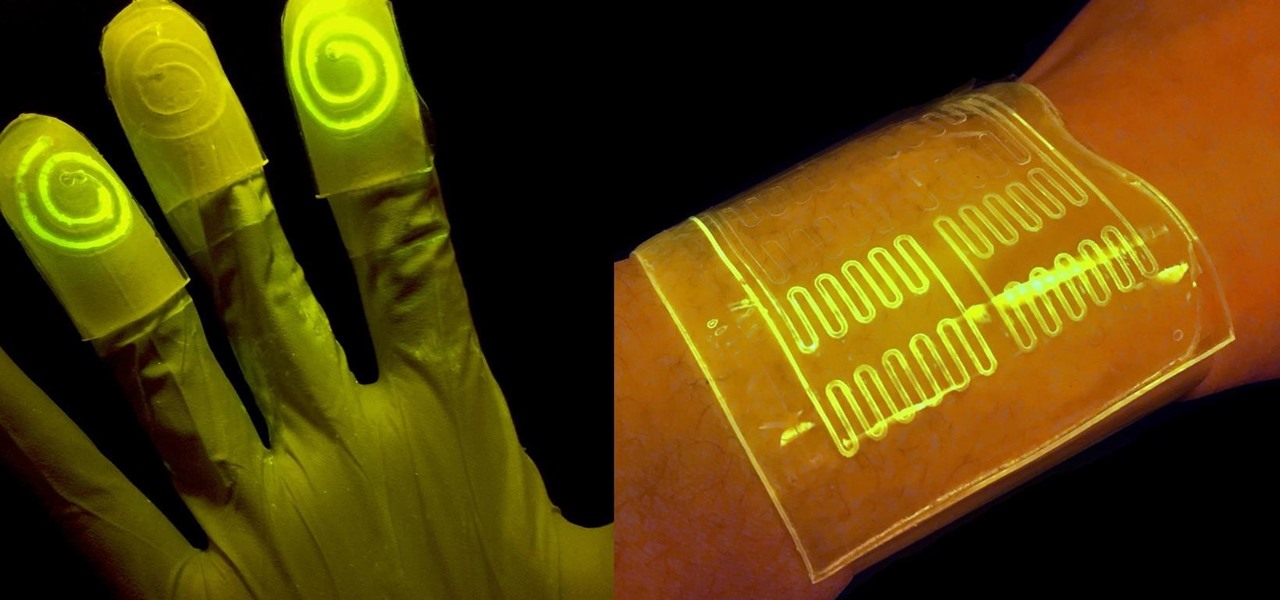
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

If you have encountered bed bugs lately, you are not alone. While the pesticides used to fight these pests are losing effectiveness, a fungus shows promise in knocking the bugs out of beds everywhere.

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

Customer service just got a lot more interesting. Construction equipment manufacturer Caterpillar just announced official availability of what they're calling the CAT LIVESHARE solution to customer support, which builds augmented reality capabilities into the platform.

Japan is in the process of curbing its aging population and mature workforce. According to The Diplomat, the country's population has been declining at a steady rate. To meet future productivity demands in commercial and industrial sectors, local officials are turning to self-driving technology, including truck platooning, where three or five vehicles travel autonomously in a string formation. This practice, according to a study by MIT, can reduce fuel consumption by up to 20% (more about thi...

Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.

There are two types of Halloween lovers: Those who like culturally-relevant costumes and serving precious ghost cupcakes, and those who live to freak their friends the hell out in the most disgusting way possible.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

Most of us know how to make a sandwich, but how many of us know how to make a sandwich correctly—i.e., so that the slippery ingredients like tomatoes and cucumber don't come gushing out the other end when we take a bite?

Beer, glorious beer! It can stop grilled meats from producing carcinogens, can make fried foods super crunchy, and it even saved civilization from total annihilation. Is there anything it can't do? Sadly, yes.

There are a lot of techniques out there for how to cook the perfect steak, from flipping it multiple times to applying a spice rub or dry brine to aging the beef. But it turns out that there's a super-easy way to make a great steak at home, and all you need is a good cast-iron skillet and some salt.

Who doesn't enjoy sitting down to a nice dinner with a cocktail in hand? After a long day, a drink is a great way to unwind. Yet your favorite spirits can do more than just help you relax after work. By utilizing alcohol in the kitchen, you can enhance everything from how food tastes to your health.

When I became serious about cooking, nearly every cookbook and guide I picked up emphasized the importance of using fresh stock, whether it was chicken, beef, or vegetable. When I didn't have time to make my own, I bought the highest quality boxed or canned stock I could find at the market.

With the introduction of the Control Center in iOS 7, we finally had a way to access common system toggles like Wi-Fi, Airplane Mode, and best of all, Flashlight. Of course, there were plenty of adequate flashlight apps in the iOS App Store, but none that made it available straight from the lock screen.

When you're scrolling through your iPhone's home screens, you'll inevitably reach the end and have to either swipe backwards or hit the Home button to return to the first page. Why Apple didn't instill an endless scrolling feature, or at the very least an option for it, is anyone's guess, but just because you can't do it out of the box doesn't mean you can't do it.

Whether you call 'em soda, pop, fizz, or coke, carbonated soft drinks are among the least healthy beverages out there, yet they're consumed by millions of Americans every day. For those of you worried about your health, there are diet and zero-calorie options available, but are they really better for you?

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Installing clutch shoes is very simple. What you need are the clutch shoes, clutch shoe installation/removal tool which costs about $5 or a flat tip screwdriver. First, line up the clutch shoe. Plastic shoes wear out faster. Aluminum last longer. With the screwdriver method you bend the spring out. Take the bent out spring and push it down. Push it straight down. This is not the authors favorite method. Using the clutch shoe installation tool, simply push the spring out and push straight down...

This is a video tutorial on how to create a mouseover link (button) in Flash. According to the author, this is an extremely easy task, the first step of which is to select the file in which the button is to be made. Then, on the extreme right-hand side, in the middle of the column of icons, one has to choose the button icon, and then select which shape and color of the button one would prefer. The text is then typed in the text box selected over the button, and converted into a symbol by pres...

Your brain actually needs to be refueled throughout the day, and our brains function best on carbohydrates. Brain foods like fruits and fish are important for fueling your brain all throughout the day. Learn some tips on eating brain foods and keeping your mind active in this nutrition how-to video.

In this video series, our expert Tim Kimmel will show you ho to do a non-fiction book proposal. Mr. Kimmel will teach you how to write a title page, a table of contents, and a synopsis for a book proposal; all in the way the publishers like to receive them. Tim will also teach you how to write an author's bio, and tell you a bit about market strategy so you know your words are reaching the right ears.

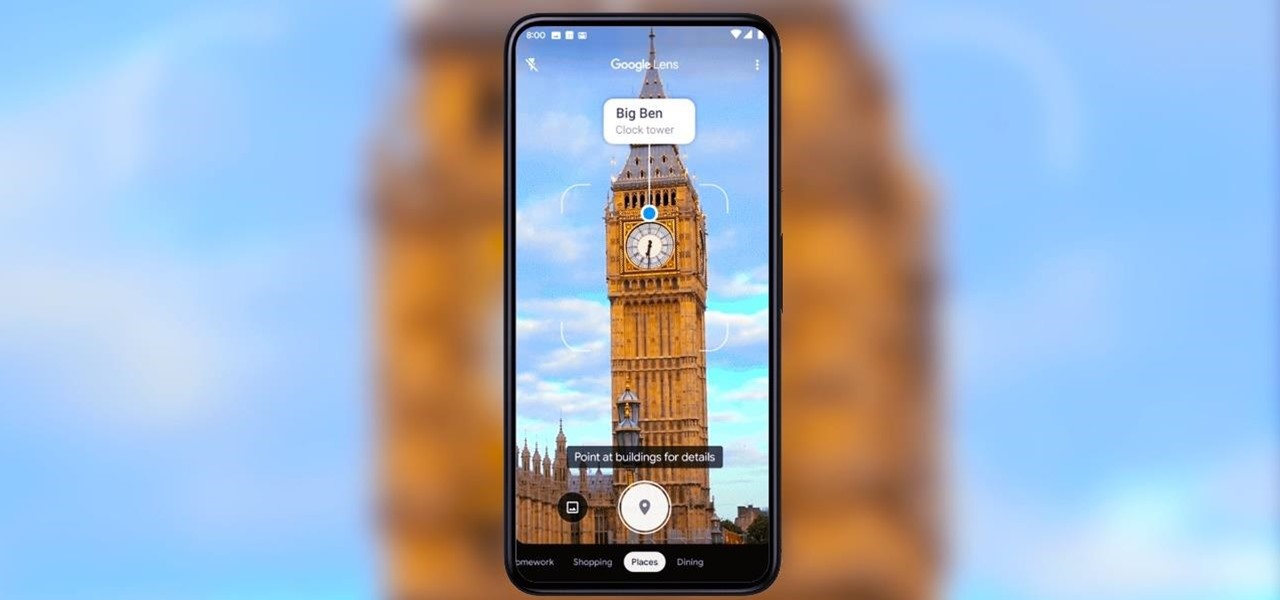
This week, Apple unveiled its own version of Google Lens in the form of Live Text. In response, Google just hit back with a new feature for its visual search tool called Places, a new search category that can recognize landmarks and return information on them within the camera view, which Apple touted as a capability of Live Text during its WWDC keynote.

Wireless headphones are convenient, comfortable, and more common than ever before. With the massive proliferation of wireless earbuds, it's hard to identify which ones are good and which ones just want to look like they're worth the price. Avanca T1 Bluetooth Wireless Earbuds are high-quality wireless earbuds with excellent functionality and a low price of $29.95 now that they're 50% off.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

For the average consumer, augmented reality is a fun way of dressing up photos and videos for social media. However, AR is also gaining momentum as a medium for storytelling, particularly in sharing powerful messages.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

It's time to make some more room at the augmented reality cosmetics counter. This week, social media giant Pinterest unveiled "Try On," a virtual make-up visualization tool running on its Lens visual search tool.