in a June 30 press release.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

Augmented reality is quickly becoming a popular tool for marketing use cases, as demonstrated by new projects serving the automotive, entertainment, and tourism industries this past week.

Ben & Jerry's addicts rejoice: Microsoft just won a patent for AR glasses that could help to combat overeating. Physical restraint is still needed to keep me away from that ice-creamy goodness, but a little virtual voice saying 'DON'T DO IT' could definitely help when the cravings come.

A new study published on April 12 in Medscape gives us an update on the Hantavirus genus of pathogens, which spread viruses via rodents that can cause fatal diseases in humans, such as hantavirus pulmonary syndrome (HPS).

Uber's driverless cabs began picking people up in Arizona in February, after its attempt at a pilot test in San Francisco. Now, one of these cars has been in an accident, and that's just the tip of the iceberg.

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

I grew up eating Korean, Japanese, and Chinese food, but it wasn't until college that I experienced Thai and Vietnamese cooking. Once I started, I couldn't get enough of these cuisines. The dishes had an incredible richness and savor that I couldn't identify, but whatever it was, it made me want to keep eating.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

John Kass from the Chicago Tribune and Gary Wiviott, author of Low & Slow, demonstrate how to make perfect ribs. The first step is to run them under cool water and rinse them with cider vinegar to clean them off. Second, coat them with mustard. This holds the rub on the rib. By holding the rub on, you will get more bark (the spicy, smokey, crusty exterior) on your rib. Gary's rub is a mix of 7 different toasted Mexican peppers, paprika, salt, black pepper. Make sure to place a good layer of r...

Rubber bands are an ordinary, everyday, common household item, right? Their hidden in your desk, wrapped around your bills, holding your pencils together at the office, but what else can you do with rubber bands? What are some extraordinary uses? Woman's Day Magazine tells you how you can repurpose those rubber bands!

John White (Doña Ana County Extension Agent) talks to Natalie Goldberg (Extension Plant Pathologist) about Powdery Mildew that affects many plants. They look at a Japonica that is heavily infested. Powdery Mildew is enhanced by shaded condition despite the dry climate. It starts with a spot spore infection that will easily spread by the wind or by rubbing. Control methods are difficult and involves a lot of routine applications of chemicals (ornamental fungicide) to keep it in check once the ...

Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...

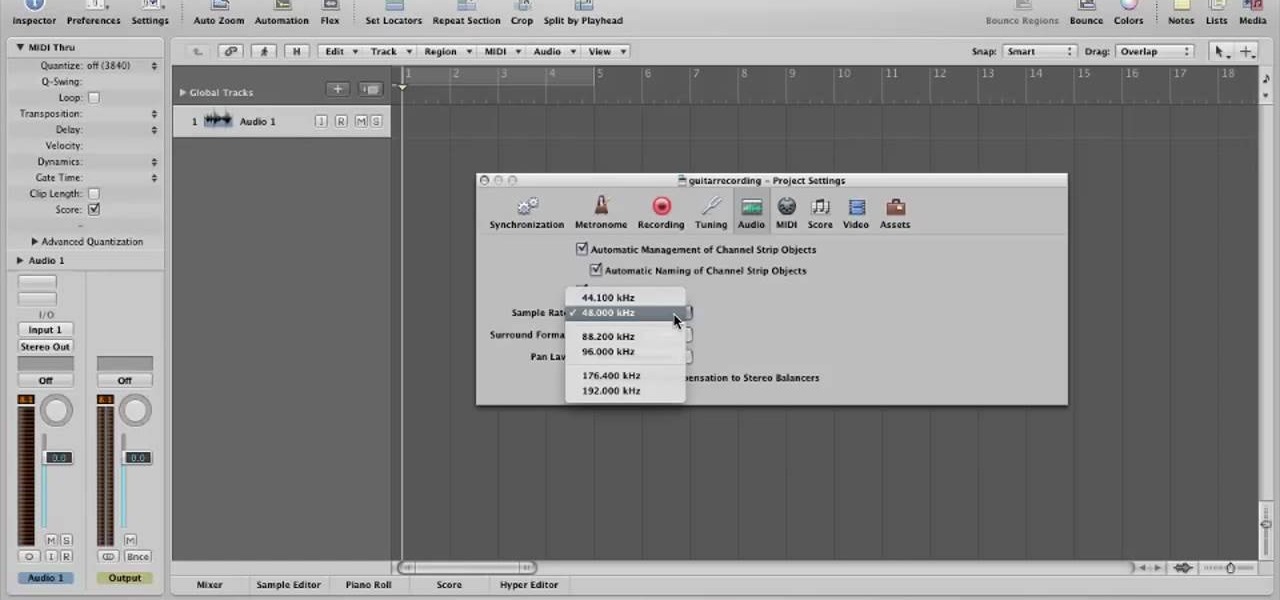
In this video, you will learn how to record using Apple Logic Pro 9. First, open the program and save the session. Make sure your audio interface is set before recording. Go to global settings and navigate to audio. Click on the general tab and change the audio settings. Wave files are the industry standard. Make sure 24-bit recording is checked. Software monitoring will allow you to monitor the audio. Save this and change the project settings. You can adjust the sample rate of your recording...

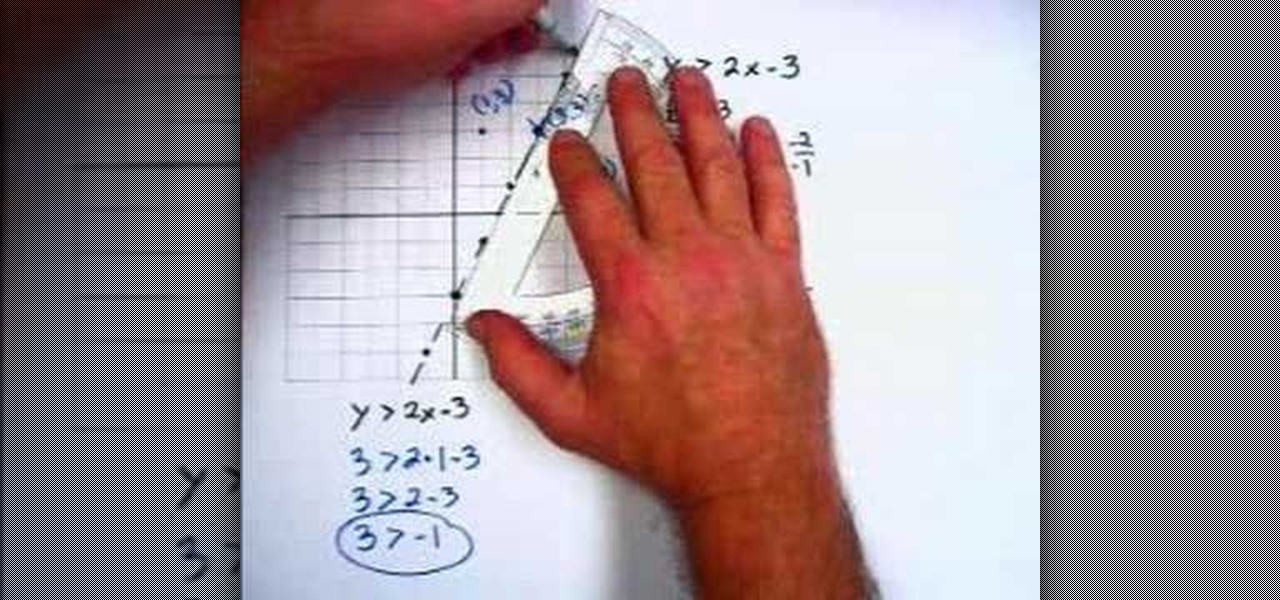
In this video the instructor shows how to graph linear inequalities. A linear in a equation is almost similar to a linear equation except for the sign in the equation. Now treat the in equation as a linear equation and graph the line. So substitute the lesser than or greater than symbol in the liner in equation with the equals to sign and graph the equation. Find the slope of the equation and identify the points that the line passes through. Now take a point on the either side of the pointed ...

The video deals with a clear step by step process of making a plastic airplane. He asked us to select the model of the airplane we are going to make first. He has selected the North American F86A SABRE model in this demo.

This video shows the method to change a word problem into algebra and to identify rational numbers among a group of numbers. In the first part of the video we take a word problem namely - The product of 9 and seven, less than a number. 9 multiplied by something can be expressed as 9(). The unknown number can be expressed as 'x'. Seven less than a number can be expressed as x - 7, so that the final equation becomes 9(x - 7). In the second part we are given a list of numbers. A rational number ...

In this video tutorial learn how to graph an equation using the slope and y-intercept. To show how this can be done, the equation 4X-5Y=20 is used as an example. The first step that needs to be done is to convert the equation into the y=mx+b format where m is the slope and b is the intersection of the y-intercept. Simply solve the equation for Y and you get Y=4/5X-4. From this, you will find that the slope, or m, is equal to 4/5 and that b is the coordinates 0 and -4. On the graph, you will w...

This lesson describes the method to find the factors of a trinomial, which consists of three terms, by grouping. First of all, factor out the greatest common factor (GCF), and write the reduced trinomial in parentheses. Let the terms of the trinomial be written in order of exponent of the variable. For example, 3(3X2+2X-8) trinomial is written in the order of variable, with 3(GCF) factored out. Now identify the coefficient of the first and last terms, for example in this case, it is 3 and 8. ...

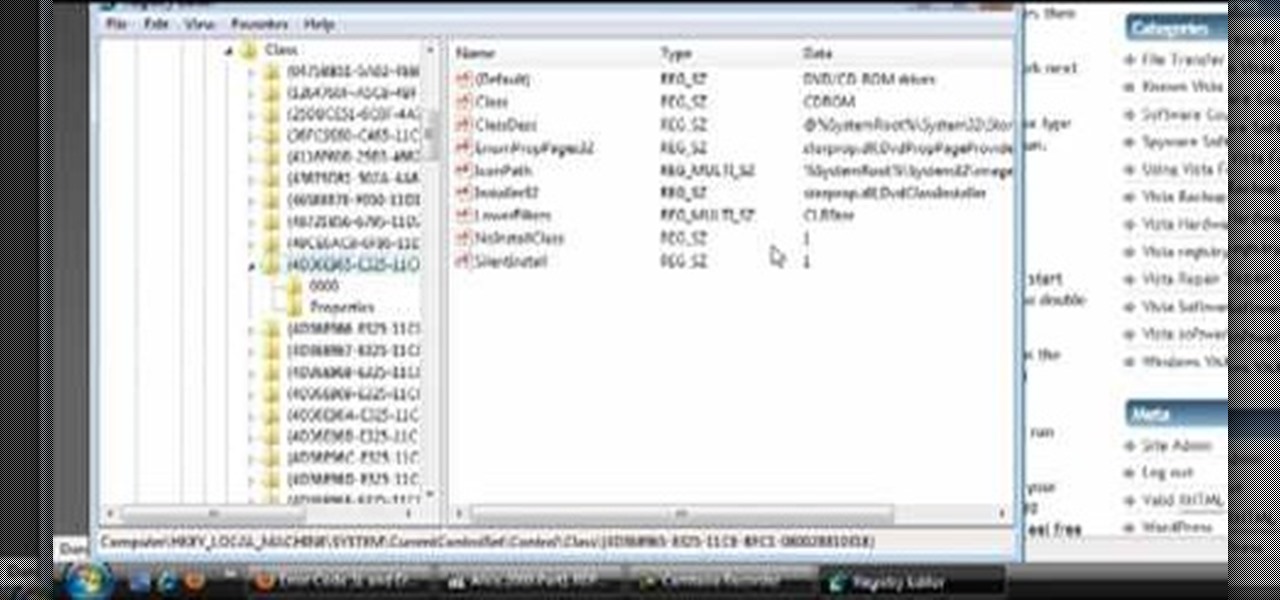
This how-to video explains how to fix DVD/CD player related issues with error code 31,32 or 19 in the computer that is having either Windows Vista or Windows 7 as their operating system.

The citizenship card is a document that naturalized Canadian citizens use to prove that they are Canadian citizens. This card is needed to get certain documents such as a Canadian passport. It never expires but it can be updated to include a new picture or name change. Citizens born in Canada do not use the card, they use their birth certificate to prove citizenship. Naturalized citizens can apply for this card and so can people with parents of Canadian descent. People who have previously had...